Passwordless Protection: THE NEXT PHASE in Zero Trust
A Zero Trust Method
With the increasing threat scenery and latest workplace shifts to aid remote control users, many companies are deploying a Zero Trust security design to mitigate, detect, and react to cyber dangers across their environment.
Zero Trust principles assist drive back identity and access-based protection dangers by requiring all customers, whether inside or beyond your organization’s network, to end up being authenticated, authorized, and continuously validated for security position and construction checks before granted usage of applications and data.
Zero Trust depends on robust consumer authentication and gadget validation over system and endpoint safety to safeguard applications and information against new and emergent threats. Of protection enforcement at the system perimeter instead, Zero Trust targets safeguarding applications and surface area areas. Users and gadgets aren’t automatically trusted since they are actually behind the business perimeter or on a reliable network.
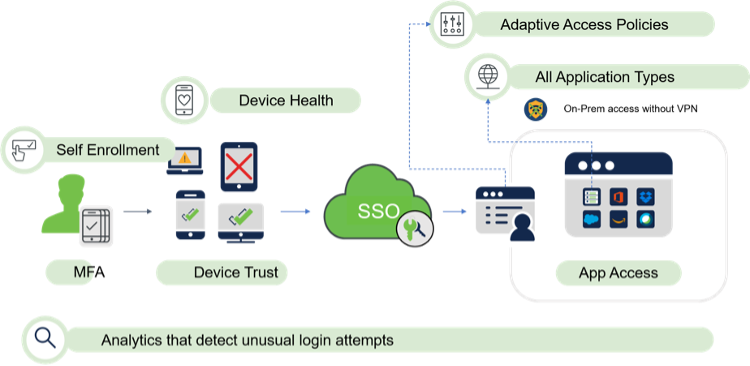
While each organization may have a varying method of deploying Zero Trust, the building blocks will be the same generally, including establishing rely upon every access demand and securing access throughout their network and apps.

Deploying a Zero Believe in architecture for a string is supplied by the workforce associated with benefits, including enhancing the end-user experience simply by allowing usage of some applications or assets that traditionally need VPN access plus streamlining authentication by means of multi-factor authentication (MFA). Businesses can leverage their current safety investments to deploy Zero Rely on often, including authentication, network accessibility control, logging, device administration, and endpoint reaction and detection, to boost their overall security position.
The Proceed to Passwordless
Exactly the same Zero Trust architectural components could be leveraged for another evolution in authentication also, that is passwordless access. The selling point of relocating to passwordless authentication will be that it unburdens IT departments which have to continually control and reset passwords for customers, that is time-consuming and costly to keep. For end-users, managing several passwords across various products and applications could be unwieldy, often leading to re-using exactly the same passwords which can be compromised and result in data breaches easily.
When implemented correctly, passwordless authentication eliminates the password from the authentication movement while maintaining MFA protection. In place, passwordless enhances safety while simultaneously reducing authentication friction for customers – a win-win for this infrastructure.
While the guarantee of passwordless authentication is exciting, it’s vital that you think strategically about deploying new technology. By putting the foundational the different parts of Zero Rely upon place very first, like SSO, MFA, and Device Trust, the changeover to passwordless will undoubtedly be smoother and much more secure. As passwordless is really a nascent technology pattern relatively, organizations should think about a phased rollout, targeting authentication and customers scenarios that produce the most sense from the technical and company perspective.
We’d want to hear everything you think. Ask a relevant question, Comment Below, and Remain Linked to Cisco Secure on interpersonal! Cisco Protected Social Channels Instagram
Facebook
Twitter
LinkedIn

You must be logged in to post a comment.