Ransomware: Secure Backup CAN BE YOUR Last Type of Defense
Individuals have questioned what we mean whenever we state, “secure back-up is your last type of protection.” During the last a decade, the security market has realized contemporary ransomware protection takes a n built-in safety architecture from endpoints to system and cloud to detect , correlat electronic and remediate assaults totally . Regarding ransomware, your alternatives for remediation are often to get over a backup or spend the rans om. The task is usually , saying “restore from back-up” oversimplifies the procedure and leads to many institutions to create assumptions about their backup and recovery features. As is the character of assumptions, they prove false often, resulting in either data loss or even the ransom needing to be paid still. In order to avoid the worst-situation situation, you will need a plan set up that contains verified , examined and safe backups which can be restored rapidly. Therefore, we desire to remind ourselves and everyone we connect to that your back-up infrastructure is section of the entire cybersecurity protection strategy and could possibly be the final choice so you can get back to, or residing in, company.
The development of episodes like ransomware offers pushed those who have not typically been regarded as part of protection, like the disaster recuperation and backup teams, to the biggest market of the recuperation and response operations. We notice in Veeam’s 2022 Data Protection Developments record that 88% of the respondents possess company continuity and disaster recuperation were either mainly or totally integrated making use of their cybersecurity methods. It’s a strange spot to be once the backup group were historically concerned about users deleting little numbers of data files, and you’re now accountable to prove it is possible to recover every little bit of data in your organization due to a cyberattack.
Dealing with a breach, and proving you haven't lost data, should suggest there’s you don't need to spend a ransom. Sadly, the 2022 Data Security Report displays us that only 36% of organizations could actually recover a lot more than 80% of these data following a ransomware assault. This statistic is irritating because it’s not an excessive amount of a leap to believe that these businesses either considered having to pay or did pay out a ransom to obtain their data back again. Developing a secure back-up for ransomware recuperation
Therefore, what do we need to do to assure we can confidently obtain operations back ready to go? At Veeam here, we believe the solution is a mix of product functions and procedural guidelines that make sure you can detect workloads because they come on-line, protect the info in a verifiable manor, and recover at level in a manner that doesn’t reintroduce threats to the surroundings.
On the backup side, it’s about protecting the info and making certain the backup job is functioning needlessly to say. There are furthermore the best procedures which make certain when everything went horribly wrong you’ll still have a duplicate of your data to revive. During recovery, you want to concentrate on rate, which ties into orchestration and automation. Once again, a variety of process and product. Finally, we have to ensure the info that’s recovered won’t re-present a threat to the surroundings. Let’s look at a few of the good reasons why that is important. I’ve also included hyperlinks to posts from our technical professionals for a lot more information.
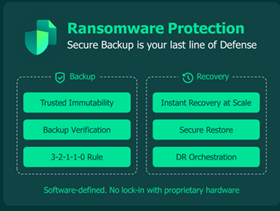
Trusted immutability
Veeam is a software-first company always. This means you’re in charge of the storage space configurations and so are not limited by the construction we choose. In addition, it means it is possible to create several layers of immutable storage space both in the cloud or on premises predicated on your network style. This flexibility also lowers operational raises and costs security since you’re making use of your existing storage platforms. There’s an excellent article on your options for what we prefer to contact “double-have fun with” immutability that you ought to read for more information.
Back-up verification
How can you prove your backup was successful? Inside our upcoming ransomware analysis report, we found nearly all organizations either depend on the work completion logs or possess built their very own scripts to verify the integrity of the back-up. The challenge is counting on backup work logs only displays the working work completed, without proving the info can be recovered. Individuals who create their very own process however are using a step of progress but are increasing their workload by sustaining scripts or trusting they’ll have period for a manual, and mundane arguably, process.
For all of us, backup verification is portion of the feature place we contact SureBackup . Put simply, SureBackup may be the Veeam technology which allows one to run multiple checks on your own backups to confirm the info is malware free of charge and that the info can become recovered. The process is often as basic or in-depth as you will need and can be operate manually or be planned in your disaster recuperation preparations. For additional information on what SureBackup can perform, click right here .
3-2-1-1-0 Guideline
When I joined Veeam very first, I met with people of our amazing customer care corporation and asked what the thing was they wished clients would do. They mentioned the 3-2-1-1-0 Rule. Contemporary malware may attack the backup level, so you want to have an activity in place to make sure resilience.
The 3-2-1-1-0 Principle states there should be at the very least three copies of important information , on at the very least two various kinds of mass media , with at the very least one of these brilliant copies being off web site . As the risk of ransomware has progressed, we recommend a minumum of one copy of information end up being resilient either through getting air-gapped, offline, or immutable. That is imperative for defending yourself against ransomware effectively. We’ve additional a zero also, for zero backup mistakes, to the rule because automated backup verification guarantees your computer data is usable and legitimate for recovery. You cannot recover information that incorrectly has already been captured, so following 3-2-1-1-0 Rule could possibly be the difference between data recuperation and loss.Instant recovery at level
The 2022 Data Protection Trends report implies that downtime is estimated to cost $1,467.00 each and every minute or $88,000.00 each hour. Blend this with the increasing gap between your SLA for data recuperation and the specific speed of recuperation and it’s no question so many businesses pay ransoms.
Veeam pioneered Quick VM recuperation this year 2010 and contains refined and extended the ability ever since. Nowadays, Veeam provides multiple recovery choices that allows one to optimize your recuperation processes and rapidly restore multiple machines at the same time. You will need granular options to recuperate a single document, we can do this. Application recovery, no nagging problem. Whole servers or volumes had been removed with ransomware, we’ve got you protected. The truth that you can make use of the various tools suitable to your preferences indicates we’re flipping the script on poor actors and producing ransomware recuperation the faster, and much more cost-effective choice and producing the mantra of “don’t spend the ransom” possible.
Protected Restore
Veeam was initial to advertise with the Secure Restore capability, which scans device data together with your antivirus software program before restoring the device to the production atmosphere. Secure Restore is easy to enable and enables you to update your selected antivirus or antimalware software program to the most recent signature ranges, no exclusions, also to verify in a non-production, network-isolated sandbox which means you shall not re-introduce threats into your computer data middle before restoring data.
Right here are a couple of resources for creating the procedure and utilizing the capability:
Ransomware Recuperation: What you ought to Know
Data Recuperation Disaster Recuperation (DR) Orchestration
Wish is not a technique, and it’s not likely to help you inside a tragedy. And let’s concur that ransomware is really a disaster. Orchestration and automation have grown to be critical to cybersecurity protection and the same could be said for recovery. The worst thing it is possible to hear someone say throughout a ransomware strike is “I believe it functions like this…” or “it will do that…” which explains why Veeam constructed the Veeam Disaster Recuperation Orchestrator item. Disaster recovery is successful for those who have a well-documented program, and that plan might help companies consider their DR preparedness to another level. Furthermore, an idea is only valid once you learn it shall work, and Veeam’s remedy provides automated recuperation SLA tests and an SLA dashboard for simple visibility of one’s DR readiness.
Backup and recovery are usually no more a siloed little bit of the infrastructure which can be assumed to work. Fast, reliable recovery can be an integral section of the general cybersecurity incident response procedure and should be thoughtfully prepared out similar to the rest of one’s security architecture. Trip to the finish of the, your data can be your most important asset, so it should be safeguarded with a protected backup solution that’s not only flexible good enough to create immutability that matches your needs, but additionally verifies the backup careers to guarantee the data will there be and malware free if you want to restore. All these reasons and more is the reason why when we consider ransomware, Veeam believes secure back-up can be your last type of defense.
For even more information on what you can enhance your ransomware defenses go to: https://www.veeam.com/ransomware-protection.html?ad=menu-solutions


You must be logged in to post a comment.