Use AWS Firewall Supervisor to deploy protection from scale in AWS Organizations
Security teams which are in charge of securing workloads in a huge selection of Amazon Web Solutions (AWS) accounts in various organizational units shoot for a frequent approach across AWS Organizations. Key objectives include enforcing precautionary measures to mitigate recognized safety issues, having a main strategy for notifying the SecOps group about possible distributed denial of support (DDoS) assaults, and continuing to keep up compliance obligations. AWS Firewall Manager works at the organizational levels to help you reach your designed security posture although it provides reporting for non-compliant resources in every your AWS accounts. This article provides step-by-step guidelines to deploy and manage protection plans across your AWS Companies implementation through the use of Firewall Manager.
You may use Firewall Supervisor to centrally manage AWS WAF, AWS Shield Advanced, and Amazon Virtual Private Cloud (Amazon VPC) security organizations across all of your AWS accounts. Firewall Supervisor helps to protect sources across different accounts, also it can protect assets with particular tags or sources in several AWS accounts which are in particular organizational devices (OUs). With AWS Organizations, it is possible to centrally manage guidelines across a number of AWS accounts without needing to use custom made scripts and manual procedures.
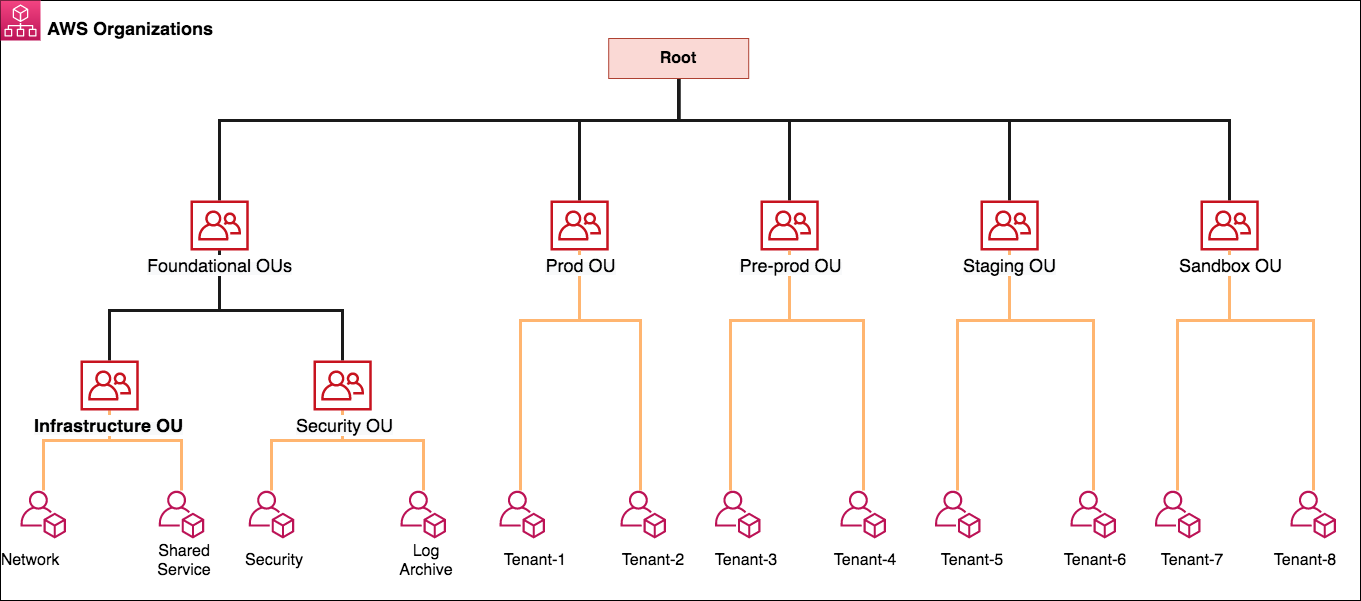
Architecture diagram
Figure 1 shows a good example organizational structure inside AWS Organizations, with several OUs that we’ll used in the example plan sets in this website post.

Figure 1: AWS Agencies and OU design
Firewall Manager could be connected to either the AWS grasp payer account or among the associate AWS accounts which has suitable permissions as a delegated administrator. Following the very best practices for organizational units, in this article we work with a dedicated Protection Tooling AWS accounts (named Safety inside the diagram) to use the Firewall Manager administrator deployment beneath the Security OU. The Protection OU can be used for hosting security-associated access and services. The Safety OU, its kid OUs, and the associated AWS accounts ought to be owned and handled by your security organization.
Firewall Manager prerequisites
Firewall Manager gets the using prerequisites that you need to complete before you create and apply a Firewall Supervisor policy:
- AWS Organizations: Your company should be using AWS Institutions to control your accounts, and All Features should be enabled. To find out more, see Creating an organization and Enabling all features in your organization.
- A Firewall Manager administrator account: You need to designate among the AWS accounts inside your organization because the Firewall Supervisor administrator for Firewall Supervisor. Thus giving the account authorization to deploy security plans over the organization.
- AWS Config: You need to allow AWS Config for several of the accounts inside your organization in order that Firewall Manager may detect newly created assets. Make it possible for AWS Config for several of the accounts in your company, use the Enable AWS Config template from the StackSets sample templates.
Deployment of safety policies
In the next sections, we clarify how exactly to create AWS WAF rules, Shield Advanced protections, and Amazon VPC security groupings through the use of Firewall Manager. We more explain ways to deploy these different plan types to protect sources across your accounts in AWS Businesses. Each Firewall Manager plan is specific to a person resource kind. If you need to enforce multiple plan sorts across accounts, you need to create multiple policies. It is possible to create several policy for every type. If you put in a new accounts to a business that you made up of AWS Organizations, Firewall Supervisor automatically applies the plan to the resources for the reason that account which are within scope of the plan. It is a scalable method to help you in deploying the required configuration when designers create resources. For example, it is possible to create an AWS WAF plan that will create a known group of AWS WAF guidelines being deployed whenever somebody creates an Amazon CloudFront distribution.
Plan 1: Create and manage security groups
You may use Firewall Manager to centrally configure and manage Amazon VPC security groups across all of your AWS accounts in AWS Organizations. A previous AWS Security blog post walks you through how exactly to apply common security team rules, audit your protection groups, and detect unused and redundant rules inside your security organizations across your AWS atmosphere.
Firewall Supervisor automatically audits new assets and rules as clients add resources or safety group rules with their accounts. It is possible to audit overly permissive protection group rules, such as for example rules with an array of ports or Classless Inter-Domain Routing (CIDR) ranges, or rules which have allowed all protocols to gain access to resources. To audit safety group policies, you may use software and protocol lists to specify what’s permitted and what’s denied by the policy.
In this website post, we work with a security plan to audit the protection groupings for overly permissive tips and high-danger applications that get to available to local CIDR ranges (for instance, 10.0.0.0/8, 192.168.0.0/16, 172.16.0.0/12). We made a custom application listing named Bastion Host for slot 22 and a custom made protocol list named Allowed Protocol which allows the child accounts to create rules just on TCP protocols. Refer link for how exactly to develop a custom managed application and protocol list.
To create audit safety group policies
- Sign into the Firewall Supervisor delegated administrator account. Demand Firewall Manager system. In the left routing pane, under AWS Firewall Manager, select Security guidelines.
- For Area, choose the AWS Area where you want to protect the sources. FMS region choice is on the services page fall down tab. In this illustration, we chosen the Sydney (ap-southeast-2) Region because just about everyone has of our assets in the Sydney Area.
- Create the plan, and in Plan details, choose Security group. For Region, select a Area (we chosen Sydney (ap-southeast-2)), and choose Next then.
- For Security group policy kind, choose Auditing and enforcement of protection group guidelines, and choose Next.
- Enter a policy title. We named our plan AWS_FMS_Audit_SecurityGroup.
- For Policy rule options, because of this example, we chose Configure managed audit plan rules.
- Under Plan rules, pick the following:
- For Protection group guidelines to audit, choose Inbound Guidelines.
- For Guidelines, choose the following:
- Select Audit over permissive safety group rules.
- For Allowed security group guidelines, choose Put Protocol checklist and choose the custom protocol listing Allowed Protocols that people created earlier.
- For Denied security group guidelines, select Deny guidelines with the allow ‘ALL’ protocol.
- Select Audit risky applications.
- Choose Applications that may only access nearby CIDR ranges. After that choose Add program list and choose the custom application checklist Bastion host that people created earlier.
- Select Audit over permissive safety group rules.
- For Policy action, for the instance in this article, we chose Auto remediate any noncompliant sources. Choose Following.

Figure 2: Policy guidelines for the security team audit policy
- For Policy scope, pick the following choices for this example:
- For AWS accounts this plan applies to, choose Include just the specified accounts and organizational device. For Included Organizational units, select OU (illustration – Non-Prod Accounts).
- For Reference type, select EC2 Instance, Security Group, and Elastic Network Interface.
- For Resources, choose Include all assets that match the chosen resource type.
- You can make tags for the protection policy. In the instance in this article, Tag Key is defined to Firewall_Supervisor and Tag Worth is defined to Audit_Safety_group.
Important: Migrating AWS accounts in one organizational unit to some other won’t remove or even detach the prevailing security group plan applied by Firewall Supervisor. For example, in the reference architecture in Figure 1 we’ve the AWS accounts Tenant-5 beneath the Staging OU. We’ve created another Firewall Manager security team plan for the Pre-Prod OU and Prod OU. If you proceed the Tenant-5 accounts to Prod OU from Staging OU, the resources connected with Tenant-5 will continue steadily to have the safety group policies which are described for both Prod and Staging OU if you don’t select or else before relocating the AWS accounts. Firewall Supervisor supports the detach choice in the event of policy deletion, because shifting accounts over the OU could have unintended impacts such as for example lack of connectivity or protection, and therefore Firewall Supervisor won’t take away the security group.
Plan 2: Managing AWS WAF v2 policy
A Firewall Manager AWS WAF plan contains the rule organizations that you want to use to your resources. Once you apply the policy, Firewall Supervisor creates a Firewall Supervisor web access control listing (internet ACL) in each accounts that’s within the plan scope.
Note: Creating Amazon Kinesis Data Firehose delivery stream is a prerequisite to control the WAF ACL logging at Stage 8 in us-east-1. (example – aws-waf-logs-lab-waf-logs)
To develop a Firewall Supervisor – AWS WAF v2 plan
- Sign into the Firewall Supervisor delegated administrator account. Demand Firewall Manager gaming console. In the left routing pane, under AWS Firewall Manager, choose Security plans.
- For Area, decide on a Region. FMS area choice is on the assistance page fall down tab. Because of this illustration, we selected the spot as Global, because the policy would be to protect CloudFront resources.
- Create the plan. Under Policy information, choose AWS WAF and for Area, choose Worldwide. Choose Next then.
- Enter a policy title. We named our plan AWS_FMS_WAF_Rule.
- On the Policy rule web page, under Web ACL configuration, add guideline groupings. AWS WAF supports custom rule groups (the client creates the guidelines), AWS Managed Rules principle organizations (AWS manages the guidelines), and AWS Marketplace managed rule groupings. For this instance, we chose AWS Managed Guidelines rule groups.
- For this illustration, for First guideline groups, we find the AWS Managed Rules principle group, AWS Core guideline set. For Last rule groups, we find the AWS Managed Rules principle group, Amazon IP reputation checklist.
- For Default web ACL actions for requests that don’t match any guidelines in the net ACL, select a default activity. We chose Allow.
- Firewall Supervisor enables logging for a particular internet ACL. This logging will be applied to all of the in-scope accounts and delivers the logs to a centralized solitary account. Make it possible for centralized logging of AWS WAF logs:
- For Logging configuration status, choose Enabled.
- For IAM role, Firewall Manager creates an AWS WAF service-part for logging. Your protection account should have the required IAM permissions. Learn more about access requirements for logging.
- Choose Kinesis stream created previously called aws-waf-logs-lab-waf-logs within us-east-1 as we’re making use of Cloudfront as a source within the policy.
- For Redacted fields, because of this example select HTTP method, Query String, URI, and Header. You can even put in a new header. To learn more, see Configure logging for an AWS Firewall Manager AWS WAF policy.
- For Policy action, because of this instance, we chose Auto remediate any noncompliant sources. To displace the prevailing web ACL that’s currently linked to the resource, select Replace internet ACLs which are currently connected with in-scope assets with the net ACLs developed by this policy. Choose Next.
Note: In case a resource comes with an association with another internet ACL that’s managed by way of a different active Firewall Supervisor, it doesn’t impact that resource.

Figure 3: Policy guidelines for the AWS WAF safety policy
- For Policy scope, pick the following choices for this example:
- For AWS accounts this plan applies to, choose Include just the specified accounts and organizational device. For Included organizational units, select OU (illustration – Pre-Prod Accounts).
- For Useful resource type, choose CloudFront distribution.
- For Resources, choose Include all sources that match the chosen resource type.
- You can make tags for the protection policy. For the instance in this article, Tag Key is defined to Firewall_Supervisor and Tag Worth is defined to WAF_Plan.
- Review the security plan, and choose Create Plan.
Note: For the AWS WAF v2 policy, the net ACL pushed by the Firewall Supervisor can’t become modified on the average person account. The account proprietor can only put in a new rule group.
- Within the policy’s 1st and last rule organizations sets, you can include additional rule groups in the linked AWS accounts level to supply additional security predicated on application requirements. You may use managed rule groupings, which AWS Managed Rules and AWS Marketplace retailers create and keep maintaining for you. For instance, you may use the WordPress app rule group, which contains guidelines that block request designs linked to the exploitation of vulnerabilities particular to a WordPress web site. You may also manage and use your personal rule groups.For more info about most of these choices, see Rule groups. Another illustration could be utilizing a rate-based guideline that tracks the price of requests for every originating Ip, and triggers the principle motion on IPs with prices that review a limit. Learn more about rate-based rules.
Plan 3: Managing AWS Shield Advanced policy
AWS Shield Advanced is really a paid service that delivers additional protections for web facing applications. Should you have Company or Enterprise support, it is possible to engage the 24X7 AWS DDoS Response Group (DRT), who is able to write rules in your stead to mitigate Layer 7 DDoS episodes. Please refer Shield Advanced prices for more information before proceeding with Shield FMS Plan.
Once you complete the prerequisites which were outlined in the prerequisites section, we’ll create Shield Advanced plan which provides the accounts and assets that you want to safeguard with Shield Advanced. Reason for this policy would be to activate the AWS Shield Advanced in the Accounts in OU’s scope and include the selected sources under Shield Advanced security list.
To develop a Firewall Supervisor – Shield Advanced plan
- Sign into the Firewall Supervisor delegated administrator account. Demand Firewall Manager system. In the left routing pane, under AWS Firewall Manager, choose Security guidelines.
- For Area, choose the AWS Area where you wish to protect the assets. FMS region choice is on the program page fall down tab. In this article, we’ve chosen the Sydney (ap-southeast-2) Region because our resources come in the Sydney Area.
Note: To safeguard CloudFront resources, choose the Global option.
- Create the plan, and in Plan details, choose AWS Shield Advanced. For Region, decide on a Region (instance – ap-southeast-2), and choose Next.
- Enter a policy title. We named our plan AWS_FMS_ShieldAdvanced Rule.
- For Policy action, for the illustration in this article, we chose Auto remediate any non-compliant resources. On the other hand, in the event that you choose Create but usually do not use this plan to existing or brand new resources, Firewall Supervisor doesn’t utilize Shield Advanced defense to any resources. You need to apply the plan to resources later. Choose Next.
- For Policy scope, this example utilizes the OU structure because the container of several accounts with similar needs:
- For AWS accounts this plan applies to, choose Include just the specified accounts and organizational products. For Included organizational units, select OU (instance – Staging Accounts OU).
- For Source type, select Application Load Balancer and Elastic IP.
- For Resources, choose Include all sources that match the chosen resource type.

Determine 4: Policy scope web page for producing the Shield Advanced safety policy
Note: In order to protect only the assets with specific tags, or even alternatively exclude sources with specific tags, choose Make use of tags to include/exclude assets, enter the tags, and choose either Include or Exclude. Tags allow you to categorize AWS sources in different ways, for instance by indicating a host, owner, or group to add or exclude in Firewall Supervisor policy. Firewall Manager brings together the tags with “AND” in order that, if you add several tag to an insurance plan scope, a resource will need to have all of the specified tags to end up being included or excluded.
Important: Shield Advanced supports safety for Amazon Route 53 and AWS Global Accelerator. However, security for these resources can’t be deployed by using Firewall Manager security plan at this time. If you want to protect these assets with Shield Advanced, you need to use individual AWS account entry through the API or gaming console to activate Shield Advanced defense for the intended sources.
- You can make tags for the protection policy. In the illustration in this article, Tag Key is defined to Firewall_Supervisor and Tag Worth is defined to Shield_Advanced_Policy. You may use the tags in the Reference component of IAM permission plan statements to either allow or deny customers to create changes to security plan.
- Review the security plan, and choose Create Plan.
Today you’ve successfully created a Firewall Manager security policy. Utilizing the organizational systems in AWS Companies as a strategy to deploy the Firewall Supervisor security policy, when a merchant account is added by one to the OU or even to any of its kid OUs, Firewall Supervisor applies the plan to the brand new account automatically.
Important: You don’t have to manually subscribe Shield Advanced on the associate accounts. Firewall Supervisor subscribes Shield Advanced about the known associate accounts within creating the policy.
Operational visibility and compliance report
Firewall Manager supplies a centralized incident notification for DDoS incidents which are reported simply by Shield Advanced. It is possible to create an Amazon SNS subject to keep track of the protected assets for potential DDoS routines and send notifications accordingly. Learn how exactly to create an SNS topic. In case you have resources in various Regions, the SNS subject needs to be produced in the intended Area. You must perform this task from the Firewall Supervisor delegated AWS account (for instance, Security Tooling) to get alerts across your AWS accounts for the reason that organization.
As a best exercise, you need to set up notifications for all your Regions where a creation is had by you workload under Shield Advanced safety.
To create an SNS subject in the Firewall Supervisor administrative console
- Within the AWS Management System, register to the Protection Tooling account or even the AWS Firewall Supervisor delegated administrator accounts. In the left routing pane, under AWS Firewall Manager, choose Settings.
- Choose the SNS subject that you intended to be utilized for the Firewall Supervisor central notification mechanism previously. For this instance, we created a fresh SNS subject in the Sydney Area (ap-southeast-2) named SNS_Subject_Syd.
- For Recipient email address, enter the e-mail deal with that the SNS subject will be sent to. Choose Configure SNS configuration.
Once you create the SNS configuration, the SNS is seen by you topic in the correct Region, as in the next example.
![]()
Figure 5: An SNS subject for centralized incident notification
AWS Shield Advanced information metrics in Amazon CloudWatch to keep track of the protected sources and will also create Amazon CloudWatch alarms. For the simplicity objective the e-mail was taken by us notification route because of this example. In security operations atmosphere, you need to integrate the SNS notification to your present ticketing pager or program duty for Realtime reaction.
Important: You can even utilize the CloudWatch dashboard to keep track of potential DDoS action. It collects and procedures raw information from Shield Advanced into readable, near real-period metrics.
It is possible to automatically enforce plans on AWS resources which exist or are created later on currently, to be able to promote compliance with firewall guidelines over the organization. For several policies, you will see the compliance position for in-scope accounts and assets utilizing the API or AWS Command Line Interface (AWS CLI) technique. For content audit safety group policies, you will see detailed violation information for in-scope resources also. This information might help one to understand and manage your risk of security better.
View all the guidelines in the Firewall Supervisor administrative account
For our illustration, we created three security plans in the Firewall Manager delegated administrator account. We are able to check policy compliance standing for several three policies utilizing the AWS Management Gaming console, AWS CLI, or API methods. The AWS CLI instance that follows could be further extended to create an automation for notifying the non-compliant resource proprietors.
To list all of the policies in FMS
Now, the plan was got simply by us id to check on the compliance status
For the preceding plan, associate account 444444444444 associated to the plan is compliant. The next example shows the position for the next policy.
For the preceding plan, associate account 555555555555 associated to the plan is non-compliant.
To supply detailed compliance information regarding the specified member accounts, the output includes sources which are in and away of compliance with the specified plan, as shown within the following example.
In the preceding illustration, two Application Load Balancers (ALBs) aren’t of a web ACL. It is possible to further introduce automation through the use of AWS Lambda features to isolate the non-compliant resources or result in an alert for the accounts owner to launch guide remediation.
Resource Clean up
It is possible to delete a Firewall Supervisor plan by performing the next steps.
To delete an insurance plan (console)
- In the routing pane, choose Safety policies.
- Choose the option close to the plan you want to delete. We developed 3 policies which must be removed one at a time.
- Choose Delete.
Important: Once you delete a Firewall Supervisor Shield Advanced plan, the plan is deleted, however your accounts remain subscribed to Shield Advanced.
Conclusion
In this article, you learned ways to use Firewall Manager to enforce necessary preventative policies from the central delegated AWS accounts managed by your security group. It is possible to extend this technique to all or any AWS OUs to meet up your own future needs as fresh AWS accounts or assets get put into AWS Organizations. A central notification shipping to your Security Functions team is crucial from the visibility perspective, sufficient reason for assistance from Firewall Manager it is possible to build a scalable method of stay protected, well informed, and compliant. Firewall Supervisor simplifies your AWS WAF, AWS Shield Advanced, and Amazon VPC protection group management and maintenance duties across several accounts and resources.
For further updates and reading through, start to see the Firewall Manager Developer Guide.
For those who have feedback concerning this post, submit remarks in the Comments section below. When you have questions concerning this post, start a brand-new thread on the AWS Firewall Manager forum or contact AWS Support.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.
