
Microsoft provides Swap Server protective tool to greatly help SMBs stymie zero-day attacks
Microsoft Tuesday issued instructions and a one-click tool to smaller businesses with on-premises Trade servers to patch the vulnerability very first disclosed by the business March 2, and which criminals have already been making use of to spy upon victims’ communications along with obtain access to other areas of their networks.
“We noticed that there is a require for a straightforward, easy to use, automated solution that could meet up with the needs of clients using both out-of-assistance and current variations of on-premises Swap Server,” Microsoft mentioned in a post to an organization blog related to the MSRC (Microsoft Security Analysis Center) Team.
The tool, dubbed (with the most common Microsoft knack of catchy monikers), “Microsoft Trade On-Premises Mitigation Tool,” is targeted at customers that don’t possess devoted IT personnel or are even “unfamiliar,” Microsoft said, with the patching and update process. The device works on Exchange 2013, 2016, and 2019, the backed editions of the server software currently. (Exchange 2013 will undoubtedly be backed until April 2023, until October 2025 as the other two editions will undoubtedly be supported.)
 Microsoft
Microsoft
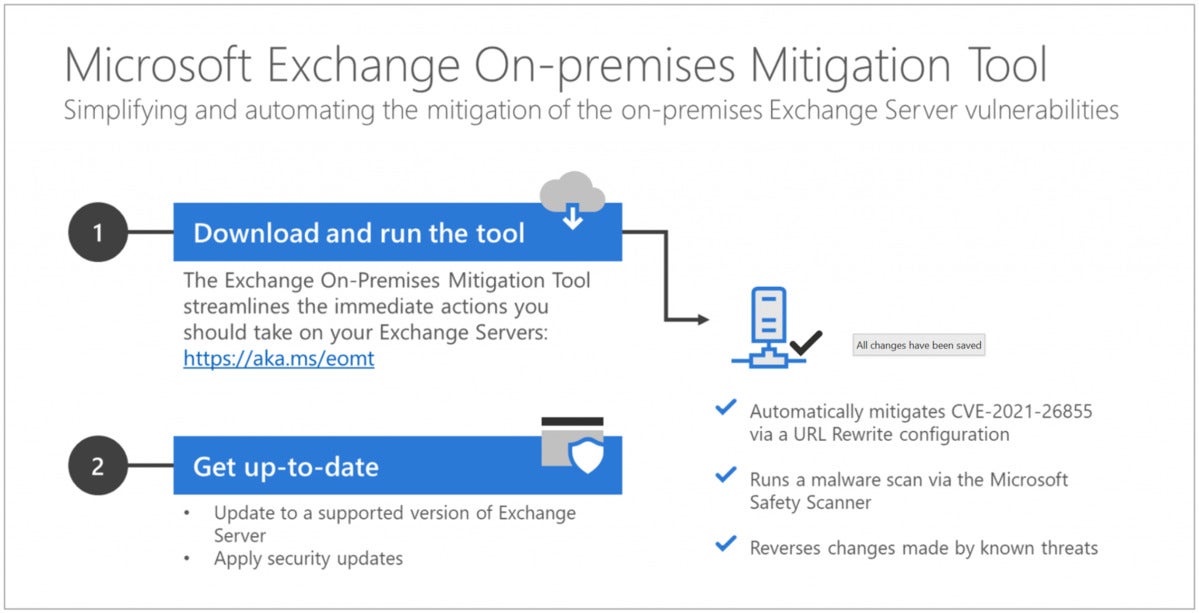
Microsoft’s free device for smaller businesses mitigates against episodes on Exchange Server making use of one of the many vulnerabilities the Redmond, Clean. developer patched March 2. (Click picture to enlarge it.)
In accordance with Microsoft, the device is “not just a alternative to the Exchange security upgrade,” but a stopgap calculate to guard vulnerable Exchange servers before consumer can deploy the specific fix.
The tool does a number of things, notably configuring Swap Server to institute a mitigation for the CVE-2021-26855 vulnerability (among four now being exploited by cyber criminals). The tool furthermore operates a malware scan making use of “Microsoft Safety Scan,” a free of charge utility that both sniffs out exploits and tries to reverse any apparent changes created by attackers. (The scanner, that may also end up being manually downloaded from right here , will be live for the next 10 days. Users may trigger this for additional scans in any right time following the mitigation during that stretch.)
This was not the initial automated script Microsoft has offered customers to mitigate against attacks in line with the Trade Server bugs patched on March 2. Three times from then on, Microsoft submitted links to a number of mitigation tools , which includes “ExchangeMitigations.ps1,” the PowerShell script that tackled many of the patched vulnerabilities, which includes CVE-2021-26855, that was addressed by the newer On-Premises Mitigation Tool furthermore.
“We recommend this script on the previous ExchangeMitigations.ps1 script since it [is] tuned in line with the most recent threat intelligence,tuesday ” Microsoft said. “For those who have currently started with another script, it really is fine to change to the one.”
The Swap Server vulnerabilities were patched March 2 in another of Microsoft’s rare out-of-band updates, meaning the update premiered beyond your usual second-Tuesday-of-each-month schedule.
Microsoft’s best way to obtain info on the vulnerabilities and the exploits of these are available in a safety post on the Exchange Server attacks.
The attacks rapidly jumped from those contrary to the largest organizations to a more substantial pool of victims because the amount of bad actors in it expanded, that unusual alone.
Additional guidance for all those in charge of maintaining the security of Exchange Server software are available in a March 16 post to the MSRC blog .
