Use AWS System Firewall to filtration system outbound HTTPS visitors from apps hosted on Amazon EKS and gather hostnames supplied by SNI
This website post shows how exactly to setup an Amazon Elastic Kubernetes Service (Amazon EKS) cluster in a way that the applications hosted on the cluster might have their outbound access to the internet restricted to a couple of hostnames supplied by the Server Name Indication (SNI) in the allow listing in the AWS System Firewall rules. For encrypted website traffic, SNI may be used for blocking usage of specific websites in the system firewall. SNI can be an expansion to TLS that continues to be unencrypted in the visitors stream and indicates the location hostname litigant is wanting to access over HTTPS.
<pre> <code> <p>This post also demonstrates how to utilize Network Firewall to get hostnames of the precise sites which are being accessed by the application. Securing outbound visitors to particular hostnames is named <a href="https://sobre.wikipedia.org/wiki/Egress_filtering" focus on="_blank" rel="noopener noreferrer"><em>egress filtering</em></a>. In personal computer networking, egress filtering may be the practice of supervising and possibly restricting the circulation of information outbound in one system to another. Securing outbound traffic is performed through a &lt usually;a href="https://searchsecurity.techtarget.com/definition/firewall" focus on="_blank" rel="noopener noreferrer">firewall</the> that blocks <a href="https://searchnetworking.techtarget.com/description/packet" focus on="_blank" rel="noopener noreferrer">packets</the> that neglect to meet certain protection requirements. One particular firewall is AWS System Firewall, a managed assistance which you can use to deploy essential system protections for all of one's VPCs that you generate with <a href="https://aws.amazon.com/vpc/" focus on="_blank" rel="noopener noreferrer">Amazon Virtual Personal Cloud (Amazon VPC)</the>. </p>
<h2>Example situation</h2>
<p>The choice is had by one to scan your application visitors by the identifier of the requested SSL certificate, making you independent from the partnership of the Ip to the certificate. The certificate could possibly be offered from any Ip. Traditional stateful packet filter systems cannot follow the changing Ip of the endpoints. As a result, the host name details that you will get from the SNI will become important in making safety decisions. <a href=”https://aws.amazon.com/eks/” focus on=”_blank” rel=”noopener noreferrer”>Amazon EKS</the> has gained reputation for operating containerized workloads in the AWS Cloud, and you will restrict outbound visitors to just the known hostnames supplied by SNI. This posting will stroll you through the procedure of establishing the EKS cluster in two various subnets which means that your software program can use the excess visitors routing in the VPC and visitors filtering through <a href=”https://aws.amazon.com/network-firewall/” focus on=”_blank” rel=”noopener noreferrer”>System Firewall</the>.</p>
<h2>Remedy architecture</h2>
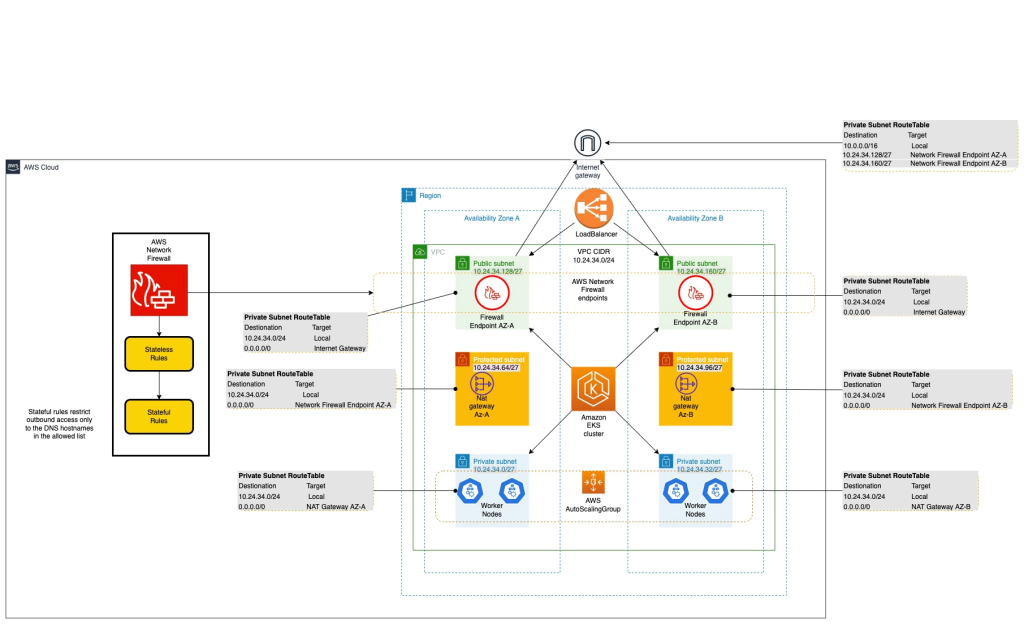
<p>The architecture illustrated in Number 1 displays a VPC with three subnets in Availability Zone A, and three subnets in Availability Zone B. You can find two open public subnets where System Firewall endpoints are usually deployed, two personal subnets where the employee nodes for the EKS cluster are usually deployed, and two guarded subnets where NAT gateways are usually deployed.</p>
<div id=”attachment_27106″ course=”wp-caption aligncenter”>
<img aria-describedby=”caption-attachment-27106″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/09/07/img1-1024×624.png” alt=”Figure 1: Outbound access to the internet through Network Firewall from Amazon EKS employee nodes” width=”760″ course=”size-large wp-picture-27106″>
<p id=”caption-attachment-27106″ course=”wp-caption-text”>Figure 1: Outbound access to the internet through System Firewall from Amazon EKS employee nodes</p>
</div>
<p>The workflow in the architecture for outbound usage of a third-party service is really as follows:</p>
<ol>
<li>The outbound request hails from the application form running in the private subnet (for instance, to https://aws.amazon.com) and is passed to the NAT gateway inside the protected subnet.</li>
<li>The HTTPS traffic received in the protected subnet is routed to the AWS System Firewall endpoint in the general public subnet.</li>
<li>The network firewall computes the guidelines, and either accepts or declines the request to pass to the web gateway.</li>
<li>If the demand is passed, the application-requested URL (supplied by SNI in the non-encrypted HTTPS header) is allowed in the network firewall, and gets to the third-celebration server for accessibility successfully.</li>
</ol>
<p>The VPC settings because of this post follow the recommendation for using private and public subnets referred to in <a href=”https://docs.aws.amazon.com/eks/most recent/userguide/create-public-private-vpc.html” focus on=”_blank” rel=”noopener noreferrer”>Developing a VPC for the Amazon EKS cluster</the> in the Amazon EKS Consumer Guide, but with extra subnets known as <em>safeguarded subnets</em>. Of putting the NAT gateway in a general public subnet instead, it shall be put into the protected subnet, and the System Firewall endpoints in the general public subnet will filtration system the egress visitors that flows through the NAT gateway. This style pattern adds additional checks and may be a suggestion for your VPC set up.</p>
<p>Like suggested inside <a href=”https://docs.aws.amazon.com/eks/most recent/userguide/create-public-private-vpc.html” focus on=”_blank” rel=”noopener noreferrer”>Developing a VPC for the Amazon EKS cluster</a>, utilizing the <strong>Open public and personal subnets</strong> option enables you to deploy your employee nodes to personal subnets, and allows Kubernetes to deploy load balancers to the general public subnets. This set up can load-balance visitors to pods which are working on nodes in the personal subnets. As demonstrated in Figure 1, the perfect solution is uses yet another subnet named the shielded subnet, from the general public and personal subnets apart. The secured subnet is really a VPC subnet deployed between your public subnet and personal subnet. The outbound internet visitors that’s routed through the covered subnet will be rerouted to the System Firewall endpoint hosted within the general public subnet. You may use the same technique described in <a href=”https://docs.aws.amazon.com/eks/most recent/userguide/create-public-private-vpc.html” focus on=”_blank” rel=”noopener noreferrer”>Developing a VPC for the Amazon EKS cluster</a> to put different AWS assets within personal subnets and open public subnets. The primary difference in this answer will be that the NAT is positioned by you gateway in another protected subnet, between personal subnets, and place System Firewall endpoints in the general public subnets to filter visitors in the system firewall. The NAT gateway’s Ip is preserved, and could be utilized for increasing the < still;em>allow checklist</em> of third-party entities that require connectivity for the apps operating on the EKS employee nodes.</p>
<p>To visit a practical illustration of the way the outbound visitors is filtered in line with the hosted names supplied by SNI, follow the methods in the next <strong>Deploy the sample</strong> section. You shall deploy an <a href=”http://aws.amazon.com/cloudformation” focus on=”_blank” rel=”noopener noreferrer”>AWS CloudFormation</the> template that deploys the answer architecture, comprising the VPC elements, EKS cluster parts, and the System Firewall elements. When that’s complete, it is possible to deploy an example app working on Amazon EKS to check egress visitors filtering through AWS System Firewall.</p>
<h2>Deploy an example to test the system firewall</h2>
<p>Adhere to the steps in this particular section to perform an example app deployment to check the use condition of securing outbound targeted traffic through AWS Network Firewall.</p>
<h3>Prerequisites</h3>
<p>The prerequisite actions necessary for the sample deployment are the following:</p>
<ol>
<li>Be sure you possess the AWS CLI <a href=”https://docs.aws.amazon.com/cli/most recent/userguide/getting-started-install.html” focus on=”_blank” rel=”noopener noreferrer”>installed</the>, and <a href=”https://docs.aws.amazon.com/cli/most recent/userguide/cli-chap-configure.html” focus on=”_blank” rel=”noopener noreferrer”>configure</the> usage of your AWS accounts.</li>
<li><a href=”https://docs.aws.amazon.com/eks/newest/userguide/eksctl.html” focus on=”_blank” rel=”noopener noreferrer”>Install and create the <period>eksctl</period> tool</the> to generate an Amazon EKS cluster. </li>
<li>Copy the required CloudFormation templates and the sample <period>eksctl</period> config documents from the blog’s Amazon S3 bucket to your neighborhood file system. You are able to do this utilizing the using AWS CLI S3 <a href=”https://docs.aws.amazon.com/cli/most recent/reference/s3/cp.html” focus on=”_blank” rel=”noopener noreferrer”>cp</the> order.<br><program code>aws s3 cp s3://awsiammedia/community/sample/803-network-firewall-to-filter-outbound-visitors/ config.yaml .
aws s3 cp s3://awsiammedia/public/sample/803-network-firewall-to-filter-outbound-visitors/ lambda_functionality.py .
aws s3 cp s3://awsiammedia/general public/sample/803-network-firewall-to-filter-outbound-visitors/ network-firewall-eks-collect-all.yaml .
aws s3 cp s3://awsiammedia/public/sample/803-network-firewall-to-filter-outbound-visitors/ network-firewall-eks.yaml .</program code>
<blockquote>
<p><strong>Essential:</strong> This control shall download the S3 bucket contents to the present directory on your own terminal, therefore the “.” (dot) inside the command is essential.</p>
</blockquote> </li>
<li>This is complete once, you should be in a position to see the set of files shown in Shape 2. (The list contains config.yaml, lambda_function.py, network-firewall-eks-collect-just about all.yaml, and network-firewall-eks.yaml.)
<div id=”attachment_27107″ course=”wp-caption aligncenter”>
<img aria-describedby=”caption-attachment-27107″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/09/07/img2.png” alt=”Figure 2: Documents downloaded from the S3 bucket” width=”592″ elevation=”152″ class=”size-complete wp-image-27107″>
<p id=”caption-attachment-27107″ course=”wp-caption-text”>Figure 2: Data files downloaded from the S3 bucket</p>
</div> </li>
</ol>
<h3>Deploy the VPC architecture with AWS System Firewall</h3>
<p>In this process, you’ll deploy the VPC architecture with a CloudFormation template.</p>
<p id=”deploy_VPC_architecture”><strong>To deploy the VPC architecture (AWS CLI)</strong></p>
<ol>
<li>Deploy the <a href=”https://awsiammedia.s3.amazonaws.com/public/sample/803-network-firewall-to-filter-outbound-traffic/network-firewall-eks.yaml” rel=”noopener noreferrer” focus on=”_blank”>CloudFormation template</the> <program code>network-firewall-eks.yaml</code>, that you earlier downloaded to your neighborhood file program from the Amazon S3 bucket. <p>You can certainly do this through the AWS CLI utilizing the <a href=”https://docs.aws.amazon.com/cli/most recent/reference/cloudformation/create-stack.html” focus on=”_blank” rel=”noopener noreferrer”>create-stack</the> command, the following.</p> <p> <program code>aws cloudformation create-stack –stack-name AWS-Network-Firewall-Multi-AZ
–template-body document://network-firewall-eks.yaml
–parameters ParameterKey=NetworkFirewallAllowedWebsites,ParameterValue=”.amazonaws.com,.docker.io,.docker.com”
–capabilities Ability_NAMED_IAM</program code></p>
<blockquote>
<p><strong>Notice:</strong> The at first permitted hostnames for egress filtering are usually passed to the system firewall utilizing the parameter key <program code>NetworkFirewallAllowedWebsites</program code> in the CloudFormation stack. In this instance, the allowed hostnames are usually <program code>.amazonaws.com</code>, <program code>.docker.io</program code>, and <program code>docker.com</program code>.</p>
</blockquote> </li>
<li>Take note of the subnet IDs from the stack outputs of the CloudFormation stack following the status would go to <program code>Create_Complete</program code>.<br> <br><program code>aws cloudformation describe-stacks
–stack-name AWS-Network-Firewall-Multi-AZ</program code>
<blockquote>
<p><strong>Take note:</strong> For simplicity, the CloudFormation stack title is AWS-Network-Firewall-Multi-AZ, nevertheless, you can transform this true name to in accordance with your preferences and follow exactly the same naming throughout this article.</p>
</blockquote> </li>
</ol>
<p><strong>To deploy the VPC architecture (system)</strong></p>
<p>In your account, release the AWS CloudFormation template by selecting the next Launch Stack button. It will require ten minutes for the CloudFormation stack to perform approximately.</p>
<p><a href=”https://gaming console.aws.amazon.com/cloudformation/home?region=us-east-1#/stacks/new?stackName=thirdparty-codepipeline-git-supply&templateURL=https://awsiammedia.s3.amazonaws.com/general public/sample/803-network-firewall-to-filter-outbound-traffic/network-firewall-eks.yaml” rel=”noopener noreferrer” focus on=”_blank”><img src=”https://d2908q01vomqb2.cloudfront.internet/22d200f8670dbdb3e253a90eee5098477c95c23d/2019/06/05/launch-stack-key.png” alt=”Choose this image to open up a web link that starts developing the CloudFormation stack” width=”190″ height=”36″ course=”aligncenter size-full wp-image-10149″></the></p>
<blockquote>
<p><strong>Notice:</strong> The stack shall start in the N. Virginia (us-east-1) Area. To deploy this remedy into other AWS Areas, download the solution’s CloudFormation template, change it, and deploy it to the selected Area.</p>
</blockquote>
<h3>Deploy and setup usage of the EKS cluster </h3>
<p>In this task, you’ll utilize the <a href=”https://eksctl.io/” focus on=”_blank” rel=”noopener noreferrer”>eksctl</the> CLI device to generate an EKS cluster.</p>
<p id=”deploy_an_EKS_cluster”><strong><a href=”https://aws.amazon.com/blogs/protection/use-aws-network-firewall-to-filter-outbound-https-traffic-from-applications-hosted-on-amazon-eks/#deploy_a good_EKS_cluster”>To deploy an EKS cluster utilizing the eksctl tool</the></strong></p>
<p>You can find two options for creating an EKS cluster. Technique A utilizes the <span>create cluster< eksctl;/span> command with out a configuration (config) document. Method B runs on the <a href=”https://eksctl.io/utilization/creating-and-managing-clusters/#using-config-files” focus on=”_blank” rel=”noopener noreferrer”>config document</the>.</p>
<blockquote>
<p><strong>Take note</strong>: Before you begin, make certain the VPC is experienced by you subnet points available from the prior procedure.</p>
</blockquote>
<p><strong>Method The: No config document</strong></p>
<p>It is possible to create an EKS cluster with out a config file utilizing the <a href=”https://eksctl.io/use/creating-and-managing-clusters/” focus on=”_blank” rel=”noopener noreferrer”>eksctl create cluster</the> order.</p>
<ol>
<li>From the CLI, enter the next commands.<br><program code>eksctl create cluster
–vpc-private-subnets= <private-subnet-The> , <private-subnet-B>
–vpc-public-subnets= <public-subnet-The> , <public-subnet-B> </program code></li>
<li>Be sure that the subnets exceeded to the <program code>–vpc-public-subnets</program code> parameter are usually protected subnets extracted from the VPC architecture CloudFormation stack result. It is possible to verify the subnet IDs by considering step two 2 in the <strong><a href=”https://aws.amazon.com/blogs/safety/use-aws-network-firewall-to-filter-outbound-https-traffic-from-applications-hosted-on-amazon-eks/#deploy_VPC_architecture”>To deploy the VPC architecture</the></strong> area. </li>
</ol>
<p><strong>Technique B: With config document</strong></p>
<p>Another real solution to create an EKS cluster is to apply the next config file, with an increase of options with the title (<program code>cluster.yaml</program code> in this illustration).</p>
<ol>
<li>Develop a document named <program code>cluster.yaml</code> with the addition of the next contents to it.
<div course=”hide-language”>
<pre><code class=”lang-text”>apiVersion: eksctl.io/v1alpha5
kind: ClusterConfig
metadata:
name: filter-egress-traffic-test
region: us-east-1
version: “1.19”
availabilityZones: [“us-east-1the”, “us-east-1b”]
vpc:
id:
subnets:
public:
us-east-1a: id: <public-subnet-A>
us-east-1b: id: <public-subnet-B>
private:
us-east-1a: id: <private-subnet-A>
us-east-1b: id: <private-subnet-B>
managedNodeGroups:
– name: nodegroup
desiredCapacity: 3
ssh:
allow: true
publicKeyName: main
iam:
attachPolicyARNs:
– arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore
– arn:aws:iam::aws:policy/AmazonEKSWorkerNodePolicy
– arn:aws:iam::aws:policy/AmazonEC2ContainerRegistryReadOnly
– arn:aws:iam::aws:policy/service-role/AmazonEC2RoleforSSM
– arn:aws:iam::aws:policy/AmazonEKSServicePolicy
– arn:aws:iam::aws:policy/AmazonEKSClusterPolicy
– arn:aws:iam::aws:policy/AmazonEKS_CNI_Policy
preBootstrapCommands:
– yum set up -y https://s3.amazonaws.com/ec2-downloads-windows/SSMAgent/most recent/linux_amd64/amazon-ssm-agent.rpm
– systemctl enable amazon-ssm-real estate agent sudo
– sudo systemctl start amazon-ssm-agent
<pre> <code> <li>Operate the following command to generate an EKS cluster utilizing the eksctl program and the <program code>cluster.yaml</code> config document.<br /><program code>eksctl create cluster -f cluster.yaml</program code></li>
<strong>To create usage of the EKS cluster</strong></p>
<ol>
<li> <p>Before you deploy an example <a href=”https://kubernetes.io/docs/ideas/workloads/pods/” focus on=”_blank” rel=”noopener noreferrer”>Kubernetes Pod</a>, make certain the < is got by you;program code>kubeconfig</program code> file create for the EKS cluster that you made in step two 2 of <strong>To deploy an EKS cluster utilizing the eksctl tool</strong>. To find out more, see <a href=”https://docs.aws.amazon.com/eks/latest/userguide/create-kubeconfig.html” focus on=”_blank” rel=”noopener noreferrer”>Develop a kubeconfig for Amazon EKS</the>. You may use <program code>eksctl</program code> to get this done, the following.</p> <p> <program code>eksctl utils write-kubeconfig -cluster filter-egress-traffic-check</program code> </p></li>
<li> <p>Established the <program code>kubectl context</code> to the EKS cluster you created, utilizing the following control.</p> <p> <program code>kubectl config get-contexts</program code></p> <p>Body 3 shows a good example of the result from this order.</p>
<div id=”attachment_27118″ course=”wp-caption aligncenter”>
<img aria-describedby=”caption-attachment-27118″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/09/07/img3-1024×51.png” alt=”Figure 3: kubectl config get-contexts control output” width=”700″ course=”size-large wp-picture-27118″ />
<p id=”caption-attachment-27118″ course=”wp-caption-text”>Figure 3: kubectl config get-contexts order output</p>
</div> </li>
<li> <p>Duplicate the context title from the control output and place the context utilizing the following order.</p> <p> <program code>kubectl config use-context <NAME-OF-CONTEXT> </program code></p></li>
</ol>
<p id=”deploy_sample_pod_about_EKS_cluster”><strong>To deploy an example Pod on the EKS cluster</strong></p>
<ol>
<li> <p>Following, deploy an example <a href=”https://kubernetes.io/docs/principles/workloads/pods/” focus on=”_blank” rel=”noopener noreferrer”>Kubernetes Pod</the> in the EKS cluster.</p> <p> <program code>kubectl run -we –tty amazon-linux -image=open public.ecr.aws/amazonlinux/amazonlinux:latest sh</program code></p> <p>When you have a Pod already, you may use the following control to <a href=”https://kubernetes.io/docs/tasks/debug/debug-application/get-shell-running-container/” target=”_blank” rel=”noopener noreferrer”>get yourself a shell to the running container</the>.</p> <p> <program code>kubectl attach amazon-linux -c alpine -we -t</program code></p></li>
<li>You can now test usage of a non-allowed website inside the AWS Network Firewall stateful guidelines, using these steps.
<ol>
<li>Very first, install the <a href=”https://sobre.wikipedia.org/wiki/CURL” focus on=”_blank” rel=”noopener noreferrer”>cURL</the> device on the sample Pod you previously created. cURL is really a command-line device for sending or obtaining data, including files, making use of <a href=”https://sobre.wikipedia.org/wiki/URL” focus on=”_blank” rel=”noopener noreferrer”>URL</the> syntax. Because cURL utilizes the libcurl library, every protocol is supported because of it libcurl supports. On the Pod where you have developed a shell to a operating container, run the next command to set up cURL.<br /><program code>apk install curl</program code></li>
<li>Access an internet site making use of cURL.<br /><program code>curl -We https://aws.amazon.com</program code> <p>Thus giving a timeout error like the right after.</p> <p> <code>curl -We https://aws.amazon.com
curl: (28) Operation timed out there after 300476 milliseconds with 0 out of 0 bytes received</program code> </p></li>
<li>Demand AWS CloudWatch system and check out the <a href=”https://docs.aws.amazon.com/network-firewall/most recent/developerguide/firewall-logging.html” focus on=”_blank” rel=”noopener noreferrer”>alert logs</a> for System Firewall. You shall visit a log entry just like the following sample, indicating that the usage of https://aws.amazon.com was blocked.
<div course=”hide-language”>
<pre><code class=”lang-text”>
“firewall_name”: “AWS-Network-Firewall-Multi-AZ-firewall”,
“availability_zone”: “us-east-1the”,
“event_timestamp”: “1623651293”,
“event”:
“timestamp”: “2021-06-14T06:14:53.483069+0000”,
“flow_id”: 649458981081302,
“event_type”: “alert”,
“src_ip”: “xxx.xxx.xxx.xxx”,
“src_port”: xxxxx,
“dest_ip”: “xxx.xxx.xxx.xxx”,
“dest_port”: 443,
“proto”: “TCP”,
“alert”:
“action”: “blocked”,
“signature_id”: 4,
“rev”: 1,
“signature”: “not complementing any TLS allowlisted FQDNs”,
“category”: “”,
“severity”: 1
,
“tls”:
“sni”: “aws.amazon.com”,
“version”: “UNDETERMINED”,
“ja3”: ,
“ja3s”:
,
“app_proto”: “tls”
</code> </pre>
</code> </pre>
</div> <p> The error shown happened because the hostname <code> www.amazon.com </code> had not been added to the System Firewall stateful guidelines allow listing. </p> <p> Once you deployed the system firewall in step one hands down the <strong> <a href="https://aws.amazon.com/blogs/security/use-aws-network-firewall-to-filter-outbound-https-traffic-from-applications-hosted-on-amazon-eks/#deploy_VPC_architecture"> To deploy the VPC architecture </a> </strong> treatment, the values supplied for the CloudFormation parameter <code> NetworkFirewallAllowedWebsites </code> had been just simply <code> .amazonaws.com </code> , <code> .docker.io </code> , <code> .docker.com </code> rather than <code> aws.amazon.com </code> . </p> </li>
</ol> </li>
</ol>
<h3> Update the System Firewall stateful guidelines </h3>
<p> In this process, you’ll update the System Firewall stateful guidelines to permit the <code> aws.amazon.com </code> domain title. </p>
<p> <strong> To update the System Firewall stateful rules (gaming console) </strong> </p>
<ol>
<li> In the <a href="https://console.aws.amazon.com/cloudformation" target="_blank" rel="noopener noreferrer"> AWS CloudFormation console </a> , find the stack you utilized to create the system firewall in the <strong> In order to deploy the VPC architecture </strong> procedure previously. </li>
<li> Choose the stack you need to update, and select <strong> Up-date </strong> . In the <strong> Parameters </strong> section, revise the stack with the addition of the hostname <code> aws.amazon.com </code> to the parameter <code> NetworkFirewallAllowedWebsites </code> as the comma-separated value. Discover <a href="https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/using-cfn-updating-stacks-direct.html" target="_blank" rel="noopener noreferrer"> Updating stacks straight </a> in the AWS CloudFormation User Guidebook to find out more on stack improvements. </li>
</ol>
<h3> Re-check from the sample pod </h3>
<p> In this task, you’ll check the outbound gain access to once more from the sample Pod you produced previous in the <strong> <a href="https://aws.amazon.com/blogs/security/use-aws-network-firewall-to-filter-outbound-https-traffic-from-applications-hosted-on-amazon-eks/#deploy_sample_pod_on_EKS_cluster"> To deploy an example Pod on the EKS cluster </a> </strong> method. </p>
test the outbound usage of the <code> aws To.amazon.com </code> hostname </strong> </p>
<ol>
<li> Get yourself a shell to a working container in the sample Pod that you deployed previous, utilizing the following order. <br /> <code> kubectl connect amazon-linux -c alpine -i -t </code> </li>
<li> On the terminal in which a shell was obtained by one to a operating container in the sample Pod, run the next cURL control. <br /> <code> curl -I https://aws.amazon.com </code> </li>
<li> The response ought to be successful HTTP 200 OK information such as this one. <br /> <code> curl -Ik https://aws.amazon.com
HTTP/2 200
content-type: textual content/html;charset=UTF-8
server: Server </code> </li>
</ol>
<p> If the VPC subnets are arranged based on the architecture recommended in this option, outbound visitors from the EKS cluster could be sent to the system firewall and filtered predicated on hostnames supplied by SNI. </p>
<h2> Collecting hostnames supplied by the SNI </h2>
<p> In this task, you’ll observe how to configure the system firewall to get all the hostnames supplied by SNI which are accessed by an currently running application-without blocking any access-by utilizing CloudWatch and <a href="https://docs.aws.amazon.com/network-firewall/latest/developerguide/firewall-logging.html" target="_blank" rel="noopener noreferrer"> alert logs </a> . </p>
<p> <strong> To configure the system firewall (system) </strong> </p>
<ol>
<li> In the <a href="https://console.aws.amazon.com/cloudformation" target="_blank" rel="noopener noreferrer"> AWS CloudFormation gaming console </a> , locate the stack that developed the network firewall previous in the <strong> <a href="https://aws.amazon.com/blogs/security/use-aws-network-firewall-to-filter-outbound-https-traffic-from-applications-hosted-on-amazon-eks/#deploy_VPC_architecture"> To deploy the VPC architecture </a> </strong> procedure. </li>
<li> Choose the stack to up-date, and choose <strong> Upgrade </strong> then. </li>
<li> Choose <strong> Replace present template </strong> and upload the template <span> network-firewall-eks-collect-all.yaml </span> . (This template ought to be accessible from the data files that you downloaded previously from the S3 bucket in the Prerequisites area.) Choose <strong> Following </strong> . Find <a href="https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/using-cfn-updating-stacks-direct.html" target="_blank" rel="noopener noreferrer"> Updating stacks directly </a> to learn more. </li>
</ol>
<p> <strong> To configure the system firewall (AWS CLI) </strong> </p>
<ol>
<li> Revise the CloudFormation stack utilizing the <code> network-firewall-eks-collect-all.yaml </code> template document that you downloaded from the S3 bucket inside the Prerequisites area previously, utilizing the <a href="https://docs.aws.amazon.com/cli/latest/reference/cloudformation/update-stack.html" target="_blank" rel="noopener noreferrer"> update-stack </a> command the following. <br /> <code> aws cloudformation update-stack --stack-name AWS-Network-Firewall-Multi-AZ
--template-body file://network-firewall-eks-collect-all.yaml
--capabilities Capacity_NAMED_IAM </code> </li>
</ol>
<p> <strong> To check on the guidelines in the AWS Administration Console </strong> </p>
<ol>
<li> In the AWS Management Console, demand Amazon VPC system and locate the <strong> AWS System Firewall </strong> tab. </li>
<li> Select the system firewall that you previously created, and then choose the stateful guideline with the title <span> log-all-tls </span> . </li>
<li> The rule team should appear as proven in Figure 4, indicating that the logs are sent plus captured to the Alert logs.
<div id="attachment_27123" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-27123" src="https://infracom.com.sg/wp-content/uploads/2022/09/img4-1.jpg" alt="Figure 4: Network Firewall rule groups" width="700" class="size-full wp-image-27123" />
<p id="caption-attachment-27123" class="wp-caption-text"> Figure 4: Network Firewall rule groupings </p>
</div> </li>
</ol>
<p> <strong> To check based on stateful principle </strong> </p>
<ol>
<li> On the terminal, obtain the shell for the working container in the Pod you made previous. If this Pod isn't available, follow the directions in the <strong> <a href="https://aws.amazon.com/blogs/security/use-aws-network-firewall-to-filter-outbound-https-traffic-from-applications-hosted-on-amazon-eks/#deploy_sample_pod_on_EKS_cluster"> To deploy an example Pod on the EKS cluster </a> </strong> process to create a brand-new sample Pod. </li>
<li> Operate the cURL order to <code> aws.amazon.com </code> . It will come back <code> HTTP 200 Alright </code> , the following. <br /> <code> curl -Ik https://aws.amazon.com/
HTTP/2 200
content-type: textual content/html;charset=UTF-8
server: Server
time:
------
----------
-------------- </code> </li>
<li> Demand AWS CloudWatch Logs gaming console and appearance up the Alert logs log team with the title <code> /AWS-Network-Firewall-Multi-AZ/anfw/alert </code> . <p> You can view the hostnames supplied by SNI within the TLS protocol moving through the system firewall. The CloudWatch Alert logs for permitted hostnames in the SNI appears like the next example. </p>
<div class="hide-language">
<pre> <code class="lang-text">
"firewall_name": "AWS-Network-Firewall-Multi-AZ-firewall",
"availability_area": "us-east-1b",
"event_timestamp": "1627283521",
"event":
"timestamp": "2021-07-26T07:12:01.304222+0000",
"flow_id": 1977082435410607,
"event_type": "alert",
"src_ip": "xxx.xxx.xxx.xxx",
"src_port": xxxxx,
"dest_ip": "xxx.xxx.xxx.xxx",
"dest_port": 443,
"proto": "TCP",
"alert":
"action": "allowed",
"signature_id": 2,
"rev": 0,
"signature": "",
"category": "",
"severity": 3
,
"tls":
"subject matter": "CN=aws.amazon.com",
"issuerdn": "C=US, O=Amazon, OU=Server CA 1B, CN=Amazon",
"serial": "08:13:34:34:48:07:64:27:4D:BC:CB:14:4D:AF:F2:11",
"fingerprint": "f7:53:97:5e:76:1electronic:fb:f6:70:72:02:95:d5:9f:2f:05:52:79:5d:ae",
"sni": "aws.amazon.com",
"version": "TLS 1.2",
"notbefore": "2020-09-30T00:00:00",
"notafter": "2021-09-23T12:00:00",
"ja3": ,
"ja3s":
,
"app_proto": "tls"
</code> </pre>
</div> </li>
</ol>
<p> Optionally, you can even create an <a href="http://aws.amazon.com/lambda" target="_blank" rel="noopener noreferrer"> AWS Lambda </a> function to get the hostnames which are approved through the system firewall. </p>
<p> <strong> To produce a Lambda function to get hostnames supplied by SNI (optional) </strong>
<pre> <code> <p><strong>Sample Lambda program code</strong></p>
<p>The sample Lambda code from Figure 5 is shown following, and is written in Python 3. The hostnames are collected by the sample which are supplied by SNI and captured in System Firewall. System Firewall logs the hostnames supplied by SNI in the CloudWatch Alert logs. After that, by <a href=”https://docs.aws.amazon.com/AmazonCloudWatch/best and newest/logs/SubscriptionFilters.html#LambdaFunctionExample” focus on=”_blank” rel=”noopener noreferrer”>developing a CloudWatch logs registration</a> filter, it is possible to deliver logs to the Lambda functionality for more processing, for instance to invoke SNS notifications.</p>
<div course=”hide-language”>
<pre><code class=”lang-text”>import json
import gzip
import base64
import boto3
import sys
import traceback
sns_client = boto3.customer(‘sns’)
def lambda_handler(occasion, context):
try:
decoded_occasion = json.loads(gzip.decompress(bottom64.b64decode(occasion[‘awslogs’][‘data’])))
body = ”’
filtermatch
”’.format(
loggroup=decoded_event[‘logGroup’],
logstream=decoded_event[‘logStream’],
filtermatch=decoded_event[‘logEvents’][0][‘message’],
)
print(entire body)# uncomment this for debugging
filterMatch = json.loads(body)
data = []
if ‘http’ in filterMatch[‘event’]:
data.append(filterMatch[‘occasion’][‘http’][‘hostname’])
elif ‘tls’ in filterMatch[‘event’]:
data.append(filterMatch[‘occasion’][‘tls’][‘sni’])
result = ‘Trying to attain ‘ + 1 ‘ ‘ + (information[0]) + 1 ‘ ‘ ‘via Network Firewall’ + 1*’ ‘ + (filterMatch[‘firewall_name’])
print(outcome)# uncomment this for debugging
message = ‘HostName’: result
send out_to_sns = sns_client.publish(
TargetArn=’ <SNS-topic-ARN> ‘, #Replace with the SNS subject ARN
Message=json.dumps(‘default’: json.dumps(message),
‘sms’: json.dumps(information),
’email’: json.dumps(information)),
Subject=’Trying to attain the hostname through the System Firewall’,
MessageStructure=’json’)
except Exception as electronic:
print(‘Function failed because of exception.’)
e = sys.exc_details()[0]
print(e)
traceback.print_exc()
Status=”Failure”
Information=(“Error occured while executing this. The error will be %s” %e)
<pre> <code> <h2>Clear up</h2>
In this task, you’ll tidy up the infrastructure that has been created within this alternative.</p>
<p><strong>To delete the Kubernetes workloads</strong></p>
<ol>
<li>On the terminal, utilizing the <period>kubectl</period> CLI device, run the following control to delete the sample Pod that you produced previously.<br /><program code>kubectl delete pods amazon-linux</program code>
<blockquote>
<p><strong>Take note:</strong> Tidy up all of the Kubernetes workloads operating on the EKS cluster. For instance, if the Kubernetes program of type LoadBalancer will be deployed, and when the EKS cluster where it is present is deleted, the LoadBalancer shall not really be deleted. The best practice would be to clean up all of the deployed workloads.</p>
</blockquote> </li>
<li>On the terminal, utilizing the <period>eksctl</period> CLI device, delete the developed EKS cluster utilizing the following order.<br /><program code>eksctl delete cluster –name filter-egress-traffic-test</program code></li>
</ol>
<p><strong>To delete the CloudFormation AWS and stack Network Firewall</strong></p>
<ol>
<li>Demand AWS CloudFormation system and pick the stack with the real name AWS-Network-Firewall-Multi-AZ.</li>
<li>Choose <strong>Delete,</strong> and at the prompt choose < then;strong>Delete Stack</strong>. To learn more, notice <a href=”https://docs.aws.amazon.com/AWSCloudFormation/most recent/UserGuide/cfn-console-delete-stack.html” focus on=”_blank” rel=”noopener noreferrer”>Deleting the stack upon the AWS CloudFormation gaming console</the>.</li>
</ol>
<h2>Bottom line</h2>
<p>By following VPC architecture explained inside this blog post, it is possible to protect the applications jogging in an Amazon EKS cluster simply by filtering the outbound visitors in line with the approved hostnames which are provided by SNI inside the Network Firewall Allow checklist.</p>
<p>In addition, with a straightforward Lambda function, CloudWatch Logs, and an SNS topic, you will get readable hostnames supplied by the SNI. Making use of these hostnames, it is possible to find out about the traffic design for the applications which are working within the EKS cluster, and later develop a strict list to permit only the mandatory outbound visitors. For more information around Network Firewall stateful guidelines, notice <a href=”https://docs.aws.amazon.com/network-firewall/current/developerguide/stateful-rule-groups-ips.html” focus on=”_blank” rel=”noopener noreferrer”>Dealing with stateful rule groups within AWS Network Firewall</the> in the AWS System Firewall Developer Tutorial.</p>
<p> <br />Should you have feedback concerning this post, submit remarks in the<strong> Remarks</strong> area below. In case you have questions concerning this write-up, <a href=”https://gaming console.aws.amazon.com/assistance/home” focus on=”_blank” rel=”noopener noreferrer”>contact AWS Assistance</the>.</p>
<p><strong>Want a lot more AWS Security news? Stick to us on <a name=”Twitter” href=”https://twitter.com/AWSsecurityinfo” focus on=”_blank” rel=”noopener noreferrer”>Twitter</the>.</strong>
<pre> <code> <!-- '"` -->
</code> </pre>
