Scaling cross-accounts AWS KMS-encrypted Amazon S3 bucket access using ABAC
This blog post demonstrates how to talk about encrypted Amazon Simple Storage space Service (Amazon S3) buckets across accounts on a multi-tenant data lake. Our goal is to display scalability over a more substantial quantity of accounts that may access the info lake, in a situation where there’s one central accounts to share from. Most use instances involve multiple organizations or customers that require to gain access to data across several accounts, making data lake options inherently multi-tenant. Therefore, it becomes essential to associate data property and set guidelines to manage these resources in a frequent way. The usage of indigenous AWS Important Management Support (AWS KMS) simplifies smooth integration with AWS solutions and will be offering improved data safety to ultimately enable information lake services (for instance, Amazon EMR , AWS Glue , or Amazon Redshift ).
Furthermore, this website post structures this process and enables bigger scale by applying an alternative solution to specifying the main element. The policy dimension limitation for Amazon S3 and AWS KMS plans is overcome by using an aws:PrincipalOrgID condition type in the problem policy. The post targets services that aren’t incorporated with AWS Lake Development; immediate access for S3 buckets is necessary for defining and enforcing entry control policies. For AWS providers that integrate with AWS Lake Development and honor Lake Development permissions, make reference to the Lake Formation Programmer Guide.
Become familiar with how exactly to use attribute-dependent access control (ABAC) being an authorization technique that defines permissions predicated on characteristics. ABAC reduces the amount of policies, because program tags are better to manage and set up a differentiation in work policies. Using ABAC together with Amazon S3 guidelines, it is possible to authorize users to learn objects based on a number of tags that are put on S3 objects also to the IAM part session of one’s users predicated on key-value set attributes, called program tags. The program tags will undoubtedly be passed when you presume an IAM function or federate a consumer (during your identity supplier) in AWS Protection Token Services (AWS STS). This permits administrators to configure a SAML-based identity service provider (IdP) to send particular employee features as tags in AWS. As a total result, it is possible to simplify the development of fine-grained permissions for workers to get access and then the AWS sources with coordinating tags.
For simplicity, in this solution you may be using an AWS Command Collection User interface (AWS CLI) obtain temporary protection credentials when producing a session. You’ll apply the worldwide aws:PrincipalOrgID condition type in your resource-based plans to restrict usage of accounts in your AWS business. It is possible to apply the wildcard personality * to the Principal condition important for broader applicability across your unique organization, and we’ll suggest additional regulates where feasible.
Cross-account accessibility
From the high-degree overview perspective, the next items are a starting place when allowing cross-account access. To be able to grant cross-account usage of AWS KMS-encrypted S3 items in Accounts A to a consumer in Account B, you’ll want the following permissions set up (goal A):
- The bucket policy in Account Essential grant usage of Account B
- The AWS KMS key policy in Account Essential grant access to an individual in Account B
- The AWS Identification and Access Administration (IAM) policy in Accounts B must grant an individual access to both bucket and type in Account A
By establishing these permissions, become familiar with how exactly to maintain entitlements (goal B) at the bucket or item level, explore cross-accounts bucket sharing at level, and overcome restrictions such as for example inline policy dimension or bucket policy quality (you can find out more information in the Policies summary area). As an expansion, you:
- Enable granular permissions
- Grant usage of sets of resources by tags
At this time in time, not absolutely all AWS services assistance tag-centered authorization, so you’ll level with innovation. Configuration choices could be demanding for cross-accounts access, particularly when the objective would be to scale across a lot of accounts to a multi-tenant information lake. This blog provides to orchestrate the many configurations options so that both goals A and B are usually met and difficulties are resolved.
Answer overview
Our goal would be to overcome challenges and style backwards with scalability at heart. The next table depicts the problems and outlines tips for a better style.
| Problem | Recommendation fine detail |
|---|---|
| Use worker attributes from your business directory | It is possible to configure your SAML-based or even web identity provider to pass session tags to AWS. Whenever your workers federate into AWS, their characteristics are put on their resulting principal in AWS. After that you can use ABAC to permit or deny permissions predicated on those features. |
| Enable granular permissions | ABAC requires fewer guidelines, because differentiation in work plans is given through program tags, which are simpler to manage. Permissions are given automatically predicated on attributes. |
| Grant usage of resources by tags | By using ABAC, it is possible to allow actions on almost all resources, but only when the resource tag fits the principal’s tag and/or the organization’s tag. It’s best exercise to grant minimum privilege. |
| Not absolutely all services assistance tag-based authorization | Look for support updates and design round the limitations. |
| Scale with development | ABAC permissions level with innovation, because it’s not essential for the administrator to up-date existing policies to permit access to new assets. |
Architecture overview

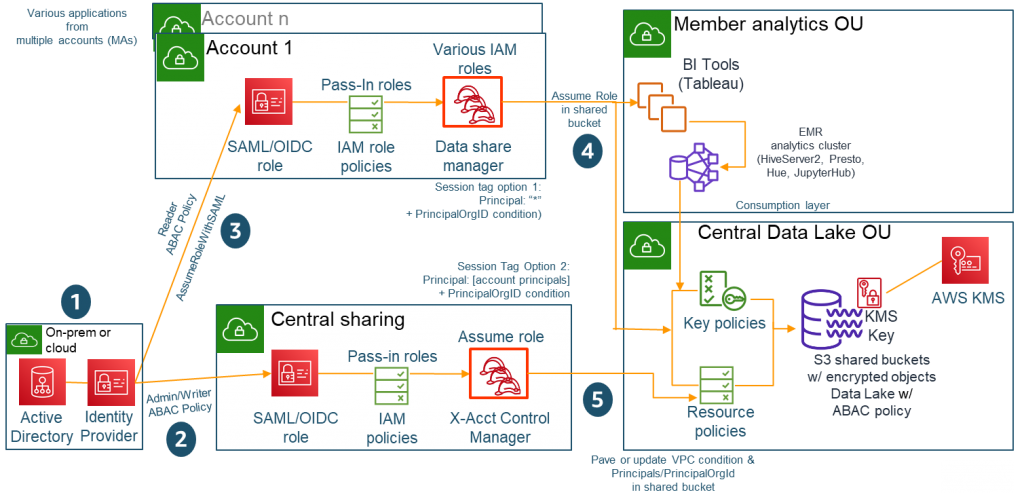
Figure 1: High-degree architecture
The high-level architecture is made to show you the benefits of scaling ABAC across accounts also to reflect on a standard model that pertains to most big organizations.
Remedy walkthrough
This is a short introduction to the essential components that define the perfect solution is:
- Identity company (IdP) – Could be either on-premises or in the cloud. Your administrators configure your SAML-based IdP to permit workforce users federated usage of AWS resources making use of credentials from your business directory (backed by Energetic Directory). You can now configure your IdP to move in consumer attributes as program tags in federated AWS classes. These transitive program tags propagate to all or any use cases (such as for example executor roles, instance functions, and service functions).
- Central revealing account – Really helps to set up the Admin/Author policy. It requires in the user’s info from the IdP and confirms authorization to gain access to resources. The X-Acct Control Supervisor creates the SAML part and trust partnership via OIDC (OpenID Connect) to permit users to assume functions and pass program tags. This account’s main purpose would be to produce data in to the lake. This accounts can also consume information from the lake if it offers such a use situation.
- Several accounts (MAs) for connecting to a multi-tenant information lake – Mirrors a big organization with a variety of accounts that could like cross-account read gain access to. Each account runs on the pre-pave data manager function that may tag or untag any IAM functions in an account and contains a cross-account have confidence in to an IAM part in a particular central account that may assume the function. Any other roles ought to be avoided from tag and untag guidelines (this is referred to as a sentinel plan).
- Associate Analytics organizational device (OU) – Is where in fact the EMR analytics clusters are usually connecting to the info in the consumptions coating to visualize via company intelligence (BI) equipment such as Tableau. Usage of the shared buckets will be given through bucket and IAM policy. MAs may also get access to buckets of their own accounts. Since this can be a consumer accounts, this account is becoming a member of the lake to take information from the lake and can not really be contributing any information to the info lake.
- Central Information Lake OU – May be the account which has Amazon S3 information location storage. The items are encrypted, that may require the IAM part to possess permissions to the specified AWS KMS type in the key plan. AWS KMS facilitates the usage of the aws:ResourceTag/tag-key global situation context key, which enables you to control usage of KMS keys in line with the tags on the KMS crucial.
Prerequisites
For using SAML program tags for ABAC, you must have the next:
- Usage of the SAML-based IdP where one can create test customers with specific attributes.
- For simplicity, you will end up utilizing an AWS CLI obtain short-term security credentials when generating a program.
- You’ll be passing program tags using AssumeRoleWithSAML.
- AWS accounts where customers can sign in. There are five makes up about conversation defined with accommodating plans and permission, as outlined in Physique 1. The numerals right here refer to labels on the figure:
- IdP accounts – IAM user with administrative authorization (1)
- Central expressing account – Admin/Writer ABAC plan (2)
- Sample accounts for connecting to multi-tenant information lake – Reader ABAC policy (3)
- Associate Analytics OU accounts – Presume roles within shared bucket (4)
- Central Information Lake OU account – Pave or upgrade virtual personal cloud (VPC) problem and principals/PrincipalOrgId in a shared bucket (5)
- AWS sources, such as for example Amazon S3, AWS KMS, or even Amazon EMR.
- Any third-party software or equipment, such as BI equipment.
Our goal is to style an AWS perimeter where designed access is allowed only when necessary and adequate conditions are met so you can get in the AWS perimeter. Start to see the following table to find out more.
| Boundary | Perimeter goal | AWS solutions utilized |
| Identification | Just My Resources Just My Networks |
Identity-based SCPs< and policies;/td> |
| Source | Just My IAM Principals Just My Networks |
Resource-based guidelines |
| System | Just My IAM Principals Just My Resources |
VPC endpoint (VPCE) plans |
You can find multiple design choices, but this post will concentrate on option A, that is a logical AND (∧) conjunction of principal organization, source, and system:
- (Only My aws:PrincipalOrgID) ∧ (Just My Resource) ∧ (Just My System)
- (Only My IAM Principals) ∧ (Only My Reference) ∧ (Only My System)
- (Only My aws:PrincipalOrgID) ∧ (Just My IAM Principals) ∧ (Only My Useful resource) ∧ (Only My System)
Policies review
To be able to properly design and consider control points and also scalability limitations, the next table shows a synopsis of the policies used in this website article. It outlines the look restrictions and briefly discusses the proposed options, which are explained in greater detail in the Establish an ABAC policy area.
| Policy kind | Sample guidelines | Restrictions to overcome | Solutions outlined inside this blog site |
| IAM user plan | AllowIamUserAssumeRole
AllowPassSessionTagsAndTransitive IAMPolicyWithResourceTagForKMS |
Inline JSON policy record is bound to (2048 bytes).
For using KMS keys, accounts are limited by particular AWS Regions. |
Enable session tags, which expire and require credentials.
This is a best exercise to grant least privilege permissions with AWS Identification and Access Administration (IAM) plans. |
| S3 bucket policy | Principals-only-from-given-Org
Access-to-specific-VPCE-just KMS-Decrypt-with-specific-essential DenyUntaggedData |
The bucket policy includes a 20 KB optimum quality.
Data exfiltration or even non-trusted composing to buckets could be restricted by a mix of policies and conditions. |
Make use of aws:PrincipalOrgID to simplify specifying the main aspect in a resource-based plan.
No guide updating of accounts IDs required, should they participate in the intended corporation. |
| ~ VPCE plan | DenyNonApprovedIPAddresses VPCEndpointsNonAdminDenyNonSSLConnections DenyIncorrectEncryptionKey DenyUnEncryptedObjectUploads |
aws:PrincipalOrgID opens upward broadly to accounts with single control-requiring additional handles.
Ensure that principals aren’t inadvertently allowed or denied gain access to. |
Restrict usage of VPC along with endpoint policies and deny statements. |
| KMS key plan | Allow-use-of-the-KMS-key-for-firm | Listing all AWS accounts IDs in an company.
Optimum key policy document sizing is usually 32 KB, which pertains to KMS essential. Changing a tag or even alias might allow or even deny permission to the KMS key. |
Specify the business ID in the problem element, rather than listing all of the AWS account IDs.
AWS owned keys usually do not count against these quotas, so make use of these where probable. Assure presence of API procedures |
With a combination of these guidelines and conditions, it is possible to mitigate accidental or intentional exfiltration of information from the non-trusted organization, IAM credentials, or VPC endpoints. You may also alleviate composing to a bucket that’s owned by way of a non-trusted accounts or principal through the use of a lot more restrictive policies for write functions. For example, utilize the s3:ResourceAccount condition important to filter usage of trusted S3 buckets that belong and then particular AWS accounts.
Ultimately, the scalability is bound by the amount of organizations, through file size which can be listed within the S3 bucket policy (20 KB) and KMS crucial policy (32 KB). Beneath the assumptions of the next policies and the utmost file size designed for listing organizations, you’re constrained to enable the next maximum amount of organizations for cross-account entry:
- S3 bucket policy: approximately 84 organizations (maximum, less for more technical policies)
- KMS essential policy: approximately 430 companies (optimum, fewer for more technical policies)
Let’s assume that each organization might have 20 or even potentially more accounts, more than 1 potentially,000 accounts could possibly be enabled for cross-account gain access to.
Number 2 demonstrates an example scenario for the functions from the specific organization inside AWS Businesses with described tags accessing an S3 bucket that’s owned by Central Information Lake OU.

Figure 2: Sample situation
Establish an ABAC policy
AWS has published extensive safety guides because of its products and person services. The base group of security manuals addresses: AWS KMS, ABAC, Amazon S3, resource-dependent policies (PrincipalOrgId), cross-account privilege style escalation, level authorization, information lake, Amazon EMR, among others.
To determine the ABAC plan
- Create an IAM function and IAM user plan by following a guidelines in this blog page to generate the IAM part.
- Create the ABAC plan for the function.An individual can start and prevent instances only when principal, PrincipalOrgID, and reference tags are usually matching. More detailed directions to define permissions to gain access to AWS resources predicated on tags can be found in the IAM guide.Plan sample to permit the session-tag consumer to assume the part
The AllowIamUserAssumeRole declaration in the next sample plan allows the test-session-tags consumer to assume the function with the attached plan. When that consumer assumes the part, they must pass the mandatory session tags and exterior ID.
"Version": "2012-10-17", "Statement": ["Sid": "AllowIamUserAssumeRole", "Effect": "Allow", "Action": "sts:AssumeRole", "Source": "arn:aws:iam::123456789123:user/test-session-tags", "Condition": "StringLike": "aws:RequestTag/Project": "*", "aws:RequestTag/CostCenter": "*", "aws:RequestTag/Department": "*" , "StringEquals": "sts:ExternalId": "Example987" , "Sid": "AllowPassSessionTagsAndTransitive", "Effect": "Allow", "Action": "sts:TagSession", "Reference": "arn:aws:iam::123456789123:user/test-session-tags", "Condition": "StringLike": "aws:RequestTag/Project": "*", "aws:RequestTag/CostCenter": "*" , "StringEquals": "aws:RequestTag/Department": [ "Engineering", "Marketing"] , "ForAllValues:StringEquals": "sts:TransitiveTagKeys": [ "Project", "Department"]]
- Permit cross-account access to a good AWS KMS essential (KMS keys). That is an IAM plan to permit principals to call particular operations just on KMS keys in your accounts. AWS KMS facilitates ABAC by enabling you to control usage of your client managed keys in line with the tags and aliases linked to the KMS keys. This gives a robust and flexible solution to authorize principals to utilize KMS keys without editing plans or managing grants. Nevertheless, you should use these functions with care in order that principals aren’t inadvertently permitted or denied access.Plan sample to permit a user inside another account to employ a KMS essential
To grant another accounts usage of a KMS essential, create an IAM plan on the secondary accounts that grants usage of use the KMS essential. For instructions, observe Allowing users within other accounts to employ a KMS major.
"Sid": "IAMPolicyWithResourceTagForKMS", "Effect": "Allow", "Principal": "AWS": "arn:aws:iam::123456789123:role/cross-account-assume-role" , "Action": [ "kms:GenerateDataKeyWithoutPlaintext", "kms:Decrypt" ], "Useful resource": "arn:aws:kms:ap-southeast-1:111122223333:essential/", "Condition": "StringEquals": "aws:PrincipalTag/Task": "Alpha" </program code>The accounts are limited by a Region (such as for example us-west2) and also have a Task=Alpha tag. You may attach this plan to functions in the instance Alpha project.
-
- Configure the S3 bucket plan.For cross-account permissions to some other AWS accounts or customers in another account, you must work with a bucket plan. Bucket policy is bound to 20 KB optimum file size.
The thought of the S3 bucket policy is founded on data classification, where in fact the S3 bucket policy can be used with deny statements that apply if an individual doesn’t have the correct tags applied. You don’t have to explicitly deny all activities in the bucket plan, because a user should be authorized in both IAM plan and the S3 bucket plan in a cross-account scenario. This can raise the complexity in your atmosphere.
Plan sample for the S3 bucket
You may use the Amazon S3 console to include a fresh bucket policy or even edit a preexisting bucket policy. Detailed guidelines for creating or modifying a bucket policy come in the Amazon S3 Consumer Guide. The next sample policy restricts accessibility and then principals from institutions as outlined in the plan and a particular VPC endpoint.
“Version”: “2012-10-17”,
“Statement”: ["Sid": "Principals-only-from-given-Org-List", "Effect": "Allow", "Principal": "", "Action": "s3:ListBucket", "Source": "arn:aws:s3:::sharedbucket", "Condition": "ForAllValues:StringLike": "aws:PrincipalTag/CostCenter": "", "aws:PrincipalTag/Task": "" , "ForAnyValue:StringEquals": "aws:PrincipalTag/Division": "Engineering", "aws:PrincipalOrgID": [ "o-teh8ggy8o9", "o-qrvnjkbfd2", "q-xxxxxxxxxxx"] , "Sid": "Principals-only-from-given-Org-Write", "Effect": "Allow", "Principal": "", "Actions": [ "s3:GetObject", "s3:PutObject"], "Resource": [ "arn:aws:s3:::sharedbucket", "arn:aws:s3:::sharedbucket/"], "Condition": "ForAllValues:StringLike": "aws:PrincipalTag/CostCenter": "", "aws:PrincipalTag/Task": "" , "ForAnyValue:StringEquals": "aws:PrincipalTag/Section": "Engineering", "aws:PrincipalOrgID": [ "o-teh8ggy8o9", "o-qrvnjkbfd2", "q-xxxxxxxxxxx"] ,“Sid”: “Access-to-specific-VPCE-only”,
“Effect”: “Deny”,
“Principal”: ” “,
“Activity”: “s3: “,
“Reference”: [“arn:aws:s3:::sharedbucket”, “arn:aws:s3:::sharedbucket/ “],
“Condition”:
“StringNotEquals”:
“aws:sourceVpce”: “vpce-xxxxxxxx”,
“Sid”: “DenyUntaggedData”,
“Principal”: ” “,
“Effect”: “Deny”,
“Motion”: [ “s3:GetObject”, “s3:GetObjectVersion” ],
“Useful resource”: “arn:aws:s3:::sharedbucket/ “,
“Condition”:
“ForAnyValue:StringNotEquals”:
“aws:PrincipalOrgID”: [
“o-teh8ggy8o9”,
“o-qrvnjkbfd2”,
“q-xxxxxxxxxxx”
]]
-
- Configure the VPCE plan.You may use S3 bucket guidelines to control usage of buckets from particular VPC endpoints, or particular VPCs.Furthermore, the S3 bucket plan should be scoped right down to explicitly deny the next:
- Non-authorized IP addresses
- Incorrect encryption keys
- Non-SSL connections
- Un-encrypted item uploads
Plan sample for VPCE-bucket plan enhancements
The set up of VPC endpoints will be referred to in the Amazon VPC User Manual .
To generate an user interface endpoint , you need to specify the VPC where to generate the interface endpoint, and the services to which to determine the connection.
It is possible to download this sample plan.
-
- Configure the KMS key plan.To be able to authorize principals’ usage of your customer handled keys or AWS maintained keys predicated on tags and aliases connected with these keys, it is possible to define the business(s) in the plan. Enabling cross-account gain access to requires authorization in the main element policy (quite simply, who can have admission) of the KMS important and within an IAM policy (put simply, who does have admission) in the exterior user’s account. Whenever you can, follow the minimum privilege principal. Especially, when working with business(s) in the plan, limit access and then the KMS keys that principals dependence on only the operations they require. Both plans need to be set up for sufficient entry.The tags enable ABAC in AWS KMS and offer a robust and flexible solution to authorize principal businesses without editing guidelines or controlling grants. The aws:PrincipalOrgID global situation key may be used with the Principal aspect in a resource-based plan with AWS KMS. Rather than listing all of the AWS account IDs within an organization, it is possible to specify the business ID in the problem component with the contact crucial aws:PrincipalOrgID . You could find detailed directions for changing the main element policy utilizing the AWS Management System in the AWS KMS Developer Guideline .
Plan sample to permit usage of the AWS KMS essential for specific corporation(s)
Following may be the sample KMS important policy statement to permit identities of AWS accounts that participate in specific organizations having an ID (for instance, “o-teh8ggy8o9”, “o-qrvnjkbfd2”) to utilize the KMS Crucial. To get the Business ID:
- Open up the AWS Companies Console .
- Choose Configurations .
- In Organization information , duplicate the Organization ID.
-
- Configure the SAML IdP (in case you have one) or article in instructions manually.Usually, you configure your SAML IdP to move in the task, cost-center, and division attributes as program tags. To find out more, notice Passing program tags making use of AssumeRoleWithSAML .The next assume-function AWS CLI command can help you perform and try this request.
-
This example demand assumes the s3Go through function for the specified duration with the incorporated program policy, session tags, exterior ID, and source identification. The resulting program is known as my-program .
Cleanup
In order to avoid unwanted costs to your AWS accounts, delete the AWS assets you created in this walkthrough.
Summary
This post explains how exactly to share encrypted S3 buckets across accounts at scale by considering access across numerous accounts to a multi-tenant data lake and selecting solutions for scalability. Following a scalability solution route, we selected several principles for the look and used them in conjunction with handling the KMS essential policy, including IAM make use of policy, S3 bucket plan, and VPCE plan. We added plans that enable additional settings, which are organized and orchestrated to optimize conversation. Also, out-of-bounds accessibility, such as for example unintended principals beyond your estate of the accounts holder, are addressed to be able to capture risk that is included with applying the worldwide aws:PrincipalOrgID condition type in your resource-based guidelines.
Our strategy centered on the scalability style; it is possible to generalize and repurpose the methods for different specifications and projects. Because of this, a scalable remedy for services not incorporated with AWS Lake Development can be acquired for customization in lots of instructions with AWS KMS. For providers that honor Lake Development permissions, you may use the Lake Formation Programmer Guide to more setup integrated solutions to encrypt and decrypt information easily.
In conclusion, the look provided is simple for large projects here, with appropriate handles to allow substantial scalability (potentially across a lot more than 1,000 accounts and several companies).
When you have suggestions about this post, submit remarks in the Remarks area below. Should you have queries about this post, start a brand-new thread on AWS Techniques Manager re:Write-up or contact AWS Assistance.
Want a lot more AWS Security news? Stick to us on Twitter.
