Set up centralized supervising for DDoS events and auto-remediate noncompliant resources
Once you build applications upon Amazon Web Providers (AWS), it’s a common security practice to isolate production resources from non-production resources by logically grouping them into useful units or organizational devices. There are several benefits to this process, such as rendering it easier to put into action the principal of minimum privilege, or decreasing the scope of adversely impactful routines that could occur in non-production conditions. After building these programs, establishing monitoring for resource safety and compliance risks, such as for example distributed denial of assistance (DDoS) episodes across your AWS accounts, is as important just. The recommended best exercise to perform this kind of monitoring involves making use of AWS Shield Advanced with AWS Firewall Manager, and integrating these with AWS Security Hub.
In this website post, I demonstrate how to setup centralized supervising for Shield Advanced-protected sources across several AWS accounts through the use of Firewall Manager and Security Hub. This permits one to easily manage assets which are out of compliance from your own security policy also to view DDoS activities which are detected across several accounts within a view.
Shield Advanced is really a managed application protection service that delivers DDoS protection for the workloads against infrastructure level (Layer 3-4) attacks, along with application layer (Layer 7) attacks, through the use of AWS WAF. Firewall Manager is really a security management program that allows one to centrally configure and manage firewall guidelines across your accounts and applications within an organization within AWS. Security Hub consumes, analyzes, and aggregates security events made by your application running upon AWS by eating security findings. Security Hub integrates with Firewall Manager with no need for just about any action to be studied by you.
I’m likely to cover two various scenarios that demonstrate how exactly to use Firewall Supervisor for:
- Centralized presence into Shield Advanced DDoS occasions
- Automated remediation of noncompliant sources
Situation 1: Centralized presence of DDoS detected activities
This scenario represents a fully native and automated integration, where Shield Advanced DDoSDetected occasions (indicates whether the DDoS occasion is underway for a specific Amazon Resource Title (ARN)) are created visible as a safety finding in Protection Hub, through Firewall Supervisor.
Solution overview
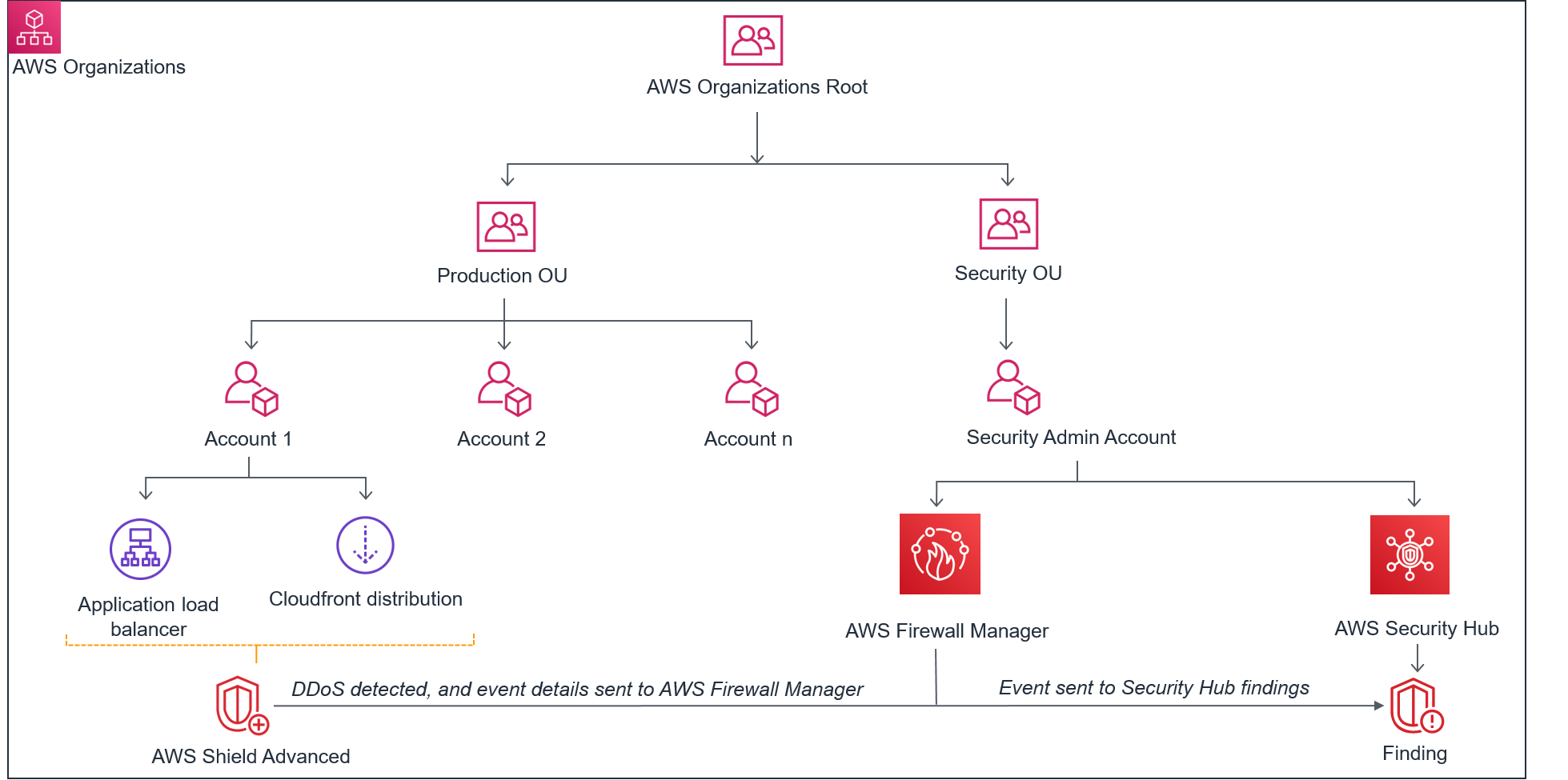
Figure 1 displays the perfect solution is architecture for scenario 1.

Figure 1: Situation 1 – Shield Advanced DDoS detected events noticeable in Security Hub
The diagram illustrates a person using AWS Organizations to isolate their creation resources in to the Production Organizational Device (OU), with further separation into multiple makes up about each one of the mission-critical apps. The resources in Accounts 1 are protected by Shield Advanced. The Safety OU was made to centralize security features across all AWS OUs and accounts, obscuring the presence of the production atmosphere resources from the Protection Operations Middle (SOC) engineers along with other security employees. The Security OU houses the designated administrator account for Firewall Manager and the Security Hub dashboard.
Scenario 1 execution
You will be establishing Security Hub within an account which has the prerequisite providers configured inside it as explained below. Before you proceed, start to see the architecture specifications within the next section. Safety Hub is enabled for the organization once, it is possible to simulate a DDoS occasion in stringent accordance with the AWS DDoS Simulation Testing Policy or use among AWS DDoS Test Partners.
Architecture requirements
To be able to implement these steps, you’ll want the following:
- An atmosphere with AWS Organizations configured. At the very least, an organization ought to be defined with at the very least two associate accounts. For additional information on establishing AWS Organizations, it is possible to review the AWS Organizations User Guide and your blog post Best Practices for Organizational Units with AWS Organizations.
- A Firewall Manager administrator accounts create with subscribed associate accounts. For additional information on setting up Supervisor administrator accounts Firewall, see AWS Firewall Manager prerequisites and your blog post Use AWS Firewall Manager to deploy protection at scale in AWS Organizations.
- AWS Config should be enabled within the accounts and Area where you possess Shield Advanced-protected assets you want to manage through the use of Firewall Manager. For managing Shield Advanced protected sources, you can elect to have AWS Config enabled on selected resource types, like a Shield Advanced-supported source.
- Shield Advanced should be enabled in every accounts you would like to monitor using Protection Hub and Firewall Supervisor.
You have each one of these requirements completed once, you can move ahead make it possible for Security Hub.
Enable Security Hub
Note: If you intend to protect assets with Shield Advanced across several accounts and in several Regions, we advise that you utilize the AWS Security Hub Multiaccount Scripts from AWS Labs. Safety Hub must be enabled in every the Areas and all of the accounts where you possess Shield protected sources. For global assets, like Amazon CloudFront, you need to enable Protection Hub in the us-east-1 Region.
To allow Security Hub
- In the AWS Security Hub console, change to the accounts you need to use because the designated Safety Hub administrator accounts.
- Select the protection standards or standard which are applicable to your program’s use-case, and choose Enable Security Hub.

Figure 2: Enabling Security Hub
- From the designated Protection Hub administrator account, visit the Settings – Accounts tab, and include accounts by delivering invites to all or any the accounts you need added as associate accounts. The invited accounts turn out to be associated as associate accounts once the proprietor of the invited accounts has recognized the invite and Safety Hub has been allowed. It’s achievable to upload a comma-separated set of accounts you wish to send out to invites to.

Figure 3: Designating a Protection Hub administrator account with the addition of member accounts
View detected activities in Safety and Shield Hub
When Shield Advanced detects signs of DDoS visitors that’s destined for a protected reference, the Events tab within the Shield console shows information regarding the event detected and a status upon the mitigation that is performed. Following can be an exemplory case of how this appears in the Shield gaming console.

Figure 4: Scenario 1 – The Events tab on the Shield console showing a Shield event in progress
If you’re managing multiple accounts, switching between these accounts to see the Shield console to help keep an eye on DDoS incidents could be cumbersome. Utilizing the Amazon CloudWatch metrics that Shield Advanced reports for Shield events, visibility across multiple accounts and Regions is simpler by way of a custom CloudWatch dashboard or by eating these metrics in a third-party tool. For instance, the DDoSDetected CloudWatch metric includes a binary value, in which a value of just one 1 indicates an event that could be a DDoS has been detected. This metric is updated by Shield once the DDoS event starts and ends automatically. You merely need permissions to gain access to the Security Hub dashboard to be able to monitor all events on production resources. Following can be an example of everything you see in the Security Hub console.

Figure 5: Scenario 1 – Shield Advanced DDoS alarm showing in Security Hub
Configure Shield event notification in Firewall Manager
In order to boost your visibility into possible Shield events across your accounts, you need to configure Firewall Manager to monitor your protected resources through the use of Amazon Simple Notification Service (Amazon SNS). With this particular configuration, Firewall Manager supplies you with notifications of possible attacks by creating an Amazon SNS topic in Regions where it’s likely you have protected resources.
To configure SNS topics in Firewall Manager
- In the Firewall Manager console, go directly to the Settings page.
- Under Amazon SNS Topic Configuration, decide on a Region.
- Choose Configure SNS Topic.

Figure 6: The Firewall Manager Settings page for configuring SNS topics
- Select a preexisting topic or develop a new topic, and choose Configure SNS Topic then.

Figure 7: Configure an SNS topic in a Region
Scenario 2: Automatic remediation of noncompliant resources
The second scenario can be an example when a new production resource is established, and Security Hub has full visibility of the compliance state of the resource.
Solution overview
Figure 8 shows the answer architecture for scenario 2.

Figure 8: Scenario 2 – Visibility of Shield Advanced noncompliant resources in Security Hub
Firewall Manager identifies that the resource has gone out of compliance with the defined policy for Shield Advanced and posts a finding to Security Hub, notifying your operations team a manual action must bring the resource into compliance. If configured, Firewall Manager can automatically bring the resource into compliance by creating it as a Shield Advanced-protected resource, and update Security Hub once the resource is in a compliant state.
Scenario 2 implementation
The next steps describe how exactly to use Firewall Manager to enforce Shield Advanced protection compliance of a credit card applicatoin that’s deployed to an associate account within AWS Organizations. This implementation assumes that you setup Security Hub as described for scenario 1.
Create a Firewall Manager security policy for Shield Advanced protected resources
In this step, a Shield is established by you Advanced security policy which will be enforced by Firewall Manager. For the purposes of the walkthrough, you’ll elect to automatically remediate noncompliant resources and apply the policy to Application Load Balancer (ALB) resources.
To create the Shield Advanced policy
- Open the Firewall Manager console in the designated Firewall Manager administrator account.
- In the left navigation pane, choose Security policies, and choose Create a security policy.
- Select AWS Shield Advanced because the policy type, and choose the spot where your protected resources are. Choose Next.
Note: You need to develop a security policy for every Region where you have regional resources, such as for example Elastic Load Elastic and Balancers IP addresses, and a security policy for global resources such as for example CloudFront distributions.

Figure 9: Choose the policy type and Region
- On the Describe policy page, for Policy name, enter a genuine name for the policy.
- For Policy action, you have the choice to configure automatic remediation of noncompliant resources or even to only send alerts when resources are noncompliant. This setting could be changed by you following the policy has been created. For the purposes of the post, I’m selecting Auto remediate any noncompliant resources. Select your option, and choose Next then.
Important: It’s a best practice to first identify and review noncompliant resources before you enable automatic remediation.
- On the Define policy scope page, define the scope of the policy by choosing which AWS accounts, resource type, or resource tags the policy ought to be put on. For the purposes of the post, I’m selecting to control Application Load Balancer (ALB) resources across all accounts in my own organization, without preference for resource tags. When you’re finished defining the policy scope, choose Next.

Figure 10: Define the policy scope
- Review and create the policy. Once you’ve reviewed and created the policy in the Firewall Manager designated administrator account, the policy will be pushed to all or any the Firewall Manager member makes up about enforcement. The brand new policy could use up to 5 minutes to surface in the console. Figure 11 shows an effective security policy propagation across accounts.

Figure 11: View security policies within an account
Test the Firewall Security and Manager Hub integration
You’ve defined an insurance plan to cover only ALB resources now, so the easiest way to check this configuration would be to create an ALB in another of the Firewall Manager member accounts. This policy causes resources within the policy scope to be added as protected resources.
To test the policy
- Switch to the Security Hub administrator account and open the Security Hub console in exactly the same Region where you created the ALB. On the Findings page, set the Title filter to Resource lacks Shield Advanced protection and set the Product name filter to Firewall Manager.

Figure 12: Security Hub findings filter
You should visit a new security finding flagging the ALB as a noncompliant resource, based on the Shield Advanced policy defined in Firewall Manager. This confirms that Security Firewall and Hub Manager have already been enabled correctly.

Figure 13: Security Hub with a noncompliant resource finding
- With the automatic remediation feature enabled, you need to start to see the “Updated at” time reflect once the automatic remediation actions were completed exactly. The completion of the automatic remediation actions may take up to five minutes to be reflected in Security Hub.

Figure 14: Security Hub having an auto-remediated compliance finding
- Go to the account where you created the ALB back, and in the Shield Protected Resources console, demand Protected Resources page, where in fact the ALB ought to be seen by you listed as a protected resource.

Figure 15: Shield console in the member account implies that the new ALB is really a protected resource
Confirming that the ALB has been added automatically as a Shield Advanced-protected resource implies that you have successfully configured the Firewall Manager and Security Hub integration.
(Optional): Send a custom action to a third-party provider
It is possible to send all regional Security Hub findings to a ticketing system, Slack, AWS Chatbot, a Security Information and Event Management (SIEM) tool, a Security Orchestration Automation and Response (SOAR), incident management tools, or even to custom remediation playbooks through the use of Security Hub Custom Actions.
Conclusion
In this website post I showed you how exactly to create a Firewall Manager security policy for Shield Advanced to enable you to monitor your applications for DDoS events, and their compliance to DDoS protection policies in your multi-account environment from the Security Hub findings console. Consistent with guidelines for account governance, organizations must have a centralized security account that performs monitoring for multiple accounts. Security Hub and Firewall Manager give a centralized solution to assist you to reach your compliance and monitoring goals for DDoS protection.
If you’re thinking about exploring how Shield Advanced and AWS WAF assist in improving the security posture of one’s application, take a look at the following resources:
- What’s new: AWS Shield Advanced proactive response
- Whitepaper: AWS GUIDELINES for DDoS Resiliency
- Blog post: Defense comprehensive using AWS Managed Rules for AWS WAF (part 1)
- Whitepaper: Guidelines for Implementing AWS WAF
When you have feedback concerning this post, submit comments in the Comments section below. When you have questions concerning this post, take up a new thread on the AWS Security Hub forum or contact AWS Support.
Want more AWS Security how-to content, news, and show announcements? Follow us on Twitter.

You must be logged in to post a comment.