Why Cisco Joined the Confidential Processing Consortium
Creating a Networked Mesh of Hacker-Resistant Software program
The world’s digital devices derive from layered software program stacks. Each one of these layers provides its security vulnerabilities. An effective attack made into among the layers of software program is normally leveraged to exploit another coating.
Some digital gadgets embed internal protections to limit potential harm. These protections are built making use of shared keys, certificates, or passwords even. Unfortunately, these shared techniques could be compromised also. Additionally, application software level must implicitly rely on underlying layers like the Operating hypervisor or even System manager. And, for these apps, there is little that you can do when the most essential layers of a tool are actively getting exploited.
Over the years, a number of security technologies have already been implemented to safeguard digital devices. From anti-virus to firewalls to intrusion recognition systems, entire industrial sectors have already been born. But hackers continue steadily to overcome these protections. As as developers continue steadily to build conventional layers of software lengthy, and as lengthy as our protections be determined by software-based shared secrets, safety exploits will continue.
Confidential Computing supplies a new paradigm. Constructed upon strategies which leave the precise computing chips never, one layer of software program could be protected from exploits while it began with another layer now. In addition, a hacker who offers obtained administrative privileges for a device’s OPERATING-SYSTEM will be struggling to read or alter an application’s information or code.
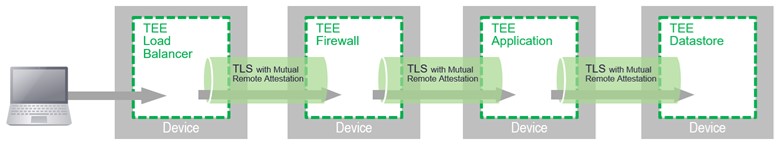
You can find two foundational Confidential Computing technologies that enable this brand new paradigm. The foremost is the hardware-centered Trusted Execution Atmosphere (TEE). There exists a course of TEE that allows application program code to end up being compiled, signed, and encrypted by way of a software developer. That program code can only just be executed and decrypted inside a compliant TEE. Subsequent memory or disk exchanges with the CPU are encrypted fully. A root hacker cannot check out the memory even.
But utilizing a TEE to run an authentic application is only area of the solution verifiably. This will be where the next foundational technology performs a job. This technology is called Remote Attestation. With Remote control Attestation, a credit card applicatoin within a TEE may assert the safe context in which it really is running externally. Consequently, the TEE’s remote peer may verify that it’s interfacing with a identified, secured example of untampered software.
2 peers have verified each additional’s identity once, it becomes possible to integrate several models of trustworthy peers collectively. The result is really a mesh of connected trusted software directly. This eliminates entire lessons of OPERATING-SYSTEM and hypervisor supervisor compromises from the set of attack surfaces a hacker might exploit.

Addressing these trustworthy meshes shall need agreements upon the inter-device protocols necessary for Remote Attestation. A few of these protocols shall not be considered a surprise. For example, we are able to assume technologies like Transportation Layer Security (TLS) may be used for connecting the TEE. But within TLS, we will nevertheless need an industry-accepted language for communicating Remote control Attestation claims in regards to a TEE. Such standardization of the protocols will need work and time.
The good thing is progress has been made. One spot to look may be the IETF’s Remote control Attestation Functioning Group. In this location, architectures for this kind of specs are nearing completion. But neither the IETF nor other conventional standards bodies need to float particular protocol proposals yet. Implementers only get access to a couple of vendor-powered proposals. And each one of these proposals provides already been framed upon the assumptions fundamental a vendor’s particular TEE chipset.
That’s where the Confidential Computing Consortium (CCC) is well positioned to are likely involved. Within the CCC, you can find tasks for acquiring attestable details out of TEEs. One of these brilliant tasks is Open up Enclave SDK for Intel SGX. Additional venues can be found for parallel efforts such as for example OP-TEE for Arm TrustZone. But these projects scratch the top of what can become Remotely Attested just. Only today is the industry able to try to generalize and agree upon:
-
- The definitions of particular attestable TEE promises
-
- The amount of trust which can be related with a kind of TEE as well as on a particular TEE instance
-
- Appropriate stacks of network transportation protocols and encodings
-
- The way the initiator of a demand can verify just approved TEEs have already been used to provide an end-to-end perform
Accomplishing these objectives shall need effort. Allowing process extensibility and vendor neutrality will undoubtedly be non-trivial simultaneously. The CCC can impact these discussions.
At Cisco, we treatment a good deal about the standing of networking peers. Our known reasons for signing up for the CCC are basic. We will advocate for Remote control Attestation interoperability. And we are likely to integrate Remote control Attestation into our System Admission Manage portfolio. We think both have substantial potential to lessen the risks which come from today’s layered software program stacks.
Have a look at our Cisco Networking movie channel
Sign up to the Cisco Networking weblog

You must be logged in to post a comment.