Migrate your Windows PKI from Microsoft Active Directory Certificate Services to AWS Private CA Connector for Active Directory
When you migrate your Windows environment to Amazon Web Services (AWS), you might need to address certificate management for computers and users in your Active Directory domain. Today, Windows administrators commonly use Active Directory Certificate Services (AD CS) to support this task. In this post, we will show you how to migrate AD CS to AWS Private Certificate Authority by using the AWS Private CA Connector for Active Directory.
<p>AWS Private CA provides a highly available private certificate authority (CA) service without the upfront investment and ongoing maintenance costs of operating your own private CA. Using the APIs that AWS Private CA provides, you can create and deploy private certificates programmatically. You also have the flexibility to create private certificates for applications that require custom certificate lifetimes or resource names. With AWS Private CA, you can create your own CA hierarchy and issue certificates for authenticating internal users, computers, applications, services, servers, and devices and for signing computer code.</p>
<h2>Use cases for certificate services that integrate with Active Directory</h2>
<p>AD CS is commonly used in enterprise environments because it integrates certificate management with Active Directory authentication, authorization, and policy management. A common use case for AD CS is certificate auto-enrollment. Using <a href="https://www.windows-active-directory.com/benefits-of-group-policy-in-active-directory.html" target="_blank" rel="noopener">AD Group Policies</a>, you can configure certificates to automatically be created for users as they log in to the domain, or you can configure computer certificates, which are associated with each workstation or server that joins the domain. You can then use these certificates for authentication or digital signature purposes. A common use case is for authentication of devices to protected networks, such as wired networks that require 802.1x authentication or wireless networks that are protected by WPA2/3 with EAP-TLS authentication. Auto-enrolled computer and user certificates are also commonly used to authenticate VPN connections.</p>
<p>In addition to certificate auto-enrollment, AD CS also integrates with Active Directory to publish certificate information directly to the user and computer objects in Active Directory. In this way, you can integrate the lifecycle management of the certificates directly into your existing processes for managing the lifecycle of AD users and computers that are joined to the domain.</p>
<h2>Options to deploy certificate services that integrate with Active Directory on AWS</h2>
<p>To migrate your Windows environment to the cloud, you probably want to retain the capabilities of a CA that integrates with Active Directory. Although you can migrate AD CS directly to AWS and run it on an <a href="https://aws.amazon.com/ec2/" target="_blank" rel="noopener">Amazon Elastic Compute Cloud (Amazon EC2)</a> instance running Windows, we will show you how to use AWS Private CA with the Connector for AD to provide an Active Directory integrated CA that offers the benefits of AD CS without the need to manage AD CS or hardware security modules (HSMs).</p>
<h2>Why migrate your on-premises CA to AWS Private CA?</h2>
<p>Migrating AD CS to AWS Private CA has several benefits. With AWS Private CA, you get simplified certificate management, eliminating the need for an on-premises CA infrastructure and reducing operational complexity. AWS Private CA provides a managed service, reducing the operational burden and providing high availability and scalability. Additionally, it integrates with other AWS services, so it’s simpler to manage and deploy certificates across your infrastructure. The centralized management, enhanced security features, and simplified workflows in AWS Private CA can streamline certificate issuance and renewal processes, enabling you to more efficiently achieve your security goals.</p>
<p>AWS manages the underlying infrastructure, which can help reduce costs, and automation features help prevent disruptions that expired certificates could cause. AWS Private CA operates as a Regional service with an SLA of 99.9% availability. For environments that require the highest level of availability, you can deploy CAs in multiple AWS Regions by following the guidance on <a href="https://docs.aws.amazon.com/privateca/latest/userguide/disaster-recovery-resilience.html#disaster-recovery" target="_blank" rel="noopener">redundancy and disaster recovery</a> in the documentation.</p>
<p>AWS Private CA Connector for AD extends the certificate management of Private CA to AD environments. With the Connector for AD, you can use Private CA to issue certificates for AD users and computers joined to your domain. This includes integration with Windows Group Policy for certificate autoenrollment.</p>
<h2>How do I migrate to the Connector for AD?</h2>
<p>Transitioning from an existing AD CS server to the Connector for AD involves several steps.</p>
<h3>Assessment and planning</h3>
<p>Before you begin, identify the use cases for your existing AD CS server and how certificates are issued. In this post, we focus on certificates that are auto-enrolled by using a Group Policy, but you might have other use cases where you must manually enroll certificates by using the Web Enrollment server or APIs. These might include use cases for signing software packages or web server certificates for intranet applications. Start by creating a certificate inventory from your existing AD CS server.</p>
<h4>To create a certificate inventory from your existing AD CS server</h4>
<ol>
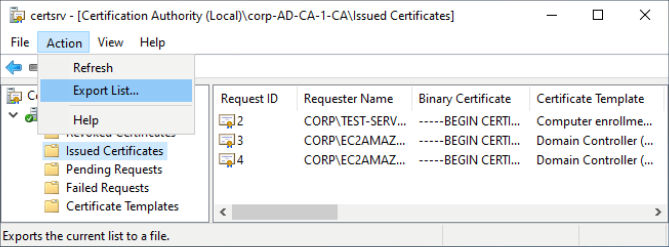
<li>In the Microsoft CA console, select <strong>Issued Certificates</strong>.</li>
<li>From the <strong>Action</strong> menu, select <strong>Export List</strong>.<br>
<div id="attachment_33681" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33681" src="https://infracom.com.sg/wp-content/uploads/2024/03/img1-1.png" alt="Figure 1: Export a list of existing certificates" width="669" height="247" class="size-full wp-image-33681">
<p id="caption-attachment-33681" class="wp-caption-text">Figure 1: Export a list of existing certificates</p>
</div> </li>
</ol>
<p>This produces a CSV file of the certificates that the server issued. To determine which certificates were created as part of an auto-enrollment policy and to identify special cases that require manual attention, sort this file by <strong>Certificate Template</strong>.</p>
<h3>Set up AWS Private CA and the Connector for AD</h3>
<p>To complete the initial setup of the Connector for AD, see <a href="https://docs.aws.amazon.com/privateca/latest/userguide/connector-for-ad-getting-started.html" target="_blank" rel="noopener">Getting started with AWS Private CA Connector for Active Directory</a>. When you complete the setup, you can start transitioning enrollment to the new CA.</p>
<h3>Configure trust for the new CA</h3>
<p>Depending on where you put the new private CA in your organization’s public key infrastructure (PKI) hierarchy, you might want to make sure that its certificate is imported into all of the client trust stores before you issue new certificates using the CA. For Windows devices, creation of the Connector for AD imports the CA certificate into Active Directory, and automatically distributes it to the trust stores of domain-joined computers.</p>
<p>For non-Windows devices, you need to evaluate other use cases for issued certificates on the network and follow vendor instructions for updating trust stores. For example, if you use client certificates for wired 802.1x and Wi-Fi Protected Access (WPA) enterprise authentication, you need to import the new root CA certificate into the trust stores of the RADIUS servers that you use for authentication.</p>
<h3>Export the CA certificate</h3>
<p>The next step is to export the certificate by using the <a href="https://aws.amazon.com/console/" target="_blank" rel="noopener">AWS Management Console</a>.</p>
<h4>To export the certificate</h4>
<ol>
<li>Open the <a href="https://console.aws.amazon.com/acm-pca/home" target="_blank" rel="noopener">AWS Private CA console</a>.</li>
<li>Navigate to your private CA.</li>
<li>Choose the <strong>CA certificate</strong> tab.</li>
<li>Select <strong>Export certificate body to a file</strong>. <p>For import into an Active Directory Group Policy Object (GPO), name the exported file with a <strong>.cer </strong>file extension.</p>
<div id="attachment_33682" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33682" src="https://infracom.com.sg/wp-content/uploads/2024/03/img2.jpg" alt="Figure 2: Export the CA certificate" width="740" class="size-full wp-image-33682">
<p id="caption-attachment-33682" class="wp-caption-text">Figure 2: Export the CA certificate</p>
</div> </li>
</ol>
<h3>Transition certificate enrollment to the new CA</h3>
<p>After you configure AWS Private CA and the Connector for AD and update your trust stores as necessary, you can begin to transition certificate enrollment to the new CA. In Active Directory domains, certificates are typically created automatically by using an auto-enrollment Group Policy. To migrate enrollment to your new CA, you need to configure certificate templates with the appropriate properties to match your requirements, assign permissions to the templates, and configure the Group Policy to point the enrollment client on Windows devices to the new CA.</p>
<h4>Configure certificate templates</h4>
<p>Certificate templates define the enrollment policy on a CA. An Active Directory CA only issues certificates that conform to the templates that you have configured. Using the certificate inventory that you collected from your existing AD CS server, you should have a list of certificate templates that are in active use in your environment and that you need to replicate in the Connector for AD.</p>
<p>Start by noting the properties of these certificate templates on your existing AD CS server.</p>
<h4>To note the properties of the certificate templates</h4>
<ol>
<li>Open the <strong>Certificate Authority</strong> console on your AD CS server.</li>
<li>Navigate to the <strong>Certificate Templates</strong> folder.</li>
<li>From the <strong>Action</strong> menu, select <strong>Manage</strong>. This opens the <strong>Certificate Templates </strong>console, which shows a list of the certificate templates available in Active Directory.<br>
<div id="attachment_33683" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33683" src="https://infracom.com.sg/wp-content/uploads/2024/03/img3.jpg" alt="Figure 3: Identify certificate templates" width="740" class="size-full wp-image-33683">
<p id="caption-attachment-33683" class="wp-caption-text">Figure 3: Identify certificate templates</p>
</div> </li>
<li>For each certificate that is in active use, open it and take note of its settings, particularly the following:
<ul>
<li>Template name, validity period, and renewal period from the <strong>General </strong>tab.</li>
<li>Certificate recipient compatibility from the <strong>Compatibility</strong> tab.</li>
<li>Certificate purpose and associated checkboxes in addition to whether a private key is allowed to be exported from the <strong>Request Handling</strong> tab.</li>
<li>Cryptography settings from the <strong>Cryptography</strong> tab.</li>
<li>The extensions configured from the <strong>Extensions</strong> tab.</li>
<li>Settings for certificate subject and subject alternate name from the <strong>Subject Name</strong> tab.</li>
<li>Review the <strong>Security</strong> tab for the list of Active Directory users and groups that have <strong>Enroll</strong> or <strong>AutoEnroll</strong> permissions. The other permission settings, which control which AD principals have the ability to modify or view the template itself, don’t apply to AWS Private CA because IAM authorization is used for these purposes.<br>
<div id="attachment_33684" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33684" loading="lazy" src="https://infracom.com.sg/wp-content/uploads/2024/03/img4.jpg" alt="Figure 4: Certificate template properties" width="424" height="593" class="size-full wp-image-33684">
<p id="caption-attachment-33684" class="wp-caption-text">Figure 4: Certificate template properties</p>
</div> </li>
</ul> </li>
</ol>
<p>After you gather the configuration details for the certificate templates that are in active use, you need to configure equivalent templates within the Connector for AD.</p>
<h4>To configure templates in the Connector for AD</h4>
<ol>
<li>Open the <a href="https://console.aws.amazon.com/acm-pca/home" target="_blank" rel="noopener">AWS Private CA console</a>.</li>
<li>Navigate to <strong>Private CA Connector for AD</strong>.</li>
<li>Select your connector.</li>
<li>In the <strong>Templates</strong> section, choose <strong>Create template</strong>.<br>
<div id="attachment_33685" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33685" src="https://infracom.com.sg/wp-content/uploads/2024/03/img5.jpg" alt="Figure 5: Certificate template configuration in the Connector for AD" width="740" class="size-full wp-image-33685">
<p id="caption-attachment-33685" class="wp-caption-text">Figure 5: Certificate template configuration in the Connector for AD</p>
</div> </li>
<li>You can then begin configuring your certificate template by using the settings that you obtained from your existing AD CS server. For a complete description of the settings that are available in the certificate template, see <a href="https://docs.aws.amazon.com/privateca/latest/userguide/create-ad-template.html" target="_blank" rel="noopener">Creating a connector template</a>.<br>
<div id="attachment_33686" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33686" src="https://infracom.com.sg/wp-content/uploads/2024/03/img6.jpg" alt="Figure 6: Certificate template settings" width="740" class="size-full wp-image-33686">
<p id="caption-attachment-33686" class="wp-caption-text">Figure 6: Certificate template settings</p>
</div> </li>
<li>Assign permissions to the template. <p>You must manually enter the Active Directory Security Identifier (SID) of the user or group that you are assigning the <strong>Enroll</strong> or <strong>Auto-enroll</strong> permission to. For instructions on how to use PowerShell to obtain the SID of an Active Directory object, see <a href="https://docs.aws.amazon.com/privateca/latest/userguide/ad-groups-permissions.html" target="_blank" rel="noopener">Managing AD groups and permissions for templates</a>.</p> <p>We recommend that you initially assign your certificate templates to a small test group that contains a set of Active Directory computers or users that will be used to test the new CA. When you are confident that the new CA issues certificates correctly, you can modify the permissions to include the full set of Active Directory user and computer groups that were assigned to the template on your original AD CS server.</p> </li>
</ol>
<h3>Configure Group Policy for automatic certificate enrollment</h3>
<p>With the Connector for AD configured with the required certificate templates, you are ready to configure the AD Group Policy to enable automatic enrollment of user and computer certificates. We suggest that you start with a test organizational unit (OU) in Active Directory, where you can put user and computer objects to make sure that enrollment is working properly. The existing AD CS server and the Connector for AD can continue to coexist until you are ready to replace the certificates.</p>
<p>In this example, you configure a new Group Policy object that is linked to an OU called Test OU, where you will place computer objects for testing.</p>
<h4>To configure a new Group Policy object</h4>
<ol>
<li>Within the Group Policy object, locate the settings for controlling enrollment under <strong>Computer Configuration > Policies > Windows Settings > Security Settings > Public Key Policies</strong>.<br>
<div id="attachment_33687" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33687" src="https://infracom.com.sg/wp-content/uploads/2024/03/img7.jpg" alt="Figure 7: Active Directory Group Policy Editor" width="740" class="size-full wp-image-33687">
<p id="caption-attachment-33687" class="wp-caption-text">Figure 7: Active Directory Group Policy Editor</p>
</div> </li>
<li>Configure the <strong>Certificate Services Client – Certificate Enrollment Policy</strong> to point clients at the URL of the Connector for AD:
<ol>
<li>Set the <strong>Configuration Model</strong> to <strong>Enabled</strong>.</li>
<li>Add a new item to the <strong>Certificate enrollment policy list</strong>.<br>
<div id="attachment_33688" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33688" loading="lazy" src="https://infracom.com.sg/wp-content/uploads/2024/03/img8.jpg" alt="Figure 8: Certificate Services Client Group Policy settings" width="418" height="482" class="size-full wp-image-33688">
<p id="caption-attachment-33688" class="wp-caption-text">Figure 8: Certificate Services Client Group Policy settings</p>
</div> </li>
</ol> </li>
<li>Enter the URL of your connector and leave the <strong>Authentication mode</strong> set to <strong>Windows Integrated</strong>. Then choose <strong>Validate</strong>.<br><blockquote>
<p><strong>Note:</strong> You can find the URL of your connector in the AWS Private CA Connector for AD console under <strong>Certificate enrollment policy server endpoint</strong>.</p>
</blockquote>
<div id="attachment_33689" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33689" src="https://infracom.com.sg/wp-content/uploads/2024/03/img9.jpg" alt="Figure 9: Connector details" width="740" class="size-full wp-image-33689">
<p id="caption-attachment-33689" class="wp-caption-text">Figure 9: Connector details</p>
</div> </li>
<li>After you save your configuration, remove the <strong>Active Directory Enrollment Policy</strong> from the list so that the Group Policy only references the Connector for AD. A completed configuration will look similar to the following:<br>
<div id="attachment_33690" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33690" loading="lazy" src="https://infracom.com.sg/wp-content/uploads/2024/03/img10.jpg" alt="Figure 10: Certificate services client settings with Active Directory enrollment policy removed" width="417" height="479" class="size-full wp-image-33690">
<p id="caption-attachment-33690" class="wp-caption-text">Figure 10: Certificate services client settings with Active Directory enrollment policy removed</p>
</div> </li>
<li>From within the Group Policy editor, open the <strong>Certificate Services Client – Auto-enrollment</strong> policy to configure auto-enrollment of computer certificates. Set <strong>Configuration Model</strong> to <strong>Enabled</strong>, and select the following:
<ul>
<li><strong>Renew expired certificates, update pending certificates, and remove revoked certificates</strong></li>
<li><strong>Update certificates that use certificate templates</strong><br>
<div id="attachment_33691" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33691" loading="lazy" src="https://infracom.com.sg/wp-content/uploads/2024/03/img11.jpg" alt="Figure 11: Certificate Services client auto-enrollment policy settings" width="413" height="527" class="size-full wp-image-33691">
<p id="caption-attachment-33691" class="wp-caption-text">Figure 11: Certificate Services client auto-enrollment policy settings</p>
</div> </li>
</ul> </li>
</ol>
<p>After you configure the Group Policy, computers in OUs that the Group Policy is linked to will start automatically enrolling certificates by using AWS Private CA, subject to the permissions defined on the certificate templates. To review the progress of certificate enrollment, use <a href="https://docs.aws.amazon.com/privateca/latest/userguide/PcaAuditReport.html" target="_blank" rel="noopener">private CA audit reports</a>.</p>
<p>When you complete testing and gain confidence in your certificate roll-out, extend the scope of the GPO and Active Directory permissions on the certificate templates to cover additional users and computers.</p>
<h3>Revocation and decommissioning</h3>
<p>You can continue to review the Private CA audit reports to confirm progress with auto-enrollment of certificates from the new CA. If you have computers that infrequently connect to the network, this can take some time. As part of this process, address your use cases that aren’t covered by auto-enrollment, which you identified from your initial certificate inventory. These might include web server certificates for internal applications or code-signing certificates for distributing software packages. You can issue replacement certificates for these use cases by using the AWS Private CA APIs or CLI without depending on the Active Directory integration. For more information, see <a href="https://docs.aws.amazon.com/privateca/latest/userguide/PcaIssueCert.html" target="_blank" rel="noopener">Issuing private end-entity certificates</a>.</p>
<p>After the required certificates have been enrolled and you have confirmed that the services that depend upon those certificates are functioning correctly, it’s time to revoke issued certificates and decommission your existing AD CS server. Microsoft provides detailed documentation for <a href="https://learn.microsoft.com/en-us/troubleshoot/windows-server/windows-security/decommission-enterprise-certification-authority-and-remove-objects" target="_blank" rel="noopener">properly revoking certificates and decommissioning an Enterprise CA</a>, including clean-up of related AD objects.</p>
<h2>Conclusion</h2>
<p>In this post, we covered some use cases for Active Directory integrated certificate management in Windows environments and introduced the new AWS Private CA Connector for Active Directory. AWS Private CA and the Connector for AD can help you reduce operational overhead, enabling you to simplify the process of provisioning certificates while maintaining the Active Directory integration that you are accustomed to in a Microsoft AD CS environment. You learned how to evaluate your existing Microsoft CA and migrate to AWS Private CA with the Connector for AD, with a specific focus on auto-enrollment of certificates, which is commonly used in enterprise environments for device and end-user authentication.</p>
<p>To learn more about the services described in the post, see the documentation for <a href="https://docs.aws.amazon.com/privateca/latest/userguide/connector-for-ad.html" target="_blank" rel="noopener">Connector for AD</a>,<a href="https://docs.aws.amazon.com/privateca/latest/userguide/PcaWelcome.html" target="_blank" rel="noopener"> AWS Private CA</a> , <a href="https://docs.aws.amazon.com/privateca/latest/userguide/ca-best-practices.html" target="_blank" rel="noopener">CA best practices</a> and <a href="https://docs.aws.amazon.com/directoryservice/latest/admin-guide/what_is.html" target="_blank" rel="noopener">AWS Directory Services</a>. You can get started creating CAs in AWS Private CA by using the console.</p>
<p>If you have feedback about this post, submit comments in the Comments section below. If you have questions about this post, start a new thread on the <a href="https://repost.aws/tags/TAJ7zd4vjzSfC_8JNlsbq2tA/aws-certificate-manager" rel="noopener" target="_blank">AWS Certificate Manager re:Post</a> or <a href="https://console.aws.amazon.com/support/home" rel="noopener" target="_blank">contact AWS Support</a>.</p>
<!-- '"` -->
