Revisiting the Program: The Prospect of Shared Signals
<span data-contrast="auto"> Sometimes to be able to move effectively, it’s great to take share of where we’ve already been. In this website, we’ll review an idea that is foundational to networking and cybersecurity right from the start: the session. Why concentrate on the session? Because the philosophy of Zero Rely on is adopted a lot more in the security business broadly, it’s vital that you understand the inspiration of access. The program is a essential component of usage of any reference. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
<span data-contrast="auto"> To obtain things started, let’s focus on a definition. A straightforward definition of a program may be: “a period devoted to a specific activity.” Not too bad, however the complexity for network and internet security springs from scoping the “particular activity.” </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
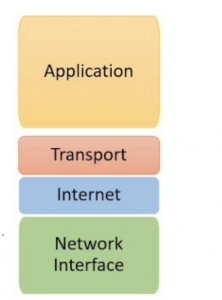
<span data-contrast="auto"> The web exists along with a standardized suite of protocols that govern how information could be transmitted or exchanged between various entities. This suite, usually known as the TCP/IP stack today, is made up of four distinctive layers that delineate how information flows between networked assets. That's where the scoping of a program becomes obscure. The “specific activity” could make reference to the network coating, which is in charge of establishing communications between your bodily networks. Or, the experience refers to the web layer perhaps, which ensures the packets of information reach their places across network boundaries. The experience may be the transport layer, responsible for the dependability of end-to-end communication over the network. It may be referencing the application form layer also, the highest level of the TCP/IP stack, that is in charge of the interface and protocols utilized by users and applications. For the familiar, these layers were described in the OSI model originally. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
<figure id="attachment_401961" aria-describedby="caption-attachment-401961" class="wp-caption aligncenter"> <img class="wp-image-401961 size-medium" src="https://infracom.com.sg/wp-content/uploads/2022/05/Screen-Shot-2022-05-23-at-5.48.38-PM-222x300-1.png" alt width="222" height="300" />
<figcaption id="caption-attachment-401961" class="wp-caption-text"> TC/IP Stack </figcaption>
</figure>
<span data-contrast="auto"> This layering framework is effective for establishing the unique session forms and how exactly we can begin to safeguard them. Nevertheless, the increase of cloud-based providers means we should now furthermore look at how classes are defined with regards to the cloud - specifically as we turn to provide protection and access settings. At the application form layer, we've client products with web applications and browsers that communicate to a cloud service. Additionally, cloud solutions could be one or a mix of SaaS, IaaS and paas, each defining their very own program and access thus. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
<span data-contrast="auto"> With all the current different lessons of sessions, you can find different protocols and mechanisms where authentication and authorization are used to ultimately provide that access. All sessions make use of some type of accounts or credential to authenticate and assess a couple of variables to find out authorization or gain access to. A few of these variables could be similar across different periods also. For instance, an enterprise may measure the device’s security position (e.g. it really is running the latest Operating system patches) as a adjustable to grant entry at both network and application coating. Similarly, exactly the same password and username can be utilized across various session layers. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
<span data-contrast="auto"> However, each layer could also use distinct and particular variables to evaluate the correct access level. For instance, the network interface level should ensure cryptographic compliance of the network interfaces. A cloud services might evaluate geographical or regional compliance. Today would be to have every program layer act alone to create its access decision the normal practice. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
<span data-contrast="auto"> Let’s have a step back and evaluation. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
<ul>
<li data-leveltext="·" data-font="Symbol" data-listid="7" data-list-defn-props=""335552541":1,"335559683":0,"335559684":-2,"335559685":720,"335559991":360,"469769226":"Symbol","469769242":[8226],"469777803":"left","469777804":"·","469777815":"hybridMultilevel"" data-aria-posinset="1" data-aria-level="1"> <span data-contrast="auto"> We’ve established there are many types of classes, and the definitions are just expanding as cloud providers become more notable. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span> </li>
<li data-leveltext="·" data-font="Symbol" data-listid="7" data-list-defn-props=""335552541":1,"335559683":0,"335559684":-2,"335559685":720,"335559991":360,"469769226":"Symbol","469769242":[8226],"469777803":"left","469777804":"·","469777815":"hybridMultilevel"" data-aria-posinset="2" data-aria-level="1"> <span data-contrast="auto"> We’ve set up that securing each kind of session is essential, yet generally each distinct program is analyzing a Venn diagram of variables, some typically common across session sorts, others specific to a specific session definition yet. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span> </li>
<li data-leveltext="·" data-font="Symbol" data-listid="7" data-list-defn-props=""335552541":1,"335559683":0,"335559684":-2,"335559685":720,"335559991":360,"469769226":"Symbol","469769242":[8226],"469777803":"left","469777804":"·","469777815":"hybridMultilevel"" data-aria-posinset="3" data-aria-level="1"> <span data-contrast="auto"> Finally, each session layer makes its access evaluation typically. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span> </li>
</ul>
<span data-contrast="auto"> Today, let’s explore something brand-new: imagine if the variables and accessibility evaluation outcomes had been shared seamlessly across program layers? </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
<span data-contrast="auto"> Imagine if recent system context and action were used to see cloud access choices? Or, recent user gain access to decisions over the network layers be utilized to see cloud application handles? Take into account the enhanced resilience supplied if network-based risk transmission like packet details could be properly mapped and distributed to the cloud application coating. Sharing information across program boundaries provides better quality fulfillment of Zero Confidence concepts by striving to judge safety context </span> <b> <span data-contrast="auto"> as holistically as you possibly can </span> </b> <span data-contrast="auto"> during entry. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
<span data-contrast="auto"> To be able to create a future where protection decisions are well informed by broader and constant context, we’ll want protocols and tools that help all of us bridge tools and map information across them. To supply improved security and accessibility, both bridge and the right mapping must be set up. It’s a very important factor to find the data used in another tool, it’s very another to map that information into relevance for the brand new tool. For example, just how do we map a privileged program credential to a tool? And, just how do we map relevant context across systems then? </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
<span data-contrast="auto"> Fortunately that work is needs to enable another where irrespective of session definition, safety context could be shared and mapped. Protocols like the </span> <a href="https://openid.net/wg/sse/" target="_blank" rel="noopener"> <span data-contrast="none"> Shared Signals and Occasions </span> </a> <span data-contrast="auto"> and the </span> <a href="https://www.openpolicyagent.org/" target="_blank" rel="noopener"> <span data-contrast="none"> Open Plan Broker </span> </a> <span data-contrast="auto"> are usually evolving make it possible for timely and dynamic transmission sharing between tools, however they are usually nascent and broader adoption is necessary. Cisco has recently contributed a specialized reference architecture as helpful information for </span> <a href="https://sharedsignals.guide/" target="_blank" rel="noopener"> <span data-contrast="none"> Shared Signals and Activities </span> </a> <span data-contrast="auto"> . Hopefully that by accelerating the adoption of the standards the gets one step nearer to actively sharing related protection context across OSI layers. As the road won’t be simple, we think the sharing signals shall lead to a far more resilient and robust safety future. </span> <span data-ccp-props=""201341983":0,"335559739":160,"335559740":259"> </span>
<hr />
<p class="p1"> <i> We’d want to hear everything you think. Ask a relevant question, Comment Below, and Remain Linked to Cisco Secure on sociable! </i> </p>
<p class="p1"> <b> Cisco Secure Social Stations </b> </p>
<p class="p1"> <b> <a href="https://www.instagram.com/CiscoSecure/" target="_blank" rel="noopener noreferrer"> Instagram </a> <br /> </b> <a href="https://www.facebook.com/ciscosecure/" target="_blank" rel="noopener noreferrer"> <span class="s1"> <b> Facebook </b> </span> </a> <b> <br /> </b> <a href="https://twitter.com/CiscoSecure" target="_blank" rel="noopener noreferrer"> <span class="s1"> <b> Twitter </b> </span> </a> <b> <br /> </b> <a href="https://www.linkedin.com/showcase/cisco-secure" target="_blank" rel="noopener noreferrer"> <span class="s1"> <b> LinkedIn </b> </span> </a> </p>
<pre> <code> <br>
<br>
