Threat Developments: DNS Security, Part 1
Part 1: Top threat types
With regards to security, deciding where you can dedicate resources is essential. To take action, it’s essential to know very well what security issues are likely to crop up inside your corporation, and their potential influence. The task is that probably the most energetic threats change as time passes, because the prevalence of different assaults ebb and flows.
That’s where it becomes beneficial to know about the bigger trends on the threat scenery. Reading up on you could be informed simply by these trends in regards to what types of attacks are active. That real way, you’ll be much better positioned to determine where you can dedicate resources.
Our Risk Trends blog page series takes a consider the activity that people notice in the threat scenery and reviews on those styles. After examining topics like the MITRE ATT&CK framework , LOLBins , among others, this release shall appear at DNS traffic to malicious sites. This data originates from Cisco Umbrella , our cloud-native security service.
We’ll briefly appear at organizations all together, before drilling into the true amount of endpoints connecting to malicious sites. We’ll also look from malicious DNS activity-the real amount of queries malicious websites receive.
Overall, this may provide insight into just how many malicious e-mail links users are simply clicking, how much conversation RATs are usually performing, or if cryptomining action down is up or. Such details can inform on where you can dedicate sources, such as for example topics requiring security teaching or areas to create threat hunting playbooks.
Summary of analysis
We’ll look at DNS queries to domains that belong to certain types of malicious activity, and perhaps specific threats, january and December of 2020 among. While performing this evaluation we looked at a multitude of threat developments. We’ve selected to highlight the ones that a business is most most likely to come across, with a concentrate on the categories which are most active.
It’s worthy of noting that we’re deliberately not getting comprehensive comparisons across groups predicated on DNS activity only. The truth is that various threat varieties require varying levels of internet connectivity to be able to perform their malicious activities. Rather, we’ll look at specific categories, having an optical eye on what they increase and fall as time passes. We’ll drill further in to the data then, considering trends for specific threats which are known to interact.
To learn more on our methodology, start to see the Methodology section at the ultimate end of the blog.
Companies and malicious DNS exercise
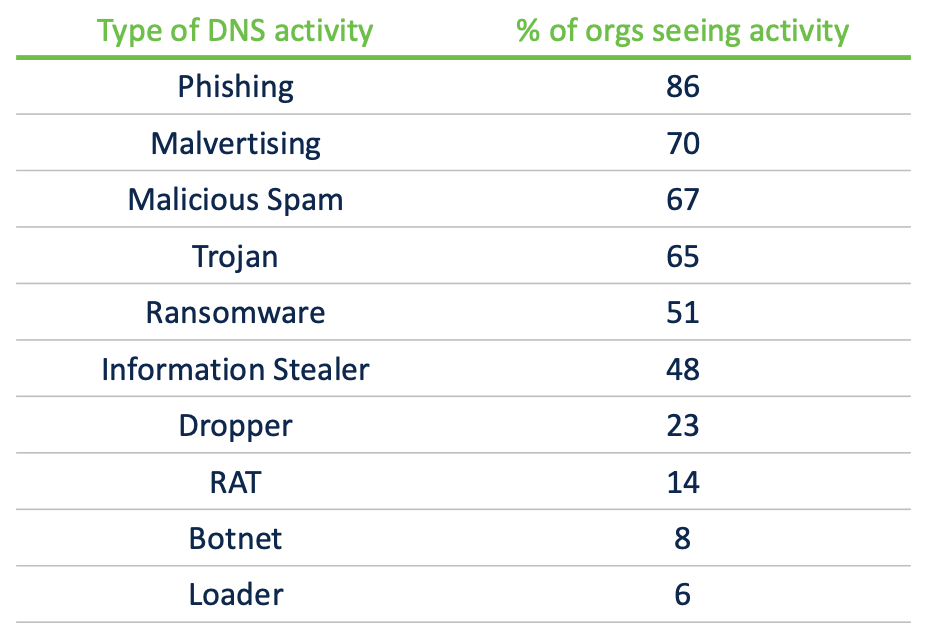
To begin, let’s look at organizations and how often they see traffic likely to sites involved within various kinds of malicious DNS activity. The next chart shows the percent of Cisco Umbrella clients that encountered each one of these categories.

To be very clear, this will not indicate that 86 percent of agencies received phishing emails. Instead, 86 percent of institutions had a minumum of one user try to hook up to a phishing web site, likely by simply clicking a web link in a phishing e-mail.
Similar stories promote themselves in other categories:
-
- 70 percent of businesses had users which were offered malicious browser advertisements.
-
- 51 % of companies encountered ransomware-related action.
-
- 48 % found information-stealing malware exercise.
Let’s have a closer look with some of the more frequent categories in further details, concentrating on two metrics: the amount of endpoints alerting to malicious action (depicted by range graphs in the next charts), and the quantity of DNS visitors seen for each kind of risk (shown by bar graphs inside the charts).
Cryptomining
It’s unsurprising that cryptomining generated probably the most DNS visitors out of anybody class. While cryptomining is frequently favored by poor actors for low-key revenue era, it’s fairly noisy on the DNS aspect, since it pings mining servers for even more work regularly.

The year cryptomining has been most active early inside, before declining till summer. This, the entire year and the gradual recuperation observed in the later section of, tracks with the worthiness of popular cryptocurrencies largely. As currency ideals increased, therefore did the rate of activity too. For instance, researchers inside Cisco Talos noticed a rise in exercise from the Lemon Duck danger starting inside late August.
It’s also worthy of noting that there’s little distinction is in between “legitimate” and illicit cryptomining traffic there. Some of the action in the chart could possibly be blocks based on plan violations, where customers attempted to mine electronic currencies using company assets. In this case, administrators would have justification for blocking like DNS activity.
Phishing
The year the quantity of phishing-related DNS activity was fairly stable throughout, of December with the exception, which saw a 52 percent increase round the holidays. With regards to the true amount of endpoints visiting phishing websites, during August plus September there have been significant increases.

This is because of large phishing campaign, between July and September where we visit a 102 percentage-point shift. More with this later, but also for now, observe the point that a lot more endpoints began simply clicking links in phishing email messages dramatically.
Trojans
Similar to cryptomining, The entire year strong trojans started. The incredibly lot of endpoints linking to Trojan websites was largely because of Ursnif/Gozi and IcedID-two threats recognized to function in tandem to provide ransomware. Inside January both of these threats alone comprised 82 % of Trojans seen in endpoints.
 However, from January were likely linked with a holiday-season marketing campaign by attackers the above-average numbers, the entire year progressed and declined and stabilized as.
However, from January were likely linked with a holiday-season marketing campaign by attackers the above-average numbers, the entire year progressed and declined and stabilized as.

July in late, Emotet emerged from its slumber once more , through September comprising an enormous level of traffic that grew. From August through September this threat on your own is in charge of the large upsurge in DNS activity. In every, 45 percent of agencies encountered Emotet.
Ransomware
The year for some of, two key ransomware threats dominated-one in breadth, another in depth.
 From April, the amount of computer systems compromised by Sodinokibi (a.k.a. REvil) more than doubled and continued to go up into autumn. The increase was significant that 46 percent of organizations encountered the threat enough. In September, of August general queries out of this particular ransomware family raised to five periods that, most likely indicating that the ransomware payload had been executed across most of the impacted systems.
From April, the amount of computer systems compromised by Sodinokibi (a.k.a. REvil) more than doubled and continued to go up into autumn. The increase was significant that 46 percent of organizations encountered the threat enough. In September, of August general queries out of this particular ransomware family raised to five periods that, most likely indicating that the ransomware payload had been executed across most of the impacted systems.

However, it is a drop within the bucket when compared to DNS exercise of Ryuk, that is in charge of the November-December spike in activity largely. (It had been so higher that it skewed general activity for all of those other year, leading to below-average quantities when it wasn’t energetic.) The true amount of endpoints linking to Ryuk-related domains remained fairly small and consistent over summer and winter, only showing modest raises before query action skyrocketed.
So, while one risk corrals more endpoints, another is a lot busier. Interestingly, this comparison between your two ransomware threats correlates with the amount of cash that all threat reportedly tries to extort from sufferers. Sodinokibi will hit numerous endpoints, demanding an inferior ransom. Ryuk compromises less systems far, demanding a more substantial payment significantly.
Tying everything together
In today’s threat scenery, the theory that ‘ no-one can be an island ’ is true for threats. Probably the most prevalent attacks these full times leverage a number of threats at different stages. For example, let’s appearance at how Emotet is frequently delivered by phishing to be able to deploy Ryuk as a payload. As the data below addresses all phishing, Emotet, and Ryuk activity, instead of specific campaigns, an obvious pattern emerges.
 Keep in mind the 102 percentage-point change in phishing between July and September? This relative lines up with a 216 percentage-point jump in Emotet DNS activity. In October exercise drops off, accompanied by an eye-watering 480 percentage-point upsurge in Ryuk activity.
Keep in mind the 102 percentage-point change in phishing between July and September? This relative lines up with a 216 percentage-point jump in Emotet DNS activity. In October exercise drops off, accompanied by an eye-watering 480 percentage-point upsurge in Ryuk activity.
Emotet’s functions were significantly disrupted in January 2021 , that will likely result in a drop-off in exercise for this specific threat chain. Nevertheless, the partnership presented will probably be worth considering, as other danger actors follow similar styles.
If you discover one threat inside your network, it’s smart to investigate what threats have already been observed employed in tandem with it and get precautionary measures to avoid them from leading to further havoc.
For illustration, if you discover evidence of Ryuk, however, not Emotet, it might be worth searching for Trickbot as well. Both Trickbot and Emotet have already been observed deploying Ryuk in episodes, sometimes in coordination, along with other times separately.
Sure enough, The year trickbot follows a similar pattern in terms of DNS activity-lower in the first half of, inside August and September hectic, in October then quiet. However, Between November and December trickbot was energetic, when Emotet had not been, likely adding to the phenomenal upsurge in Ryuk activity of these two months.
 Preventing prosperous attacks
Preventing prosperous attacks
As mentioned earlier, the info used showing these trends originates from Cisco Umbrella , our cloud delivered security service which includes DNS protection, secure internet gateway, firewall, and cloud accessibility security broker (CASB) efficiency, and threat intelligence. In each one of these full cases, the malicious action was halted in its tracks by Umbrella. An individual who clicked on a phishing email has been unable to hook up to the malicious web site. The RAT wanting to speak to its C2 server had been unable to phone house. The illicit cryptominer couldn’t get function to mine.
Umbrella combines multiple safety functions into one remedy, so that you can extend security to devices, remote customers, and distributed places anywhere. Umbrella may be the easiest way to safeguard your users everywhere inside minutes effectively.
Also, if you’re seeking to get more information about the malicious domains your organization encounters, Umbrella Investigate provides most satisfactory view of the relationships and evolution of internet domains, IPs, and files – assisting to pinpoint attackers’ infrastructures and predict future threats. No other vendor offers the same level of interactive threat intelligence – exposing developing and current threats. Umbrella delivers the context you will need for faster incident reaction and investigation.
Desire to find out more?
Up following
In this website we looked at probably the most active threat categories observed in DNS traffic, along with how proof one threat can result in uncovering others. Partly two, we’ll break the info right down to examine which industries are targeted simply by these threats further. Stay tuned for more information about the effect on your industry!
Methodology
We’ve organized the info set to acquire overall month-on-30 days and percentages trends. We’ve aggregated the info by the amount of endpoints that possess attemptedto visit certain websites which have been flagged as malicious. We’ve furthermore aggregated the total amount of times sites flagged as malicious have already been visited. These true figures have already been grouped into meaningful risk categories and, when possible, have already been marked as getting of a particular threat.
We’ve also used filtering to eliminate certain information anomalies that may appear when considering malicious DNS visitors. For example, whenever a C2 infrastructure will be removed, compromised endpoints wanting to call back again to a sinkholed domain can generate huge amounts of traffic because they unsuccessfully try to connect. In situations like these, we’ve filtered out such information from the info set.
A variation can be used by the charts of the Z-score approach to statistical measurement, which describes a value’s connection to the mean. In this full case, of using the amount of regular deviations for comparison rather, we’ve shown the percent decrease or raise from the mean. We feel this gifts a more digestible evaluation for the common reader.
A word on personal privacy
Cisco seriously takes client privacy very. To help expand this final end, we’ve attended great lengths to make sure that the data useful for this blog series will be anonymized and aggregated before any evaluation is conducted on it. While Cisco Secure items can statement telemetry to us back again, that is an opt-in feature.

You must be logged in to post a comment.