Ransomware aberration recognition by Veeam
Over 4, 000 private businesses were polled in Veeam’s Data Protection Trend report, and it was discovered that 85 % of them had encountered ransom in the previous 12 months. It’s crucial that IT organizations plan for quick recovery in the event of ransomware, as was previously discussed, given that a wasteland attack has much higher chance of occurring than if it were triggered by natural disaster, power outage, or other disaster recovery ( DR ) event. Finding the last known good fallback that took place is a necessary step in successful and effective recoveries. Without it, businesses could invest numerous years, if not decades, in trying to restore data that has already been corrupted. In truth, this article found that businesses typically took one to two weeks to recover their data. Since identifying and searching for the last known clear backup takes up a lot of time, recovering from other DR events takes much less time than this does. Veeam uses a three-tier strategy to assist businesses in determining the best point-in-time to survive from:
- Identify suspicious behavior on your VMware and Hyper-V virtual machines( VMs ) that are currently in use.
- Find flaws in the back files’ underlying structure.
- Before restoring your machines to supply, quickly scan storage folders.
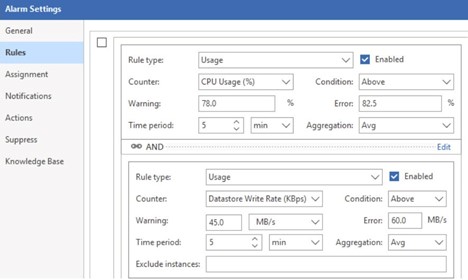
Detecting Unusual Behavior on Virtualization
The first step is to make sure there is a usable backup, but it’s also crucial to keep an eye on your entire environment for wary or unusual activity. Veeam examines the host and system levels in addition to backup data in search of anomalies. These higher-than-normal writes on the drive or CPU can be a sign that the computer has been infected by malware. The alarm’s objective is to identify the possible infected product before it spreads to many systems.
Meanwhile, the historical perspective holds the key to this concern. Knowing where malware might have occurred and what files to start with can be done with the help of this concern.
Finding Problems in Files
Cautious Backup File Size Analyzer by Veeam lives up to its name. This alert detects patterns in the storage data you have. Additionally, it examines updates, searches for numerous files, and blocks changes to your data. Your system officials will receive a notification if an oddity is found.
Owing to a fantastic book from Steve Herzig, this alarms can be easily integrated into Veeam’s important console! The job studies may reflect any anomalies that are found.
Taking this hand from git and add it to your backup jobs’ post-script section. In the” Depth” field, specify how many previous PITs you want to analyze and how much growth would be regarded as suspicious.
These first two tips give your company a clear understanding of the historical events you want to bounce back from. Because of the endless hours or even days that are spent personally determining when is best to recover from, ransom is the worst kind of hazard without these tips.
Files should be easily scanned before being restored.
Finally, Veeam can check your backup files for malware before restoring machines to production, whether you do so actively or dynamically. You may maintain or stop the rescue if malware is discovered without connecting a network for more in-depth forensics.
Any monitoring program with a CLI can be used by businesses. Trend Micro, Bitdefender, Windows Defender, etc. may all be used for this. Here, just delete the XML document.
Conclusion
Veeam is on a commission to assist users in recovering from ransom. Veeam has frequently been the soldiers for businesses that are having trouble, as I have personally witnessed. Veeam thinks that combining the methods below to find a clear point in time with the quickest recovery options on the market will greatly improve the quality of sleep for IT organizations at evening.








You must be logged in to post a comment.