Secure and Compliant Protection for Your Data
In the world of IT, the importance of maintaining a comprehensive security posture while adhering to compliance standards and requirements is growing every day. Attackers are consistently targeting backups as they know that disrupting an organization’s ability to recover can halt operations. From a business operations standpoint, secure and trusted recovery is paramount. But, as enterprises continue to rely increasingly on technology, IT departments find themselves at the forefront of safeguarding digital assets and becoming stakeholders in ensuring regulatory adherence.
As with many things when it comes to data protection and recovery, uncovering gaps in your plans after the fact can be catastrophic. Reviewing your best practices, security posture, and overall compliance was once something that was an occasional task. In the era of HIPPA, GDPR, and cyber-insurance, these checks need to be performed frequently and in a proactive manner. Veeam has always been committed to giving customers the tools and the advantages that they need to meet their goals, and that rings as true as ever with the enhancements and new features in Veeam Data Platform 23H2.
Guarantee Your Survival
With backups being a front-and-center target for attackers, you need to ensure that you do everything you can to fortify your defense. After all, if you cannot restore your data reliably, where does that leave your organization from an operations standpoint? With the recent release of Veeam Data Platform 23H2, Veeam has added several enhancements to help you proactively beat the odds when it comes to conquering a cyberattack.
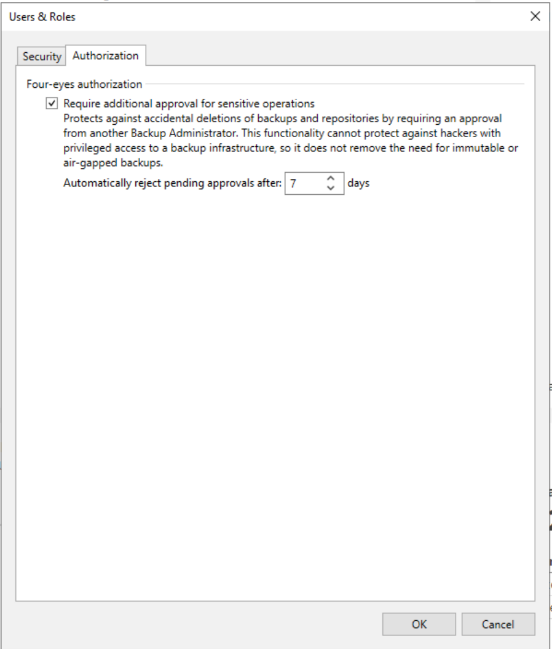
The Four-eyes principle, sometimes referred to as the two-person rule, while not a new concept, is one that has proven valuable over its history. In short, it requires two persons to authorize specific actions. Why is this important when we are talking about protecting your data? Starting with V12.1, you can enable Four-eyes authorization to prevent any single user account from performing destructive operations such as deleting backups or repositories. Additionally, actions such as adding new users will also invoke this mechanism. This powerful functionality is one more additional roadblock to preventing hackers from deleting your data, but it also provides safeguards against insider threats and accidental deletions.
When you apply this to existing safeguards such as multifactor authentication and immutability, you can work towards achieving a zero-trust architecture for your data protection. By invoking authorization challenges, employing encryption for communication and storage, and leveraging concepts such as immutability, enterprises can ensure that their invaluable data is retrievable in the face of a disaster.
Verify Security and Compliance
Adhering to compliance standards set forth by various governing bodies can be a daunting task. As is routinely verifying that all the current checks and measures are in place and configured correctly. Government-mandated regulatory compliance is not the only instance where violations can occur. Oftentimes, enterprises have their own requirements that may supplement or supersede those imposed by governing bodies. Cyber insurance policies are increasingly getting more well-defined as well. All of this cumulates to increased workloads for enterprise teams as they need to verify that all the required checks are being met.
One of the most popular features introduced in Veeam Backup & Replication v12 was the Best Practices Analyzer. Customers absolutely loved being able to perform critical checks at the click of the button. In true Veeam style, customer feedback was heard, and V12.1 introduced expanded checks, both in number and scope. The evolved now goes a step further – numerous checks are performed that align with data protection best practices and not just product configuration recommendations. Key best practices such as confirming immutable backups, adherence to the 3-2-1 Rule, or ensuring that email notifications are enabled can all be performed from a single spot. In situations where internal audits require regular reporting, scans can be scheduled automatically with results emailed.
Put the Spotlight on Cyberthreats
Risks to your business don’t just end at hacking attempts though. Failed backup jobs can lead to missed RPOs, which can lead to financial penalties or worse. Similarly, identifying trends can be an indication of a larger problem, but without a centralized view, these trends can be difficult to spot. Performing regular reviews for risks and trends can be a key proactive step to combatting threats. However, it can also be quite time-consuming.
When it comes to data protection, the is your single-stop dashboard to gather insights, assess risks, and rank priorities. Included in Veeam Data Platform Advanced and Premium edition, and powered by Veeam ONE’s advanced monitoring and analytics, the unified view is integrated and accessible within Veeam Backup & Replication, Veeam ONE, and Veeam Recovery Orchestrator.
With an at-a-glance view, you will be able to measure your security score, spot RPO anomalies, identify SLA compliance violations, and much more. Each of these widgets is customizable, allowing the dashboard to be tailored to display and measure the criteria that you need to ensure confidence in your data’s security.
Adopt the Radical Mindset
Resilience is about more than being able to cope with the unexpected. Rather, it is about withstanding or recovering from any problems or threats that may arise. It’s also a way to describe an object that can quickly spring back into shape – something that enterprises need to do when faced with a threat. Veeam can help achieve radical resiliency in the face of adversity by giving you the complete confidence you require in your protection, response, and recovery.
The relationship between security and compliance serves as the basis for the resilience and integrity of enterprises in today’s online world. As organizations navigate the complex terrain of cyberthreats and regulatory frameworks, the need to adopt a proactive stance cannot be overstated. Compliance adherence ensures that businesses operate within the bounds of legal and regulatory expectations, mitigating the risks associated with data breaches and potential legal ramifications.
Ultimately, the journey toward a secure and compliant IT environment is ongoing, requiring continual adaptation to emerging threats and evolving regulations. As technology advances, so too must the strategies employed by IT professionals to safeguard valuable data. By embracing the principles of security and compliance, corporate IT departments position themselves as stewards of not only digital assets but also the trust and confidence of clients, partners, and employees. The resilience of enterprises is tested daily, and the outcome can be the difference between surviving an attack or going out of business. Stack the odds in your favor: adopt a radical resilience methodology and let the Veeam Data Platform play a critical part in bridging the gap between your teams.




You must be logged in to post a comment.