
What’s in the latest Chrome update? Whole lot of security, privacy shakin’ goin’ on

Google this week released Chrome 83, picking up after skipping a version because of the COVID-19 pandemic, auto-upgrading eligible users to DNS-over-HTTPS (DoH) and enabling tab groups for everyone.
The search firm paid at least $76,000 in bounties to bug researchers who reported some of the 38 vulnerabilities patched in Chrome 83. Five were marked “High,” the second-most serious in Google’s four-level threat ranking, with three of those marked as “use after free” flaws. The first vulnerability listed, a use-after-free bug in Chrome’s reader mode, earned researcher Woojin Oh a $20,000 reward.
Chrome updates in the background, so most users can finish the refresh by relaunching the browser. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab shows that the browser has been updated or displays the download process before presenting a “Relaunch” button. Those who are new to Chrome can download version 83 for Windows, macOS and Linux directly.
Google updates Chrome every six to eight weeks; the previous upgrade landed April 7.
Note: Google suspended Chrome releases in mid-March because of the pandemic and its impact on businesses. Chrome 81 was slated to launch March 16 but was postponed three weeks. Google skipped Chrome 82 and resumed upgrade numbering on May 19 with Chrome 83. Chrome 84 will be the next upgrade.
Tab grouping…, we really mean it this time!
Tab Groups, a feature that Google has been working on and testing for months, does what it says: Users organize tabs in the bar atop the browser by lumping together several tabs, each lump designated by color and name, adding new tabs and removing existing ones.
The feature was to debut in February’s Chrome 80, then in a roll-out “throughout Chrome 81.” Except it didn’t. Google now says, “This has been rolled out to Chrome, Mac, Windows, and Linux users throughout Chrome 83,” as in past tense. Except it hasn’t: All of Computerworld‘s instances of Chrome 83 – both on Windows 10 and macOS – still lacked the tool.
Those without tab grouping can switch it on manually by entering chrome://flags in the address bar, searching for Tab Groups, changing the setting at the right to Enabled, and relaunching the browser.
Chrome 83 was also to be the final step in automatically upgrading eligible users to DNS-over-HTTPS (DoH), a security feature that Google and other browser makers like Mozilla have been implementing, each in their own way.
The DNS (Domain Name Service) requests from users whose DNS provider offers the defensive feature of transmitting that traffic over encrypted connections (hence, HTTPS) is to gradually roll out to all users during Chrome 83’s lifecycle. The list of DNS providers that have DoH capability is relatively short, so not all Chrome users will get this. (The current list of providers can be found here, and includes names such as Cloudflare, Comcast, Google and OpenDNS.)
In a Tuesday post to the Chromium blog, Kenji Baheux, product manager laid out Google’s thinking on DoH and explained why it chose its approach. It’s well worth reading.
IT admins can disable DoH with the DnsOverHttpsMode group policy or in the Google Admin Console.
But wait, there’s more (privacy and security)
Not only has Google revamped the Privacy and security section’s UI (user interface) within Settings, but the company has loaded Chrome 83 with a slew of new security and privacy features.
Note: As with so much else Google does in Chrome, some users will see these changes before others as the firm ladles out the tools piecemeal to a gradually expanding set. Impatient users can prematurely turn on some of the still-missing through the chrome://flags options page.
Google has started what sounded like a long-term project with Chrome 83 by offering what it calls Enhanced Safe Browsing Protection. This was billed as a build atop Safe Browsing – the 13-year-old blocklist and associated API – that began by warning users when they were headed to what was probably a phishing website and has expanded to cover, among other things, to-be-downloaded files.
The primary difference in Enhanced is that the new, more advanced feature would not anonymize the incoming data, in effect linking an individual to the specific sites visited or even attempted to access. “If you are signed in to Chrome, this data is temporarily linked to your Google Account,” said a quartet of engineers on the Safe Browsing team.
While that may set off bells in the minds of privacy advocates, Google argued that it’s necessary for a next-step in protection. “We do this so that when an attack is detected against your browser or account, Safe Browsing can tailor its protections to your situation. In this way, we can provide the most precise protection without unnecessary warnings,” wrote Nathan Parker, Varun Khaneja, Eric Mill and Kiran C Nair.
Enhanced Safe Browsing Protection will be slowly deployed to Chrome 83 users, after which it will appear as an “Enhanced protection” option under Safe Browsing in the Privacy and security section.
The feature will gradually expand in what defenses it offers, the four engineers said. “We’ll be adding even more protections…, including tailored warnings for phishing sites and file downloads and cross-product alerts.”
Also on the books will be Safety check, actually a small set of security exams including one that scans the browser for blacklisted malicious extensions. The best in the bunch, though, does a Mozilla Lockwise-like look at the user’s passwords, then flags accounts that had previously been involved in known data breaches. The check is supposed to show in the Privacy and security section of the browser’s settings.
Other privacy additions will include a by-default blocking of all third-party cookies when browsing in Chrome’s Incognito (aka privacy) mode, a move reminiscent of Mozilla’s auto-blocking of Firefox’s private browsing mode five years ago.
Elsewhere in the browser, Chrome users can now manage individual site cookies as well as individual cookies within a website. Options let users block all third-party cookies, block all cookies on just some – or all – sites, and block some of the cookies on some sites. Management is so granular, however, that it’s unlikely that many will take advantage of the new control.
Google’s AbdelKarim Mardini, a senior product manager, described these security and privacy changes and others in a long post to the Chrome blog, a rare instance of the Mountain View company outlining the new simultaneously with an upgrade’s launch.
Chrome’s next upgrade, to version 84, will release on July 14.
Chrome 81
Google last week released the postponed-by-three-weeks Chrome 81, patching 32 vulnerabilities – plus one more on April 15 – and pledging to roll out a tab grouping feature to all users before the next upgrade lands in mid-May.
The California search firm paid at least $25,500 in bug bounties to researchers who reported some of the vulnerabilities. Three were tagged as “High,” the second-most serious in Google’s four-step threat ranking, and one – patched with build 81.0.4044.113 on Wednesday – was pegged “Critical,” the rare top-most rating. The latter, as well as two of the High trio, were submitted by engineers at Qihoo 360, a Chinese security software developer.
Chrome updates in the background, so most users can finish the refresh by relaunching the browser. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab shows that the browser has been updated or displays the download process before presenting a “Relaunch” button. Those who are new to Chrome can download version 81 for Windows, macOS and Linux here._
Google updates Chrome every six to eight weeks. It last upgraded the browser on Feb. 4.
Note: Google suspended Chrome releases in mid-March because of the COVID-19 pandemic and related disruptions, notably orders from companies, including Google, that sent home many employees to work remotely. Chrome 81 was originally slated to launch March 16 but was postponed three weeks. That pause, said Google, necessitated skipping version 82 and resuming upgrade numbering with Chrome 83, now set to release on May 19.
Tabs now form groups
The most prominent addition to Chrome 81, Tab Groups, is likely still invisible to most users. It was to Computerworld staffers running the browser.
Tab Groups, which has been under construction for months, essentially does what it says: Users organize tabs in the bar atop the browser by lumping together several, each lump designated by color and name, adding new tabs and removing existing ones.
The feature was to debut in February’s Chrome 80, and may have in a small number of instances worldwide. It wasn’t on Computerworld‘s numerous copies running under Windows 10 and macOS. Now, Google said, Tab Groups will roll out in Chrome 81, although it may not be immediately available by default.
“This will be rolled out widely to Mac, Windows, and Linux users throughout Chrome 81,” Google said in these release notes, under the section title of “Introduction of tab groups for remaining users.”
The impatient can manually engage Tab Groups by entering chrome://flags in the address bar, searching for Tab Groups, changing the setting at the right to Enabled, and relaunching the browser.
Tab Groups is easy to use: Right-clicking tabs now offers menu items to assign tabs to new or existing groups, or remove tabs from those groups. Other actions let users name each group and/or select a color, which boxes the name and borders the tabs of that group; ungroup the tabs; or close all tabs in the group.
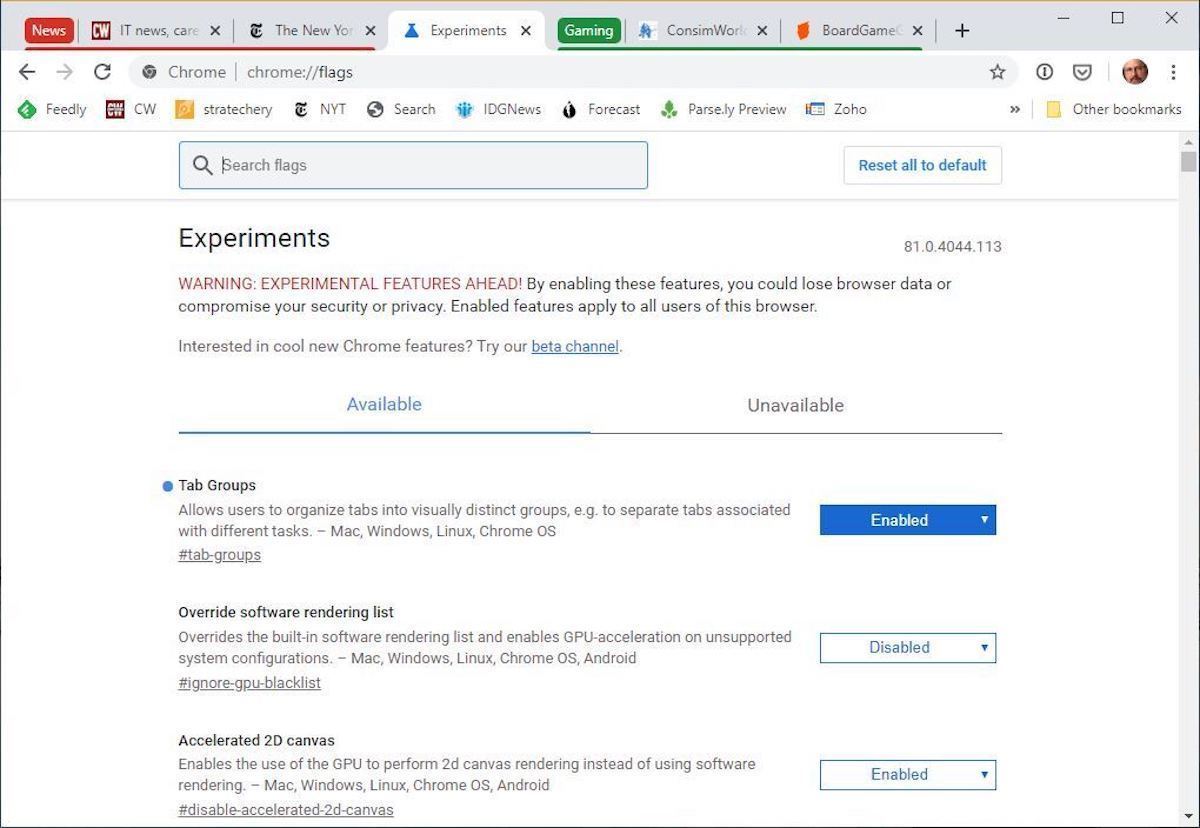
After enabling Tab Groups in the chrome://flags options pane, the Chrome user can create groups, as shown here by the red-tinted News group on the left and the Gaming group in green on the right.
Chrome 81’s tab functionality will be most useful to those who regularly wrangle a large number of tabs each session. Segregating tabs into collections brings some organization to what otherwise would likely be a randomized mess. Tab Groups’ simplicity is its best characteristic, since it’s more likely the feature will be adopted into browser workflow.
But it’s hardly a compelling reason to stick with Chrome or take it up, as some have argued. It lacks at least one crucial tool – a way to save groups, either singly or collectively, for later recall – and can be mimicked, even surpassed, by add-ons, such as Simple Tab Groups for Mozilla’s Firefox. (Firefox had a tab grouping feature at one point – known as Panorama – but Mozilla scrubbed it from the browser in 2016 because it was used by so few.)
Browser rollbacks are now a thing
Many bits of Chrome 81 that are notable are not because they’re there but because they aren’t. If that’s confusing, join the club.
Google had planned for several things to happen in Chrome 81, in particular protocols that were to be dropped or skills it was to surrender or security moves it was supposed to take. A number of them, though, were canceled, at least for this version, presumably to reappear in a future upgrade.
FTP’s back! Although Google said months ago that it would remove support for FTP (File Transfer Protocol) – an early Internet system for file transfer – in Chrome 81, and apparently did, it soon restored support. In an April 9 message on the Chromium bug tracker, a Google engineer wrote, “In light of the current crisis, we are going to ‘undeprecate’ FTP on the Chrome stable channel, i.e. FTP will start working again.” FTP will be put on the chopping block “once people are in a better position to deal with potential outages and migrations.”
TLS 1.0 and 1.1 not departing this mortal coil yet. As Computerworld noted previously, browser makers, Google included, issued reprieves for TLS (Transport Layer Security) 1.0 and 1.1, encryption protocols that were to be dropped in March.
Support for TLS 1.0 and TLS 1.1 will now be removed from Chrome 84, the upgrade scheduled to launch July 14.
SameSite enforcement put off. With Chrome 80, the version Google began distributing in early February, the browser was to begin enforcing SameSite, the standard pushed by Google, Microsoft and Mozilla designed to give web developers a way to control which cookies can be sent by a browser and under what conditions. Cookies distributed from a third-party source – not by the site the user was at, in other words – had to be correctly set and accessed only over secure connections.
The SameSite enforcement was to roll out slowly, as most Chrome changes do, beginning around mid-February when small numbers of users would see their browsers take action. Enforcement was to expand to more Chrome users over time.
Now, that has all been reversed.
In an April 3 post to the Chromium blog (three days before Chrome 81 released), Justin Schuh, the director of Chrome engineering, said that “in light of the extraordinary global circumstances due to COVID-19, we are temporarily rolling back the enforcement of SameSite cookie labeling, starting today.”
Schuh said Google didn’t want to chance destabilizing “essential services” rendered through the websites of banks, grocery stores, government agencies and healthcare organizations. Google will resume enforcement down the road, perhaps over the summer, Schuh added.
Chrome’s next upgrade, to version 83 – remember, Chrome 82 won’t exist – is scheduled to debut on May 19.

Chrome 80
Google this week released Chrome 80, beginning a promised process of locking down cookies and at the same time patching 56 vulnerabilities.
The California company paid at least $48,000 in bug bounties to researchers who reported some of the vulnerabilities. Ten were tagged as “High,” the second-most serious in Google’s four-step threat ranking. Half of those 10 were submitted by engineers of Google’s own Project Zero team.
Chrome updates in the background, so most users can simply relaunch the browser to finish the upgrade. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab shows that the browser has been updated or displays the download process before presenting a “Relaunch” button. Those who are new to Chrome can download the latest for Windows, macOS and Linux here.
Google updates Chrome every six to eight weeks. It last upgraded the browser on Dec. 10, 2019.
Enforcement of cookie-control starts now
Last year, Google said it would clamp down on cookies – the small bits of code websites rely on to, among other things, identify individual users – using the SameSite standard. SameSite, which has also been pushed by Mozilla and Microsoft, was designed to give web developers a way to control which cookies can be sent by a browser and under what conditions.
With Chrome 80, Google will begin enforcing SameSite, said Barb Smith, a Google executive, in a Feb. 4 post to the Chromium blog. Cookies distributed from a third-party source – in other words, not by the site the user is at – must be correctly set and accessed only over secure connections.
“Enforcement of the new cookie classification system in Chrome 80 will begin later in February with a small population of users, gradually increasing over time,” Smith wrote. Google frequently rolls out new features and other changes in stages, letting it verify that things worked as expected before expanding the pool of users. The company has set the week of Feb. 17 as the opening switch-on-SameSite salvo.
Also, as of Chrome 80, cookies without a SameSite definition will be considered as first-party only by default; third-party cookies – say, those from an external ad distributor tracking users as they wander the web – won’t be sent.
It’s complicated – for users, even IT admins, if not for developers – as this Google video demonstrates. But the result will likely be an aggressive push by Google, using the club of Chrome’s dominance, to motivate site makers and other cookie distributors to get behind the SameSite standard.
SameSite is not Google’s answer to the increasing anti-tracking positions being staked out by rivals such as Mozilla and Microsoft. Google has emphasized SameSite’s security prowess – preventing cross-site request forgery (CSRF) attacks, for instance – not any privacy benefits.
That’s no surprise.
No more notification nagging? That would be great
Chrome 80 also implemented the quieter notifications that Google pledged last month.
Rather than let sites place pop-ups on the page requesting permission to send notifications, Chrome 80 features an alarm bell icon with a strike-through near the right edge of the address bar. The first time Chrome presents the quiet UI, an in-browser dialog, which can be dismissed, will explain the feature.
Users will be able to engage the new notification UI manually using an option in Settings > Advanced > Privacy and security > Site Settings > Notifications. Toggling the “Use quieter messaging (blocks notification prompts from interrupting you)” switch turns on the pop-up blocker. Google has said it would also automatically enable the quieter UI for some. Those who “repeatedly deny” the notification requests will be auto-enrolled. Google will automatically silence some sites as well.
Not all users will see the less-intrusive notification requests immediately; although Google promised that Chrome 80 would launch the feature, Computerworld‘s copies of the browser did not yet show the new UI.
Tab groups supposed to begin to show
Tab groups are also supposed to debut in Chrome 80, but that, too, was not yet enabled by default on Computerworld‘s numerous copies running under Windows 10 and macOS. (The option to turn it on is behind chrome://flags: Search for Tab Groups, change the setting at the right to Enabled, and relaunch the browser.)
Last month, Google said that the feature – which does what it sounds like it does, organizes tabs by lumping together several, each lump designated by color and name – should begin rolling out to users with Chrome 80 but finish that process with March’s Chrome 81.
When it does appear – or after the browser’s owner manually enables it – users can right-click tabs and choose new menu items to create groups, assign tabs to them or remove tabs from those groups.
Enterprise-only
Other additions to Chrome 80 were enterprise-centric as Google continued to enhance the browser’s in-business skills, even more important of late as Microsoft introduced the Chromium-based Edge last month as an alternative.
Enterprise IT admins can enable or disable each type of synchronized data, ranging from History and Themes to Open Tabs and Passwords (just as individuals can do manually in Settings > Manage Sync.), using the newly-documented SyncTypesListDisabled group policy.
More management in Chrome 80 allows for a full blockade on employees trying to install external add-ons. Administrators can call on the BlockExternalExtensions policy to stop the practice. (Note: this does not block kiosk apps or extensions installed by policy.)
Chrome’s next upgrade, to version 81, is scheduled to ship on March 17, 2020.
Chrome 79
Google this week launched Chrome 79, touting the browser’s warnings when a site password may have been divulged and patching 51 vulnerabilities.
The California company paid $80,000 in bug bounties to researchers who reported some of the vulnerabilities. Two were ranked “Critical,” Google’s top-most rating, and eight were tagged “High,” the next level down in the four-step ordering. One report of a critical vulnerability was submitted by engineers at Tencent Keen Security Lab, a subsidiary of People’s Republic of China-based Tencent; Google awarded the researchers $20,000. The other bug alert? That one came from inside the house, reported by Sergei Glazunov of Google Project Zero.
Chrome updates in the background, so most users can just relaunch the browser to finish the upgrade to the latest version. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab shows that the browser has been updated or displays the download process before presenting a “Relaunch” button. Those who are new to Chrome can download the latest for Windows, macOS and Linux here.
Google updates Chrome every six to eight weeks. It last upgraded the browser Oct. 22.
Your password is kaput!
Google baked the functionality of its web-based Password Checker into Chrome 79 so that when the feature is enabled, the browser will alert its user if an entered password has been revealed by a prior data breach.
The online service, which examined the username-password combinations stored in Chrome’s password manager and reported back the authentication pairings that have been exposed in publicly-known data breaches, went live in early October. (The web service remains available.)
With Password Checker, Chrome will pop up a warning when a username + password combination has been exposed by a hack. Just as when Computerworld spot-tested the checker two months ago, an alert did not always appear when it was supposed to. One site whose password had been reported in a breach failed to display a warning, while other sites – some relying on the same username + password – did offer an on-screen warning.
The alert contains a Check passwords button that, when tapped, opens the status of all saved passwords, showing those that have been disclosed and giving the user a way to change the password.
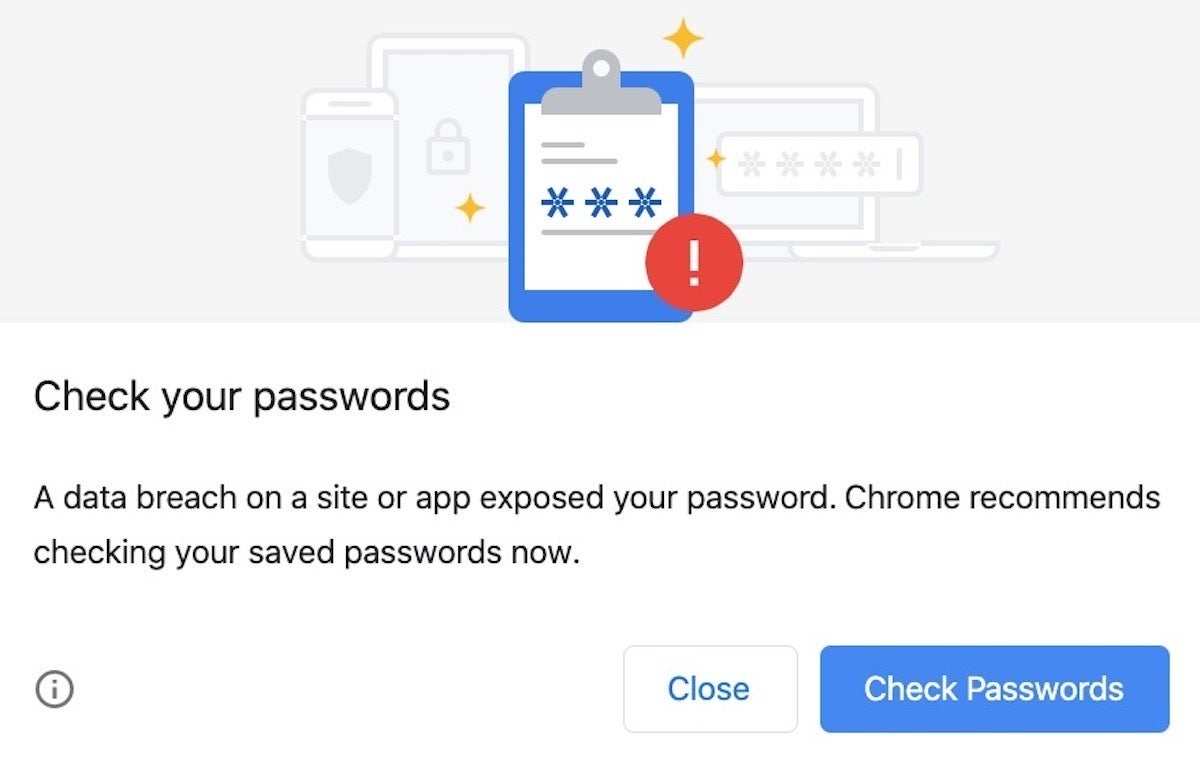
This pop-up should appear when a Chrome 79 user types in a password that Google suspects has been divulged by hackers.
Not everyone will have the new password notifier immediately, Google said. “We’re gradually rolling this out for everyone signed into Chrome as a part of our Safe Browsing protections,” wrote AbdelKarim Mardini, a senior product manager, in a Dec. 10 post to a company blog.
(To check whether it’s available to you, open Settings and click on People > Sync and Google services. If it’s available, it will be under the Other Google services section as Warn you if passwords are exposed in a data breach. Slide the toggle to the right if necessary, to enable the feature.)
Fighting phishers
Also new to Chrome 79 are changes to the browser’s long-in-place anti-phishing safeguards.
Safe Browsing, a Google-crafted technology, warns when a user steers toward a site that may contain malicious content. (The term is also applied to the API Google makes available to other browser builders; for instance, Mozilla relies on the Safe Browsing API to warn Firefox users about dangerous websites.)
The list of potentially-malevolent sites refreshes every 30 minutes, Google said. But that’s often not frequently enough. “Some phishing sites slip through that 30-minute window, either by quickly switching domains or by hiding from our crawlers,” wrote Google’s Mardini. Now Google will compare impending destination URLs against its list in real time. To start, Mardini added, the real-time lookups will be enabled for everyone with Chrome’s Make searches and browsing better enabled. (That option’s toggle can be found at Settings > Advanced > Synch and Google services > Other Google services.)
Chrome 79 also alters a 2017 function that warned users when they entered their Google Account (that’s what one uses to, for example, sync copies of Chrome or access Gmail) at a suspected phishing site.
(The feature stems from the concern that users can be tricked into divulging their Google Account credentials by a sophisticated – or unsophisticated, for that matter – phishing email with a link to a fraudulent site. Such emails often claim to be from Google, telling the user they need to log in to, say, retrieve a special offer or maintain their account.)
Prior to Chrome 79, only users who have signed into Chrome and enabled synchronization were alerted. “Now, we’ll be protecting your Google Account password when you sign in to Chrome, even if Sync is not enabled,” said Mardini. Atop that, the feature also warns if any password saved to Chrome is entered at a site thought to host phishing attacks.
Odds, ends and enterprise
Other debuts in Chrome 79 will affect users generally, and in some cases, enterprise users most of all.
A long-in-the-making feature that allows users to search Google Drive content from the Chrome address bar finally wrapped up and is being switched on in stages this month. (Google began testing this Chrome-Google Drive integration for G Suite Business, Enterprise, and Enterprise for Education subscribers in March.)
This will start rolling out to G Suite users starting Dec. 16, when Google will enable such searching by default. G Suite administrators can control the feature from their consoles.
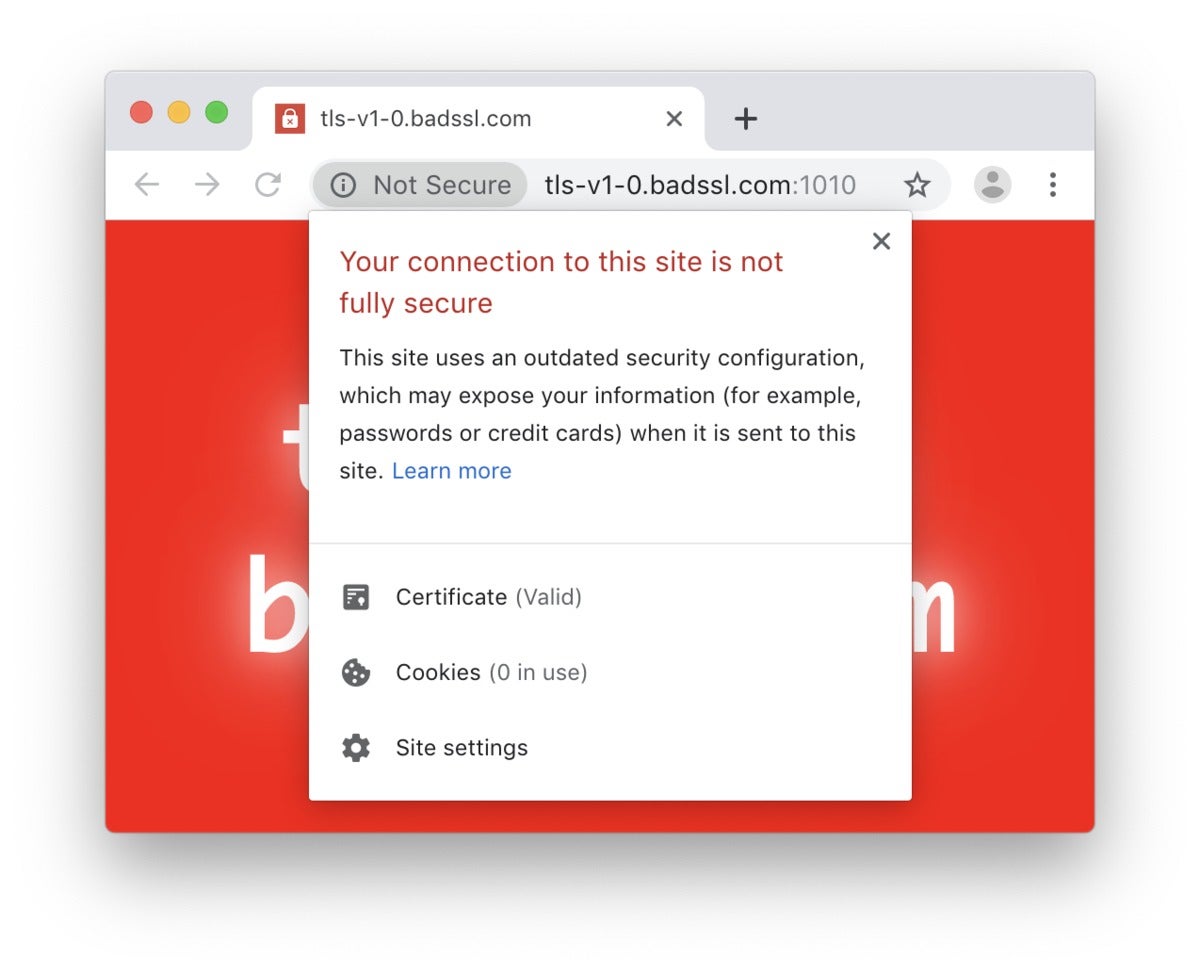
As of Jan. 13, 2020, Chrome 79 will put this in front of users when they connect to a site which encrypts traffic with the outdated TLS 1.0 or 1.1 standards.
(Users likely hope Google actually follows through on the Drive integration this time; at the launch of Chrome 78 in late October, the company said the feature would be “rolling out in the coming weeks.” Not in Chrome 78, though.)
Chrome 79 also includes a warning when users connect to a site that encrypts traffic with the outdated TLS (Transport Layer Security) 1.0 and 1.1. That warning will be switched on starting Jan. 13, 2020, Google has said. Two Chrome versions later (Chrome 81), Google will begin blocking connections to sites that rely on TLS 1.0 or 1.1 with a full-page warning.
Chrome’s next upgrade, to version 80, is slated for release on Feb. 4, 2020.
Chrome 78
Google on Tuesday rolled out Chrome 78, the latest version of its world-dominant browser, that included patches for 37 security vulnerabilities, new customization options for the new tab page, and search integration with Google Drive.
The Mountain View, Calif. firm paid out $58,500 in bug bounties — up 41% over September’s Chrome 77 — to researchers who reported some of the flaws. Three were ranked “High,” the second-most-serious category in Google’s four-step ratings, but none was tagged as “Critical,” the topmost rating. Two of the three High-ranked vulnerabilities were submitted by Man Yue Mo of Semmle, a San Francisco security company, in return for $35,000 in reward money.
Chrome updates in the background, so most users only need to relaunch the browser to finish the upgrade. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab shows that the browser has been updated or displays the download process before presenting a “Relaunch” button. Those who are new to Chrome can download the latest for Windows, macOS and Linux from here.
Google updates Chrome every six to eight weeks. It last upgraded the browser September 10.
New new tab page options
Google continued to make progress in a slow process of, if not overhauling the new tab page, then at least upping the customization quotient.
Chrome 77 introduced backgrounds to the browser, giving users several image collections — landscapes, seascapes, geometric patterns and such — and letting them upload one of their own to fill in the previously plain new tab page. (The image is not like a skin, à la Firefox, but appears only on the new tab page.)
The newer Chrome 78 keeps that but also adds more options when the user flips some bits. After typing chrome://flags in the address bar and pressing Return or Enter, search for two settings:
- Chrome Colors menu
- NTP customization menu version 2
Set each to “Enabled” and relaunch Chrome 78.
In the lower right of the new tab page, click on the pencil icon to see and set the new options for colors and on-page shortcuts.
At some point, Google will switch this on for everyone, eliminating the need to set flags; it hasn’t said when, however.
Search Google Drive from Chrome’s address bar
A long-promised feature — comprehensive search of Google Drive — will also come to Chrome 78, even though it may not be immediately available.
“Rolling out in the coming weeks, users will be able to search for Google Drive files that they have access to from the address bar,” Google wrote in its accompanying Chrome-in-the-enterprise documentation. “Their input will search through both titles and document contents, and the most relevant documents based on their history will appear.”
There’s a big caveat: It’s available only to users of G Suite Business, G Suite Enterprise, or G Suite Enterprise for Education. “This behavior is on by default and can be controlled with the ‘Google Drive search suggestions’ setting in the G Suite admin console,” wrote Google.
Google, like other software makers, often distributes its work in stages, rolling out new features and functionality in waves so that if problems pop up, those issues don’t impact everyone.
Google also wrapped up work bringing Legacy Browser Support (LBS) into Chrome with version 78. Starting with Chrome 74, Google began deconstructing a long-available add-on and putting it inside Chrome. Configured by IT personnel, LBS automatically opens Internet Explorer 11 (IE11) when links clicked within Chrome lead to websites, web services or web apps requiring Microsoft’s browser or its ActiveX controls. Administrators can deploy the baked-in LBS support and manage it using group policies or Chrome Browser Cloud Management’s User Settings.
Tab hover, progress on passwords and, of course, who can forget dark mode?
Chrome 78 now puts text boxes at the pointer’s position when the user hangs it over any tab. Dubbed “tab hover cards,” the aides are particularly helpful when the browser’s tab bar is overloaded to the point where there’s no room for distinguishing labels.
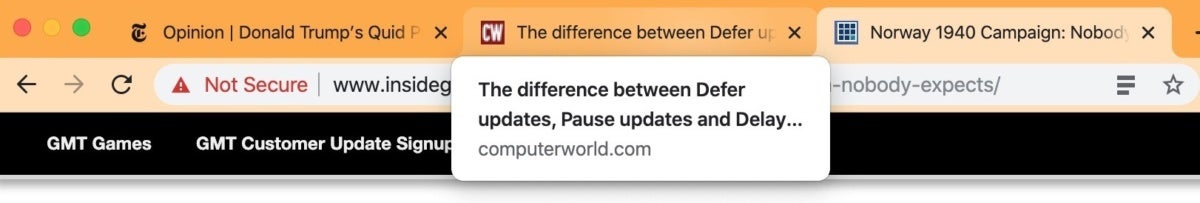
Tab hover cards pop up in Chrome 78 when the user suspends the pointer on an inactive tab (in this case, the middle of the three tabs). The box tells users what’s on that tab.
Elsewhere, Google moved closer to finalizing work on in-Chrome notification of exposed credentials. Originally intended to ship in this version (Chrome 78), the feature was pushed to Chrome 79 instead. Exactly how Chrome will notify users that a username/password pair has been revealed by a data breach has not been explained, but the tool has not been activated in Chrome 78. (Rival Mozilla just introduced password alerts in Firefox 70, the version that launched Tuesday.)
Even though it hasn’t been switched on by Google, users of Chrome 78 can do so: After accessing the chrome://flags page, find and set Password Leak Detection to “Enabled.” That will turn on the feature; to verify, users should call up Settings and look under Autofill > Passwords for the toggle marked “Check password safety.” If the toggle is in the on position, Chrome should tell you when it detects that a data breach-revealed password has been used.
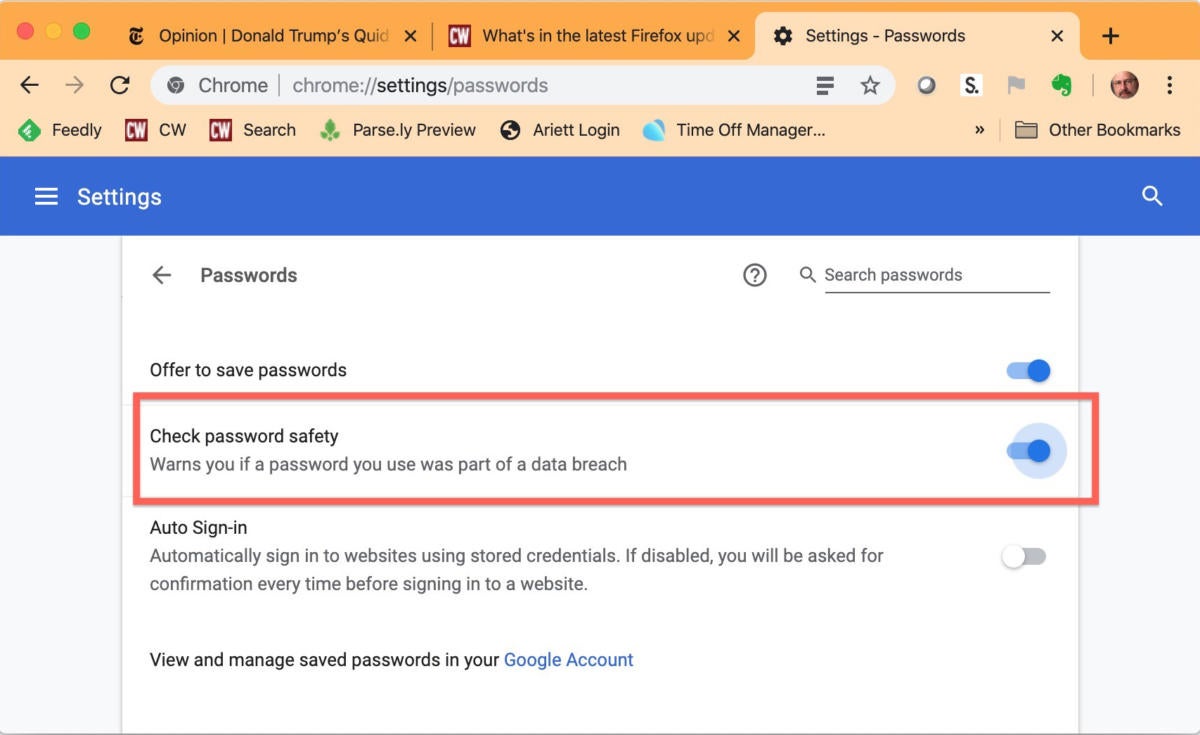
Chrome 78 is supposed to warn users when they type in passwords that have already been blown by a data breach, but the feature requires a trip into chrome://flags. The toggle shown here is how the alert system is controlled from then on.
(Computerworld‘s spot testing of leaked-password detection in Chrome 78 returned iffy results. Entering the password of one of the accounts that Google said had been compromised caused a pop-up to appear, carrying the message “A data breach on a site or app you use exposed your password. Chrome recommends checking your saved passwords now.” But other accounts that Google lumped in the same compromised category did not trigger the warning.)
Another not-quite-ready feature, dubbed “Force Dark Mode,” can be enabled by those who can’t get enough dark mode. Rather than wait for websites to support an operating system’s dark mode — the sudden fascination with flipping light to dark — Chrome will invert every website. From the chrome://flags page, locate Force Dark Mode for Web Contents and set it to Enabled. (This option has seven switched-on options; experiment to find a preference.) Relaunch the browser, and the web will be turned inside out, or at least go dark.
Chrome’s next upgrade, to version 79, is slated to debut on or about Dec. 10. That refresh will be the last one for 2019.
Chrome 77
Google last week updated Chrome to version 77, patching 52 security flaws, offering tab sharing and dumping an address bar indicator that the destination site was using more expensive digital certificates.
The company paid out $34,500 in bug bounties to the researchers who reported some of those vulnerabilities. Eight of the flaws were ranked “High,” the second-most-serious category in Google’s four-step ratings, and one was marked with rarely-used top-most “Critical.” The latter was submitted to Google by a security researcher with Qihoo 360, a company based in the People’s Republic of China that distributes a browser by the same name. (The Qihoo 360 browser relies on the same Chromium-developed technologies as does Chrome.)
Because Chrome updates in the background, most users just need to relaunch the browser to finish the upgrade. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab shows that the browser has been updated or displays the download process before presenting a “Relaunch” button. New to Chrome? Download the latest in versions for Windows, macOS and Linux from here.
Google updates Chrome every six to eight weeks. It last upgraded the browser July 30.
Not a lot of visible changes
Chrome 77 is another of those upgrades where visible changes are in short supply, where engineers advanced development tools, tweaked the browser’s underbelly or pushed through performance improvements.
The browser did ditch the Extended Validation (EV) certificate indicator in its address bar. EVs, unlike run-of-the-mill digital certificates, can be issued only by a select group of certificate authorities (CAs). To acquire one, a company must go through a complicated process that validates its legal identity as the site owner. And they’re more expensive.
The idea behind EVs was to give web users confidence that they were at their intended destination, that the site computerworld.com, for example, was owned by its legal proprietor, IDG, and not a fishy – and phishy – URL run by Crooks, Grifters & Scammers LLC and brimming with attack code. Browsers rewarded EV-secured sites with visual cues, notably the verified legal identity in the address bar and the color green.
Google has questioned EVs’ usefulness, though. In a document that announced the demise of EV in-browser notifications, Google said, “Users do not appear to make secure choices (such as not entering password or credit card information) when the UI is altered or removed, as would be necessary for EV UI to provide meaningful protection.”
The EV indicator was moved in Chrome 77 to the Page Info pop-up, which appears when the user clicks on the padlock icon at the far left of the address.
Share tabs, spice up the browser with a background
Also in Chrome 77, Google added a tab-sharing tool that doesn’t ask users to open the browser’s history pane. Instead, users can right-click on a tab and select the “Send to name of other device in the ensuing menu. Like any of Chrome’s sharing feature set, of course, this requires the user to be logged into Chrome on the other device(s).
Another new feature in Chrome 77 is a background customizer for the browser’s new tab page.
Although others noted that, while promised, the new page customizer was absent, Computerworld encountered it after installing Chrome on a Windows 10 Pro virtual machine, hinting that it may be part of the browser’s “out-of-box” experience but not yet enabled for existing copies. (For example, a copy running on macOS did not display the customizer.) Although Google frequently practices a staged roll-out of Chrome features – gradually enlarging the pool of users given the new shiny – the omission may mean it was bagged for some reason for current copies.
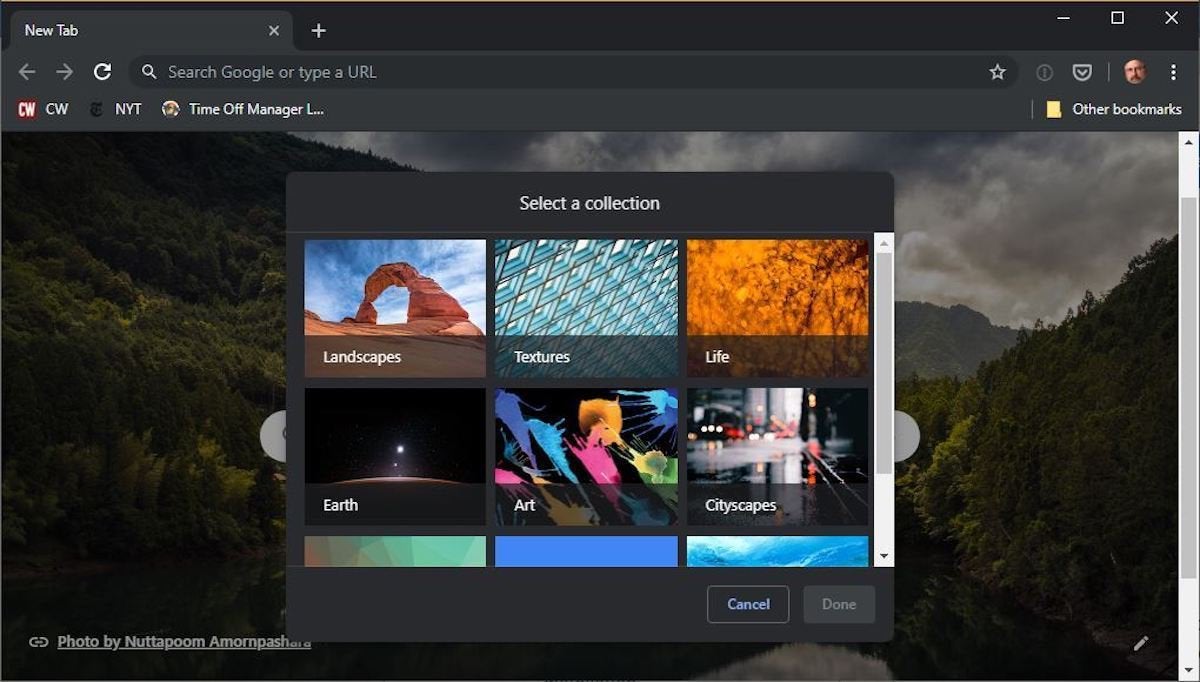
Chrome 77’s new tab page lets users – new users only, from what Computerworld found – choose from pre-selected backgrounds for the browser. These are now themes or skins; the backgrounds only appear on the new tab page.
Users can select from collections of provided images – landscapes, geometric patterns, solid colors and the like – or upload one of their own to use as a fill-in background on the new tab page. (The image is not akin to a Firefox theme or a skin of some kind, as it appears only on the new tab page.)
Elsewhere, Google added a new performance metric to site designers’ toolboxes. Dubbed “Largest Contentful Paint,” it measures the time it takes Chrome to put the main content of the page in front of users’ eyes.
“We’ve found that a more accurate way to measure when the main content of a page is loaded is to look at when the largest element was rendered,” reported Google engineer Philip Walton in an early-August post to the Web.Dev site, when he touted the new metric as better than earlier measurements such as load or First Contentful Paint. “The Largest Contentful Paint (LCP) API, available in Chrome 77, reports the render time of the largest content element visible in the viewport.”
Walton also pointed site designers to links with additional information on how to improve the LCP measurement.
Chrome’s next upgrade, version 78, should reach users on or about Oct. 22.
Chrome 76
Google this week updated Chrome to version 76, patching 43 security flaws and making good on a promise to switch off Flash by default.
The company paid out $28,000 — more than three times the last cycle — in bug bounties to a half dozen researchers who reported a few of those vulnerabilities. Five of the flaws were ranked “High,” the second-most-serious category in Google’s four-step ratings, including one that paid $10,000 to its discoverer and another that garnered $6,000. None were rated “Critical,” the topmost threat.
Because Chrome updates in the background, most users only need to relaunch the browser to finish the upgrade. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab shows that the browser has been updated or displays the download process before presenting a “Relaunch” button. New to Chrome? Download the latest in versions for Windows, macOS and Linux from here.
Google updates Chrome every six to eight weeks. It last upgraded the browser on June 4.
Last anti-Flash step before Chrome nixes it altogether
With the debut of version 76, the browser disabled Flash by default, the state Chrome will remain in until all support is yanked in late 2020.
Sites requiring the plug-in will show the “missing puzzle piece” symbol and the message “Adobe Flash Player is blocked.” Users will not be able to run Flash — at all — without going into Settings. After re-enabling Flash at Settings > Advanced > Privacy and security > Site Settings > Flash > Ask First (that last is done by toggling the switch from Block sites from running Flash (recommended)), Chrome users can again run Flash and display Flash content but only after authorization through a click.
Note: IT-set group policies that manage Flash within Chrome were not affected by the version 76 change. You can still control Flash behavior using DefaultPluginsSetting, PluginsAllowedForUrls, and PluginsBlockedForUrls, Google said.
Chrome now leads the second-place browser, Mozilla’s Firefox, in deflecting Flash. (The only browser further along, Apple’s Safari, has been anti-Flash since 2010, when Cupertino told users to fetch Flash themselves.)
And Google came through with the “infobar” it had pledged previously. If the user manually switches Flash back on through Settings, the infobar appears, warning that the plug-in won’t be supported at all after December 2020. It also offers a link for more info on the ban.
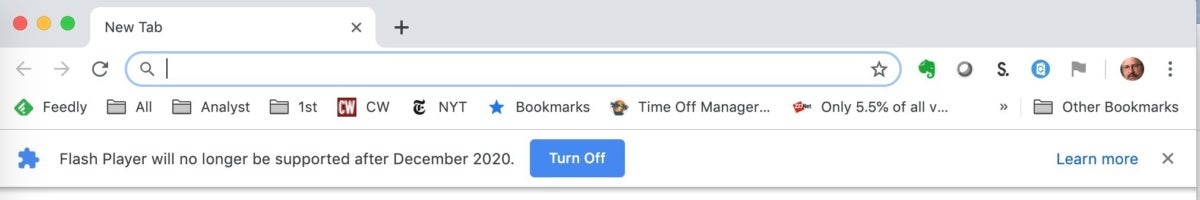
A new infobar pops up if the user resets Chrome 76 to run Flash Player, reminding them that the software won’t be supported at all after December 2020.
Currently, Chrome is to completely nix support for Flash as of version 87, which should debut in December 2020.
Chrome slams door on Incognito Mode loophole
Chrome 76 also closed a loophole that some websites were exploiting to shut down users trying to slip past article count meters.
Many sites with paywalls — the New York Times, for one — let visitors view x number of stories free of charge, a way to show the quality of the content behind the wall. After that count is reached, access is blocked. Browsers’ privacy modes, including Chrome’s Incognito Mode, were a way for readers to “reset” that meter and read more than the allotted number of articles.
Site publishers, of course, were onto the privacy mode ploy and in Chrome, monitored an API that was automatically disabled in Incognito Mode. If a call to the API returned an error — as it did when the API was off — the site assumed the visitor was in privacy mode and then blocked them from reading.
Two weeks ago, Google announced it was shutting down the ability of sites to sniff out Incognito Mode through the API. “Chrome will likewise work to remedy any other current or future means of Incognito Mode detection,” promised Barb Palser, a manager in Google’s news and web partnerships group, in a post to a company blog.
She also had recommendations for site publishers who had used the API to detect story count scofflaws. “Sites that wish to deter meter circumvention have options such as reducing the number of free articles someone can view before logging in, requiring free registration to view any content or hardening their paywalls,” Palser wrote. “Other sites offer more generous meters as a way to develop affinity among potential subscribers, recognizing some people will always look for workarounds.”
Site publishers could be excused for breezing by Palser’s unsolicited advice, seeing as how Google’s business model is the antithesis of most sites’.
PWA isn’t the sound you make when you spit
As another part of its push to boost Progressive Web Apps (PWAs), the platform-independent apps that behave much like standard desktop applications, Chrome 76 simplifies their installation.
If the distributing website meets the PWA install criteria, Chrome now displays a small icon at the right edge of the address bar; clicking that icon initiates the PWA installation process. By bringing PWA availability to the forefront, Google hopes to raise awareness of the standard.
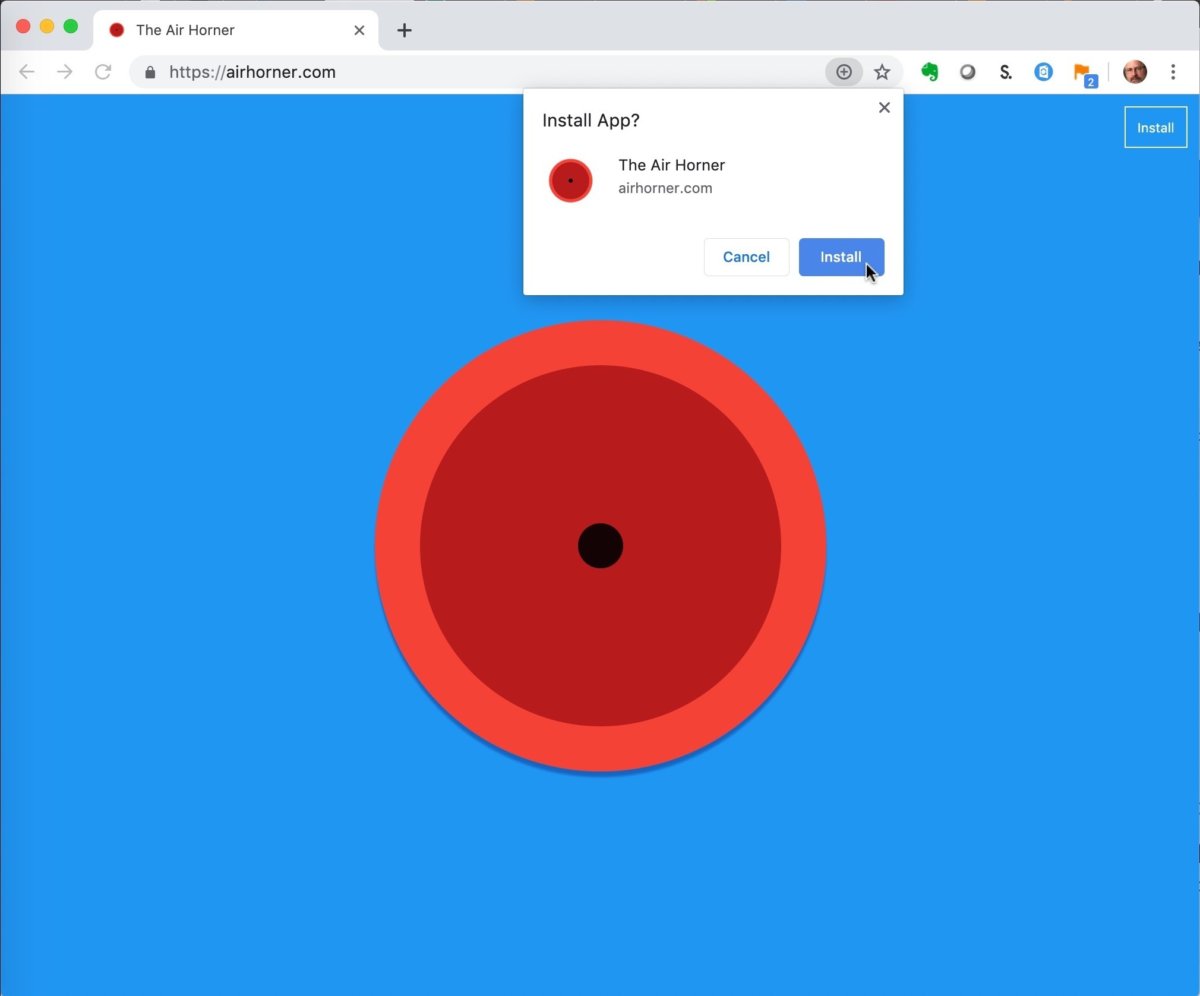
Chrome 76 now has PWA (Progressive Web App) awareness. A small icon at the right end of the address bar — it vaguely resembles a crosshair — launches the installation process for any PWA, assuming the hosting site meets Google’s criteria.
“On desktop, there’s typically no indication to a user that a Progressive Web App is installable, and if it is, the install flow is hidden within the three-dot menu,” wrote Pete LePage, a Google developer advocate, in a June document. “We’re making it easier for users to install Progressive Web Apps on the desktop by adding an install button to the address bar.”
(Not surprisingly, Chrome is a huge booster of PWA; Google coined the term.)
For enterprise eyes only
A few of Chrome 76’s additions and improvements are only for organizations that manage the browser.
As of this version, private-hosted Chrome add-ons — in other words, those not in the Chrome Web Store e-market — must be packaged with the CRX3 format. (The prior format, CRX2, used the SHA1 cryptographic hash function to secure extension updates; CRX2’s SHA1, however, can technically be broken, potentially giving attackers who intercept an over-the-Internet update a way to inject malicious code into the add-on refresh.)
“If your organization is force-installing privately hosted extensions or third-party extensions hosted outside of the Chrome Web Store that are packaged in CRX2 format, the extensions will stop updating in Chrome 76 and new installations of the extension will fail,” Google warned.
Chrome 76 also nulls the ability of IT staffs to use group policies to opt out of the site isolation technology Google introduced in 2007 with version 63. A year ago, Google switched on site isolation for the vast majority of Chrome users.
But because site isolation impacted Chrome’s performance, Google has let enterprises that manage the browser disable the defensive technology. That’s now ended.
“Starting with Chrome 76, we will remove the ability to opt out of site isolation on desktop using the SitePerProcess or IsolateOrigins policies,” Google announced. The change only applied to desktop Chrome, including Chrome OS; on Android, the comparable SitePerProcessAndroid and IsolateOriginsAndroid policies can continue to be used to turn off site isolation.
Google has also created a new Chrome policy list for enterprise IT. Notably, the list can be filtered by platform — macOS, Windows, Android and the like — as well as by Chrome version.
Chrome’s next upgrade, version 77, should reach users on or about Sept. 10.
Chrome 75
Google last week refreshed Chrome, upgrading it to version 75 by patching 42 security vulnerabilities and adding a basic “reader” view that rips ads and nonessential non-text content from pages.
The company paid out $9,000 – only a third the amount of the last cycle – in bug bounties to a handful of researchers who reported some of the vulnerabilities fixed in Chrome 75. Only two of the flaws were ranked “High,” the second-most-serious category in Google’s four-step rating system. None were rated “Critical,” the top-most threat level.
Because Chrome updates in the background, most users only need to relaunch the browser to finish the upgrade. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab shows that the browser has been updated or displays the download process before presenting a “Relaunch” button. New to Chrome? Download the latest in versions for Windows, macOS and Linux from here.
Google updates Chrome every six to eight weeks. It last upgraded the browser on April 23.
Distilling leaves 100-proof pages
Some Chrome upgrades pack a lot of changes, easily noticed changes like brand new features, significantly enhanced existing tools or major upsets to the user interface (UI).
Chrome 75 isn’t one of those.
There may be much for developers here – Google’s description of 75’s is loaded – but for users, particularly for individual users, there’s little to write home about.
Even the most noted feature wasn’t, well, noticeable, since it wasn’t switched on yet. But it is available, if in beta.
Dubbed “Distill Page” when enabled but labeled “Reader Mode” elsewhere, the feature is Chrome’s catch-up to rivals, which have long offered bare-bones pages sans ads, some or all images, and snazzy layouts, leaving text and little else. Most browsers slap “Reader something” on the feature; Firefox, for example, labels its iteration as “Reader View.”
While Google has monkeyed with something similar for years, it’s always hidden the feature, first behind a command-line trick in Windows and now, with Chrome 75, on the options page reached after entering chrome://flags in the address bar.
Find the listing Enable Reader Mode and change the setting at the right to “Enabled,” then click the “Relaunch Now” button at the lower right. Distill Page / Reader Mode is now on.
To use it, access the menu – click the vertical ellipsis at the far right of the line containing the address bar – and select “Distill Page.” Chrome repaints the page, dropping all but text and in-article images.
The effort is crude compared to other browsers. Where Firefox lets users toggle between reader and non-reader modes, Chrome’s can’t. Instead, the user must close the distilled page and then reopen the original. Nor, like Safari, will Chrome deposit a reduced page in a collection for later reading. But again, Chrome’s Distill Page is, according to Google, still in beta, the reason it’s behind the optional chrome://flags setting to begin with.
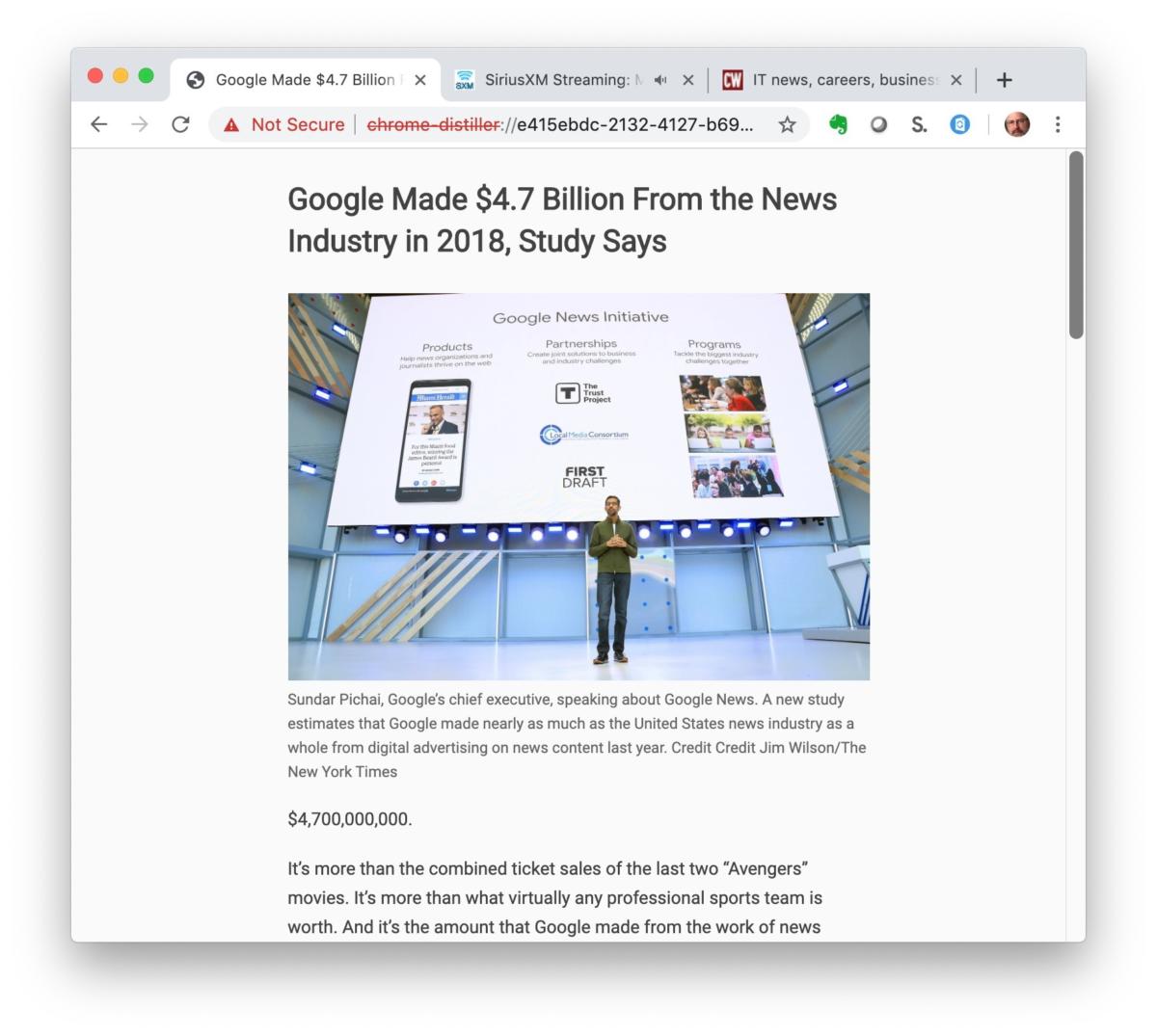
Chrome 75’s ‘Distill Page’ beta strips a webpage – in this case a news story – down to its text and inline images. Other browser have had this ‘reader mode’ feature for years.
Only for the enterprise
Some of Chrome’s latest additions and improvements are, as is often the case, only for organizations that manage the browser.
Top of the list for Chrome 75 is a roll-back process for enterprises that want to return to an older version of the browser. The functionality will be available only to customers using Windows’ group policies to manage Chrome and the furthest back in time the roll-back allows will be Chrome 72, which debuted in late January.
The most likely reason for wanting to roll back Chrome to an earlier version would be because the latest browser caused problems, perhaps a mission-critical app compatibility or workflow issue.
More information about rolling back Chrome and preserving user data can be found here.
Chrome’s next upgrade, version 76, should reach users on or about July 30.
Chrome 74
Google on Tuesday updated Chrome to version 74, an update that patched 39 security vulnerabilities and added support for websites that want to honor users’ requests to limit stomach-churning motion effects.
The search company paid out $26,837 in bug bounties to 17 researchers who reported some of the vulnerabilities quashed in Chrome 74. Five of the flaws were ranked “High,” the second-most-serious category in Google’s four-step rating system.
Because Chrome updates in the background, most users only need to relaunch the browser to complete the upgrade. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab shows that the browser has been updated or displays the download process before presenting a “Relaunch” button. New to Chrome? Download the latest in versions for Windows, macOS and Linux from here._
Google updates Chrome every six to seven weeks. It last upgraded the browser on March 12.
The world’s spinning’
With a rapid release tempo, browser development changes can seem minute, even microscopic, from one version to the next. This upgrade is like that. The public-facing feature touted by Google is one that many won’t notice. But those who do will appreciate it.
Chrome 74 now supports the prefers-reduced-motion media query by websites, an effort by site designers and developers to honor operating systems’ options to minimize unnecessary motion and animation. For example, macOS has a “Reduce motion” setting in the Display section of the Accessibility pane of System Preferences. If that was checked and Chrome 74 was directed to a site that uses the prefers-reduced-motion query, the browser would follow the site’s instructions – assuming they exist – to provide a motion-dampened alternative.
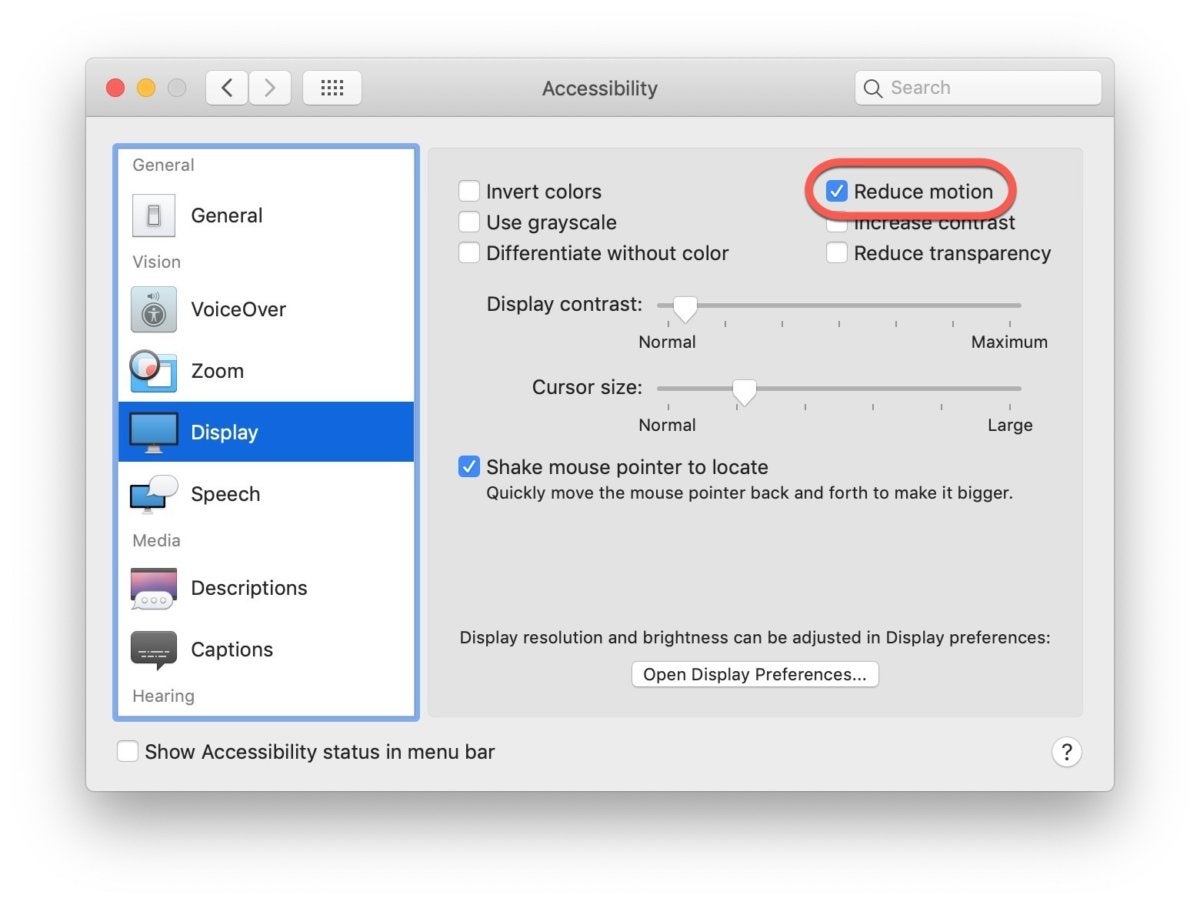
Chrome 74 supports websites which give users a less frenetic look when those users set ‘Reduce motion’ options like this one in macOS. People susceptible to visually induced motion sickness can become dizzy or even nauseated by on-page animations and attention-grabbing movements.
Some are affected by what’s called “visually induced motion sickness” – with symptoms mimicking traditional motion sickness, including dizziness and nausea – which is triggered by on-screen stimuli. The jumpy button that attracts the attention of most could make others ill.
Chrome 74 joined some of its rivals, including Apple’s Safari and Mozilla’s Firefox, in supporting the motion reduction. Microsoft’s browsers – Internet Explorer and Edge – and Opera Software’s namesake, Opera, do not.
Where’s dark mode, man?
When the Mac version of Chrome went dark (mode) in version 73 six weeks ago, Google said the fashionable feature would reach Windows at some unspecified future date.
A slew of users assumed it would be in Chrome 74 and started asking questions when they couldn’t find it. “I’ve gone back and forth, rebooted, did anything I could to make dark mode work with Windows 10 and it does not,” wrote lilalien Tuesday in a thread on the Chrome Help forum. Others chimed in with similar reports and questions, and a few got really hot over the issue. “What a joke this is – just get on with it already,” ranted one.
Google’s answer came courtesy of a Chrome community manager in the same thread. “I can confirm that we are rolling out this feature to a small number of Chrome M74 users now, and that it will become more widely available in the near future,” wrote Craig._His explanation was no real surprise, as Google often enables new features in stages. The practice is meant to give the company a chance to fix problems before everyone is afflicted.
Elsewhere, users posted workarounds to force Chrome to follow Windows’ lead and use dark mode:
- Right-click the Chrome shortcut icon on the desktop and select Properties
- In the Target field, add this to the end of the text: -force-dark-mode
- Click the OK button
- If Chrome is currently open, relaunch it.

Google is slowly rolling out ‘dark mode’ in Chrome 74 on Windows, but by editing the browser’s shortcut, users can see it immediately.
Enterprise only
Some of the changes to Chrome were solely for organizations that have adopted the browser.
Among the enterprise-only enhancements was the debut of baked-in Legacy Browser Support (LBS), a feature that (before Chrome 74) was available using a separate add-on from Google. LBS has now been integrated into the browser, making the extension unnecessary. And as a bonus, Google launched it an edition early; in March the company said it was shooting for in-browser LBS for Chrome 75.
Once configured by IT, LBS automatically opens Internet Explorer 11 (IE11) when links clicked within Chrome lead to websites, web services or web apps requiring Microsoft’s browser, or more likely, IE’s ActiveX controls or Java, neither of which Google’s browser supports.
More information about LBS, including setting policies to manage the browser switching, can be found on Google’s website.
Chrome’s next upgrade, version 75, should reach users on or about June 4.

Chrome 73
Google last week issued Chrome 73, an update that added support for desktop “Progressive Web Apps” on Macs and consolidated settings – both old and new – that let users opt out of Google’s services.
Chrome 73 also patched 60 vulnerabilities; security researchers who reported nine of them were paid a total of $13,500 in bug bounties. Other flaws’ rewards had not yet been calculated by Google.
Chrome updates in the background, so most users can just relaunch the browser to install the latest iteration. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download process before presenting a “Relaunch” button. Those new to Chrome can download version 73 in versions for Windows, macOS and Linux from this Google website.
Google updates Chrome every six to seven weeks. It last upgraded the browser Jan. 29.
PWA for Macs
Google added support for desktop “Progressive Web Apps,” or PWAs, for the Mac in this version, after Chrome 70 and Chrome 67 did the same for Windows and Chrome OS, respectively.
PWAs are web-based apps which have the look and feel of native-to-the-OS applications. Rather than run inside a Chrome frame, for example, they appear within the operating system’s standard windowing.
Google has pitched PWAs rather than Chrome-only apps – the latter were long available in Google’s e-store – since mid-2016 when the search giant announced it would phase out the apps.
Shifty settings
Google also said changes to Chrome’s settings that would shift some options to a new, more visible, section were “rolling out.”
The setting, labeled “Sync and Google Services,” will appear under the top People section and include a host of options, including “all of the settings related to data collected by Google in Chrome Browser,” according to Google’s release notes written for enterprises. “Many of these settings were previously in the Privacy section.”
Computerworld‘s check of numerous instances of Chrome on both Windows 10 and macOS showed that the change had not been implemented after the upgrade to version 73. That’s not unusual: Google often deploys a new feature in stages, a practice meant to give the company a chance to fix any problems before all users suffer.
New tools will also be made available to those who sign into a Google account for syncing browsers, including an enhanced spellchecker and more detailed reporting for safe browsing, the technology Google uses to warn users of potentially malicious sites.
Google did not give a reason why it reorganized the sync and services settings, but it may have been a response to the kerfuffle last year over Chrome 69. In that version, signing into any Google service automatically also signed the user into Chrome. Many objected, citing privacy issues; signing in here and having Chrome automatically log in there was unacceptable to them because they believed that once signed into Chrome, data escaped their control and headed toward Mountain View’s servers.
In the upgrade to Chrome 70, Google added an option for disabling the automatic sign-in.
For enterprise only
As is now standard, some of the changes to Chrome are only for businesses and other organizations that have adopted the browser.
Along with several new group polices that IT administrators can set for employees’ browsers, version 73 now displays an item on the More Tools menu telling users that Chrome is being managed. Clicking “Managed by your organization” takes users to information about Chrome management. (Previously, users had to type about:policy in the address bar to see if the browser was being maintained by IT.)
Elsewhere in Chrome, version 73 added a dark mode for macOS; when the latter is set to the darker shade, Chrome follows suit. Google said dark mode support would be added to Chrome on Windows at some later date.
Chrome’s next upgrade, version 74, should reach users on or about April 26.

Chrome 72
Google this week released Chrome 72, a refresh that includes no new notable user-facing features but does take a first step toward ending support for older web encryption protocols.
Chrome 72 also patches 58 vulnerabilities reported by security researchers, who were paid a total of $50,500 in bug bounties.
Chrome updates in the background, so most users can just relaunch the browser to install the latest iteration. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download process before presenting a “Relaunch” button. Those new to Chrome can download version 72 in versions for Windows, macOS and Linux from this Google website.
Google updates Chrome every six to seven weeks. It last upgraded the browser Dec. 4.
Dump TLS 1.0 and 1.1, Step 1
Last year, all of the major browser makers announced that their wares would drop support for the TLS (Transport Layer Security) 1.0 and 1.1 encryption protocols by early 2020.
TLS was the successor to the still-better-known SSL (Secure Socket Layer) encryption protocol; SSL and TLS secured data communications between browser and the destination server so that criminals could not read the traffic, and by doing so, spy on users or steal valuable information. Both TLS 1.0 and 1.1 – the former turned 20 this month – have been rendered obsolete by successors, TLS 1.2 and 1.3. All four browsers now support TLS 1.2, and Chrome and Firefox also support the enhanced TLS 1.3.
Most websites support TLS 1.2; almost 95%, according to Qualys’ latest survey._
Each browser maker set its own schedule for de-supporting TLS 1.0 and 1.1 last year. Google at the time said that Chrome 72 would start the process, and Chrome 81 would pull the plug. In a document spelling out changes to Chrome 72, Google said, “Removal is expected in Chrome 81 (early 2020),” confirming the plan remains on schedule. As of Chrome 81, the browser will not connect to websites supporting just TLS 1.0 and 1.1.
In Chrome 72, a warning displays in the Developer Tools view when the browser has been pointed at sites that only support TLS 1.0 and 1.1.
Strips out other stuff, too
Chrome 72 also drops other bits from the browser.
One is “HTTP-based Public Key Pinning,” aka HPKP, which Google explained was “intended to allow websites to send an HTTP header that pins one or more of the public keys present in the site’s certificate chain.”
HPKP is a security measure meant to combat fraudulent certificate usage by criminals. But Google said it had dangerous side effects and, by the way, was little used. “Although it provides security against certificate misissuance, it also creates risks of denial of service and hostile pinning,” Google argued.
Chrome began the process of getting out from under the FTP protocol, too, with version 72.
FTP, which stands for “File Transfer Protocol,” is a legacy protocol from the earliest days of the Internet, used for exactly its defined purpose: Moving files.
But it’s ancient. Noting that “when even the Linux kernel is migrating off FTP, it’s really time for us to move on,” Google said it’s time to remove support for the little-used protocol. A first step, Google decided, was to download non-directory listings, such as an image hosted at an FTP link, rather than rendering them within the browser itself. Chrome 72 debuted that behavior.
Google has not publicly disclosed when all support for FTP within Chrome will be yanked.
Chrome’s next upgrade, version 73, will reach users on or about March 12.

Chrome 71
Google this week boosted Chrome to version 71, the last refresh of 2018 and one that includes punitive measures against sites spewing what the search giant described as “abusive experiences.”
Chrome 71 also patched 43 security vulnerabilities reported by outside researchers, who were paid $59,000 in finders’ fees.
Chrome updates in the background, so users can typically just relaunch the browser to install the latest. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download process before presenting a “Relaunch” button. New-to-Chrome users can download it from this Google site for Windows, macOS or Linux.
The Mountain View, Calif. company updates Chrome every six to seven weeks. It last upgraded the browser on Oct. 16.
Slapping some sites with total ad embargo
A month ago, Google ran an ad-raid drill, telling Chrome users, “Starting in December 2018, Chrome 71 will remove all ads on the small number of sites with persistent abusive experiences.” (Google defines abusive experiences here.)
Removing all ads could, of course, easily put an advertising-dependent website on the poor farm. That’s the point. Through Chrome – which dominates the Web – Google has been shaping online to its taste, often using the browser as a bludgeon to punish sites or practices it feels are hostile to customers or noxious to itself.
Auto-play policies, meet Web Audio
Chrome 71 started the process of synchronizing the already-in-place auto-play rules in Chrome – which generally, though not always, block ads from blaring sound from a PC’s speakers as soon as a site renders – with the Web Audio API (application programming interface).
According to Google, the sync has not yet been enabled, but is tucked behind one of the option flags which can be set in the UI at chrome://flags.
At its most basic, the API can be used by site and app developers to add audio to their creations. Currently, only Chrome – via the Chromium open-source project, which feeds code to the production browser – supports Web Audio.
Chrome, like rival browsers, has been hammering against sites’ auto-playing audio because of user complaints that the blaring is annoying at best. Most of the auto-play instances have been initiated by advertisements, another reason people have become increasing fed up with the Web and its underpinnings. The move to make Web Audio follow Chrome’s standard auto-play practices can be seen as simply an expansion of a long-running battle.
Third-party code blocking delayed again for enterprise users
Google also patched 43 vulnerabilities in version 71, including 13 marked “High,” the second-most serious ranking in its four-step system. The company cut checks totaling $59,000 to researchers who reported 28 of the bugs.
In the enterprise edition of Chrome, a well-publicized decision this summer that the browser would soon block all third-party code injections has been put on indefinite hold. Billed as a stance on security and stability, the anti-injection mandate was, Google said in October, to go into effect by default with Chrome 71. Not so.
“Due to an issue with anti-virus file scanning, we’re delaying this change until we have a solution that better covers customers’ needs,” Google said in the v. 71 enterprise version release notes.
This move has been postponed more than once; it was to roll out for enterprise customers in Chrome 68 (July), then in Chrome 69 (September).
Chrome’s next upgrade, version 72, will reach users on or about Jan. 29, 2019.

Chrome 70
Google this week upgraded Chrome to version 70, following through on a promise made to disable automatic sign-in after users and privacy advocates complained about changes in the prior edition.
Chrome also sported patches for 23 security vulnerabilities as Google paid researchers $22,000 in bug bounties.
Chrome updates in the background, so in most cases users can simply relaunch the browser to install the latest version. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download-and-upgrade process before presenting a “Relaunch” button. New-to-Chrome users can download it from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks. It last upgraded the browser on September 4.
Auto log-on backtrack
As of Chrome 69, signing into any Google service automatically also signed the user into Chrome. For example, logging into one’s Gmail account also logged into one’s Google account when Chrome opened. (That was the case whether a user had accessed Gmail using Chrome or another browser, like Firefox.)
Because logging into a Google account allowed syncing of data — including bookmarks and passwords — between machines, and because some users did not want their data transiting Google’s servers — ever — they strongly objected to the new model.
When the blowback blew, Google said it would add an option to disable the automatic sign-in to Chrome 70. But it did not retreat from the position that such would be on by default.
Chrome 70 did insert the option into Settings panel, called up when the user clicks the vertical ellipsis at the upper right and chooses “Settings” from the menu. After clicking the “Advanced” button on the Settings panel, the user can toggle the slider under “Privacy and security” marked with the phrase “Allow Chrome sign-in.” A relaunch of Chrome will be necessary.
With the slider toggled to the off position — moved to the left — the user can sign into a Google service, like Gmail, without also signing into Chrome.
PWA and more anti-HTTP warnings
On Chrome running in Windows, Google added support for desktop “Progressive Web Apps,” or PWAs, following the same move on Chrome OS with that operating system’s version 67.
PWAs are, as the name implies, web-based apps which have the look and feel of native-to-the-OS applications. Rather than run inside a Chrome frame, for example, they appear within the operating system’s standard windowing. In Windows 10, a PWA operates like any other application, including installing to the Start menu.
Google has pitched PWAs rather than Chrome-only apps — long available in its e-store — since it announced two years ago that it would drop them from the browser and point them toward Chrome OS-only.
Google will add PWA support to the macOS and Linux editions of Chrome with version 72; that should ship around the middle of January.
Also new to Chrome 70 was another step in Google’s longtime effort to secure the user by forcing site owners to abandon HTTP and institute HTTPS instead. As per Google’s plan, Chrome 70 tags any HTTP site with an insecure icon — a small red triangle — and the text “Not secure” in the address bar as soon as the user interacts with any input field, such as a password field or one that requires credit card information.
More add-on lock-down
Earlier this month, Google made note of new ways it would lock down Chrome extensions — for years, the search giant has pointed to extensions as potential security nightmares — that included requiring developers to adopt two-factor authentication on their accounts (so criminals would have a tougher time hijacking those accounts, then feeding malicious add-ons to the Chrome Web Store) and giving users a way to limit the permissions an extension had been granted.
“Beginning in Chrome 70, users will have the choice to restrict extension host access to a custom list of sites, or to configure extensions to require a click to gain access to the current page,” wrote James Wagner, product manager for Chrome extensions, in an October 1 post to a company blog. “While host permissions have enabled thousands of powerful and creative extension use cases, they have also led to a broad range of misuse because they allow extensions to automatically read and change data on websites.”
A right-click on an add-on’s icon will bring up new options to, for instance, restrict the already-agreed permissions to just that page.
Computerworld tested the add-on management enhancement on both Windows and macOS, but neither version of Chrome 70 showed evidence of the new options. That wasn’t surprising: Google often enables a Chrome feature only after a week or more has passed, perhaps to make sure the updated browser is in most users’ hands.
Patches and certs
Google also patched 23 security vulnerabilities in version 70, including six marked “High,” the second-most serious ranking in its four-step system. The company cut checks worth $22,000 to researchers for reporting 15 of the bugs.
In another security-related move, Chrome 70 made the last move in a series that Google (and other browser makers) instituted against Symantec-granted SSL (Secure Socket Layer) certificates. Any certificate issued by Symantec should trigger a “Not secure” warning in the browser’s address bar, essentially telling the user not to trust that the website is legit.
This was to be the final step in a process outlined more than a year ago, after Google and Mozilla — the maker of Firefox — charged Symantec and its partners with improperly issuing certificates, violating rules set by the CA/Browser Forum, a standards groups whose members include browser makers and certificate authorities. Google and others declared that Symantec’s problems were endemic, and that the accumulated incidents were proof that it was untrustworthy in a critical way: that a website was what it claimed to be, not a fake set on stealing users’ money or credentials or data.
(Mozilla last week announced it was delaying a similar move on the part of Firefox, saying that “well over 1% of the top 1-million websites are still using a Symantec certificate that will be distrusted.” That, Mozilla decided, was too many for it to proceed.)
Computerworld used a list of sites that, as of late September, were still using a Symantec-issued certificate, and after spot-checking, found very few that had not switched in time for Chrome 70. Some took it to the wire, though, getting a new certificate just days ago.
(One example of a site that missed the memo: digg.com.)
Chrome’s next upgrade, version 71, is set to release December 4.
Chrome 69
A decade after Google launched the first iteration of Chrome, the company on September 4 updated the browser to version 69, touting a freshened user interface (UI), an enhanced password manager and a more informative address bar.
Google also patched 40 security vulnerabilities in the browser and paid bug bounties to researchers who reported the flaws.
Chrome updates in the background, so users can usually just relaunch the browser to install the latest version. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download-and-upgrade process before presenting a “Relaunch” button. New-to-Chrome users can download it from this Google site.
The Mountain View, Calif. company updates Chrome every six or seven weeks. It last upgraded the browser on July 24.
10 years after
Chrome debuted Sept. 2, 2008, putting an end to years of speculation that the search company would go head-to-head with Internet Explorer (Microsoft), Firefox (Mozilla) and Safari (Apple). Ten years later, after mercilessly pummeling the competition, Chrome is the browser pick for two-thirds of the world’s population that went online from a personal computer.
Saying that “our 10th birthday update is bigger than normal,” Google ticked off the top-of-list changes in version 69.
“Our newest update includes a refreshed design that lets you navigate the web faster (and) a completely revamped password manager,” Rahul Roy-Chowdhury, the executive who leads the Chrome and Chrome OS teams, wrote in a post to a company blog. “And Chrome’s search box (the ‘Omnibox’) gives you more information directly as you type, saving you even more time.”
First UI changes in two years
Chrome’s UI changes, the first in two years, focus on the top-of-window elements, such as the browser’s tabs. Those have changed from their earlier trapezoids for rectangles with slightly-rounded upper corners, and the active tab has been brightened to make it stand out more than before.
Chrome 69’s address bar – some at Google still call it by its oldest name, “Omnibox” – has also been rounded, replacing its flat left end with a curve. Even the icons in the new tab page representing frequently-visited sites have been altered; they’re much smaller and enclosed within small circles.
The overall effect is to steer Chrome toward a simpler, even more minimalist design that generally can’t overpower a page’s contents.
Passwords, please
Another improvement to Chrome 69 trumpeted by Google is its enhanced password manager.
“When it’s time to create a new password, Chrome will now generate one for you (so you’re not using your puppy’s name for all of your passwords anymore),” said Ellie Powers and Chris Beckmann, two Chrome project managers, in a post to a Google blog. The password manager will automatically fill in the username and password – whether the latter is generated by Chrome or by the user – with a single click in the site’s sign-on form.
Password creation has been long available from third-party password management apps such as LastPass – and the browser add-ons those apps rely on – but not within browsers themselves. Apple’s Safari, for instance, has this capability, thanks to ties to the operating system’s credential manager, but Microsoft’s Edge and Mozilla’s Firefox do not.
Score one for the Omnibox
“(The Omnibox) will now show you answers directly in the address bar without having to open a new tab,” said Powers and Beckmann.
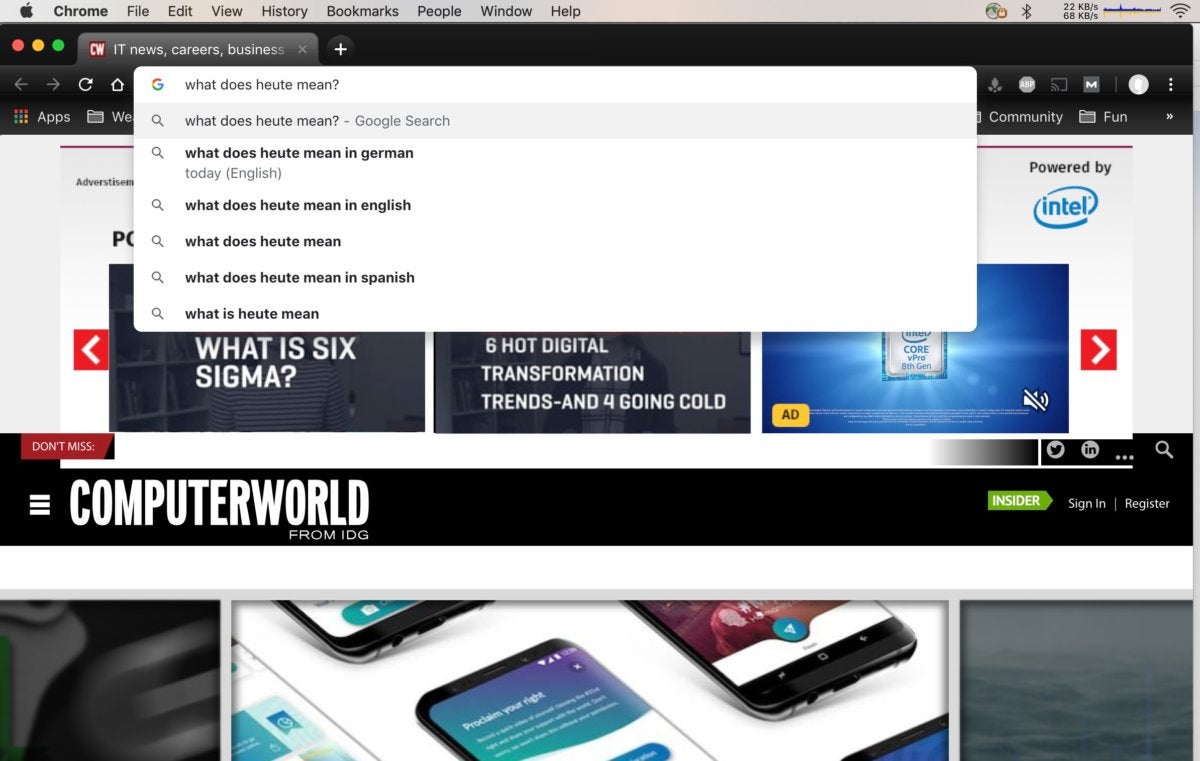
Chrome 69’s Omnibox now provides answers directly in the address bar.
The new functionality offers answers to some questions – what does heute mean in English, for instance, or the current weather in Boston – within the address bar, or Omnibox, itself, saving the time it would take to generate a search results list or display an answer on the browser page.
It was hit or miss in Computerworld‘s testing, with some systems demonstrating the feature, others not (perhaps because the feature has not yet been enabled on all copies of Chrome 69), and in-Omnibox answers not provided for all questions. Although Chrome’s Omnibox gave up the score of the Seattle Mariners’ most recent game – 5-2 over the Orioles – it could not do the same for the minor league Bees of Salt Lake City.
The Omnibox will also sniff out an open tab and switch to it if the search string matches part of the URL; alternately, the user can open the site in a new tab. (Computerworld wasn’t able to verify this feature on either a Mac or a Windows 10 system.)
But wait, there’s more!
Google also patched 40 security vulnerabilities in version 69, including seven marked as “High,” the second-most serious ranking in the company’s four-level system. The Mountain View, Calif. company cut checks totalling $31,500 to researchers for reporting 16 of the bugs.
In another security move, Google also removed the “Secure” label from the address bar when displaying sites using HTTPS encryption, as it had promised to do. With the next release, Chrome will mark all HTTP pages with “Not secure” when users enter any data.
Chrome’s next upgrade, version 70, will reach users the week of Oct. 14-20.

Chrome 68
Google on July 24 released Chrome 68 for Windows, macOS and Linux, patching 42 security flaws, adding new APIs for developers and marking sites relying on HTTP as “Not Secure.”
Chrome updates in the background, so users can usually just relaunch the browser to install the latest version. To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download-and-upgrade process before presenting a “Relaunch” button. New-to-Chrome users can download it from this Google site.
The Mountain View, Calif. company updates Chrome every six or seven weeks. It last upgraded the browser on May 27.
Turns on ‘Not Secure’ warning
The biggest change to Chrome with the debut of version 68 was the new warning labels set into the address bar. While sites whose traffic is encrypted – marked by the HTTPS at the beginning of the URL – will be marked as “Secure,” those transmitting data via the unencrypted HTTP will be tagged as “Not Secure.”
This campaign of Google’s to call out HTTP websites as unsafe began four years ago, with incremental steps toward that goal since. In January 2017, for example, Chrome 56 shamed pages that didn’t encrypt password or credit card form fields with the “Not secure” label.
This latest move will not be the last, Google has promised. In early September, with Chrome 69, the browser will remove the “Secure” tag from sites using HTTPS so that encrypted traffic is considered the default. Google’s 180-degree turn from browsers’ decades-long signage – marking secure HTTPS sites, usually with a padlock icon, to indicate encryption and a digital certificate – to labeling only those pages that are insecure, will wrap up this year. In October, with the launch of Chrome 70, the browser will tag HTTP pages with a red “Not Secure” marker when users enter any kind of data.
As usual, Google adds APIs and plugs security holes
Chrome 68 sports some behind-the-scenes newness as well, which is standard for the browser’s updates.
Google highlighted several new APIs (application programming interfaces) in notes to developers, including the Page Lifecycle API and the Payment Handler API.
The former API, Page Lifecycle, offers site and web app developers a way to restore a tab that, for performance reasons, had previously been “frozen” by the browser to conserve resources, including memory and processor load. When the user then returns to the tab, it can be resumed as if nothing had happened.
Payment Handler, on the other hand, lets web-based payment app makers tie into the already-available online checkout infrastructure built into Chrome.
Google also patched 42 security vulnerabilities in version 68, including five marked as “High,” the second-most serious ranking in the company’s four-step system. Google shelled out $21,500 to researchers for reporting 19 of the bugs, with several bounties still to be decided.
Chrome’s next upgrade, version 69, will start reaching users the week of Sept. 2-8.
Chrome 66
Google on April 17 released Chrome 66 for Windows, macOS and Linux, patching 62 vulnerabilities, banning older site certificates issued by security giant Symantec, and refusing to run auto-play content unless the volume was muted.
Chrome updates in the background, so users only need relaunch the browser to install the latest version. (To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download-and-upgrade process before presenting a “Relaunch” button.) Those new to Chrome can download it from this Google site.
The Mountain View, Calif. company updates Chrome every six or seven weeks. It last upgraded the browser on March 6.
While some Chrome upgrades, like version 65, are almost entirely about under-the-hood changes, others feature oh-so-obvious new functionality. Still other upgrades boast a mix-a-lot blend of the two. Chrome 66 is definitely in that third camp.
The most visible Chrome 66 enhancement is the arrival of Google’s long-discussed ban on auto-play content that dared blare sound from the speakers. Chrome’s blockade of such content was first announced last year, when version 64 was to debut the feature. But the mandate did not go live in January, as expected, nor in March with Chrome 65. The ban has finally been made the default in Chrome 66.
Some exceptions apply: If the user clicks or taps (desktop or mobile, respectively), “somewhere on the site during the browsing session,” the audio will play. On personal computers, Google tracks behavior and “if the user has frequently played media on the site, according to the Media Engagement Index” (MEI), audio will play. The MEI, according to a Google explanatory document, “provide[s] a metric reflecting the engagement of a given user with regards to media playback on a given origin.” The goal, said Google, is to let websites with high MEI scores bypass the no-sound-in-autoplay-content rule. Users can peruse their MSI status by typing chrome://media-engagement into Chrome’s address bar.
Users can peruse their MSI status by typing chrome://media-engagement into Chrome’s address bar.
Chrome 66 also sports some under-the-covers newness, including a trial of “Site Isolation” in preparation for a broader launch later. Site Isolation, which was revealed in December, is a new security technology meant to mitigate risks posed by Spectre, the processor vulnerability sniffed out by Google’s own engineers earlier in 2017.
The optional defense – users must manually switch it on – will eventually be made the default in Chrome. But first Google wants to test it on a limited pool of users after addressing earlier issues when it was enabled. Users can decline to participate in the trials by typing chrome://flags/#site-isolation-trial-opt-out in the address bar and then changing “Default” to “Opt-out (not recommended).”
Another big background alteration in Chrome 66 is the move to mark as untrustworthy older digital certificates from Symantec. With its newest version, Chrome labels Symantec-issued certificates generated before June 1, 2016, as insecure. Websites that failed to replace those certificates may be affected as the browser spews messages, some explicit, others subtler, telling users that the connection between them and the destination is insecure, and thus potentially dangerous.
Later this year, Chrome 70 – now set to roll out during the week of Oct. 14-20 – will distrust every Symantec certificate, no matter when it was issued.
The dispute between Google and Symantec over certificates, and Chrome’s ban, goes back to 2015, when several browser makers, Google included, accused Symantec and its partners of improperly issuing certificates. Google, for one, concluded that Symantec’s problems were endemic.
Google also patched more than 60 security vulnerabilities in version 66, including two marked as “Critical,” the most serious ranking in the company’s four-step system, and six tagged as “High.” The two critical vulnerabilities were reported by researcher Ned Williamson, on March 28 and 30; Google’s fast patching was almost certainly due to their seriousness.
Google shelled out $34,000 for reporting 19 of the bugs, with several bounties, including Williamson’s, still to be decided.
Chrome’s next upgrade, version 67, should start reaching users May 29.

Chrome 65
Google on March 6 released Chrome 65 for Windows, macOS and Linux, with fixes for 45 vulnerabilities, and security and developer improvements and enhancements that users won’t see, or even notice.
Chrome updates in the background, so users only need relaunch the browser to install the latest version. (To manually update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right; the resulting tab either shows the browser has been updated or displays the download-and-upgrade process before presenting a “Relaunch” button.) Those new to Chrome can download it from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks. It last upgraded the browser on Jan. 24.
Some upgrades, like Chrome 64, boast obvious-to-the-end-user modifications that alter the browser’s performance, signal adoption of web standards or debut new functionality. (The user interface, or UI, of Chrome has changed little since the browser’s 2008 launch.) Other versions – and Chrome 65 is firmly in this camp – make virtually no splash because changes are exclusively behind the scenes, or nearly so.
Tops on that background list is support for the Web Authentication API “enabling the creation and use of strong, attested, scoped, public key-based credentials by web applications, for the purpose of strongly authenticating users.” Both Microsoft (for Edge) and Mozilla (Firefox) have also committed to the standard. Support for the API was left disabled in Chrome 65; it can be enabled from the page that results from typing chrome://flags in the address bar.
Other improvements include the introduction of CSS Paint API and Server Timing API. The former lets web developers craft images programmatically, eliminating the need to insert actual images – and thus load a resource from a server – as, say, background. The latter introduces new functionality that site designers and administrators can use to pass performance information on the server, from the server, to the browser.
In other areas, however, Chrome was twiddling thumbs. Last year, Google announced that Chrome 64 would not allow any auto-play content unless the audio was muzzled. Some exceptions were to apply: If the user clicked or tapped (desktop Chrome or mobile Chrome, respectively), “somewhere on the site during the browsing session,” the audio would still play. But the mandate did not go live in January with Chrome 64, as expected. Nor has it been activated in Chrome 65. Instead, Google has delayed enforcement to the middle of April, when Chrome 66 will appear.
But sites that have long relied on auto-play content – the sports website espn.com, for one – have been preparing for the Chrome ruling by muting the audio on video clips (the video still cranks up as soon as the user navigates to a story).
Google also patched nearly four dozen security vulnerabilities in version 65, including nine marked as “High,” the second-most-serious ranking in the company’s four-step system. Google paid researchers $34,500 for reporting 19 of the 45 bugs, with one additional report’s bounty still to be decided.
Chrome’s next upgrade, to version 66, should start reaching users on April 17.
Chrome 64
Google on Jan. 24 released Chrome 64 for Windows, macOS and Linux, boosting the browser’s defenses against the microprocessor flaws that blitzed through the news earlier this month.
The upgrade also beefed up Chrome’s pop-up blocker, put a stop to hucksters hijacking the browsing session by automatically steering to an unwanted website, and implemented a promised option to let users mute auto-playing audio on a site-by-site basis. And Google’s security team patched 53 new vulnerabilities in the browser.
Chrome updates in the background, so most users can simply relaunch the browser to get the latest version. To manually manage an update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser has been updated or displays the download-upgrade process before presenting a “Relaunch” button. Those new to Chrome can download it from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks; the last time it upgraded the browser, to version 63, was Dec. 5, or seven weeks ago.
Earlier this month, Google promised to bolster defenses against the Spectre vulnerabilities its Project Zero team had uncovered in most modern processors. The firm followed through with Chrome 64, which boasts a refresh of Google’s V8 JavaScript engine. Tweaks to V8 have been added to make it much tougher for hackers to pull off a successful Spectre attack.
Other browser makers beat Google to the punch on Spectre, but the difference appeared to be moot: Active attacks leveraging the vulnerabilities have not appeared, or if they have, been detected.
Chrome 64 included patches for more than four dozen other, more run-of-the-mill vulnerabilities, with Google paying out at least $22,000 in bounties to the researchers who reported the bugs. Google listed some of those bugs here.
Google also continued its war on unwanted and intrusive content by improving Chrome 64’s built-in pop-up blocker so that it can handle more kinds of abuses. Devious behavior – including disguising links to third-party websites as an audio/video play control, or as a close-window button – will be spotted by Chrome 64, which will then refuse to open the new tab or window that the criminals had pre-programmed.
Likewise, Chrome 64 sniffs out hidden-to-the-human-eye page elements that auto-open a tab or create a new browser window, then drag the unsuspecting user to a rogue destination. “Usually one of them is an ad or something that you didn’t want,” Pete LePage, a Google developer advocate, asserted in a post to a company blog. “Starting in Chrome 64, these types of navigations will be blocked, and Chrome will show some native UI [user interface] to the user – allowing them to follow the redirect if they want.”
A more noticeable change to Chrome was the adoption of a long-promised option that lets users manually mute auto-play audio on a site-by-site basis.
In September 2017, Google announced that starting with December’s Chrome 63, users would be able to select a site-specific muting option from the Page Info bubble (called up by clicking on the “i” within a circle at the far left of the URL in the address bar). Changing the option to “Always block on this site” from “Allow” would silence all auto-play audio on that domain.
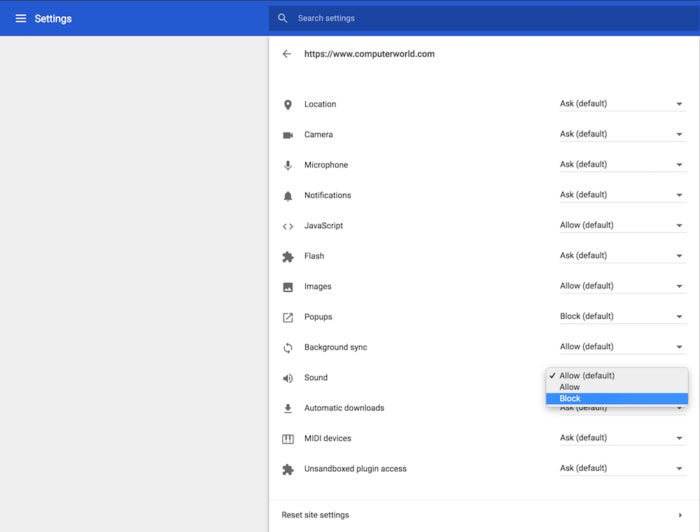
Chrome 64 users can select a site-specific muting option to silence all auto-play audio on that domain.
Google missed the Chrome 63 timeline but managed to bake it into Chrome 64 instead.
However, a more draconian auto-play policy has yet to be put into place. Last year, Google announced that Chrome 64 would not allow any auto-play content unless it muzzled the audio. Some exceptions were to apply: If the user clicked or tapped (desktop Chrome or mobile Chrome, respectively), “somewhere on the site during the browsing session,” the audio would still play.
The new keep-it-down-over-there mandate did not go live with Chrome 64, as expected. Instead, Google pushed off the rule’s introduction to the middle of April, when Chrome 66 is scheduled to show up.
Google’s next browser upgrade, Chrome 65, should reach users the week of March 4-10, according to its release calendar.

Chrome 63
Google this week issued Chrome 63 for Windows, macOS and Linux, adding important security enhancements for enterprises to stress the importance the company now puts on the commercial market.
“Starting with [this] release, Site Isolation is now available … [which] renders content for each open website in a separate process, isolated from other websites. This can mean even stronger security boundaries between websites than Chrome’s existing sandboxing technology,” wrote Matt Blumberg, product manager for Chrome, in a post to a company blog.
Chrome updates in the background, so most users can simply relaunch the browser to get the latest version. To manually manage an update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser has been updated or displays the download-upgrade process before presenting a “Relaunch” button. New to Chrome? It can be downloaded from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks; the last time it upgraded the browser, to version 63, was Oct. 17, or seven weeks before its Wednesday refresh.
Although Chrome 63 includes improvements aimed at all users – such as a speedier V8 JavaScript engine – Google chose to trumpet a number suitable only for corporate customers.
The most prominent is the Site Isolation Blumberg discussed. When enabled, the feature and its underlying technologies render each open website in a separate, dedicated process, isolating that site – and more importantly, its contents – from other sites. A major step up from the already-in-Chrome by-tab process assignments, site isolation will prevent remote code that does execute within Chrome’s renderer sandbox from manipulating other sites, and the code within them.
The new quarantine is more rigid than Chrome’s current sandboxing. According to Google, while Chrome now “makes an effort to place pages from different websites in different renderer processes when possible,” that doesn’t always happen. Site Isolation guarantees that each site is separated from all others.
It also comes at a price: Google acknowledged that turning on Site Isolation will increase Chrome’s memory usage up to 20%, a tough penalty when users already bemoan the browser’s voracious appetite.
Site Isolation can be enabled for all sites, or just a select few – a company’s intranet, for example – or other internal websites that contain the most sensitive information and are thus the most valuable to hackers, like customer data.
Windows GPOs – Group Policy Objects – can be set by administrators and then pushed to those workers running Chrome. Command-line flags can also be used on individual machines or for IT testing prior to wider deployment via group policies. Instructions are available here.
Google isn’t the only browser maker trumpeting isolationist technologies. Chrome may have led the way to multiple processes – it debuted in 2008 with that in place – and historically been the most difficult of the major browsers to crack and hack, but Microsoft has expended time and money on its Edge, too. The latest move by Microsoft – Application Guard, baked into Windows 10 – isolates Edge in a bare bones virtual machine; it cannot be duplicated by Google.
Also on the Chrome 63 change list: GPOs that the IT staff can set to bar Chrome extensions by the privileges they demand. For example, the new policies could be used to ensure users don’t install any add-on that can capture audio through a device’s microphone or access the company’s printers. The upgrade also turns on TLS (Transport Layer Security) 1.3, a more robust encryption standard, when Chrome is steered to gmail.com. Blumberg promised that TLS 1.3 support would expand “to the broader web” in 2018.
Blumberg also issued one of Google’s periodic advance warnings about future moves meant for Chrome, telling users that come version 68 – slated to ship the week of July 22-28, 2018 – Google will start blocking third-party software from injecting code into Chrome on Windows. Antivirus (AV) applications in particular use code-injection, a now-disparaged technique because of stability issues and vulnerability to hackers’ attacks, to monitor browsers for possible infection.
With version 68, only software that, if banned from injecting code into Chrome, crashes the browser will be allowed to run so that Chrome can launch and display a message advising the user to remove the culprit. When Chrome 72 launches in early 2019, all code injection will be stymied. However, recognizing that enterprises may be wedded to such software, and unable to abandon those programs or find substitutes, Google plans to introduce GPOs that “offer admins extended support for critical apps” requiring code injection.
Included in Chrome 63 are patches for 37 security flaws, one of which was rated “Critical,” Google’s most-serious, and rare, ranking. That bug’s finder was awarded $10,500 for his report, with more than $36,000 in bounties paid to security researchers for the remaining vulnerabilities.
The next upgrade, Chrome 64, should reach users the week of Jan. 21-27, 2018, according to Google’s release calendar.
Chrome 62
Google this week released Chrome 62 for Windows, macOS and Linux, setting the stage for a new warning when users enter data on an unencrypted website and patching nearly three dozen security vulnerabilities.
Chrome updates in the background, so most users can simply relaunch the browser to get the latest version. (To manually manage an update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser has been updated or displays the download-upgrade process before presenting a “Relaunch” button.) New to Chrome? It can be downloaded from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks; the last time it upgraded the browser, to version 61, was Sept. 6, or just under six weeks before its Tuesday refresh.
Version 62, like most of Chrome’s upgrades, hands over few if any obvious-at-a-glance changes. An exception this time: Chrome 62 is now ready to alert users that a site is insecure if it a) isn’t encrypted with a digital certificate and b) the user starts to fill out any form field on the page. Also set to receive warnings are all pages viewed in Chrome’s “Incognito” mode, the browser’s no-tracks session. In those scenarios, users will see the text “Not Secure” at the far left of the address bar.
The feature is “now ready” because as of Friday, Google had not switched on the alert. That wasn’t a surprise: Google typically tests a new feature with a small fraction of the total Chrome user base before remotely enabling the feature for all users. Assuming that feedback and Google’s own telemetry point to zero problems, it will flip a flag and the warnings will appear.
Those who want to see the warning immediately should enter chrome://flags in the address bar, search for and find the entry “Mark non-secure origins as non-secure,” and change the entry in the drop-down list from “Default” to “Warn on HTTP while in incognito mode or after editing forms.”
The Not Secure warning is the latest step in an extended process that Google has aggressively implemented – mainly using Chrome, but with other services in its stable, too, like Gmail – to pressure all sites to encrypt their traffic. Chrome already sounded the alarm when an unencrypted site accepted passwords or credit card information; 62 is the next in the planned progression.
Eventually, Chrome will show the Not Secure notice on every HTTP page.
Also on the Chrome 62 change list are support for OpenType variable fonts, which compact multiple font sizes and styles in a single package, giving site designers more flexibility in crafting attractive pages; and support for an expanded Network Information API (application programming interface) that provides connection performance metrics from the browser, a useful tool for web app developers creating software suitable for a variety of speeds.
Included in Chrome 62 are patches for 35 security vulnerabilities, a fifth of which were rated “High,” Google’s second-most-serious ranking. The firm paid out just over $40,000 in bug bounties to security researchers for reporting the vulnerabilities.
The next upgrade, Chrome 63, should reach users the week of Dec. 3-9, according to Google’s release calendar.

Chrome automatically downloads its latest update in the background, then refreshes itself the next time it’s launched.
Chrome 61
Google on Wednesday released Chrome 61 for Windows, macOS and Linux, adding several new behind-the-scenes features — including one that lets web apps access USB peripherals — and patching 22 security vulnerabilities.
Chrome updates in the background, so most users need only relaunch the browser to get the latest version. (To manually manage an update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser has been updated or displays the download-upgrade process before presenting a “Relaunch” button.) New to Chrome? It can be downloaded from this Google site.
The Mountain View, Calif. company updates Chrome every six to seven weeks; the last time it upgraded the browser, to version 60, was July 25, or just over six weeks ago.
Version 61, like many if not most of Chrome’s upgrades, deals users few if any changes they’ll notice at a glance. Instead, this month’s update offers new under-the-hood functionality aimed at site and app developers.
Near the top of that change list is the WebUSB API (application programming interface), which is intended to give web app and site developers access to unusual USB devices.
“Most hardware peripherals such as keyboards, mice, printers, and gamepads are supported by high-level web platform APIs,” Pete LePage, a developer advocate at Google, noted in a post about Chrome 61. “But, using specialized educational, scientific, industrial or other USB devices in the browser has been hard, often requiring specialized drivers.”
And Chrome 61 added native support for JavaScript modules so developers can properly call up discrete and reusable chunks of script code from within the browser without performing a build step. Chrome’s support – like that already baked into Apple’s Safari browser – allows for fetching dependent modules in parallel, and guarantees that the script executes in the right order. Mozilla and Microsoft plan to natively support JavaScript modules in their Firefox and Edge browsers down the road.
Additionally, Chrome will now automatically drop out of full-screen mode if a JavaScript dialog box opens; scammers often use such dialogs, and a forced shift to full-screen, to prevent the user from discarding their bogus claims of PC infections.
Also included in Chrome 61 are patches for 22 security vulnerabilities, a quarter of which were rated “High,” Google’s second-most-serious ranking. The firm also paid out $23,500 in bug bounties – and will pay more once it decides how much to fork over for one of the flaws – to security researchers for reporting the vulnerabilities.
Although it didn’t tie it to the release of Chrome 61, Google also recently made it possible for users to install browser previews alongside the stable, production-grade version on a Windows personal computer. The Beta and Dev channel builds can be downloaded from here.
The next edition, Chrome 62, should reach users the week of Oct. 15-21, according to Google’s release calendar.
Chrome updates automatically in the background, then upgrades itself the next time it’s launched.

Chrome 60
Google on Tuesday released Chrome 60 for Windows, macOS and Linux, adding support for the Touch Bar on the newest MacBook Pro laptops and a new online payment API, and patching 40 security vulnerabilities.
Chrome updates in the background, so most users need only relaunch the browser to get the latest version. (To manually manage an update, select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right. The ensuing page either shows the browser is already up to date or displays the updating process before presenting a “Relaunch” button.)
The Mountain View, Calif. company updates Chrome every six or seven weeks; the last time it upgraded the browser, to version 59, was June 5, or just over seven weeks ago.
Much of Chrome 60’s new features and functional changes are under the hood, aimed exclusively at website and app developers. One exception: Support for the MacBook Pro Touch Bar.
In October 2016, and on the top-end 13- and 15-in. models, Apple replaced the static row of function keys at the top of the MacBook Pro keyboard with an OLED (organic light-emitting diode) display whose contents change depending on the active application. Initially, Touch Bar support came from Apple and its own software, such as Maps. A few third-party programs, including Adobe Photoshop and Microsoft Office, have followed suit.
Apple’s own browser, Safari, supported the Touch Bar out of the gate last year.
Now, when Chrome is the active application, the Touch Bar displays Chrome-specific virtual buttons, like those for moving forward and backward through browsing history, refreshing the current web page or bookmarking it. Users can customize the Touch Bar settings for Chrome from within the browser.
Google added a host of developer-only features and APIs (application programming interfaces) to Chrome 60, notably support for the already existing Payment Release API, which is designed to simplify online payments by eliminating the traditional check-out forms many websites use. Currently, Chrome, Microsoft’s Edge and Mozilla’s Firefox all support the API, although the latter has disabled it in current builds.
Also included in Chrome 60 were patches for 40 security vulnerabilities, nearly a quarter of which were rated “High,” the second-most-serious ranking in Google’s four-step system. Google paid out $26,000 in bug bounties — and will pay more than that in the end, as it has yet to decide on three of the vulnerabilities — to security researchers for reporting the flaws.
People who haven’t tried Google’s desktop browser can download Chrome 60 for Windows, macOS Linux from Google’s website. Current users can let the automatic updater download and install the new version. To manually trigger the pending update, users select “About Google Chrome” from the Help menu under the vertical ellipsis at the upper right.
The next edition, Chrome 61, should reach users the week of Sept. 3-9, according to Google’s release calendar.
