Understanding Container Images, Component 1: Image Layers
You’re probably using containers for the development work (and when you aren’t – you need to really contemplate it). They behave therefore to presenting a customized virtual device close, with nearly instant-on startup that it’s an easy task to forget they’re not necessarily virtual machines… nor ought to be treated as one!.
I prefer to believe on container images much less a virtual device, but as a (very advanced) packaging program with good dependency monitoring. It helps to believe you’re just packaging several files… what’s had a need to make the application run just.
Let’s take a look at some examples and make an effort to look from our build levels with another perspective.
Hello globe app – Consider 1
I want to create my C ‘Hello planet’ application. Since on desktop computer I take advantage of ubuntu, I feel convenient with that distribution, so my 1st impulse is make an effort to mimic my regular growth environment just.
That is my first attempt:
I shall create a good ‘app’ directory, add my source program code right now there, and create my Dockerfile.
|-- Dockerfile
`-- app
`-- hello.c
My hello entire world C program:
#consist of
int main(void)
printf("Hello from the container!n");
return (0);
In my own Dockerfile, I’ll do what I’d do on our desktop system:
- Start with the base image
- Add the deals I (roughly) require
- Add my supply code
- Build
- Run!
Dockerfile FROM ubuntu:18.04 RUN apt-get update RUN apt-obtain install -y build-essential WORKDIR /app COPY app/hi there.c /app/ RUN gcc -o hi hello.c ENTRYPOINT [ "/app/hi there" ]
Let’s construct it:
$ docker develop -t stage0 . Action 1/7 : FROM ubuntu:18.04 18.04: Pulling from library/ubuntu f22ccc0b8772: Pull complete 3cf8fb62ba5f: Pull complete [... a complete large amount of output ...] $ docker run stage0 Hello from the container!
Great! We’ve our program working! But, let’s discover what occurred behind the scenes.
You can see for every relative line inside our Dockerfile, docker prints a ‘Step’ accompanied by a hash.
What’s that hash? Continue reading to discover it…
Layered filesystems
Among the core areas of the container images is founded on the layered filesystem they’re.
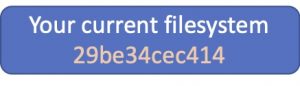
Let’s imagine the snapshot is taken by all of us of one’s hard drive since it is now. The hash of the filesystem contents can be noted: 29be…. with this example.

What goes on when some documents are added by one to it? (let’s state your hello.c file). In the entire situation of the filesystem of one’s computer, it’s simply added there. It’s not possible to differentiate it from any document on your hard disk drive.
On a layered filesystem, however, this is exactly what you get:

You truly have two components here:
- The disk since it before was.
- The change you did
It may not appear to be a big difference, but it is really!
Let’s observe how container images utilize this concept to accomplish some magic.
Docker build procedure
Considering our Docker build procedure, this is exactly what we saw:
$ docker create -t stage0 . Sending construct context to Docker daemon 77.31kB Phase 1/7 : FROM ubuntu:18.04 18.04: Pulling from library/ubuntu f22ccc0b8772: Pull complete 3cf8fb62ba5f: Pull complete e80c964ece6the: Pull complete Digest: sha256:fd25electronic706f3dea2a5ff705dbc3353cf37f08307798f3e360a13e9385840f73fb3 Status: Downloaded newer picture for ubuntu:18.04 ---> 2c047404e52d Step 2/7 : Operate apt-get update ---> Operating in a8d65ab87a93 Get:1 http://archive.ubuntu.com/ubuntu bionic InRelease [242 kB] Get:2 http://security.ubuntu.com/ubuntu bionic-safety InRelease [88.7 kB] ... Fetched 21.8 MB in 20s (1078 kB/s) Reading package lists... Removing intermediate container the8d65ab87a93 ---> fcdd591c3bfd Step 3/7 : Operate apt-get install -y build-essential ---> Working in c15a1c650b0a Reading package lists... Building dependency tree... ... Digesting triggers for libc-bin (2.27-3ubuntu1.3) ... Eliminating intermediate container c15a1c650b0a ---> 9fbbc8093ab5 Stage 4/7 : WORKDIR /app ---> Operating in fed79856ded7 Getting rid of intermediate container fed79856ded7 ---> 8bec0c4a2826 Step 5/7 : Duplicate app/hi.c /app/ ---> 5bf5977f4128 Step 6/7 : Operate gcc -o hello hi there.c ---> Running in 48c0f7dc9fcb Removing intermediate container 48c0f7dc9fcb ---> 8a99d3e111df Action 7/7 : CMD [ "/app/hello" ] ---> Running in 2cc8c55e417b Removing intermediate container 2cc8c55e417b ---> 87a0electronic7eb81da Successfully built 87a0e7eb81da Successfully tagged stage0:latest $
Each correct time docker executes a fresh line in the dockerfile, it creates a fresh layer with the full total consequence of executing that line. It adds that coating to the docker picture then, but it monitors all of the individual layers as cache furthermore. This technique took around 2 mins on my computer.
Looking at the pictures on docker I start to see the image I based through (ubuntu:18 now.04) and my last image: ‘phase0’ – with the hash that I actually saw on the construct log: 87a0e7eb81dthe
$ docker image ls REPOSITORY TAG Picture ID CREATED SIZE stage0 latest 87a0electronic7eb81da 4 minutes ago 319MB ubuntu 18.04 2c047404e52d 7 weeks hence 63.3MB $
The stage0 image is manufactured upon the next layers

docker picture will automagically hide the intermediate pictures, but they’re stored indeed. If you run docker picture ls -a, you’ll find every one of them:
$ docker image ls -a
REPOSITORY TAG Picture ID CREATED SIZE
stage0 latest 87a0electronic7eb81da 4 minutes ago 319MB
5bf5977f4128 4 a few minutes ago 319MB
8bec0c4a2826 4 minutes ago 319MB
8a99d3e111df 4 minutes ago 319MB
9fbbc8093ab5 4 moments ago 319MB
fcdd591c3bfd five minutes ago 98.2MB
ubuntu 18.04 2c047404e52d 7 weeks hence 63.3MB
You can also start to see the size of every image: Base ubuntu is 63 Mb, that visited 98 when it executed
RUN apt-find update
also to 319 Mb when it ran again
RUN apt-have install -y build-necessary
Exactly what will happen if the program code is changed by you you need to compile (your hello.c program)?
In the event that you were deploying a virtual device, it would mean you need to get your complete build atmosphere again – remember you’re beginning with a lean ubuntu device.
Using containers, in the event that you change your C plan and again construct, this is exactly what you get:
Hello.c
#consist of
int main(void)
printf("Hello from the container! - Second versionn");
return (0);
$ docker develop -t stage0 . Sending create context to Docker daemon 77.31kB Phase 1/7 : FROM ubuntu:18.04 ---> 2c047404e52d Step 2/7 : Work apt-get update ---> Using cache ---> fcdd591c3bfd Step 3/7 : Work apt-get install -y build-essential ---> Using cache ---> 9fbbc8093ab5 Stage 4/7 : WORKDIR /app ---> Using cache ---> 8bec0c4a2826 Step 5/7 : Duplicate app/hi.c /app/ ---> 3853b3aff546 Step 6/7 : Work gcc -o hello hi there.c ---> Running in 580c3f378281 Removing intermediate container 580c3f378281 ---> 583b361ff9a2 Action 7/7 : CMD [ "/app/hello" ] ---> Working in a2d18fe0c6b9 Removing intermediate container the2d18fe0c6b9 ---> 8fb6676c5b38 Successfully built 8fb6676c5b38 Successfully tagged stage0:latest
You will notice a couple of things:
- This was Considerably faster. First run got about two mins. This 2nd run took 10 mere seconds
- It didn’t print the consequence of all of the apt-get lines
The reason being docker noticed until line 4, the consequence of each one of the lines will be the same as it offers cached exactly. How does it end up being known by it? It’s tracking the level it starts from, and the scheduled system it was run. It knows the effect must be the identical to before then, so that it avoids executing it and reuses the coating that has been built before just.

Exploring images
There are some tools that allows one to explore container images. I strongly suggest spending time exploring your images to comprehend the magic that’s going on fully!
A fantastic tool is Dive
You’re allowed by this tool to explore what sort of particular image was built, what changed on the filesystem on each one of the layers, the command that has been used to make a layer, etc.
Let’s explore our image:
$ dive stage0:latest Image Source: docker://phase0:latest Fetching image... (this may have a while for large pictures)
Caveats building Dockerfiles
There are some important aspects right here, that you’ll want to consider when creating Dockerfiles:
- Dockerfile idempotency
- Amount of layers
- Dockerfile order
Dockerfile idempotency
Docker assumes that applying exactly the same order to a graphic produces exactly the same output, apart from ADD or COPY commands. For ADD or COPY, Docker shall check out the hash of the data files being copied. If they are exactly like applied to the build producing the layer, the step can be used and skipped from cache. While this ongoing functions fine quite often, it will fail if you make an effort to get any powerful details from the container while it’s getting built. For instance, this Dockerfile:
FROM ubuntu:18.04 WORKDIR /app Work cp /proc/uptime /app/build_uptime CMD ["/bin/bash", "-c", "cat /app/construct_uptime"]
$ docker develop -t uptime . Sending create context to Docker daemon 2.048kB Phase 1/4 : FROM ubuntu:18.04 ---> 2c047404e52d Stage 2/4 : WORKDIR /app ---> Using cache ---> 3804acc82f3c Step 3/4 : Work cp /proc/uptime /app/build_uptime ---> Using cache ---> e6a794f1d69c Action 4/4 : CMD ["/bin/bash", "-c", "cat /app/build_uptime"] ---> Using cache ---> 00542cb52a4f Successfully built 00542cb52a4f Successfully tagged uptime:newest
$ docker run uptime 18946.11 111237.49 $
Reducing amount of layers
Each brand-new line in your Dockerfile will generate a fresh layer – That involves some overhead. If some instructions are coupled tightly, it may seem sensible to put them within an unique layer. For example, of doing instead
FROM ubuntu:18.04 RUN apt-get update RUN apt-find install -y build-necessary
FROM ubuntu:18.04 RUN apt-have upgrade && apt-obtain install -y build-essential
Making optimal usage of cache
In order to take advantage of the caching, it’s essential the relative line purchase in your Dockerfile. For example, if of using instead
FROM ubuntu:18.04 RUN apt-get update RUN apt-find install -y build-essential WORKDIR /app COPY app/hi.c /app/ RUN gcc -o hi there hello.c CMD [ "/app/hi" ]
FROM ubuntu:18.04 WORKDIR /app COPY app/hi there.c /app/ RUN apt-get update RUN apt-have install -y build-essential RUN gcc -o hi hello.c CMD [ "/app/hi there" ]
Each correct time you modify your source file, the layer at step three 3 changes – therefore from that true stage on, everything shall need to be rebuilt. Which means Docker will pull all of the compiler files each best time you modification anything on your own app!
Read only layers
All the layers created by a Dockerfile are read only They’re immutable -. This is needed, to allow them to be reused.
But, what happens whenever a docker is work by you container and transformation things in the filesystem?
Whenever a container is started simply by you, Docker takes all of the layers on your own image, and offers a new one along with it – That’s the read-write layer, and the main one containing all the modifications you do to your filesystem: File changes, document additions, file deletions.
In the event that you delete a document on your own container – you’re not changing the picture layers, you’re simply adding a ‘take note’ on your own read-write level stating ‘this document was deleted’.

Apart from getting read-write, that is clearly a regular layer that people can use for the own purposes. We are able to create a new picture with it even! Let’s perform an experiment:
Run the application as usual, yet let’s give it the name so it’s simpler to track:
$ docker operate -ti --title deleting_files stage0 bash root@4c1c0ee8492b:/app# ls -l total 16 -rwxr-xr-x 1 root root 8304 Jan 19 13:19 hello -rw-r--r-- 1 root root 115 Jan 19 13:18 hello.c
Let’s delete the application form and surface finish the container:
root@4c1c0ee8492b:/app# rm -rf * root@4c1c0ee8492b:/app# exit $
Let’s begin the container – once again; you don’t need to now provide a name.
$ docker operate -ti stage0 bash root@c2c5bcdbd95e:/app# ls -l total 16 -rwxr-xr-x 1 root root 8304 Jan 19 13:19 hello -rw-r--r-- 1 root root 115 Jan 19 13:18 hello.c root@c2c5bcdbd95e:/app# exit $
The files are noticed by you are back there – All the deletions we did went into that read-write layer. Since our container begins from the previous coating, any modification is dropped. This is exactly what makes containers excellent, since you begin from a known state usually!.
However, that read-write layer isn’t lost. It could be observed by us by performing
$ docker ps -a CONTAINER ID IMAGE Order CREATED STATUS PORTS NAMES c2c5bcdbd95e stage0 "bash" 2 minutes ago Exited (0) 2 minutes ago hopeful_villani 4c1c0ee8492b stage0 "bash" 4 minutes ago Exited (0) 4 minutes ago deleting_files $
As possible plainly see, in the event that you don’t give your container a genuine name, Docker shall opt for random one for you personally.
Getting the container ID, we are able to make its read-write level a regular one through the use of docker commit plus the container id:
$ docker commit c2c5bcdbd95e image_with_files_deleted sha256:f8ac6574cb8f23af018e3a998ccc9a793519a450b39ece5cbb2c55457d9a1482 $
$ docker image ls
REPOSITORY TAG Picture ID CREATED SIZ
image_with_documents_deleted latest f8ac6574cb8f 25 secs ago 319MB
f1eb9f11026f ten minutes ago 319MB
stage0 latest 87a0electronic7eb81da 25 minutes ago 319MB
ubuntu 18.04 2c047404e52d 7 weeks hence 63.3MB
It is a regular image now.. so we are able to run a container as a result:
$ docker operate -ti image_with_files_deleted bash root@92dcc85d241a:/app# ls -l total 0 root@92dcc85d241a:/app# exit
And surely, the files you can find not.
Being truly a regular image, you might push it to the remote repository and perform As a result in other Dockerfiles.
However, please think that before doing this twice. By pressing a read-write layer you’re hiding one fundamental factor – Nobody shall understand how this coating was generated! While which can be sometimes helpful (and we’ll explore it on another post), this is simply not everything you usually want.
On another post, I’ll dig even more on how we are able to use layers to help expand optimize docker builds.
For any relevant query or comment, please i want to know in the Comments Section below, or via Twitter or Linkedin
Furthermore check other great related content inside our Cisco Blogs:
https://blogs.cisco.com/datacenter/docker-and-the-rise-of-microservices
https://blogs.cisco.com/networking/application-hosting-on-catalyst-9000-series-switches
