What exactly are you missing once you don’t enable global risk alerts?
Network telemetry is really a reservoir of information that, if tapped, may reveal users’ behavioral designs, weak spots in protection, malicious equipment installed in enterprise conditions potentially, and malware itself even.
Worldwide threat alerts (formerly Cognitive Threat Analytics referred to as CTA) is excellent at consuming an enterprise’s network telemetry and working it by way of a pipeline of state-of-the-art machine learning and graph algorithms. After processing the visitors information in batch in just a matter of hrs, global risk alerts correlates all of the consumer behaviors, assigns priorities, and organizations detections intelligently, to provide security analysts clearness into what the main threats come in their network.
Wise alerts
All detections are presented inside a context-rich manner, gives users the opportunity to drill in to the specific security activities that assistance the threat detections grouped eventually into alerts. That is useful because simply detecting potentially malicious visitors in your infrastructure isn’t enough; analysts have to build an knowing of every threat detection. That’s where global danger alerts saves your time, investigating alerts and accelerating quality.

As depicted below in Number 2, users may both change the severe nature degrees of threats and position high-priority asset groupings from within the global threat alerts portal. This permits customers to customize their configurations to just alert them to the forms of threats that their companies are most worried about, as properly as to point which assets are most valuable. The users are allowed by these configurations to create proper context for threat alerts within their business environment.

Figure 2: You modification the priority of threats and asset organizations from within the worldwide risk alerts portal.
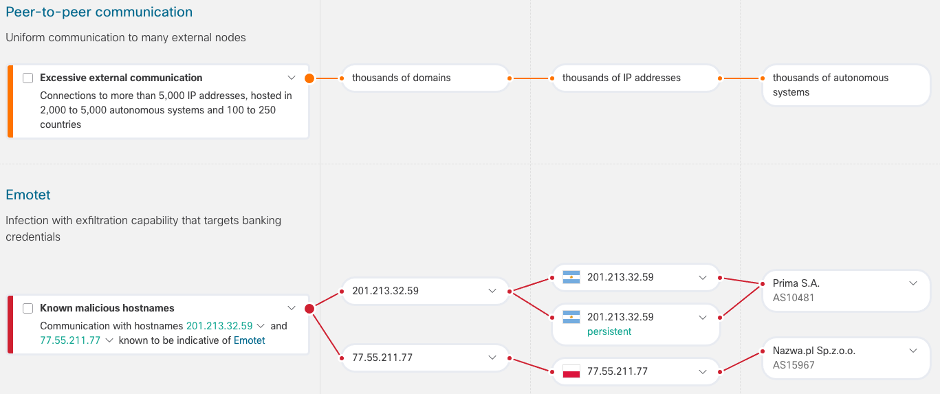
Worldwide threat alerts are presented inside a far more intuitive manner also, with several threat detections grouped into one particular alert in line with the following parameters:
-
- Concurrent threats : Different threats which are occurring collectively.
-
- Asset groups worth : Band of threats happening on endpoints that belong to asset groupings with similar business worth.

Rich recognition portfolio
Global threat alerts is definitely continuously evolving and tracking a huge selection of threat detections across different malware families, attack patterns, and tools utilized by malicious actors.
Each one of these outcomes and detections are for sale to Encrypted Visitors Analytics telemetry (ETA) aswell, which allows customers to get threats in encrypted visitors with no need to decrypt that visitors. Furthermore, because ETA telemetry includes more information than conventional NetFlow, the global danger alerts’ research team in addition has developed specific classifiers which are capable of finding extra threats in this information, such as for example with algorithms which are centered on detecting malicious styles in the road and the query of a URL.
The global threat alerts’ research team is continuously engaged in dissecting new security threats and implementing the associated threat intelligence findings into a huge selection of specialized classifiers. These classifiers are usually targeted at revealing strategies that attackers are employing on a worldwide scale. Types of the Maze is roofed by these promotions ransomware and the njRAT remote control access trojan. Numerous algorithms are made to capture generic malicious strategies like command-and-control traffic furthermore, command-injections, or lateral system movements.
Danger map of the web
There are many algorithms centered on uncovering threat infrastructure in the network. These versions are continuously discovering human relationships between identified malicious servers and fresh servers which have not however been thought as malicious, but either talk about client or designs bases with the recognized malicious servers. These models also continuously exchange identified threat cleverness with other Cisco protection products and groups recently, such as Talos.

This complex approach of threat recognition includes multiple layers of model learning algorithms to supply high-fidelity detections which are always up-to-time and relevant, as researchers are usually constantly updating the device models. Additionally, all of this computation is performed in the cloud and utilizes just network telemetry information to derive new results. The alerts and findings are presented to users in Secure System Analytics and Secure Endpoint.
Worldwide threat alerts uses state-of-the-art algorithms to supply high-fidelity, special threat detections for north-south network traffic, Intelligent Alerts to greatly help prioritize and accelerate resolutions, and a risk map to supply greater context and knowledge of how threats span over the network.
It is possible to enable it in Secure Network Analytics or Web Appliance together with your Secure Endpoint license.
<br>

You must be logged in to post a comment.