Why Endpoint Security Issues in Protecting Remote Employees – Part 2
As attack areas expand customers see enhanced presence with AMP for Endpoints!
In part 1 of the blog series we discussed how securing your workforce on any endpoint, anywhere, at any right time, is more important than previously now, and that Cisco AMP for Endpoints performs a critical role in the brand new Cisco Protected Remote Worker solution that connects and protects people and products working remotely.
In the initial entry of the blog series we promised to have a a lot more in-depth look at our customer’s applying for grants the worthiness that AMP for Endpoints provides with their business. As an instant recap the very best 3 business ideals from that Endpoint survey are usually:
- Better visibility – for insights and security to avoid threats from the expanding strike surface
- Better efficacy – to remediate faster and fully expose, contain and solve threats
- Getting time back – for improved security performance, eliminating complexity and improving security admin efficiency
Now partly 2 of the series let’s check out the very first of the very best three business values – presence.
Company Value #1: Better presence into endpoints
The customer challenge: Customers reveal that their endpoints are usually under constant attack through phishing attempts, advanced persistent threats (APTs) and exploits. Among the key must defend their networks would be to arm groups with better presence and actionable insights. Sufficient reason for recent events in conjunction with the new actuality of securing remote employees, we have been hearing; “…endpoints are moving, a lot more, from the office at this point …we make use of Cisco AMP and Umbrella on those endpoints to protected them also to deliver consistent plan.”
Presence described: A definition is to be able. The short solution is that presence provides protection practitioners the opportunity to see threat standing, indicators and timelines on endpoints (along with the files) on an overview basis or separately. You can find other ways to spell it out presence, but as our AMP for Endpoint clients prefer to say, “we are able to see everything that’s heading on inside our endpoints.” Which is very valuable.
Why it’s essential: As mentioned within the first blog, if you don’t have presence into your endpoints you truly don’t understand if malware exists or where it originated from. Consequently, your group could waste precious time wanting to eradicate low concern threats or possess threats go undetected, even while your infrastructure could possibly be at risk from possible malware lateral motion. Our clients have noticed the huge benefits after deploying AMP for Endpoints, as you mentions; “It has decreased time and energy to detection by 95%. A whole lot of enough time, to having AMP prior, …we weren’t alert to any kind of malicious activity until a direct effect was had because of it on the organization.”
Let’s have a look at three types of visibility now; (1) a high-level look at of endpoint safety through the dashboard, and (2) a drill down of activities that happened on a particular endpoint that people call gadget trajectory, and lastly, (3) a snapshot watch from Orbital, our Advanced Research feature.
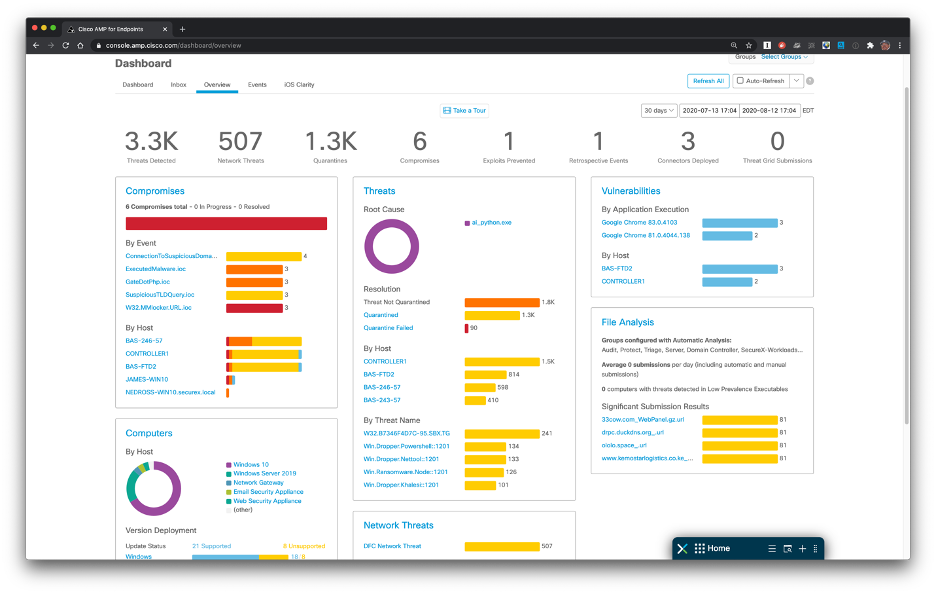
Dashboard view: The AMP for Endpoints dashboard see has an instantaneous real-period snapshot of key elements such as Compromises, Vulnerabilities and threats. The key objective would be to help the protection team understand routines on the endpoint and assist determine priorities. It offers a quick look at of many other factors while enabling an individual mouse click for more information, from the dashboard. A standard comments from customers we hear is, “For the endpoint, Cisco gives us good clearness in what our endpoints are doing actually. When we get poor actors in to the network, we obtain fast visibility into which gadgets are compromised.”
 Figure 1: An endpoint safety engineer or SOC analyst can buy a real-time overview of endpoints position and events
Figure 1: An endpoint safety engineer or SOC analyst can buy a real-time overview of endpoints position and events
Gadget Trajectory: Unlike the dashboard view which gives a worldwide summary of endpoint action, tools like document trajectory, and regarding gadget trajectory below depicted within figure 2, use AMP’s continuous evaluation capabilities showing your security group the entire scope of a risk. AMP identifies all impacted applications, processes, and techniques to pinpoint threats such as for example patient zero, and also the point and approach to entry. These features help your team rapidly see and realize the scope of the issue by determining malware gateways and the road that attackers are employing to get a foothold into various other systems. Hence, in a customer’s phrases, “If malware has contaminated a certain laptop computer, we get all of the forensic proof around that notebook and, if it’s jumped, where that bad things provides jumped to and what it’s completed. All that visibility can be done due to AMP for Endpoints.”
 Figure 2: These devices trajectory helps the protection team perform forensics upon specific endpoints
Figure 2: These devices trajectory helps the protection team perform forensics upon specific endpoints
Forensic Snapshots with Orbital Advanced Lookup: Especially ideal for threat hunters, we are able to catch a forensic snapshot of data from an endpoint such as for example running processes, open up network ports and a whole lot more during detection or upon demand. You can consider it as a “freeze framing exercise” on an endpoint to as soon as when something malicious had been seen. This enables you to know just what was happening on your own endpoint at that true time. It’s big on providing you time back! Among our customers, a safety consultant, describes it this real way, “…Orbital is conserving us five to eight hrs per incident. Week in one, it might save eight hours, another week and then, it might save 32 hrs.”
 Figure 3: Rapidly get yourself a forensic snapshot in close to real-time upon any endpoint.
Figure 3: Rapidly get yourself a forensic snapshot in close to real-time upon any endpoint.
Wait! There’s a lot more: With AMP for Endpoints, you get access to our built-in SecureX system, providing integration with some other Cisco security technology and an array of third-party items, backed by Talos threat intelligence, to assist you prevent, detect, investigate, and react to threats across your complete atmosphere – not at your endpoints just.
Among our customer information that; “This remedy interfaces with Talos Cleverness, Threat Grid, SecureX Threat Reaction and the SecureX (system). Most of these items are integrating collectively and lots of security is right now needs to happen automatically…”
For another entry in this collection
Within the next blog access of this series we shall dive in to the second of the three business values (better efficacy) and demonstrate how our customers are receiving the results they want.
For the time being, please go to the TechValidate Survey and IT Central Station testimonials to see types of what our customer’s problems were, and within their own words, convey how they were in a position to achieve their company goals with Cisco AMP for Endpoints as area of the Cisco SecureX platform.

You must be logged in to post a comment.