Pinpoint Your SolarWinds Direct exposure with Cisco Endpoint Security Analytics
As various private companies and high-value government bodies find out the blast radius of the latest state-sponsored SolarWinds attack, with Cisco Endpoint Security Analytics (CESA) within your toolkit you can quickly assess your personal exposure…such as the CESA consumer noted below.
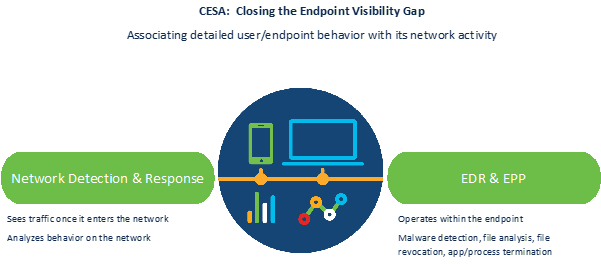
CESA includes the unparalleled endpoint behavioral presence of Cisco’s AnyConnect Network Visibility Module (NVM) and the info transformation strength of the Splunk analytics platform to greatly help deal with the endpoint presence gap left out by traditional EDR/EPP solutions and network security analytics systems.
So so how exactly does CESA make this happen for the SolarWinds breach? Well, it’s in fact in its wheelhouse.
CESA’s capability to associate what endpoint accessed what domain, along with what software protocols and procedures were used, enables immediate visibility from what endpoints are usually exposed-for both off-internet and on-net endpoints-within mins. How do we realize? Our CESA customers have told us.
Here’s an excerpt from the customer e-mail we received:
“(IR analyst) raised a great stage today while digging using this Solarwinds mess. We could actually connect local Windows procedures to domains which were documented in the IOC lists.
With this information we’re able to quickly know very well what our endpoint direct exposure was for several managed hosts from their NVM logs. In addition, it gave us a look at into additional domains that may have been connected with this attack, however, not publicly published yet.
We likely never could have seen this information and may not explain our contact with this severe risk. (AnyConnect) NVM logs in Splunk once more helped to save your day.”
In order to can get on this deep, below is really a sample CESA Splunk query tuned because of this scenario that the client used to discover phase-2 C&C activities from SolarWinds that their malware solution overlooked.
CESA Splunk-query:
earliest=-365d index=anyconnect (avsvmcloud OR freescanonline or digitalcollege OR deftsecurity OR thedoccloud OR virtualdataserver OR websitetheme OR panhardware OR zupertech.com OR highdatabase OR incomeupdate OR databasegalore) | areas *
Below can be an actual sample derive from this basic query showing information on an endpoint exposed:
pr=”6″ sa=”192.168.30.243″ sp=”59422″ da=”13.59.205.66″ dp=”443″ fst=”Sat May 16 19:38:31 2020″ fet=”Sat May 16 19:38:32 2020″ udid=”3AECA……2504C3The66″ liuid=”” liuida=”” liuidp=”” liuat=”32770″ pa=”NT AUTHORITYSYSTEM” paa=”NT AUTHORITY” pap=”Program” puat=”2″ pn=”SolarWinds.BusinessLayerHost.exe” ph=”A650DElectronic5170E4A1D6EB1DADE89BDE7215The30CD4C005BEC9C3241865B40220B9D0″ ppa=”NT AUTHORITYSYSTEM” ppuat=”2″ ppn=”providers.exe” pph=”9090E0E24E14709FB09B23B98572E0E61C810189E2DE8F7156021BC81C3B1BB6″ ibc=”445″ obc=”570″ ds=”.com” dh=”yykr55grenarianna67g.appsync-api.us-west-2.avsvmcloud.com” iid=”246″ mnl=””” mhl=”””
CESA dashboard example: Supervising endpoint traffic heading across split VPN tunnels
CESA closes the endpoint presence gap for events such as this a single with SolarWinds. But there are several other bad items that take place in this endpoint gap. CESA addresses endpoint safety visibility use situations such as:
- Unapproved SaaS and applications
- Endpoint security evasion
- Attribution of consumer to device to program to location
- and traffic
- Zero-trust monitoring
- Data loss recognition
- Day-zero malware and threat hunting
- Asset inventory
As well as the benefits that CESA provides to close up the endpoint visibility gap, Cisco Secure supplies a system approach with Cisco SecureX, a cloud-native, built-in system experience. With the Cisco Secure platform approach, you will be in a position to provide greater visibility, faster response and much more efficient security functions. Explore our integrated method of find out how it is possible to identify and contain 70% even more malicious intent and danger exposure with 85% much less dwell time.
Learn even more about how exactly CESA may protect your system and its own endpoints.



You must be logged in to post a comment.