Scalable Security with Cisco Protected Firewall Cloud Native
Today, companies spend money on making their security handles scalable and dynamic to meet up the ever-increasing requirement on their network(s). Oftentimes, the response is really a massive change to Kubernetes® (K8s®) orchestrated infrastructure that delivers a cloud-indigenous, scalable, and resilient infrastructure.
That’s where Cisco Secure Firewall Cloud Native (SFCN) will come in. You are distributed by it the flexibleness to provision, run, and level containerized security services. Cisco Protected Firewall Cloud Native provides the advantages of Kubernetes and Cisco’s industry-leading security technology together, supplying a resilient architecture for infrastructure safety at scale.

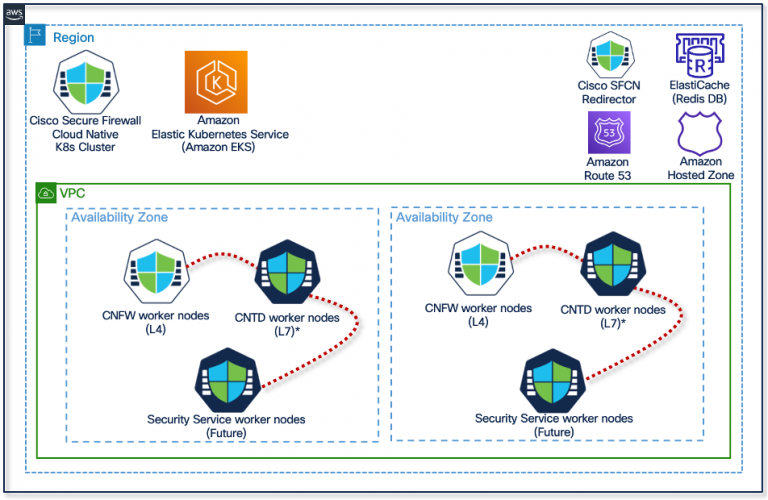
The architecture depicted above displays a modular platform that’s scalable, resilient, DevOps friendly, and Kubernetes-orchestrated. In the original launch of Cisco Secure Firewall Cloud Native, we’ve added assistance for CNFW (L3/L4 + VPN) in AWS. Upcoming releases will add assistance for CNTD (L7) protection along with other cloud providers.
Essential capabilities of Cisco Secure Firewall Cloud Native include:
scalable and
-
- Modular architecture
-
- Kubernetes orchestrated deployment
-
- DevOps helpful with Infrastructure-as-Code assistance (IaC)
-
- Information externalization for stateless providers with a high-performance Redis™ data source
-
- Multi-AZ, multi-region, and multi-tenant assistance

The architecture depicted above displays the Cisco Secure Firewall Cloud Native system, which utilizes Amazon EKS, Amazon ElastiCache™, Amazon EFS with industry-major Cisco VPN and L3/L4 security manage for the advantage firewall use-condition. The administrator can manage Cisco Safe Firewall Cloud Indigenous infrastructure making use of kubectl + YAML or Cisco Protection Orchestrator (CDO). Cisco offers APIs, CRDs, and Helm™ charts because of this deployment. It utilizes custom made metric and Kubernetes horizontal pod autoscaler (HPA) to scale pods horizontally.
Key components include:
-
- Control Stage (CP): The Control Point is in charge of config validation, distribution and compilation, licensing, routes administration. CP pods accept construction from Relaxation APIs, kubectl+YAML, or Cisco Protection Orchestrator.
-
- Enforcement Stage (EP): CNFW EP pods have the effect of L3/L4 and VPN visitors dealing with and VPN termination.
-
- Redirector: Redirector pod is in charge of intelligent load balancing remote control access VPN traffic. Whenever a request is obtained by the redirector, it contacts Redis DB and Fully Qualified Domain Title (FQDN) of the enforcement pods managing the least amount of VPN sessions.
-
- Redis DB: The Redis data source has info on VPN sessions. The redirector uses this given information make it possible for smart load balancing and recovery.
The next instance type is supported for every component.
 Preliminary use-cases:
Preliminary use-cases: -
- Scalable Remote Entry VPN architecture
-
- Scalable Remote Accessibility VPN architecture with intelligent load balancing and program resiliency
-
- Scalable DC backhauls
-
- Multi-tenancy
-
- Scalable cloud hub
-
- Scalable advantage firewall
Scalable Remote Gain access to VPN architecture
Cisco Secure Firewall Cloud Native has an easy solution to deploy scalable remote control accessibility VPN architecture. It utilizes custom made metrics and horizontal pod autoscaler to improve or decrease the amount of CNFW Enforcement Factors as required. The Control Stage controls configuration, routing, and Amazon Path 53™ configuration for the auto-scaled Enforcement Point.

Traffic stream:
-
- The remote control VPN user transmits a DNS query for vpn.mydomain.com. Amazon Route 53 monitors all CNFW nodes, and contains “An archive” for every node with weighted typical load balancing allowed for incoming DNS requests.
-
- The remote control VPN user gets “Elastic IP – EIP” of the exterior interfaces of the CNFW node.
-
- The remote control VPN user links to the CNFW node. Each node offers a separate VPN swimming pool for correct routing.
Scalable Remote Accessibility VPN architecture, with clever load balancing and program resiliency
Cisco Secure Firewall Cloud Native architecture with sensible load balancing makes use of Amazon ElastiCache (Redis DB) to store VPN program details. Redirector node consults Redis data source to execute load balancing structured VPN session count, of weighted average load balancing instead.
The Control Stage controls configuration, routing, redirector configuration, and Route 53 configuration for the auto-scaled enforcement point.

Figure 4 - Scalable Remote Gain access to VPN architecture with wise load balancing and program resiliency Traffic circulation:
- The remote control VPN user transmits a DNS query for vpn.mydomain.com, and vpn.mydomain.com factors to the CNFW redirector.
- The remote control VPN consumer sends the demand to the redirector after that.
- CNFW redirector periodically polls the Redis data source (Amazon ElastiCache) to discover the FQDN of the Cisco Protected Firewall Cloud Native nodes with minimal amount of VPN endpoints. CNFW redirector offers FQDN of minimal loaded CNFW node to the remote control VPN user.
- The remote consumer resolves FQDN, we immediately add “A” report for every CNFW enforcement stage in Amazon Route 53.
- The remote control VPN user links to the CNFW node which has the least amount of VPN sessions.
Scalable DC backhauls
The autoscaled Enforcement Factors can develop a tunnel to the info center automatically back. Cisco offers a sample Kubernetes deployment make it possible for this functionality.

Multi-tenancy
This architecture offers multi-tenant architecture making use of cloud-indigenous constructs such as for example namespace, EKS cluster, nodes, subnets, and security groups.

Figure 6 - Multi-tenancy Scalable cloud hub
This architecture offers a scalable cloud architecture making use of CNFW, Amazon EKS, along with other cloud native controls.

Scalable advantage firewall
This architecture offers a scalable architecture making use of CNFW, Amazon EKS, along with other cloud-native controls.

Figure 8 - Scalable advantage firewall Licensing
Cisco Secure Firewall Cloud Native can be acquired you start with ASA 9.16. This discharge provides CNFW (L3/L4 + VPN) safety with Bring YOUR PERSONAL Licensing (BYOL), making use of Cisco Smart Licensing.
-
- Licenses derive from CPU cores utilized
-
- Works with multi-tenancy
-
- Unlicensed Cisco Secure Firewall Cloud Indigenous EP runs at 100 Kbps
-
- AnyConnect permit model is equivalent to the ASA AnyConnect permit model
Resources
We’d want to hear everything you think. Ask a relevant question, Comment Below, and Remain Linked to Cisco Secure on sociable!
Cisco Secure Social Stations
Instagram
Facebook
Twitter
LinkedIn
<br>

You must be logged in to post a comment.