Optimizing cloud governance upon AWS: Integrating the NIST Cybersecurity Framework, AWS Cloud Adoption Framework, and AWS Well-Architected
Your method of security governance, risk administration, and compliance is definitely an enabler to electronic business and transformation agility. As more organizations improvement in their electronic transformation journey-empowered by cloud computing-security processes and companies cannot simply participate, they must lead for the reason that transformation.
<p>These days, many customers set up a security foundation making use of technology-agnostic risk administration frameworks-such as the Nationwide Institute of Specifications and Technologies (NIST) Cybersecurity Framework (CSF)-to understand their organization’s current capabilities, established goals, and create a program to improve and keep maintaining security posture. Nevertheless, you still need the proper model to optimize safety outcomes in the cloud. To assist you adapt your protection system for the cloud, AWS created two equipment the: AWS Cloud Adoption Framework (CAF) and AWS Well-Architected Framework. By complementing your risk-based basis with the AWS CAF, it is possible to integrate your organizational company drivers at level as you proceed to the cloud; and, when you’re prepared to implement particular workloads, you may use the AWS Well-Architected Framework to create, measure, and enhance your technical execution.</p>
Through this post, we shall explore the utilization and value of the NIST CSF as a framework to determine your security objectives, assess your organization’s current capabilities, and create a strategy to improve and keep maintaining your desired security posture. We shall then appearance at how to utilize the AWS CAF to assist you begin your electronic transformation trip in the AWS Cloud with methods around organizational procedures and governance at level that align to your organization drivers. Next, we shall cover the way the AWS Well-Architected Framework can enable safety guidelines at the workload degree. And lastly, we shall bring everything to show how these frameworks are mutually supportive together. Figure 1, below, displays how making use of these three complementary frameworks can optimize your protection outcomes. While they are able to independently be utilized, each builds upon another to reinforce and mature your cloud atmosphere and organizational security plan.
Utilizing the AWS Cloud Adoption Framework (CAF) plus AWS Well-Architected Framework to greatly help satisfy NIST Cybersecurity Framework (CSF) Objectives and Achieve the Target User profile

<div course="lb-skt-overlay lb-none-pad lb-modal lb-comp-content-container" data-lb-comp="modal" data-lb-modal-id="modal">
<div course="lb-modal-content">
<figure course="lb-img">
<a href="https://aws.amazon.com/blogs/security/optimizing-cloud-governance-on-aws-integrating-the-nist-cybersecurity-framework-aws-cloud-adoption-framework-and-aws-well-architected/#" data-lb-modal-trigger="modal"> <img src="https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2021/04/08/CSF-CAF-WA-Graphicr.png" alt="Figure 1: How exactly to make use of CAF and AWS Well-Architected to greatly help meet NIST CSF goals" class="cq-dd-picture"></the>
<br></figure>
</div>
<p> <a class="lb-modal-close" function="button" href="https://aws.amazon.com/blogs/security/optimizing-cloud-governance-on-aws-integrating-the-nist-cybersecurity-framework-aws-cloud-adoption-framework-and-aws-well-architected/#" title="Near"><span course="lb-sr-only">Near</period></the> </p>
</div>
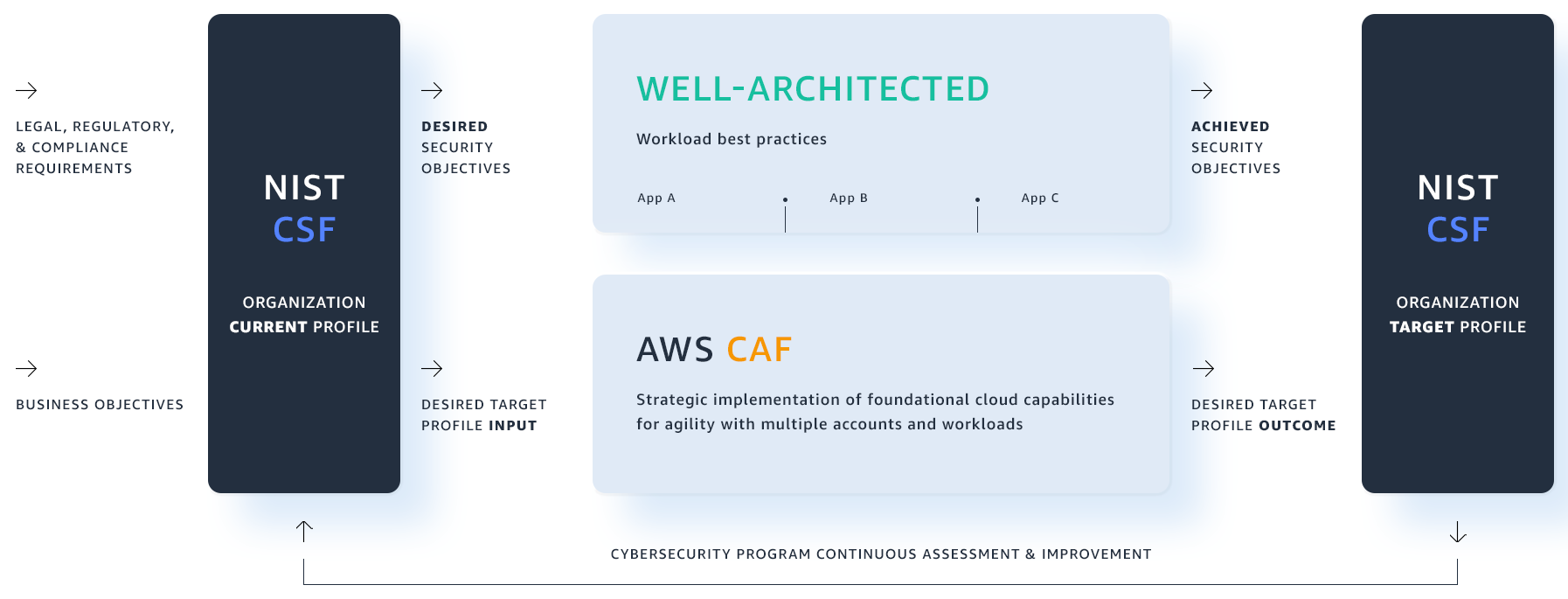
<p>Determine 1: How to make use of CAF and AWS Well-Architected to greatly help meet NIST CSF goals</p>
As shown in Physique 1, this technique involves the next :
- Establish your organization’s cybersecurity governance and preferred safety outcomes with the NIST CSF utilizing the Core features and implementation Tiers to generate your target user profile.
- Prepare for cloud migration and carry out a scalable foundation making use of AWS CAF to map those features in the cloud.
- Improve< and measure;/strong> your protection architecture and oeprational methods with AWS Well-Architected and choose the AWS providers to aid your security requirements.
As you function to arrange and optimize safety on AWS, it is very important understand that protection is a shared obligation between you and AWS, as described inside our shared responsibility design. This shared design can reduce your safety burden and assist you to attain your risk-based protection goals.
NIST CSF – Establish your safety governance and desired protection outcomes
 Ideally, your company is utilizing a framework for the organizational security program currently, but if not, it is possible to contemplate using the NIST CSF, an acknowledged risk management framework designed for use by any firm internationally, of sector or dimension regardless. The CSF offers a simple and effective way for communicating and understanding risk of security across your organization. Its technologies and industry-agnostic approach permits an outcome-based typical taxonomy which you can use across your organization, from the board degree to your specialized teams. We continue steadily to notice accelerating adoption of the CSF across countries and industries, and its principles have become standardized approaches, once we see in the most recent ISO 27103:2018 and draft ISO 27101 criteria.
Ideally, your company is utilizing a framework for the organizational security program currently, but if not, it is possible to contemplate using the NIST CSF, an acknowledged risk management framework designed for use by any firm internationally, of sector or dimension regardless. The CSF offers a simple and effective way for communicating and understanding risk of security across your organization. Its technologies and industry-agnostic approach permits an outcome-based typical taxonomy which you can use across your organization, from the board degree to your specialized teams. We continue steadily to notice accelerating adoption of the CSF across countries and industries, and its principles have become standardized approaches, once we see in the most recent ISO 27103:2018 and draft ISO 27101 criteria.
The NIST CSF includes three elements-Core, Tiers, and Profiles. The Primary includes five constant functions-Identify, Protect, Detect, Respond, and Recover-which it is possible to map to other manage or standards specifications as required by your organization. The Tiers characterize an organization’s maturity and aptitude for managing the CSF functions and controls, and the Profiles are designed to convey the organization’s “as is” and “to be” security postures. Collectively, these three components are created to enable your company to prioritize and address security risks in keeping with your mission and company needs. See the whitepaper Aligning to the NIST CSF within the AWS Cloud to comprehend how AWS resources and services can integrate together with your existing program.
NIST CSF use situation with identity
Unlike the procedure for developing on-premises datacenters and networks that focus on physical facilities, storage and computer hardware, and a network perimeter to safeguard what’s being built out, adopting the cloud begins with access and identification management with the selected cloud service provider. For AWS, this implies producing an AWS leveraging and accounts AWS IAM to generate users and organizations, define roles, and assign policies and permissions. Customers who are acquainted with the NIST CSF should understand the five functions-Identify, Protect, Detect, Respond, and Recover. If we consider the Protect perform as a good example, you can find 7 subcategories beneath the Identity Administration, Authentication and Access Manage (PR.AC) class:
- PR.AC-1: Credentials and identities are usually issued, maintained, verified, revoked, and audited for authorized products, processes< and users;/li>
- PR.AC-2: Physical usage of possessions is managed and safeguarded
- PR.AC-3: Remote entry is handled
- PR.AC-4: Entry authorizations and permissions are usually managed, incorporating the principles associated with least separation plus privilege of duties
- PR.AC-5: System integrity is protected (electronic.g., network segregation, system segmentation)
- PR.AC-6: Identities are usually bound and proofed to credentials and asserted within interactions
- PR.AC-7: Users, devices, along with other property are authenticated (electronic.g., single-factor, multi-aspect) commensurate with the chance of the transaction (electronic.g., individuals’ safety and privacy risks along with other organizational dangers)
Of the 7 subcategories, PR.AC-2 is an excellent example of the way the shared responsibility design is necessary. With most cloud solutions, physical security will be managed and applied by the cloud company and you reach inherit those controls. This is real for AWS, other than when you start using a hybrid cloud program, such as for example AWS AWS or Snowball Outposts, where we shall ship a physical gadget to work with in your on-prem atmosphere or in the industry, you are in charge of their physical security as the physical gadget is usually in your custody. For the purpose of this weblog, however, we shall concentrate on non-hybrid AWS cloud providers, and so we shall skip PR.AC-2 because of this use case. Clients retain the responsibility to control the physical protection of these datacenters and their actual physical assets that hook up to and access cloud solutions.
For the rest of the 6 subcategories, the AWS frameworks that people will discuss next contain guidelines and implementation sprints that may build out your governance structure, permissions and roles, access and authentication controls, and automated auditing.
The organizational context: Utilizing the AWS Cloud Adoption Framework – Ready your company for the cloud
 Cloud computing introduces a substantial shift within how technology will be procured, accessed, utilized, and managed. To operationalize and improve your security system for the cloud, your company needs to realize the brand new paradigm, and upgrade skills, adapt existing procedures, and introduce new procedures. The AWS Cloud Adoption Framework (CAF) assists organizations plan for an effective cloud migration, rather than the technical factors for an individual application lift-and-shift just, but with the intent to determine an organizational base to facilitate deploying, operating, and securing workloads from scale. This may consist of establishing a DevSecOps procedures and culture, coaching staff and incorporating brand new paradigms into function and assignments, building shared cloud administration and infrastructure provider environments, implementing main logging and governance, and other elements which will integrate with individual apps and use situations. Each organization’s path changes, so it’s vital that you plan forward and connect your organization goals and desired safety outcomes to the proper processes and systems.
Cloud computing introduces a substantial shift within how technology will be procured, accessed, utilized, and managed. To operationalize and improve your security system for the cloud, your company needs to realize the brand new paradigm, and upgrade skills, adapt existing procedures, and introduce new procedures. The AWS Cloud Adoption Framework (CAF) assists organizations plan for an effective cloud migration, rather than the technical factors for an individual application lift-and-shift just, but with the intent to determine an organizational base to facilitate deploying, operating, and securing workloads from scale. This may consist of establishing a DevSecOps procedures and culture, coaching staff and incorporating brand new paradigms into function and assignments, building shared cloud administration and infrastructure provider environments, implementing main logging and governance, and other elements which will integrate with individual apps and use situations. Each organization’s path changes, so it’s vital that you plan forward and connect your organization goals and desired safety outcomes to the proper processes and systems.
As shown in Number 2, the AWS CAF is made up of six perspectives which you can use for preparing and strategic considerations, predicated on common concepts that connect with most agencies. Three perspectives-Business, Individuals, and Governance-concentrate on the business, while technical factors are believed in the Platform, Protection, and Operations perspectives. Once we have observed with the NIST CSF, most of these perspectives impact management of security dangers and help reach your protection outcomes. Utilizing the AWS CAF, it is possible to structure your security plan to meet your preferred outcomes with agility, level, speed, and advancement that is included with AWS. The Security Viewpoint of the AWS CAF helps customers operationalize their security objectives through its four concepts: Directive, Preventive, Detective, and Responsive. Like the NIST CSF Identify, the Directive principle provides guidance to assist you understand your computer data and environment in the cloud. Preventive provides assistance to assist you operate selected safety controls in AWS; Detective offers a means to analyze the surroundings and alert on dangers and anomalies; and Responsive appears to mitigate detected dangers then, with an focus on automation.

Figure 2: CAF perspectives
The AWS CAF Safety Perspective is made up of 5 core + 5 augmenting security epics-or themes-as depicted in Figure 3. In keeping with the concepts of the NIST CSF, an organization’s foundational abilities concentrate on identifying, applying, and scaling security guidelines at the scheduled system and organizational levels to aid business outcomes. Protection epics begin with accessibility and identity management because the backbone to secure cloud deployment.

Figure 3: Safety epics
AWS CAF use situation with identity
Once you consider the Identity and Access Management (IAM) sprint from the AWS CAF Security Epics (Figure 3), you visit a few AWS providers being configured and put on govern IAM at scale. Working bottom-up, you can find three tiers to take into account when designing and creating your IAM security-Put into action IAM Guardrails, Operationalize IAM, and Privileged Access Administration. At AWS, we change the mindset from “locking down” something, which implies inflexibility that may impact company and usability agility, to the idea of “guardrails” where protection is defined by outer limits that allow freedom of motion within those constraints. This enables for more versatility for developers also it operators to explore brand new methods and technology to meet up dynamic market changes. For AWS IAM specifically, look at applying guardrails through solutions such as AWS Companies, AWS IAM, and AWS Manage Tower. For instance, AWS Control Tower supplies the easiest way to create and govern a fresh, secure, multi-account AWS atmosphere based on guidelines established through AWS’ encounter dealing with thousands of enterprises because they proceed to the cloud.
Next, operationalize IAM by federating having an existing directory support, or developing a cloud directory, and implementing accounts and access manage lifecycles. And, lastly, explore options to apply a privileged gain access to management (PAM) treatment for protect these essential accounts. AWS Secrets Techniques and Manager Manager Periods Manager are two providers that can help with this objective.
By using this small excerpt associated with the AWS CAF, sufficient reason for your input in to the process, you can style your AWS IAM to meet up the NIST CSF subcategories PR.AC-1, 3, 4, 6, and 7 highlighted over.

Figure 4: CAF Identity sprint
Protected and resilient program architecture: Making use of AWS Well-Architected Framework to gauge and enhance your workload architecture
 The AWS Well-Architected Framework can help you understand factors and key decision factors for building techniques on AWS- this is a framework for guiding and analyzing your workload architectures. Through the use of AWS Well-Architected, you shall learn architectural guidelines for designing and working reliable, secure, effective, and cost-effective techniques in the cloud. It offers a method for you yourself to consistently gauge your architectures against guidelines and identify locations for improvement. The procedure for reviewing an architecture is really a constructive discussion about architectural choices and getting AWS Well-Architected systems escalates the likelihood of business achievement.
The AWS Well-Architected Framework can help you understand factors and key decision factors for building techniques on AWS- this is a framework for guiding and analyzing your workload architectures. Through the use of AWS Well-Architected, you shall learn architectural guidelines for designing and working reliable, secure, effective, and cost-effective techniques in the cloud. It offers a method for you yourself to consistently gauge your architectures against guidelines and identify locations for improvement. The procedure for reviewing an architecture is really a constructive discussion about architectural choices and getting AWS Well-Architected systems escalates the likelihood of business achievement.
To aid customers within measuring and documenting their workloads, you can expect the AWS Well-Architected Tool (notice Figure 5)- a questionnaire on the AWS Management Gaming console that can help you answer, “Am We well-architected?” AWS Well-Architected targets the workload level-your infrastructure, systems, information, and processes-by examining five primary pillars: Operational Excellence, Protection, Reliability, Performance Performance, and Price Optimization.

Figure 5: Well-Architected Device
You may use AWS Well-Architected for developing, evaluating, and improving your architectures continuously. After preparing, preparing, and scaling for cloud migration utilizing the Cloud Adoption Framework, AWS Well-Architected can inform the way you secure particular workloads based on the security outcomes (and Focus on Profile) used from the NIST CSF.
AWS Well-Architected use situation with identity
You can find five areas in the security pillar of the AWS Well-Architected Framework: Identity and Access Management (IAM), Detection, Infrastructure Protection, Data Protection, and Incident Response. AWS Well-Architected provides assistance for secure execution and approaches for choosing the right AWS solutions to place these core security procedures set up in your workloads. You may notice that these certain specific areas act like those beneath the AWS CAF security perspective. That’s because those features which were determined at the strategic levels should be resolved at the specialized layer. That traceability from company requirement to technical technique to specialized architecture and functions is really a crucial element to ensure safety is used at all degrees of your organization, and that it’s meeting an ongoing business need.
Once you go through the IAM of the AWS Well-Architected protection pillar, you’ll see quite a few workload-level guidelines for pursuits like multi-factor authentication, usage of temporary credentials, auditing, and least privilege. Following you could be helped by these recommendations meet up with NIST CSF subcategories 1, 3, 4, 6, and 7 for individual programs and workloads, for every if needed uniquely.
For instance, PR.AC-1 includes a target to audit for authorized gadgets, users, and providers. Although there are many options to carry out auditing, and places to focus on, among the AWS Well-Architected guidelines would be to audit and rotate credentials periodically. Following general guidance below alongside prescriptive AWS service assistance, you can style your workload to greatly help meet this necessity.
To get this use case, AWS Well-Architected recommends that you transition from user and group permissions to the usage of inherited roles for individual and machine principals, retire long-term access and credentials keys for short-term credentials and MFA where suitable, and use automation to confirm controls are usually enforced then.
Putting everything together
Making use of NIST CSF, AWS CAF, and AWS Well-Architected, it is possible to tailor your method of incorporate security management methods for the cloud journey best. These three frameworks present related, but specific lenses on how best to approach security for the organization, connecting company outcomes and goals in order to your security program.
Utilizing the NIST CSF, it is possible to develop an organizational knowing to managing security challenges. Utilizing the AWS CAF, it is possible to plan your cloud safety approach and map routines to security controls working in the cloud and level them throughout the business. This can assist you to build out your architecture. You may use AWS Well-Architected to regularly gauge your workload against guidelines and identify locations for enhancement.
What’s Next?
The intent of the blog post would be to demonstrate the way the AWS Cloud Adoption Framework (CAF) and AWS Well-Architected will help you align with and meet up with the NIST Cybersecurity Framework (CSF) objectives, and offer an understanding they are supportive mutually.
Here are some recommendations to assist you benefit from this new knowing and show you through the various frameworks which will help you meet your protection and compliance goals:
- Download and evaluation:
- Utilize the AWS Well-Architected tool to execute a self-assessment of one’s alignment to AWS guidelines. When you have questions concerning the results from your own well-architected review and:
- there is no need a support program and so are not assigned an AWS account executive, leverage the free AWS Forums.
- you have Basic, Developer, or even Business Assistance, and you also have an designated AWS accounts executive, request a gathering with a options architect to go over.
- you have Business Support, contact your aws accounts executive and technical accounts manager (TAM) to demand a meeting to go over.
- If you’re no existing consumer, start your own trip on AWS by < calling us;a href=”https://aws.amazon.com/contact-all of us/” target=”_blank” rel=”noopener noreferrer”>here.
- If you’re searching for migration assistance, consider AWS Professional Providers < and offerings;a href=”https://aws.amazon.com/partners/consulting/” focus on=”_blank” rel=”noopener noreferrer”>AWS consulting companions that can help with implementing the AWS WAF and CAF in your cloud migration or even optimization strategy.
- If you’re not used to AWS, there are several in-person and online certification< and training;/a> options supplied by AWS and our companions.
Should you have feedback concerning this post, submit remarks in the Remarks area below.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.

You must be logged in to post a comment.