Reliable and precise Threat Detection for the Security Program
On the Sunday evening it’s 11:59PM, and your phone begins alerting one to a fresh threat that is getting actively exploited. It is simple to anticipate that another information you shall receive will be from somebody in your C-Suite, asking the obvious issue, “Are we protected from this?”
As security practitioners, just about everyone has been there. The week just what a way to start!
Of course, we have to tailor our reaction to any senior executive, very first with the alarming realization that zero product is 100% efficient, and temper it with comforting phrases that the merchandise that protects the business is indeed with the capacity of detecting brand-new threats. But, will be this the reality?
Take into account the decisions that proceeded to go into purchasing your safety product. Has been it from a reliable and trustworthy vendor, or has been it just the less-expensive selection that satisfied a few of the compliance and security requirements? This is simply not a comfortable place to stay during an emergency.
Accurate threat detection – dependability versus liability
Accurate threat recognition is a difficult subject matter. How will you know that your item is working successfully? Does the number of detections supersede the product quality?
When we think about how exactly to answer these relevant queries, specifically to a senior executive who’s responsible for the protection of the ongoing organization, the solution shall not be predicated on technical data; in this case, reliability will be the determining element . Remember, recently, corporate executives can’t languish in neuro-scientific “plausible deniability” about protection. Recent rules have removed most of the corporate-structured insulating protections also, departing an executive available to private liability for information breaches . In a nutshell, there exists a reason that your
C-Suite is becoming hyper-aware of cybersecurity activities.
The landscape of the recognition capabilities is evolving, which is key to producing higher fidelity detections really, instead of relying solely on atomic indicators and legacy methods. Although these old methods may be affordable, they produce less-than-stellar outcomes, and so are easily evaded by threat actors often.
In some instances, a business may think that utilizing a large numbers of threat feeds shall provide superior results, but this is simply not true necessarily. You can easily realize that quantity will not imply high quality. Most danger feeds duplicate data, therefore seeing more of a similar thing won’t ensure accuracy, or dependability.
To access our exemplory case of the 11:59PM alerts back, how exactly to you convince your C-Suite you are protected against these new threats indeed? Humorously, you can stage them to Cisco’s Safety Outcomes Study , but they might not find much humor for the reason that during a right period of crisis. However, now might be a good time and energy to digest the insights in the scholarly study, before that near-midnight telephone alert.
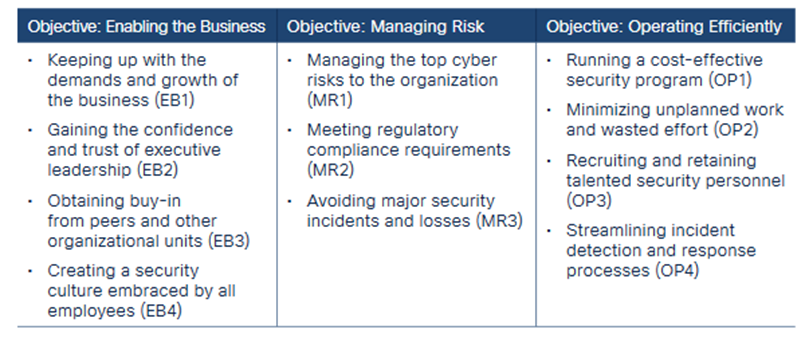
Key Results from the Protection Outcomes Research
The Security Outcomes Research interviewed 4,800 visitors to learn their views on questions regarding their security posture. The entire disposition of the scholarly study shows the significance of reliability on the main element indicators for success.

While it will be nice to condition that a lot of organizations are well-equipped within their capability to accurately track incidents, giving comfort to a nervous band of executives, the responses tell a far more sobering tale. A lot more than one-3rd of the respondents had been less likely to concur that their corporation follows the exercise of accurate threat recognition.  Needless to say, one could posit that leaves a large section of interpretation as to just how many of the interviewees ran the spectrum from “relatively likely to agree”, all of the real solution to “more than likely to agree”. If that additional two-3rd of respondents are employing accurate threat detection, that is clearly a fantastic indicator then. Nevertheless, from the viewpoint of an attacker, this opens up a industry of many targets that are not using precise threat recognition. While optimism can be an admirable trait, our job as safety practitioners dictates that people must think just like the attacker always.
Needless to say, one could posit that leaves a large section of interpretation as to just how many of the interviewees ran the spectrum from “relatively likely to agree”, all of the real solution to “more than likely to agree”. If that additional two-3rd of respondents are employing accurate threat detection, that is clearly a fantastic indicator then. Nevertheless, from the viewpoint of an attacker, this opens up a industry of many targets that are not using precise threat recognition. While optimism can be an admirable trait, our job as safety practitioners dictates that people must think just like the attacker always.
Also, to quote straight from the report:
Security specialists used to possess to fight tough for executive assistance and attention, but respondents reveal that we’ve come quite a distance in that regard. However, a few of the fundamentals that the forever has been focusing on, such as for example threat vulnerability and recognition remediation, remain a problem for most organizations. This an excellent reminder that “obtaining back to the fundamentals” isn’t quite as basic since it sounds. Cisco Safe – helping executives obtain the sleep they want
At Cisco Protected our mission would be to develop, acquire and integrate a protection portfolio that simplifies functions, accelerates group success, and positions companies to secure their upcoming. With this comprehensive portfolio and the threat intelligence supplied by Talos , we deliver enhanced improve and efficacy alert fidelity.
With the Cisco SecureX , you can utilize a integrated ecosystem fully, enable intelligence coordinated and revealing response. With this platform approach, it is possible to change your infrastructure from the group of disjointed solutions right into a completely integrated ecosystem that provides you a unify presence into threats, increase operational efficiency, and invite you to lessen your mean time and energy to detect.
Before all of the fancy flashing lights and trend lines on your own security dashboard begin to indicate the “strong chance for a definite probably” of a potential threat, you need to know that the merchandise is buoyed by the knowledge and experience of a reliable head in the security industry. That is one method that you could let your executives obtain the sleep they need.
To understand of some other methods to achieve security achievement in your organization, make sure to study our blog collection and download and revel in the entire Safety Outcomes Research
<br>

You must be logged in to post a comment.