
Microsoft Patch Alert: June 2020
There’s never a dull moment for folks who try to keep Windows and Office patched.
Windows 10 version 2004 continues to make slow inroads among the “Go ahead and kick me” crowd, in spite of its (now documented) lack of update deferral settings, while those of us who are still trying to keep Win10 versions 2009, 2003 and 1809 afloat have our hands full.
June saw two truly innovative patching methods: A fix for a Windows bug delivered as an update to Office Click-to-Run and a fix for a different Windows bug delivered through the Microsoft Store.
If you can’t fix things the normal way, I guess there’s always the back door.
The two printer bugs
All of the Win10 cumulative updates in June broke some printers, some of the time. The damage fell into two heaps:
- USB-attached printers have to be powered up before you fire up Windows per Knowledge Base article 4566779: “If you connect a USB printer to Windows 10 version 1903 or later, then shut down Windows and disconnect or shut off the printer, when you start Windows again the USB printer port will not be available in the list of printer ports. Windows will not be able to complete any task that requires that port…. We are working to fix the issue in a future version of the operating system.”
- Networked printers with drivers based on PCL 5 or earlier versions of PCL 6 (the PostScript printing standards) may suddenly freeze, or just not work at all per the Windows Release Information Status page: “Print spooler may error or close unexpectedly when attempting to print and no output will come from affected printer. You might also encounter issues with the apps you are attempting to print from. You might receive an error from the app or the app may close unexpectedly. Note This issue might also affect software-based printers, for example printing to PDF.”
Microsoft fixed the second set of bugs with a manual-download-only out-of-band patch, known as KB 4567512. If you installed one of this month’s cumulative updates and your networked printers suddenly stopped, you have to know (by osmosis?) that the problem lies with the update, and either roll back the update, upgrade your print driver to one that supports a more recent version of PCL 6, or manually download and install this patch.
The Outlook drive-by
Although the official documentation mentions the conflict only obliquely, the June Windows cumulative updates were apparently responsible for the June 2 and 9 versions of Microsoft 365 (nee Office 365) Click-to-Run refusing to open.
After updating to Version 2005 Build 12827.20268 or higher and starting Outlook you may see the following error prompt: “Something is wrong with one of your data files and Outlook needs to close.” The Outlook Team is investigating this issue with the Windows Team. We are not sure yet if the primary fix will come from Outlook or Windows. When we have more information on fix details we will add them here.
Microsoft fixed the bug in Windows by releasing an update to Office (er, Microsoft) 365, on June 25:
This issue is fixed in Monthly Channel Version 2005 Build 12827.20470 and higher. To install the fixed build from Outlook select File, Office Account, Update Options, Update Now.
That isn’t the only novel Windows bug fix this month.
The Microsoft Store month-end stinger
On June 30, Microsoft posted details about two vulnerabilities known as CVE-2020-1425 and CVE-2020-1457. Both are Remote Code Execution security holes (translation: very bad), but they haven’t been exploited yet (translation: they aren’t zero-days).
Trend Micro’s Zero Day Initiative has just published details –sorely lacking in the Microsoft descriptions – for both CVE-2020-1425 and CVE-2020-1457:
“The specific flaw exists within the parsing of HEIC files. The issue results from the lack of proper validation of user-supplied data, which can result in a read past the end of an allocated data structure. An attacker can leverage this in conjunction with other vulnerabilities to execute code in the context of the current process.”
HEIC is a video compression routine developed by the MPEG group, initially made popular in iOS and macOS.
Here’s what’s crazy about the fix. Microsoft is distributing it through the Microsoft Store – not through Windows Update, not through the Microsoft Update Catalog.

HEIC updates.
Any machines that block access to the Store, for whatever reason, aren’t going to get the fix. Paul Rathbone, posting on the patchmanagement.org mailing list, offers a number of germane observations:
“Microsoft Windows Codecs Library” – is that a component that is built into Windows10/2019 or something that would have been installed as part of an app from the Microsoft Store in the first place? I’m guessing it’s built into Windows as Server Core is impacted too (why would Server Core need Codecs ????? I thought that was a reduced non-GUI version to lessen the surface area that could be attacked and so reduce patching requirements!)
“If I manage patching behind a WSUS/SCCM server and block outbound internet access from my servers, so they can’t reach the MS Store, do I need to patch those servers and if so how? Will the fixes be included in next month’s cumulative updates? Will the fixes be published in the Update Catalog?
“Is this a sign of things to come – multiple sources of patches from Microsoft which all have to be managed – how can I tell that a machine is patched up to date without vuln scanning everything every month? Am I expected to allow servers access to the MS Store? If access to the MS Store has been blocked by Group Policy how do I patch? Do I need to patch?
“Even if my machine can reach the store and has updated itself, how can I check / monitor that across all my clients/servers? I can’t find any details of files affected, version numbers etc.”
So in June, we had:
- A traditionally botched patch with a manual-download-only Out of Band fix;
- A botched Windows patch that knocked out Outlook Click-to-Run, fixed by a fix for Outlook;
- And a couple of patches distributed via the Windows Store.
It’s all a bid for patching diversity, right?
Still no fix for the temporary profile bug
I’ve been kvetching about this bug since February. Microsoft still hasn’t confirmed the issue or given any hints as to its source or fix. As I said in April:
“In some set of circumstances, as yet undiagnosed, the Win10 Cumulative Update installer hits a ‘race condition’ on reboot, with the user coming back up in a temporary profile. That sounds like a lot of buzz words, and it is, but the net result is that the user runs the update, reboots, and returns to a clean desktop, without their desktop customizations, while files in their customary folders (such as Documents) have disappeared.
“It’s disconcerting, even if you’re savvy enough to realize you’ve been pushed into a temporary profile. The desktop customizations are still there, as are the files, but they behave as if they belong to a different user.”
I still see complaints about the temporary profile bug constantly, in every recent version of Windows, including Windows 10 version 2004.
Win10 version 2004
Microsoft’s having lots of fun with the Win10 version 2004 rollout, which is still in its infancy. From a data-eating bug in a specific oddball type of Storage Spaces to a just-unveiled axing of the advanced deferral settings, to a laundry list of bugs and gotchas (e.g., repeated erroneous security warnings as documented by Mayank Parmar at Windows Latest), Win10 version 2004 clearly isn’t ready for all but the most masochistic Windows testers.
It’s getting better. Earlier this week, Microsoft finally removed blocks that prevented Surface devices from receiving the Win10 version 2004 upgrade. Imagine. Microsoft now says that its latest version of Windows is finally able to run on its latest hardware.
LSASS and the rest
Microsoft has acknowledged a bug in the May (and June) Win10 cumulative updates:
“The Local Security Authority Subsystem Service file (lsass.exe) might fail on some devices with the error message, “A critical system process, C:WINDOWSsystem32lsass.exe, failed with status code c0000008. The machine must now be restarted.” We are working on a resolution and estimate a solution will be available in July.”
There are other various and sundry bugs. And, yes, your Windows 7 machine will get a pushed copy of the new Chrome-based Edge browser, whether you’ve paid for updates or not.
@PKCano has an update to the AKB2000016 Guide for Windows Update Settings for Windows 10 that covers the latest info about Windows Update advanced settings.
Patch Lady Susan Bradley has posted two new satisfaction surveys, one for Consumer patching and one for Business patching. Feel free to participate in either or both, depending on your predilections and station in life.
See any other problems? Hit us on AskWoody.com.

May 2020
With most of the fanatical Windows fan base now circling the trough on the just-released upgrade to Windows 10 version 2004, it’s time for those of us who rely on stable PCs to consider installing the May patches.
While the general outlook now is good, we’ve been through some rough patches – which you may, or may not, have noticed.
Unannounced Intel microcode patch triggers reboots
On May 20, Microsoft released another of its ongoing series of “Intel microcode updates,” all named KB 4497165. Ostensibly intended to fix the Meltdown/Spectre security holes, many of them have a history of problems and hassles not commensurate with the amount of protection they provide (unless you’re running a bank transaction system or decrypting top secret emails).
This incarnation has proven relatively benign. The main problems:
- Microsoft pushed it out the Automatic Update chute (and thus triggered a reboot) without warning anybody.
- The Knowledge Base article still doesn’t describe this particular version.
- Many machines that shouldn’t receive the patch – including AMD-based machines, which clearly don’t need an Intel patch – got it.
If you leave your machine set to install Automatic Updates, you get what you paid for. And then some.
The 5 scary new zero-days
Given the sensationalistic turn Windows patching has taken, I’m surprised we haven’t seen a rash of headlines, “Run for the hills! FIVE new Windows zero-days published!” But that’s what happened late last week. Trend Micro’s Zero Defense Initiative, ZDI, published descriptions of five new Windows zero-days. Four of them are the dread Privilege Escalation Vulnerabilities. Microsoft didn’t patch them quickly enough, so ZDI acted according to its conventions – waited four months to give Microsoft time to fix the hole – and then published “a limited advisory.”
Truly tempest in teapot territory. The holes aren’t particularly gaping. In fact, they’re just barely interesting.
The zero-day that wasn’t announced
Windows observers – especially security folks without much Windows experience – are prone to jump on the “OMG! There’s a zero-day you have to patch RIGHT NOW!” bandwagon. In fact, when Microsoft releases a fix for a zero-day security hole (identified with “Exploited = Yes” in the associated CVE article), it’s exceedingly rare for a new, widespread related security breach to appear in short order. Sometimes Microsoft identifies security holes as zero-days, then without any fanfare goes back a couple of days later and changes the “Exploited” setting to “No.”
I’ve searched high and low for “Exploited” zero-days that rapidly turned into working, widespread malware. The worst case I found was the Sasser worm, which was patched, then exploited, two weeks later.
That was 16 years ago.
This month saw the situation in reverse: Microsoft released a patch for the CVE-2020-1048 Windows Print Spooler elevation of privilege bug. It was (and still is) marked “Publicly disclosed: No” and “Exploited: No.” Immediately after the patch came out on Patch Tuesday, two security researchers published a lengthy paper on the security hole, complete with working exploit code.
Rob VandenBrink, writing on the SANS Internet Storm Center, says:
“This vulnerability was actually disclosed to Microsoft by the research community, so the code to exploit it absolutely does exist and was disclosed, and a full write-up was posted as soon as the patch came out.”
For a while I was concerned that a fully-formed exploit was imminent. Silly me. I still haven’t seen any widely available threat – although the folks at 0patch have released a fix for this “PrintDemon” security hole in Windows 7.
Temporary user profile bugs continue
We’ve had problems with this for months – and Microsoft still hasn’t confirmed the issue, or given any hints as to its source or fix. As I said last month:
“In some set of circumstances, as yet undiagnosed, the Win10 Cumulative Update installer hits a ‘race condition’ on reboot, with the user coming back up in a temporary profile. That sounds like a lot of buzz words, and it is, but the net result is that the user runs the update, reboots, and returns to a clean desktop, without their desktop customizations, while files in their customary folders (such as Documents) have disappeared.
“It’s disconcerting, even if you’re savvy enough to realize you’ve been pushed into a temporary profile. The desktop customizations are still there, as are the files, but they behave as if they belong to a different user.”
Yep, Microsoft knows all about it. Nope, they haven’t officially acknowledged – much less fixed – the problem.
Ongoing audio problems
In addition to all of the usual problems we’ve seen – Mayank Parmar has a well-researched list of failed installations, performance problems, blue screens and black screens on Windows Latest and Lawrence Abrams has a second, detailed take at BleepingComputer – I’m seeing many reports of messed up audio that may be related to the latest updates. Or maybe not.
AskWoody poster @LoneWolf found a solution for some of the bugs:
“This issue occurs with people who have Realtek audio; which of course, means 3/4 of those with on-mainboard audio out there. It’s likely that you had a driver update from Microsoft, and there’s an issue there. Symptoms:
- Your Device Manager once showed “Realtek High Definition Audio;” now it shows “Realtek(R) Audio” instead.
- You also see in Device Manager a new Audio Device entitled “Nahimic mirroring device” or similar
Realtek’s latest driver includes these Nahimic software drivers for some future 3D audio enhancement (likely done in software and provided by this third-party vendor). What didn’t happen with the driver update is that the Nahimic control panel wasn’t installed. This is a UWP application you can get from the Microsoft Store; search for “nahimic” and you’ll get this app that’s a blue square with a squiggly white N.
In my case, installing this app and rebooting the system resolved the issue. Also note that Realtek has gone to a UWP application as well; if you don’t have this, you may need to install theirs from the Microsoft store as well.
Sadly, Realtek’s own latest driver download from their website seems to have the same problem, which explains why my installing it didn’t fix the issue either. I think it’s the exact same package Microsoft bundled in their driver updates.”
(Also note @EP’s comments on the various boards, chips and errors.) No way the Nahimic app will solve all the audio problems out there, but for many it’s a godsend.
HP’s KMODE_EXCEPTION_NOT_HANDLED Blue Screen
Early this month, HP computer owners started encountering Blue Screens that say KMODE_EXCEPTION_NOT_HANDLED. Ends up that the BSoDs were triggered by a conflict between the support software for HP’s OMEN series of computers, and one of the recent Windows Defender updates.
HP released an update last week called “HP Software Component 4.1.4.3079” that seems to solve the problem. The patch came out through Windows Update, even though it’s listed as a driver update. (Thx, @FAKramer.)
Thumbs down for Fast Startup
Earlier this week, Microsoft revealed that, “Windows updates might not be installed on your system after you shut down your computer. This behavior occurs when the Fast Startup feature is enabled. This behavior doesn’t occur when you restart your computer.”
The culprit, Fast Startup, intercepts your request to shut down your computer and fudges things a bit by creating a backup copy of certain system files, which are used to start the next time. As Microsoft says, “When you shut down your computer, your computer actually enters a hibernation state instead of a full shutdown.” So if your updates require a full shutdown, you may not get them because your shutdown isn’t a shutdown.
Try explaining that to a Chromebook user.
Nope, it hasn’t been fixed. Microsoft says it’ll get around to solving the problem “in a future Windows version.”
Office 365 Click-to-Run bug got fixed
Yet another bug in Office 365 Click-to-Run sent some folks running for pitchforks. Per an anonymous poster on AskWoody:
“Outlook would open in tiny window slightly larger than close icon and then crash. Usual fix was deleting Outlook profile and recreating. This particular machine / user I had done that twice and the fix no longer worked. I initiated an online repair via Add Remove programs and clicking Modify in Office. The repair failed during the reinstall phase. This left the machine with no Office install. I went to Office.com and attempted new install from C2R download. It got stuck on initial download screen once launching. I rebooted and tried multiple times.
“I tried office cleanup tool but all it did was say Office wasn’t installed. I got fed up and starting ripping things out myself. Deleted Office reg keys from HKCU and HKLM. Then deleted Office dir from Program Files. After all of that it seemed to install properly.”
Microsoft fixed the bug the next day. No telling how many admin-hours were wasted.
Next up: Windows 10 version 2004
As expected, Microsoft released the latest Windows 10 update. As expected, it’s full of problems.
For starters: If you own one of Microsoft’s latest PCs – the Surface Pro 7, Surface Laptop 3, or Surface Pro X – you won’t even see the upgrade offered. Microsoft has upgrade blocks in place for all three.
Keep in mind that Microsoft has had five months to beta test this latest, greatest version of Win10 – and that the customer-facing part of Windows and the entire Surface effort report to the same guy. That has to give you pause.
We’re following the latest version 2004 foibles intently
See any other problems? Hit us on AskWoody.com.
April 2020
The patching pace this month returned to normal: We had the Patch Tuesday patches on April 14, followed by the “optional, non-security, C/D Week” patches one week later (Monthly Rollup Preview for you Win8.1 afficionados). With a bit of luck, that’s the last round of confusing “optional” Win10 patches: Microsoft promises we won’t see any more of them.
We also had an out-of-band patch for Office 2016 Click-to-Run, Office 2019 (which is only available as Click-to-Run) and Microsoft 365 Apps for Enterprise (previously known as Office 365 ProPlus). The big concern with those patches falls into the “it’s not a bug, it’s a feature” column.
More big, scary zero-day vulnerabilities
For the Chicken Little crowd, we had three zero-day patches – ones identified by Microsoft as being “Exploited” when issued – and, as best I can tell, none of those have found their way into mainstream attacks. Same old story.
As a perplexing sidenote, many reports included a fourth zero-day patch, CVE-2020-0968, which was issued with an indication of “Exploited: Yes” but is now listed as “Exploited: No.” Long story, but the divergent reports on the web have largely been updated. (Thx, @campuscodi, @dangoodin001)
I’m not aware of any widespread attacks based on any of the three (or four) “Exploited” patches. As usual, the exploits at this point are limited to extremely targeted attacks.
VBA libraries get blocked with the Office Click-to-Run patches
If you use one of the recent Click-to-Run versions of Office and you start getting “Compile error: / Can’t find project or library” error messages (see screenshot), there’s a reason why. You’re running a VBA command – whether you realize it or not – that’s trying to open something out on the wild, wild web.

Patch Lady Susan Bradley explains in her Patch Watch column (paywall, donation required):
“Microsoft is doing you a favor; it’s pointing out that an application you’re using is breaking security by pulling links or references directly from the Web rather than from your computer…. Microsoft recommends that you move your VBA object libraries to an intranet (i.e., local network) location. You can then use a Group Policy object setting to remove the blocking.”
The old ‘missing’ data new profile bug is still there
I’ve been talking about this bug for months, and it doesn’t seem to be getting any better.
It’s not clear to me why or how, but in some cases, the Win10 Cumulative Update installer hits a “race condition” on reboot, with the user coming back up to a temporary profile. In plain English, the user runs the update, reboots, and returns to a clean desktop, without their desktop customizations, while files in their customary folders (such as Documents) have disappeared.
I don’t know what causes the race conditions, but I do know lots of people have complained about deleted data files when, in all likelihood, they’re sitting at the bottom of an obscure backup profile. I’ve even heard from someone who upgraded from Win10 1903 to version 1909 and hit the same problem.
The right people at Microsoft know all about the problem, but nobody has acknowledged it or confirmed it. The best solution is to re-boot all the way through log in four or five times and, if that doesn’t work, try to retrieve your wayward profile using an enormously complex series of steps outlined by Shawn Brink on Tenforums.
Installation problems and blue screens
Every month we see Win10 cumulative update installation problems – the installer runs for a while, hiccups, then rolls back the cumulative update. This month there have been more than the usual number of reports, at least in my experience.
We also frequently see one-off bluescreens after installing the latest cumulative update. It’s hard to tell whether the bluescreen is actually caused by the patch, or if it’s just serendipity in reverse.
Usually, sooner or later, a pattern emerges – a specific hardware combination, or driver, or other software conflict – and it becomes clear who should avoid trying to install the cumulative update. This month, though, I’ll be hanged if I can see a pattern.
Microsoft really wants to know about the bugs you hit
Surprisingly, uniquely, and much to its credit, Microsoft issued a call for help with the latest outstanding bugs:
“We have seen social media reports related to KB4549951 [the April Win10 version 1903 and 1909 cumulative update] that mention Bluetooth, stop error with blue screen and other related issues… To date, we have not seen these issues reflected in telemetry, support data or customer feedback channels. We continuously investigate all customer feedback and are closely monitoring this situation. Note If you experience any issues we’d like to know. Please provide feedback using the keyboard shortcut Windows + F or go to the Start menu and select Feedback Hub so that we can investigate.”
Of course, reports of the problems have peppered the Microsoft Answers Forum, the Windows Feedback Hub, the official Windows 10 cumulative update thread on Reddit, and in dozens (or more) online articles and blogs.
Still, it’s nice of them to ask.
I was recently informed that, if you want to report a cumulative update bug in the Feedback Hub, you should NOT necessarily put it in the Install and Update category (screenshot).
The Install and Update category is reserved for problems with the update installer itself. For example, install failures would go in the Install and Update category – but “missing” data and bogus temporary profiles would, presumably, go under Desktop Environment, even if the problem’s clearly linked to a specific update. Likewise, presumably, cumulative update-induced reboot bluescreens would go in… some other category. You get to choose which one.
Sporadic problems connecting to v4 printers
Susan Bradley is following a handful of complaints about the latest Win10 version 1903 and 1909 cumulative update breaking access to shared printers. It appears that the cumulative update knocks out some shared printers using the v4 Printer Driver.
We still don’t know whether the problem lies with the cumulative update, the driver, Group Policy settings, or the phase of the moon. Two official Microsoft support cases have yielded zero useful results.
Not looking forward to May
I’m dreading May. Microsoft seems hell-bent on releasing Win10 version 2004 in May. Computerworld’s Gregg Keizer and I have both strongly recommended that it hold off until we aren’t in the middle of coping with a massive shift to Work-from-Home.
I’m seeing more and more reports of problems with the version of Win10 2004 that’s currently available to Windows Insiders. Gene Morgan, for example, wrote to tell me:
“I’m an Insider and installed the Pre-Release offering which is usually equal to what will soon be unleashed into the wild and previous such updates worked with no issues. After the installation and the numerous reboots involved, the desktop appeared and all seemed well until I went to open Outlook 365. Click on It and nothing happens. Try to open Word 365, frame comes up but nothing you can work with. Try to open Adobe Acrobat DC, won’t open. Try to open the new Edge Browser, ditto. Open Google Chrome, the frame and tabs come up but after 45 minutes, there was nothing in any of the tabs. Hard Drive light is on continuously – not even flashing, solid on.
I rebooted, thinking something may not have loaded properly. Nothing resolved. Hard Drive light on continuously as before. Thinking “well maybe there’s just a lot of cleanup that needs to be done after the install” I left the machine to its own devices overnight. Next morning, no programs will open as before. Annoyed, restored my PC to v. 1903 and everything works like lightning.”
For every botched upgrade I’m sure there will be dozens of clean ones. But why kick the dog? The list of new features in Win10 version 2004 seems even less compelling than any Windows version upgrade, ever. That’s quite an accomplishment. Microsoft should re-examine its motives, in light of the current state of computing.
Keep us stable, folks.
We’ll keep pushing on AskWoody.com.
March 2020
It’s been another strange patching month. The usual Patch Tuesday crop appeared. Two days later, we got a second cumulative update for Win10 1903 and 1909, KB 4551762, that’s had all sorts of documented problems. Two weeks later, on Monday, Microsoft posted a warning about (another) security hole related to jimmied Adobe fonts.
Predictably, much of the security press has gone P.T. Barnum.
The big, nasty, scary SMBv3 vulnerability
Patch Tuesday rolled out with a jump-the-gun-early warning from various antivirus manufacturers about a mysterious and initially undocumented security hole in the networking protocol SMBv3.
Later that day, Microsoft released a broad description of the SMBv3 security hole in Security Advisory ADV200005 – apparently trying to close the door after the cow escaped. And the crowd went wild. How could Microsoft tell these antivirus vendors about a forthcoming fix, then fail to deliver the fix – and not warn the AV folks in time to pull their press releases? Tales of impending doom ran rampant.
Then, on Thursday, we saw another cumulative update for Win10 versions 1903 and 1909. KB 4551762 patches the SMBv3 security hole and, being a cumulative update, includes all earlier patches. The rush was on to install the patch-of-a-patch, but we started seeing all sorts of problems: errors on installation; random reboots; performance hits; and the return of our old profile-zapping bug, which leaves folks with empty desktops and hidden files.
Here’s the punch line. (Tell me if you’ve heard this one before.) After all the sturm un drang, researchers (notably including Kevin Beaumont) discovered that they couldn’t effectively use the security hole to take over a system:
“Windows Defender, which is enabled by default, detects exploitation even if unpatched.”
As of this writing, I don’t know of any real-world attacks using the SMBv3 vulnerability. Certainly, one will appear sooner or later, but it isn’t a big deal right now.
The big, nasty, scary Adobe Type Manager font bugs
Yesterday, Microsoft released another Security Advisory. ADV200006 — Type 1 Font Parsing Remote Code Execution Vulnerability describes a security hole in the way Windows handles fonts. We’ve seen a lot of those in Windows over the years. This one came with the usual zero-day language, advising that Microsoft has seen “limited targeted attacks that could leverage un-patched vulnerabilities.” The advisory shows that every version of Windows – going back to Win7 – is vulnerable.
Once again, the blogosphere went nuts. Microsoft’s warning meeeeeeelions of Windows users that their systems are under attack!
Yeah. Sure.
When Microsoft says it’s seen “limited targeted attacks,” that means some well-heeled hacking group is using the security hole against a very specific target – usually a government agency or a high-stakes corporate group. For normal people, in normal situations, it’s not a big deal.
We’ve seen these “sky-is-falling” scenarios play out over and over again in the past year or so. Some security holes (e.g., for EternalBlue/WannaCry and BlueKeep) need to be plugged shortly after the patches are released. But in the vast majority of cases, waiting a week or two or three to install the latest crop of Windows and Office patches just makes sense.
Windows Defender ‘Items skipped during scan’
Many – but not all – Windows 10 users report that a manual scan by Windows Defender triggers this “Items skipped during scan” notification (screenshot).

It appears to be a bug. According to Lawrence Abrams at BleepingComputer:
“It seems that in the older Windows Defender engines network scanning was enabled by default… [in newer versions of the engine] you can see that the Windows Defender preferences show that network scanning has now been disabled by a newer engine. It is not known why Microsoft decided to make this change, but the alerts appear to just indicate that network scanning was skipped.”
Günter Born originally reported on the bug. He has come up with a manual workaround to enable network scanning.
Other developments
More on the patching front:
- Microsoft has announced that it’s extending end-of-life for Win10 version 1709 Enterprise (and Education) to Oct. 13, 2020.
- Abbodi86 has discovered a way to install the latest Windows 7 security patches, even if you haven’t yet set up Extended Security Updates. Many people, including Patch Lady Susan Bradley, are asking Satya Nadella to offer Win7 Extended Security Updates to all “genuine” Win7 customers, particularly because of the increase in work-from-home.
- In the same vein, there’s a lot of discussion about throttling back on Windows auto updates, specifically to help keep work-from-home systems stable. Many advocate holding off on the inevitable Win10 version 2004 update. No indication that Microsoft has heard the pleas.
If there ever were a time for Windows patching stability, this is it.
We’ll keep pushing on AskWoody.com.

February 2020
The real stinker this month, KB 4524244, rolled out the automatic update chute for four full days until Microsoft yanked it – leaving a trail of wounded PCs, primarily HP machines, in its wake. The other big-time bug in this month’s patches, a race condition in the KB 4532693 Win10 version 1903 and 1909 cumulative update installer, hasn’t been officially acknowledged by Microsoft outside of a blog post. But at least it’s well known and understood.
Folks running SQL Server and Exchange Server networks need to get patched right away.
Win10 UEFI update KB 4524244 blockages
Patch Tuesday brought KB 4524244 for Windows 10 owners, a bizarre single-purpose patch apparently directed at one specific UEFI bootloader. I talked about it last week.
The patch was pulled on Friday, but in the interim lots of people reported problems. Most notably, many folks running HP machines with Ryzen processors saw their machines hang, followed by an HP Sure Start Recovery message saying Sure Start had “detected an unauthorized change to the Secure Boot Keys.” HP has posted a list of affected machines:
HP EliteBook 735 G5 Notebook PC, 735 G6, 745 G5, 745 G6, 755 G5, and HP ProBook 645 G4 Notebook PCs. HP EliteDesk 705 35W G4 Desktop Mini PC, 705 65W G4 Mini PC, 705 G4 Microtower PC, 705 G4 Small Form Factor PC, 705 G4 Workstation Edition, 705 G5 Desktop Mini PC, 705 G5 Small Form Factor PC, HP mt44 Mobile Thin Client, mt45 Mobile Thin Client, and HP ProDesk 405 G4 Small Form Factor PC.
If you have any of those machines and left your PC open to Microsoft’s updates during Patch Week, you got clobbered. In addition, Microsoft documents a bug in the “Reset this PC” function but doesn’t give any details.
There’s nothing you can do about it now. If KB 4524244 installed successfully, everything’s OK. If it didn’t, you need to follow HP’s removal instructions or Microsoft’s removal instructions to get things working again.
Win10 Cumulative Update KB 4532693 clears desktops, moves files
Shortly after the Patch Tuesday patches arrived, we started seeing reports from folks who installed the Win10 1903 and 1909 cumulative update, KB 4532693, saying that their desktops got wiped out. A little poking revealed that all of their customizations had been tossed – icons, wallpaper – and many of their files weren’t where they left them.
Long story short, it looks like the patch gets ensnared in a race condition bug, which I wrote about last week. We’ve never been able to pin down which other programs trigger the race condition, but at least in some cases certain antivirus and “secure banking software” programs will leave your PC with a dangling temporary profile.
Microsoft hasn’t identified the offending software. Nor has it even acknowledged the problem either on the Knowledge Base article page or the Windows Release Information status page, two places that bugs like this are traditionally documented. (Perhaps Microsoft figures it’s the other software’s problem, so it has no need to report it?)
Fortunately, there’s a Microsoft Answers forum post that addresses the problem:
Microsoft is aware of some customers logging into temporary profile after installing KB4532693, on both versions 1903 and 1909.
Rebooting into Safe Mode* and then starting back in normal Mode should resolve this issue for most customers.
You may uninstall any secure banking software or anti-virus in the temporary profile which may resolve this if the above steps do not help.
If you didn’t accidentally find that explanation, or don’t know what a temporary profile is, or how it could get secure banking software, heaven help ya. But at least Microsoft “is aware” of the problem.
What’s the big deal?
How many people were affected by those high-profile bugs? I don’t know. Judging by the number of complaints online – hardly a reliable metric – both of the problems were widespread and became apparent shortly after release.
HP could probably come up with a tally of the number of afflicted machines and whether or not those machines installed the buggy UEFI patch. But the only organization that has comprehensive numbers about these bugs is Microsoft, and it’s not talking.
Think of all of that lovely telemetry we’re providing to Microsoft.
Odds ‘n Ends
That “exploited” Internet Explorer JScript hole, CVE-2020-0674 – the one that prompted computer security “experts” to tell you that you had to get patched RIGHT NOW? It hasn’t gone anywhere. This is the second month in a row that we’ve been inundated by Chicken Little warnings about the need to get patched immediately. Look where knee-jerk installation of new patches has left folks running HP Ryzen computers, or the unidentified “secure banking software,” this month.
Those of you running Windows 7, who haven’t paid for Extended Security Updates, should know that 0patch has released a micro patch for that particular security hole. It also has an online test you can use to confirm that your Win7/IE 11 system has properly swallowed the micro fix.
To be sure, there are major security holes that need your attention, but only if you’re in charge of a network running SQL Server or Exchange Server. That latter vulnerability is particularly vexing because anyone who can get access to any Exchange account on your server can take over Exchange. Seems that somebody forgot to delete hard-coded keys.
We’re looking into a report that Win10 version 1903 running Hyper-V is throwing “Synthetic_Watchdog_Timeout” errors. There are unconfirmed reports that there will be a fix in late March.
There seems to be a way to cheat the 35-day “Pause updates” limitation imposed in Win10 version 1903 and 1909. In a nutshell, if you tell Windows to Resume Updates, then unplug the computer from the internet, you may be able to reboot and get 35 more days paused, without installing the outstanding updates. In addition, @abbodi86 has a more complex but apparently foolproof way to wipe out the 35 day limitation.
Join the patch watch on AskWoody.com.

January 2020
The big patching problems this month fell at the feet of admins who had to deal with an unholy mess of pressing exposures: Fixing the holes in Microsoft’s RD Gateway (CVE-2020-0610; see Susan Bradley’s Patch Watch, paywalled); dealing with Server 2008 R2 systems that booted to Recovery mode after installing the January patches; scrambling to pick up after breaches in Citrix networking products; or the 334 Oracle security patches. They all took a toll.
Those of us not in charge of multinational networks could breathe a little easier. In spite of a stellar advertising campaign from the National Security Agency (NSA), the Chain of Fools/CurveBall CVE-2020-0601 hole hasn’t turned into an active attack. As I said at the time, it’s a long way from a third-degree polynomial to working ransomware.
Yes, you need to patch sooner or later. But, no, the sky isn’t falling. Those reports of the internet’s impending CurveBall doom were just a little bit overblown.
As usual.
Still no ‘optional, non-security’ patches
I would conjecture that the January Patch Tuesday crop is relatively well-behaved because, at least apparently, they only contain security patches. Normally, Microsoft releases dozens of “optional, non-security” patches every month – bug fixes – but those annoying little gnats haven’t made an appearance since October.
I expect that will change shortly. We’ll no doubt see dozens – if not hundreds – of smaller patches out in the usual “C Week/D Week” cadence soon. Since we’ve seen no such infestation in three months, you’d be smart to avoid the “optional” patches, once they arrive, until they’ve been well vetted.
Common patching problems persist
Günter Born has put together a comprehensive list of printing problems associated with recent patches. They seem to come and go – many different printers, many different symptoms.
There are also many reports of January cumulative updates failing to install, with various error message.
None of the problems seem particularly remarkable – or even replicable – to me, but if you get stuck trying to install one of the January patches, your opinion may vary.
Upgrades to 1909 press forward, Microsoft continues to honor 1803 deferrals
If you “seek” by clicking on the “Check for updates” button in Win10 1809 or 1903, Microsoft warns that it may upgrade you to Win10 version 1909:
Current status as of Jan. 21:
Windows 10, version 1909 is available for any user on a recent version of Windows 10 who manually selects “Check for updates” via Windows Update. The recommended servicing status is Semi-Annual Channel.
Of course, Microsoft disavowed any use of the bafflegab phrase “Semi-Annual Channel” a year ago. Consistency. Hobgoblins. Little minds. Microsoft may feel that 1909 is ready for widespread deployment, but I’m still seeing many reports of problems with Win10 version 1909 – the well-documented Search in File Explorer bugs, power problems, video problems, Your Phone oddities.
In addition, Microsoft has warned that it’s starting to force Win10 version 1809 customers onto 1909:
“We are starting the next phase in our controlled approach to automatically initiate a feature update for an increased number of devices running the October 2018 Update (Windows 10, version 1809) Home and Pro editions, keeping those devices supported and receiving the monthly updates that are critical to device security and ecosystem health. Our rollout process starts several months in advance of the end of service date to provide adequate time for a smooth update process.”
For reference, Win10 version 1809 is supposed to hit end of service on May 12. You 1809 users are getting four months shaved off of your promised end of life. As a Service.
Remarkably, tests by @PKCano show that Microsoft is still honoring the “Defer feature updates” setting in Win10 version 1803 Pro. It looks like the methods for staying on 1803, 1809, and 1903 as documented in How to block the Windows 10 November 2019 Update, version 1909, from installing still work. And if you want to upgrade to 1903, avoiding 1909 for the time being, the method described here also works.
Windows 7 gets its butt slapped on the way out
Everybody’s favorite whipping boy, Windows 7, got slapped with two bugs in the final round of free patches.
Anybody using Win7 who installs the January patches will find that their “stretched” desktop wallpaper comes out black, which can look disconcertingly like a Black Screen of Death. Lawrence Abrams has a full description, and a clever workaround, at BleepingComputer.
More alarmingly, Microsoft posted Security Advisory ADV200001 on Jan. 17. The Advisory details yet another security hole in Internet Explorer’s JScript engine, CVE-2020-0674. There’s a manual workaround with numerous side-effects, at least some of which have been overcome by a 0patch micropatch that you can install if you feel threatened.
Here’s the big open question: Will Microsoft fix Windows 7 later this month, in spite of the Jan. 14 end of service deadline? Or will Win7 drift into the sunset with a Black Screen bug and a known IE hole?
Seven semper fi.
Microsoft’s tone-deaf threat to hijack Google Chrome’s search engine
This isn’t a widespread problem. It only applies to those who are running Office 365 ProPlus, which is directed at (but not limited to) Enterprises with savvy admins. But it’s an astounding push nonetheless.
In an official post from ‘Softie Daniel Brown entitled, Microsoft Search in Bing and Office 365 ProPlus, Microsoft seems to be saying that everyone who installs the latest patch for Office 365 ProPlus will have their default search engine in Google Chrome changed to Bing.
I fully expect someone with some sense at Microsoft will swoop down in the next week or two and rescind the decision. But until that happens, this stands as a browser hijacking threat of unprecedented proportions.
Join us for the latest on AskWoody.com.

December 2019
It was the kind of month admins dread: Mysterious problems on hundreds of machines, with no apparent cause or cure. Toss in the holidays, and we had a whole lot of Mr. and Ms. Grinches in the industry.
Fortunately, it looks like the problems have been sorted out at this point. Individual users had many fewer problems. Microsoft’s left and right hands still aren’t talking on the 1909 team, but what else is new…
Win7 hang on ‘Preparing to configure Windows’
Microsoft dropped a new Servicing Stack Update for Windows 7 on Dec. 10, and it gummed up the works for many. Here’s a good summary on Reddit from poster Djaesthetic:
“We had over 100 Windows 7 Professional endpoints all stuck on “Preparing to configure windows” screen. We couldn’t get beyond that error in any simplistic manner. We eventually got a remediation to get beyond that error (involving booting each one from an ISO and making several registry hive edits to TrustedInstaller). Unfortunately, even after we were able to log in, the entire OS is functionally broken….
“…We are having this same issue on 111 different Windows 7 machines, each one consistently having the same environment problems. We are unable to roll back the KB4530734 Windows Update, likely because the Windows Module Installer (TrustedInstaller.exe) service itself is broken… I’ve been working non-stop all weekend. Currently waiting for (yet another) callback from Microsoft….
As Djaesthetic later posts, the problem is triggered by the Dec. 10 Servicing Stack Update, KB 4531786:
“In our investigation we confirmed the problem having to do with KB4530734 (December Monthly Rollup for Windows 7 Service Pack 1). More specifically, we believe it had something to do with KB4531786 (Servicing stack update for Windows 7 SP1 and Server 2008 R2 SP1: December 10, 2019) applying out of order. Interestingly, if you look at the notes for the December rollup it specifies a recommendation to install the SSU afterward (not a requirement). Lastly, we found some (not all) machines in various states of “Uninstall_Pending” regarding the November Monthly Rollup….”
Those of you using plain old single-system Monthly Rollups won’t encounter the problem. But if you or your system’s admin is manually installing patches, getting them in the wrong order can cause all sorts of problems. Manually installing the Servicing Stack Update can be particularly vexing because SSUs won’t show up until you’ve installed (or hidden) all outstanding patches.
Server 2012 (not R2) reboots
There were lots of reports of Server 2012 (not R2) servers going into reboot loops after last month’s updates. I originally reported on AskWoody that the problem appeared to be with KB 4533096, the “Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows Server 2012.” But I now think that a bad Malicious Software Removal Tool (MSRT) version may have been at fault.
Manually rebooting cleared up the issue. And the mid-December version of MSRT is long gone. There’s no official confirmation or explanation that I can find.
Win10 version 1909 bugs continue
The December patch didn’t fix the long-decried File Explorer Search bug in Win10 version 1909. You may recall that Microsoft’s known about the bug – which makes Search in File Explorer unusable – since 1909 shipped. They fixed the bug in a Win10 version 2004 beta test version
Microsoft still hasn’t confirmed the bug in the official Release Information Status page. I’ve seen Twitter threads where Microsoft employees claim no knowledge of the problem – in spite of the fact that the bug’s been reported over and over again in many different places (including the Feedback Hub) for months. @navh2009 nails it:
“If they are going to keep half baking these new changes, then they should stop making changes to things [that] were never broken. File Explorer search didn’t need windows search. Delete key still doesn’t work. How does basic functionality like this get forgotten every time?”
@railmeat goes on to say:
“These kinds of problems reoccur [due] to inadequate testing. These should be found in regression and functionality testing. Microsoft has the resources to do that testing, but apparently chooses not to.”
@abbodi86 has an explanation:
“In 1909, the upper bar of File Explorer (address + search box) no longer belongs to the Win32 platform. It’s a hybrid WinRT (UWP) feature. It’s half-baked, ugly, slow, and requires some prerequisite tasks to even semi-function (clipboard and other services including the MsCtfMonitor task schedule).”
I still recommend that folks avoid 1909 for precisely this reason.
Join us for the latest on AskWoody.com.
November 2019
What a relief. The only major patching problem for November came from Office, not Windows. We had a handful of completely inscrutable patches – including two .NET non-security previews that apparently did nothing – but that’s the worst of it.
November saw the last security patch for Win10 version 1803. Win10 version 1909 got released, gently. We also had a much-hyped “exploited” zero-day security hole in Internet Explorer (again) that didn’t amount to a hill of beans (again).
As promised, we received no “optional, non-security” Windows 10 patches in November – and Microsoft promises there won’t be any this month, either. I think that’s great. If Microsoft wants to roll out beta test versions of Windows, it should have testers sign up for an Insider ring.
About those buggy Office patches
All of the Office patches in November throw a “Query is corrupt” error message in Access under certain circumstances. Access says “Query xxxx is corrupt,” when in fact the query in question is just fine.
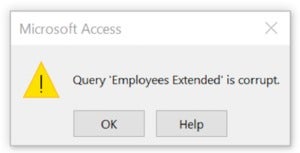
I talked about the bug on Nov. 13. Microsoft finally acknowledged it almost a week later.
Microsoft rolled out a patch for Access 2016 on Nov. 18, but didn’t get the other installed (“MSI”) versions patched until Nov. 27. We’re still waiting for patches to the Click-to-Run versions of Office, which are currently scheduled for Dec. 10 – the next Patch Tuesday.
Inscrutable .NET previews
Along with Win7 and 8.1 Monthly Rollup previews, we were also graced with four optional preview .NET patches – two of which don’t appear to do anything – and a group of one-off patches (not cumulative updates), available by manual download only, to fix a weird bug in ClickOnce.
In short, there weren’t any .NET patches in November worth the distraction.
Another ‘exploit’ fizzle
Speaking of distractions…, November saw a fix for an “exploited” security hole, CVE-2019-1429. The parallels to September’s CVE-2019-1367 are hard to ignore. Like -1367, -1429 is a “Scripting Engine Memory Corruption Vulnerability” that is known (by Microsoft) to be used in some sort of attack. Like the earlier doppelganger, this new incarnation hits Internet Explorer directly, but can be leveraged by an aberrant Office document that links to IE. Both exploits seem full of sound and fury – 800 million Windows users exposed! Hurry and get patched! Click here! – but in the end, neither leaked into the wild.
There’s one big difference between the old -1367 and the new -1429: Microsoft didn’t start flailing around like a beached whale this time. If you recall, the September hole was subject to four – count ‘em, four – different out-of-band updates, poorly conceived and worse implemented. Local news broadcasts predicted the Windows sky was falling. Meh.
My advice then – and now – is to ignore the “exploited” designation, stop using Internet Explorer, set any other browser as your default, and read up on False Authority Syndrome (thanks, Rob).
Win10 version 1909, not yet ready for prime time
If you’re thinking about moving on to Win10 version 1909, make sure you weigh the benefits (are there any real benefits?) against the problems. Several bugs in Win10 1903 are running over into 1909, and 1909 has a handful of its own:
It remains to be seen whether there are any 1909-specific bugs. But it also remains to be seen whether there are any real benefits to moving to 1909.
Choose your version of Win10
Those of you running Win10 1809 Home may be distressed to discover that, unless you take significant steps to prevent it, Microsoft now upgrades your machine to version 1909, not 1903. That may be what you want – if so, I salute you! – but moving to Win10 1903 now gives you the opportunity to choose when you’ll get pushed onto 1909.
In fact, if you’re running Win10 version 1803 or 1809 (or don’t know what version you’re running!), there’s a relatively easy way to make sure you end up on the version you want. Full step-by-step instructions are here in, Running Win10 version 1803 or 1809? You have options. Here’s how to control your upgrade.
Get the latest on AskWoody.
October 2019
October started out on an extraordinarily low note. On Oct. 3, Microsoft released an “out of band” security update to protect all Windows users from an Internet Explorer scripting engine bug, CVE-2019-1367, once thought to be an imminent danger to all things (and all versions) Windows.
It was the third attempt to fix that security hole and each of the versions brought its own set of bugs.
What? You haven’t heard of any CVE-2019-1367 exploits in the wild? Me, neither. What was once the bogeyman du jour, topic of many local TV station warnings and plenty of PC-busting online screams of terror, turned into another…meh.
Since then, we’ve had the usual crop of two cumulative updates (security and “optional”) for each current version of Windows 10, as well as monthly rollups, security-only patches and monthly rollup previews for Win7 and 8.1. Pretty typical.
Here’s the rest of the story.
Lingering problems with Win10 1903 Start and Search

Günter Born opines that this bug is a retrograde mistake from an earlier buggier patch, KB 4512941, the second (“optional,” non-security) August Win10 1903 patch released on August 30. Whatever its origin – and in spite of Microsoft’s claim that it has fixed the bug – I’m seeing lots of reports that it’s still breaking systems.
Here’s what Microsoft posted on Sept. 19:
Some users report issues related to the Start menu and Windows Desktop Search
“Microsoft has received reports that a small number of users are having issues related to the Start menu and Windows Desktop Search.
“Affected platforms: Client: Windows 10, version 1903
“Resolution: At this time, Microsoft has not found a Search or Start issue significantly impacting users originating from KB4515384 [the first cumulative update for September -WL]. We will continue monitoring to ensure users have a high-quality experience when interacting with these areas.”
You don’t need to look very far to see complaints that Start in particular – and for some, Search – don’t work right after installing any of the most recent patches. On Oct. 11, MS engineer Paul Sey said on the Answers Forum, “We are aware of this issue and estimate a resolution to be released in late October.”
At this point, KB 4522355, the only Win10 1903 patch “released in late October,” still throws both Start and Search errors, as Lawrence Abrams discusses in BleepingComputer.
Continuing problems with RDP, disconnects and unresponsive VMs
Microsoft has had another lingering problem – this one with disconnected Remote Desktop connections triggering big time redline spikes – that may be solved in this month’s second (“optional” non-security) cumulative update for Win10 version 1903. That bug, and one described by Noel Carboni as triggering jitters in mice running over RDP, may be connected to a change in display driver model used in RDP.
There’s a post on the Microsoft Answers forum from Kevin Marchant that complains about the “high CPU after disconnecting” problem on Win10 1903, which is now marked “*** PROBLEM RESOLVED BY KB4522355 RELEASED OCTOBER 24TH 2019. ***”
It’s possible that the KB 4522355 cumulative update may have fixed the problem. This is one (of many!) changes listed in the KB article:
“Addresses an issue with high CPU usage in Desktop Window Manager (dwm.exe) when you disconnect from a Remote Desktop Protocol (RDP) session.”
It’s still too early to tell, but that may have finally fixed the bug.
Older programs using Visual Basic on Win10 1903 throw “unexpected error”
It took a while for this one to surface, but it appears as if older programs running on 32-bit Win10 Home version 1903 may fall over with the error “unexpected error; quitting.” Granted, there aren’t many people running programs on Win10 1903 that use VBRUN300.CLL – the apparent proximate cause of the error message – but Microsoft hasn’t acknowledged the problem.
I’m also seeing reports of the Win10 version 1903 cumulative updates for both September and October causing a Realtek LAN adapter to stop working with an Error 10. Again, the problem hasn’t been officially acknowledged.
Don’t get me started on the Autopilot sorta-security patch that was pushed out the automatic update chute then pulled without any warning or description. A Microsoft engineer has confessed that they made a mistake in releasing it – and, no, you don’t need to uninstall it.
We’re still shaking our fists at clouds on AskWoody.

September 2019
So you think Windows 10 patching is getting better? Not if this month’s Keystone Kops reenactment is an indicator.
In a fervent frenzy, well-meaning but ill-informed bloggers, international news outlets, even little TV stations, enjoyed a hearty round of “The Windows sky is falling!” right after the local weather. It wasn’t. It isn’t – no matter what you may have read or heard.
The fickle finger of zero-day fate
Microsoft has a special way of telling folks how important its patches might be. Every individual security hole, listed by its CVE number, has an “Exploitability Assessment” consisting of:
- Publicly disclosed – whether there has been open discussion of the security hole. Many holes are disclosed privately to Microsoft.
- Exploited – whether there’s an active attack in the wild
- Denial of Service – whether the security hole can be used to knock out a computer
There is also an indicator of how “likely” it is for a given hole to become a problem with the current software release and/or older versions.
It probably won’t surprise you to know that the definitions of the terms are fluid, inexact, and very hard to nail down.
Security people tend to get excited when they see an “Exploited: Yes” entry for a newly publicized security hole: Obviously, that particular bug needs to be fixed quickly because it’s out there on the loose.
Except that isn’t always the case, and it’s becoming less and less pressing as time goes on. Why? Because most of the “Exploited: Yes” zero-days are directed at a very, very narrow target population. Governments attacking governments. Big, shadowy criminal enterprises spearing high-profile targets. If you’re protecting state secrets or billion-dollar projects, sure, you need to watch out for the zero-days, and right away. If you’re a normal user, normal business, normal organization – not so much.
We saw that ambivalence in action this month. When Patch Tuesday arrived on Sept. 10, Microsoft listed two separate security holes as “Exploited: Yes” – the holes identified as CVE-2019-1214 and CVE-2019-1215. Security folks were tripping over themselves insisting that normal users needed to get both of those patches applied right away.
And then, without announcement or fanfare, sometime late on Sept 11 or early Sept. 12, Microsoft simply switched those two patches from “Exploited: Yes” to “Exploited: No.” Few people noticed. The red flags had been thrown, the whistle blown, and those two patches remained Patching Public Enemy Nos. 1 and 2.
This month’s IE zero-day patch CVE-2019-1367
That brings me to this month’s big, scary, exploited, emergency-patched IE security hole CVE-2019-1367. In what may be the worst rollout in modern Windows patching history, Microsoft rolled all over itself.
Sept. 23: Microsoft released the CVE-2019-1367 bulletin, and published Win10 cumulative updates in the Microsoft Catalog for versions 1903, 1809, 1803, 1709, 1703, Server 2019 and Server 2016. It also released an IE rollup for Win7, 8.1, Server 2012 and Server 2012 R2. Those were only available by manual download from the Catalog – they didn’t go out through Windows Update, or through the Update Server. Admins in charge of networks were going crazy because this “Exploited: Yes” patch was out, but not in a form that they could readily push to all of their machines.
Sept. 24: Microsoft released “optional, non-security” cumulative updates for Win10 version 1809, 1803, 1709, 1703, 1607/Server 2016. Nothing for Win10 version 1903. We also got Monthly Rollup Previews for Win7 and 8.1. Microsoft didn’t bother to mention it, but we found that those Previews include the IE zero-day patch as well. This bunch of patches went out through normal channels – Windows Update, Update Server – but they’re “optional” and “Preview,” which means most savvy individuals and companies won’t install them until they’ve been tested.
Sept. 25: Microsoft “clarified” its badly botched patching strategy:
Starting September 24, 2019, mitigation for this vulnerability is included as part of the 9C optional update, via Windows Update (WU) and Microsoft Update Catalog, for all supported versions of Windows 10, with the exception of Windows 10, version 1903 and Windows 10, version 1507 (LTSB).
It makes me wonder who was minding the store last week.
Sept. 26: Microsoft releases the “optional, non-security” patch for Win10 version 1903. It apparently includes the fix for this IE zero-day.
Sept. 30: As of early morning, Microsoft hasn’t provided additional details about the security hole or the patch. If there are exploits in the wild, I don’t know anyone who’s seen them. We also don’t know whether exploiting the security hole requires IE, or whether it can somehow be triggered without using the browser. The situation’s so absurd that Patch Lady Susan Bradley says (paywalled):
At this time, the IE exploits appear to be highly targeted and narrowly applied. But the company hasn’t clearly spelled out the extent of the threat — except indirectly by making the fix relatively difficult to get. So in what might be a first — and with some concern — I’m recommending skipping the still-optional zero-day IE patches, both the standalone updates and in the preview cumulative updates. I believe it’s safer to wait and ensure that the possible side effects are fully investigated.
We have three reported bugs in the latest IE patches.
Other problems
While September’s most spectacular patching failure incorporates innovative new screw-ups, there are plenty of mundane problems as well:
- Microsoft tried to fix the System File Checker bug in the July 2019 updates with a new version of the Defender Antimalware engine – which didn’t work.
- There were more reported problems with the Win10 version 1903 upgrade. Even though Microsoft has declared Win10 1903 “ready for broad deployment,” the upgrade is still being blocked on Microsoft’s own Surface Book 2 because it knocks out the separate (expensive) dGPU graphics card.
- Many users reported a problem in this month’s first Win10 1903 cumulative update, where audio got knocked out or turned down substantially. The bug was fixed in the third cumulative update this month.
- And in another case of déjà vu all over again, the September Security-only patches for Win7 and 8.1 install Microsoft’s telemetry Security-only, Microsoft style.
There is a bit of good news: In spite of initial reports that a working exploit of the BlueKeep vulnerability has hit the fan, there still aren’t any signs of an imminent major infection. We could use a little good news, eh?
Still and all, Win10 patching – Windows patching in general – isn’t getting better. Of this I’m sure.
Join us for free help and commiseration on AskWoody.com

August 2019
What happens when Microsoft releases eight – count ‘em, eight – concurrent beta test versions of Win10 version 1909 without fixing bugs introduced into 1903 on Patch Tuesday?
Pan. De. Moaaan. Ium.
The VB/VBA/VBScript debacle
No doubt, you recall the first wave of pain inflicted by the August 2019 patching regimen. Microsoft somehow managed to mess up Visual Basic (an old custom programming language), Visual Basic for Applications (for Office macros) and VBScript (a largely forgotten language primarily used inside Internet Explorer). Folks running applications in any of those languages would, on occasion, receive “invalid procedure call error” messages when using apps that had been working for decades.
Some companies’ commercial applications stopped working intermittently. More importantly, many large corporations’ internal custom programs turned belly-up.
The bug affects every single version of Windows – all the way from Win7 to Win10 version 1903. I think of it as Patching as a Keystone Kops Service.
If you’ve been following the details, you know that on Aug. 16, three days after Patch Tuesday, Microsoft released fixes for the bug in:
- Win10 version 1709
- Win7
- 1
- Server 2008
- Server 2008 R2
- Server 2012
- Server 2012 R2
Then on Saturday (!), Aug. 17, we got fixes for:
- Win10 1809
- Win10 1703
- Win10 1607
- Win10 1507
- Server 2016
- Server 2019
And on Monday, Aug. 19, Microsoft released a fix for:
- Win10 1803
As of today, Aug. 30, we still don’t have a fix for Win10 1903, the latest version of the last version of Windows. It’s not clear why, but I have a guess that Microsoft’s so wrapped up in beta testing Win10 1903 that it somehow fell through the cracks. We still don’t have the second August cumulative update for Win10 1903 – the one that’s common called “optional non-security,” with varying degrees of accuracy. And therein lies a tale.
The unholy mess that is Win10 1909 beta testing
Normally, beta testing doesn’t have much of an influence over month-to-month patching. But this month it looks like we had a significant divergence of direction.
For the past year, Microsoft has been testing its Win10 1903 patches thoroughly, using the Windows Insider Release Preview ring. That’s great – it’s what the Release Preview ring was made for.
During the month of August, though, the Microsoft beta people took over a corner of the Release Preview ring and pushed the beta version of 1909 onto (supposedly) 10% of the 1903 testers. The official announcement came on Aug. 26:
For a small subset of Insiders (around 10%) in the Release Preview ring, we have enabled the “seeker” experience for version 1909 [Editor’s note: MS calls it 19H2, just to confuse you]. For these Insiders, if they go to Settings > Update & Security > Windows Update, they will see that there is a Windows 10, version 1909 update available. They will be able to choose to download and install this update on their PC. After the update finishes, they will be on version 1909 [Editor’s note: I changed it again] Build 18363.327.
That seems complicated, but reasonable enough – until you realize that the Win10 1909 beta currently has eight different versions. Some of those versions are being distributed to people who are in the Release Preview ring. In particular, the 18362.327 preview of the Win10 1903 patch went out at the same time “the 10%” got a Win10 1909 patch called 18363.327 (see how 18362 changes to 18363?)
Apparently that build wasn’t good enough, so on Aug. 29 we got the latest bifurcated patch 18362.329 (for the 90%) and 18363.329 (for the 10%). It looks like we’re waiting until Microsoft gets the bifurcated patch to work on both Win10 version 1903 and on the beta of version 1909.
Regardless of the genesis, those of you waiting to get a fix for the VB/VBA/VBScript problem in Win10 version 1903 will have to wait a little longer.
While DejaBlue simmers
All of this would be frustratingly academic, if it weren’t for the fact that DejaBlue – a new set of “wormable” security holes in Windows itself – made its debut this month. While I’ve read lots of Chicken Little reports that DejaBlue has been exploited, none of those warnings has come true. As of this moment, there are no publicly available DejaBlue exploits.
Of course, plenty of people are trying to build them.
Until Microsoft releases a fix for the VB/VBA/VBScript problem in Win10 1903, you have two choices – either patch, protect yourself from DejaBlue, but break VB. Or you can hold back on patching, keep VB working, but leave your system open to a DejaBlue infection.
Nice choice, eh?
From the oldies but goodies file
We’ve had loads of additional fun ‘n games this month:
- Microsoft was blocking August Win7 patches on systems running Symantec/Norton antivirus, apparently because of the shift to SHA-2 encryption, which has been widely anticipated for six months. The block was lifted – but apparently nothing was changed. We still don’t know why.
- There have been many reported problems with this month’s .NET updates.
- We found out that the August Security-only Win7 patch does NOT contain the telemetry subsystem so evident in the July Security-only patch.
- There’s a hue and cry about a 20-year-old security hole in MSCTF.DLL, which is apparently fixed in this month’s patches. I haven’t heard of any exploits in the wild.
- Several folks have reported that the Win7 boot error 0xc0000225 happens if you haven’t properly installed the SHA-2 patch. Don’t worry about the alphabet soup, just install the BitLocker patch KB 3133977.
Have a patching problem? Don’t we all. Join us on AskWoody.com.
July 2019
This month, Microsoft Patch Land looks like a stranger Stranger Things Upside Down, where Security-only patches carry loads of telemetry, Visual Studio patches appear for the wrong versions… and we still can’t figure out how to keep the Win10 1903 upgrade demogorgon from swallowing established drivers.
As we end the month, we’ve seen the second “optional” monthly cumulative updates for all Win10 versions — the 1903 patch was released, pulled, then re-released — and fixes for Visual Studio’s transgressions. There’s a kludge for getting the Win10 1903 upgrade to work. And BlueKeep still looms like a gorging Mind Flayer.
Win7 Security-only patch brings telemetry
Those of you who have been dodging Windows 7 telemetry by using the monthly Security-only patches — a process I described as “Group B” three years ago — have reached the end of the road. The July 2019 Win7 “Security-only” patch, KB4507456, includes a full array of telemetry/snooping, uh, enhancements.
We don’t know what information Microsoft’s collecting with the new patch, but if you’ve been hoping to minimize Microsoft snooping by staying on the increasingly difficult Security-only path, the jig is up. You have two options:
- Install the July Security-only update and start sending your telemetry to Microsoft, or
- Stop patching entirely (“Group W”), six months before Win7’s end of life
It’s not an easy choice.
In my opinion, if you want to continue to patch Win7, you’re better off paying the devil his due and installing the Win7 Monthly Rollup, KB4507449 (“Group A”). That’ll give you the full version of Win7 telemetry, along with many small bug fixes.
To be sure, there are two sides to this development. On the one hand, you have people who feel that Microsoft should start collecting all of the data it can to guide the inevitable demise of Win7 and help customers onto Win10. On the other hand, you have people who just don’t like the intrusion.
I’m surprised that regulators haven’t launched an investigation into Microsoft’s newfound nosiness, but the fact remains that we don’t know what telemetry is being collected along either the Monthly Rollup or Security-only path.
Win10 1903 upgrade block for Intel RST drivers
Microsoft has halted Win10 version 1903 upgrades for PCs that have older versions of the Intel Rapid Storage Technology (RST) drivers. (Think Optane memory or certain RAID drivers.) The latest official Release Information status page says:
To safeguard your update experience, we have applied a compatibility hold on devices with Intel RST driver version between 15.1.0.1002 and 15.5.2.1053 installed from being offered Windows 10, version 1903 or Windows Server, version 1903 until the driver has been updated.
Just one problem. Many, many people report that the Win10 1903 upgrade refuses to proceed in spite of the fact that they have recent Intel RST drivers. When they try to upgrade to 1903, they’re getting a block notice, which looks like this:
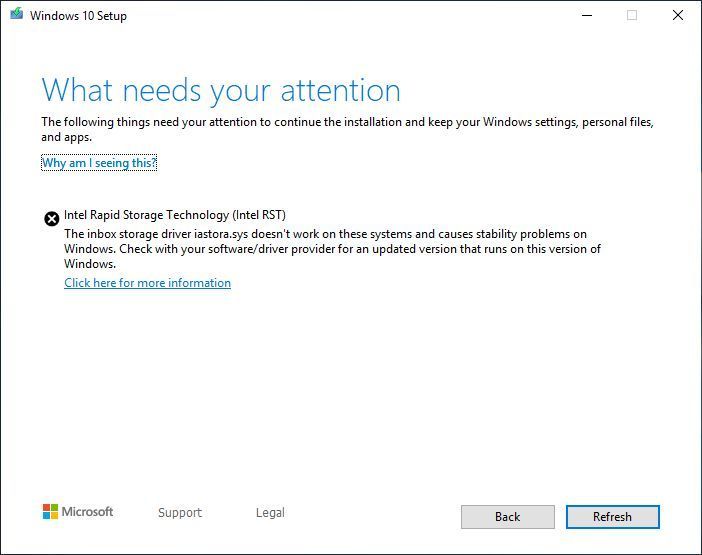
This is in spite of the fact that these folks have moved heaven and earth to try to get the latest versions of the RST drivers. An anonymous poster on AskWoody has a workaround that may or may not apply in all situations.
To my point of view, this is a feature, not a bug. It’s still too early to move to Win10 version 1903. There are still too many bugs lurking about — this being an excellent case in point. Give 1903 a few more months to mature, and then let’s take a new look.
It’s very difficult to keep the 1903 upgrade from changing your drivers
Speaking of problems with the Win10 1903 upgrade, Rick Corbett has been trying to get the 1903 upgrade to bypass updating his drivers — he has his drivers set up the way he likes, and he doesn’t want the upgrader to come in and mess with them.
So far, we don’t have a definitive method for blocking new drivers. In particular, the techniques that worked for 1809 and earlier aren’t working right in 1903.
Second monthly Win10 cumulative updates are all available
The second, “optional” Win10 July cumulative updates are all out, although the 1903 patch was posted last Thursday, pulled, then released again last Friday.
Miscellaneous problems with Visual Studio, SQL Server
If you couldn’t get the Visual Studio patch KB4506161 installed, you aren’t alone. Microsoft messed up the version detection mechanism. It was fixed in a re-release on July 19, leaving admins everywhere scratching their heads for 10 days.
Also, in case you missed it, SQL Server 2008 has been relegated to the big bit bucket in the sky. Susan Bradley has the full story, including some workarounds, in her Patch Watch column.
Updated support sites
We have a new set of Servicing Stack Updates for all versions of Win10, as well as Win8.1. (If you use Windows Update to get your updates, you don’t need to worry about the new SSUs. They only apply if you manually install updates.)
There are new lists of cumulative updates for .NET:
There aren’t any entries in the latter list, so far.
Get Windows XP, Vista, Win7 systems patched to May
I would remiss if I didn’t repeat, loudly, the BlueKeep message I’ve been posting for months. If you run a WinXP, Vista, Win7, Server 2003, or Server 2008 machine and you haven’t installed the May patch, you’re playing with fire. Tell your friends to get patched. There are still many hundreds of thousands of machines sitting out there with “Kick me” signs facing the internet.
Although there’s a BlueKeep exploit available for sale, it hasn’t turned into a for-real threat. Yet.
Don’t let the heat get to you. We’re cool on the AskWoody Lounge.
June 2019
How many bugs could a WinPatcher patch, if a WinPatcher could patch bugs?
Ends up that June’s one of the buggiest patching months in recent memory – lots of pesky little critters, and the ones acknowledged by Microsoft led to even more patches later in the month.
In June, we saw eight single-purpose Windows patches whose sole mission is to fix bugs introduced in earlier Windows patches. I call them silver bullets – all they do is fix earlier screw-ups. If you install security patches only, these eight have to be installed manually to fix the bugs introduced earlier. It’s a congenital defect in the patching regimen – bugs introduced by security patches get fixed by non-security “optional” patches, while waiting for the next month’s cumulative updates to roll around.
The Win10 Silver Bullets
Every modern version of Win10 except 1903 – which is to say, versions 1607, 1703, 1709, 1803, 1809, Server 2016 and Server 2019 – all got three cumulative updates this month. The third cumulative update for June resolves this one issue:
Devices may have issues connecting to some Storage Area Network (SAN) devices using Internet Small Computer System Interface (iSCSI) after installing KB4497934. You may also receive an error in the System log section of Event Viewer with Event ID 43 from iScsiPrt and a description of “Target failed to respond in time for a login request.”
In other words, it’s a silver bullet – an optional patch that fixes a bug introduced in an earlier patch that you’ll only get if you download and install it manually, or if you click on “Check for updates.”
What’s strange about this bevvy of patches is the timing. Apparently, the bug arrived with the third May cumulative updates on May 21. I first saw mention of it on a Dell support forum, on June 11 and posted about it on June 19. Microsoft hadn’t acknowledged the bug at the time. (The first official announcement I saw was on June 26, the date all four silver bullets appeared.)
That’s more than a little disconcerting because Microsoft should be warning us about these problems quickly on the Release Information Status page.
The Win7 and 8.1 silver bullets
On June 20, Microsoft released silver bullet patches for Win7, 8.1, Server 2008 R2 SP1, 2012, 2012 R2, and Internet Explorer 11 to fix bugs introduced in the June 11 Monthly Rollups and Security-only patches.
The update for 7 SP1 and Server 2008 R2 SP1 KB 4508772, for Windows 8.1 and Server 2012 R2 KB 4508773 and for Server 2012:
“Addresses an issue that may display the error, ‘MMC has detected an error in a snap-in and will unload it.’ when you try to expand, view, or create Custom Views in Event Viewer. Additionally, the application may stop responding or close. You may also receive the same error when using Filter Current Log in the Action menu with built-in views or logs.”
Cumulative Update for Internet Explorer 11 KB 4508646
“Addresses an issue that causes Internet Explorer 11 to stop working when it opens or interacts with Scalable Vector Graphics (SVG) markers, including Power BI line charts with markers.”
The bug fixes are not included in the June Monthly Rollups or Security-only patches (June 11, 2019), but are included in the Preview Monthly Rollups released on June 20.
Once again, bugs introduced by security patches are getting the latest fixes in non-security patches.
More Win10 1903 bugs
The second monthly cumulative update for Win10 1903 appeared late, as usual, on June 27. KB 4501375 includes fixes for several acknowledged bugs, including the MMC error with Custom Views described in the preceding section.
Many people are complaining that this particular patch was downloaded without their consent – which is to say, without clicking “Check for updates.” @abbodi86 looked into it and discovered:
Based on my tests… KB4501375 (18362.207) behaves exactly the same way that Feature Updates behave on 1809 and 1803 – the “download and install now” behavior. In other words, KC 4501375 will be bundled and offered as [a] secondary update with any available update even if you don’t “Check for updates.” It’s possible that the latest .NET cumulative update will trigger this behavior.
That said, deferring Feature Updates (version updates) for just 1 day makes KB4501375 go away.
Win10 1903’s disappearing Update advanced Options
We’re still in a quandary about the behavior of Win10 1903’s update deferrals.
In Win10 1903 Pro, if you go into Windows Update, advanced options, you get a pane that looks like this.
Windows 10 1903 Pro update advanced settings.
Several of you have noted that if you specify deferral options as I have here (non-zero numbers in either of the two bottom boxes), the entire “Choose when updates are installed” part of the advanced options dialog disappears.
@abbodi86 has undertaken some experiments with the settings. Here’s what he has concluded:
Yep, the Feature Update deferral box disappears once i change the entries to non-zero. Maybe it’s an intentional move so the user cannot change the period frequently? ?
Anyway, the Feature Update deferral period can be still controlled with registry setting
Group policy can be used to show you the feature update deferral period. The box will show up greyed, but at least you can know the period
@abbodi goes on to say that he tested changing the Quality Update deferral period the same way, with the same result — if you set it to anything other than zero, the whole section disappears. It may be related to an internal conflict with the way Semi-Annual Channel (Targeted) was removed.
Maybe, just maybe, this is the way it’s supposed to work. If so, I’d like to nominate this particular behavior for the “Harebrained Design” hall of fame. Giving a user an option, any option, then forcing them to dig into Group Policy to modify it, stinks.
On the radar
If you’ve been struggling with the “Intel” microcode updates for Meltdown/Spectre and other “Side Channel vulnerabilities,” you aren’t alone. The latest twist appears with Karl-WE’s enormous leg work, posted on GitHub, that brings some sense to the ongoing litany of patches.
In particular, Karl notes – and MS Security Response Center guru Jorge Lopez confirms – that the phrase in KB 4346085 that says:
Important Install this update for the listed processors only.
is, quite simply, wrong. Some of the updates apply to processors that are not listed. You’re better off trusting Windows Update to pick the ones that are right for your machine. Says Lopez:
“The team didn’t want to mislead anyone reading this KB in isolation to think that installing this KB/deploying across a fleet would mean they have met the requirement for microcode for these side-channel issues – that is only true for the processors listed on the KB. We will update the line, that’s not the right way to provide that warning. So yes, you don’t have to go through some complicated deployment matrix on this KB, but you still have to do so to determine what is protected or not (vuln scanning tools should help). The logic to apply or not a microcode update is part of the boot sequence in the OS – if the processor has a microcode revision that is older than what the OS has, the OS will update the CPU microcode as part of the boot sequence.
Expect to see a correction to the KB article shortly.
To end on a positive note… remember the BlueKeep vulnerability? The one that had me crying that the sky is falling and you needed to install the May patches, like, right away? Kevin Beaumont (Twitter’s @GossiTheDog) has good news:
If anybody is pondering why there’s no public BlueKeep Remote Code Execution exploit, it’s a mix of difficulty [There’s a high bar for exploitation – in theory it is ‘just’ a use after free bug, but to be able to kernel spray you have to reverse engineer the RDP driver. There’s no documentation on how to do it for this.] and a handful of people in the InfoSec world being very responsible.
Yes, you still need to make sure you have the fix installed. You should’ve done it in May. When the exploit hits it’ll be painful. But at least we’ve been spared a bloodbath of unprecedented proportions.
Join us for more thrilling Tales from the Crypt on the AskWoody Lounge.

May 2019
In a normal month, you need a scorecard to keep track of Windows patches. Now, your scorecards need a scorecard. One ray of hope: It looks like some Windows 10 cumulative updates will include the new “Download and install now” feature.
The May 2019 Windows updates have taken so many twists and turns it’s hard to pin things down, but as of Thursday morning, here’s what we’ve seen.
Windows 10 cumulative updates
As of now, all of the recent versions of Win10 (1607/Server 2016, 1703, 1709, 1803, 1809/Server 2019) have had three cumulative updates in May. Depending on where you live (or, more correctly, which locality you’ve chosen for your machine), you’ve been pushed one or two of them. If you’re a “seeker” (and clicked “Check for updates” or downloaded and installed the patches), you’ve had at least two, and maybe three. Got that?
The reason for all the hilarity: The original Win10 cumulative updates broke access to certain sites that end with “gov.uk” for Internet Explorer and Edge users. All 10 of you.
The latest “optional” (meaning for “seekers” only) non-security patches include the usual laundry list of fixes for an unconscionable number of bugs. Win10 1809, which has had an inordinate amount of work lavished on its bug fixes over the past eight months, still has several acknowledged flaws including this one:
When attempting to print from Microsoft Edge or other Universal Windows Platform (UWP) applications, you may receive the error, “Your printer has experienced an unexpected configuration problem. 0x80070007e.”
The special case of Win10 version 1903
Microsoft officially started pushing Win10 version 1903 on May 21 (see Gregg Keizer’s birth announcement), although I haven’t heard from anyone yet who’s had 1903 pushed onto their systems. Lots of people upgraded to 1903 by clicking on “Check for updates,” and many were already on 1903 when it went legit, by virtue of being in the Windows Insider Release Preview or Slow rings.
For good measure, Microsoft put its first “real” Win10 1903 cumulative update, KB 4497935, through the Release Preview wringer – a practice formerly reserved for Win10 1809 patches, which were notoriously late and arguably better vetted. All sorts of confusion resulted when KB 4497935, the May 29 cumulative update for 1903, was released to the teeming masses. (I heard lots of complaints about update deferral settings not being honored.)
As it happens, the settings for those still in the Insider program are different from the settings for those who received their copies of 1903 without being beta testers. Günter Born has a detailed explanation of what he’s seen in various permutations and combinations.
The single most important fix to Win10 this month arrived on Wednesday with the Win10 1903 KB 4497935 update:
Addresses an issue that may cause an external USB device or SD memory card to be reassigned to an incorrect drive during installation.
Win10 1903, as shipped, had a bug in it that swapped drive letters willy-nilly on external USB drives, SD memory cards, and even some internal drives. Susan Bradley put it this way:
My Lenovo laptop is “throttled” because I have an external usb drive that I am using to upgrade this device. This doesn’t bode well for my Acer that only has 32 gigs that I HAVE to attach an external hard drive in order to upgrade it.
So it now appears as if this cumulative update will fix Win10 1903. But in classic Catch-22 fashion, you can’t install the cumulative update on a machine that needs a USB drive in order to install the update.
In more Win10 1903 news, Trend Micro now says it won’t have a fix for Win10 1903 compatibility problems with its Apex One/OfficeScan XG SP1 products until early June. Microsoft’s release information page doesn’t mention the gaffe, although it does acknowledge the Sandbox fail to start with error code “0x80070002” bug, Dolby Atmos bugs, AMD RAID driver incompatibilities, display brightness issues, and a dozen additional bugs that should keep you from installing 1903 until Microsoft gets its act together.
See what I mean about scorecards?
Hope that the ‘Download and install now’ option will work with cumulative updates
Microsoft has been talking about – and showing off – a new feature called “Download and install now” that will give everyone some control over when Win10 updates get installed. It’s a tremendous new feature – arguably the most important new feature in Windows 10 since the very first version shipped almost four years ago.
The official explanation of the feature states without reservation that the “Download and install now” option will be available for version changes: Before your machine is upgraded to a new version of Win10, you have to explicitly ask for it. Great. The explanation doesn’tspecifically say that the same “Download and install now” option will be available for cumulative updates.
Earlier this month, I wrote about the implications: “Download and install now” for version changes is tremendous. “Download and install now” for cumulative updates would be a game-changer, at least for those of us concerned about bad patches.
Now comes word from Leopeva64 – who’s been right about several Windows Update revelations – that Microsoft may implement “Download and install now” for (many? most? all?) of the monthly second (or third or fourth) “optional non-security” patches.
Time will tell, but we may be witnessing a real breakthrough.
‘Wormable’ BlueKeep still on the horizon
Earlier this month we had quite a shock when Microsoft announced, with appropriate fanfare, that every Windows XP, Win7, Server 2003, 2008 and 2008 R2 machine needed an inoculation to protect against a very mean “wormable” hole in Windows Remote Desktop Services. Billed as the son of WannaCry, Microsoft had everyone – including me – sounding the alarm to get the crazy thing patched.
Now, two weeks later, BlueKeep (as Kevin Beaumont has named the hole) is still a threat, but it’s nowhere to be seen. Ends up that creating a real, working, destructive worm using the security hole is a highly non-trivial task.
I’ve asked every expert I can find about an obvious solution — isn’t it sufficient to simply turn off the Remote Desktop Protocol in the user interface? (In Win7, Start > Control Panel > System and Security > System > Remote Settings, in the System Properties dialog box, click Don’t Allow Connections to This Computer.) That, and/or blocking port 3389 (the port RDP uses by default) should be enough to keep any RDP-related malware at bay. At least, it appears that way to me.
But I haven’t received a positive response from any of those experts. The ones who know ain’t sayin’. And the ones who probably do know aren’t willing to stick their necks out. It’s hard to fault them: Microsoft hasn’t provided any guidance on the matter, one way or another, so if blocking RDP ends up being insufficient — no matter how logical — there’s a lot of exposure to the person making the recommendation.
Oh. For the dozens of you who still use Vista, Microsoft initially forgot to mention that the Server 2008 SP2 version of the patch also works with Windows Vista.
Peruse the Patching Pilgrim’s Progress on the AskWoody Lounge

April 2019
You have to wonder who’s testing this stuff.
Admins, in particular, have had a tough month. April brought widespread breakdowns – bluescreens, hangs, very sluggish behavior – to hundreds of thousands of Win7 and 8.1 machines. This wasn’t a “small percentage” kind of event. For some companies, rebooting overnight on Tuesday brought seas of blue screens on Wednesday morning.
The first round of cumulative updates and Monthly Rollups arrived on Patch Tuesday, but the now-ubiquitous second round didn’t show up until late Thursday afternoon, two and a half weeks later. Talk about admins taking a beating.
We still have one Tuesday left this month – the mythical “E week” that Microsoft never talks about – so the month may yet end with both a bang and whimper.
Here’s how things look as early Monday morning.
Still no ‘optional non-security’ cumulative update for 1809
It took a while, but the second round of April patches finally arrived. The one exception is for Windows 10 version 1809, which still hasn’t seen an “optional non-security” patch. (They’re “optional” because you have to be a seeker – click Check for updates – in order to get hit with the patch.)
We have a reliable report that the second patches this month were held up because of continuing problems with the Japanese new era date bugs. That same report also says that even the latest patches have bugs. I find it all amazing – Microsoft’s been working on this problem for at least a year, and the patches-of-patches have been stumbling all over themselves.
Even Win10 1903 – the version still in beta testing – got a new patch, KB 4497093, bringing the build number up to 18362.86. It’s for “Insiders who are currently in the Fast ring only and on Build 18362.53. We’ll roll this out to the Slow and Release Preview rings in a bit.”
Six dirty patches, five blasted antivirus companies
April’s Patch Tuesday brought immediate complaints of Win7 bluescreens. Within a couple of days we found out that six patches – for Win 7, 8.1, Server 2008 R2, 2012 and 2012 R2 – had conflicts with five different companies’ antivirus products. The current tally:
Sophos – The company now says it’s figured out the source of the problem:
“We have identified a permanent fix and are now automatically rolling out the fix to customers starting 25th April 2019. This will take place over a two- to three-week period.”
Microsoft continues to block the six dirty patches on systems running Sophos Endpoint.
Avira – The folks at Avira have been remarkably quiet. Our latest report from UAz says they may have finally hit upon a solution – verified in the very early hours of Monday morning. Earlier attempts at an Avira solution failed, sometimes spectacularly. Microsoft has not changed its terse announcement:
“Microsoft has temporarily blocked devices from receiving this update if Avira antivirus software is installed. We are presently investigating this issue with Avira and will provide an update when available.”
Arcabit – The small Polish-language AV supplier has released an update that solves the problem, according to Microsoft, although the Microsoft link to Arcabit’s support article points to a Technical Assistance phone number, and no discussion.
Avast/AVG – The company has issued hotfixes to avoid the bluescreens. (Avast owns AVG.) Oddly, though, the way to install the hotfixes isn’t what you might expect:
- Boot your machine
- Let the machine stand for approximately 15 minutes while emergency updater works. The updater runs on system context rather than the user, so you do not need to log in for it to activate.
- Reboot your machine. Your machine should now operate normally, even with the Microsoft updates listed above.
That, to me at least, is a very distressing way to apply a hotfix.
Microsoft no longer blocks the six dirty patches on machines running Avast or AVG.
McAfee – Late to the game, McAfee has acknowledged that installing the dirty six patches may lead to slow boot up times or slow performance. The only solution to the problem, at present – aside from uninstalling the dirty six – is to disable any user-defined (non-default) Access Protection rules.
Microsoft says it is “presently investigating this issue with McAfee,” but they’ve been saying that for a week.
A few more patch problems
I’m seeing scattered reports that Win7 users are being offered KB 3185319 — an update from Sept. 13, 2016 — as a checked Important update to Win7. It’s part of the MS16-104 bundle. I wrote about bugs in this patch back in October 2016. This isn’t the first time we’ve seen KB 3185319 appear out of the blue.
There are also reports of locked Server 2008 machines after installing this month’s Monthly Rollup, KB 4493471.
Keep up with the latest on the AskWoody Lounge.

March 2019
March was an unusually light patching month – all of Office only had one security patch – and there don’t appear to be any immediate patching worries. Just as in the past few months, Microsoft’s holding off on its second cumulative update for Windows 10 1809, raising hopes that it’s taking Win10 quality more seriously.
Win10 1809 deployment proceeded at a positively lethargic rate, even though Microsoft declared the OS fit for business consumption last week, leading to all sorts of speculation about the next-next update, Win10 version 1903, ultimately overtaking its younger sibling.
Dell’s Encryption Console gets clobbered by March’s Patch Tuesday Win10, 8.1, 7 patches
Dell has confirmed that every Windows patch in March – every one of them — bowled over its Encryption Local Management Console. The only solution offered is to either roll back the March patch or upgrade to Dell Encryption 10.2.1.
Few individual users have the Encryption Console, but it’s not uncommon on corporate machines.
Win10 version 1809 second cumulative update still MIA
All of the Windows 10 versions had two cumulative updates in March, except for Win10 version 1809, the latest version of the last version of Windows. I take it as a hopeful sign that Microsoft’s spending more time to get the bugs ironed out before delivering the “optional non-security” Win10 patch. (It’s “optional” in the sense that you’ll only get it if you click on “Check for updates.”)
There are five irritating, acknowledged bugs in Win10 1809 that haven’t been fixed yet:
- IE 11 authentication issues
- Audio devices stop working unexpectedly
- MSXML6 may freeze the system
- Custom URI schemes may not work correctly
- Windows Deployment Services PXE may not work
Other versions of Win10 have some of the same bugs, introduced by earlier patches.
Just what Windows 7 needs – another round of ‘Get Windows 10’ nags
We’re covering the demise of Windows 7 intently over on AskWoody. But there’s one thing you definitely don’t need – another nagging patch from Microsoft. KB 4493132, a Win7 patch that does nothing bug nag, is definitely worth skipping.
We have some late-breaking news from Michael Horowitz that Win7 now has a scheduled task called refreshgwxconfig-B that seems to be associated with the widely despised “Get Windows X” campaign. It’s not clear at this point where the unwanted task came from.
Win10 1809 now ready for prime time, with 1903 on its heels
Microsoft changes its Windows updating terminology capriciously and with absolutely no consideration for settings baked into earlier versions of Win10. But never mind. With word from on high that Win10 version 1809 has been deemed worthy of business deployment, we also have assurances that we’ll get similar confirmation for Win10 versions from 1903 onward. (And that makes me wonder whether we’ll have yet another change in terminology soon.)
In general, March’s patches seem quite tame. Let’s hope that’s the new normal.
Questions answered and discussions dissed on the AskWoody Lounge.

February 2019
Microsoft continues to hold Windows 10 version 1809 close to the chest. While all of the other Win10 versions have had their usual twice-a-month cumulative updates, the latest version of the last version of Windows, 1809, still sits in the Windows Insider Release Preview Ring.
For most people, that’s excellent news. It seems that Microsoft is willing to hold off until they get the bugs fixed, at least in the 1809 releases. May I hear a “hallelujah” from the chorus?
Mystery update bulldozer KB 4023057 hits the Catalog
You’ve heard me talk about KB 4023057 many times, most recently in January. It’s a mysterious patch that Microsoft calls an “update reliability improvement” whose sole reason for existence, as best I can tell, is to blast away any blocks your machine may have to keep the next version of Windows (in this case, Win10 1809) from installing on your machine.
KB 4023057 and its predecessor KB 4022868 have gone through 50 or so versions over the past three-plus years, and it’s always been distributed stealthily – you get it when you install updates, unless you go to great pains to block it. @PKCano has a thorough description of the tortuous procedure for preventing its installation.
Now comes word from @abbodi86 that on Thursday, for the first time, KB 4023057 has appeared in the Microsoft Update Catalog. It’s not clear why the old bete noire has been elevated to Catalog status – and I doubt Microsoft will ever tell us.
Old Access bugs fixed. Mostly.
February’s earlier Windows patches wreaked havoc on old Access databases. In January, Access 97 file format databases got clobbered by all of the Windows updates. Then Access 95 databases got the shiv. It’s almost as if nobody tests the Win10 cumulative updates against older databases, wouldn’t you say?
As of this writing, all is well (apparently), except for Win10 version 1809, which hasn’t yet received the Access 95 inoculation.
Word to the wise: If you have an older database program that you really need to use, watch out.
Fixing with a wing, a prayer, and a silver bullet
There’s a smattering of new bugs introduced by the Patch Tuesday patches, and subsequently fixed by Third Tuesday patches. The most entertaining of the lot is the Internet Explorer backslash bug. Of course, you don’t use IE, but for those who do…
February’s Patch Tuesday patches for Win7 and 8.1 contained this weird, acknowledged, bug:
After installing this update, Internet Explorer may fail to load images with a backslash () in their relative source path.
That bug, and several others, were fixed in the Third Tuesday Monthly Rollup preview patches – but those aren’t distributed through normal channels. You have to wait until later in March, when the Monthly Rollup Preview patches will (presumably) be added to the March Monthly Rollups. Got that? A bug in the February security update is fixed by a patch in the next month’s (presumably non-security) monthly rollup.
Here’s where things get weird. On Feb. 19, Microsoft released KB 4491113, a “Cumulative update for Internet Explorer: February 19, 2019,” which is a silver bullet patch with one intent:
This cumulative update includes improvements and fixes for Internet Explorer 11 that is running on Windows 8.1 or Windows 7, and resolves the following issue:
Internet Explorer cannot load images that have a backslash () in their relative sources path.
So we have a cumulative update, KB 4491113, that fixes a bug introduced in this month’s Monthly Rollups, but which is also fixed in this month’s Monthly Rollup previews. The previews fix other bugs as well, but I guess this one was problematic enough to warrant a single silver bullet.
Except… now comes word (from an anonymous poster) that KB 491113 is causing problems:
FWIW, this “silver bullet” isn’t quite ready to be fired; it caused problems with the game Halo: Spartan Strike by omitting some of the sound and then letting the game hang after a few minutes. It may also have caused some problems with videos on Firefox. Upon uninstalling, the Spartan is again killing Covenanters and Prometheans with full sound.
If you’re using Win10, the bug was fixed in the Third Tuesday patches – except for Win10 1809, which doesn’t yet have a Third Tuesday patch.
Moral of the story: Internet Explorer isn’t a browser. It’s a decorative appendage.
To further complicate matters, the Win8.1 Monthly Rollup Preview, which fixes this bug, introduces a truly bizarre bug that enables Location Services and makes a nuisance of itself in the Notification (er, Action) Center.
Windows 10 1809 still not ready for prime time
Microsoft changed its terminology, again, but it hasn’t yet officially declared that version 1809 is ready for business deployment. You can think of that as CBB, or SAC-not-T, SP1, or VGBS (venerable gray beard status), but whatever hokey name you put to it, the fact remains that Microsoft has not yet come out and said that Win10 version 1809 is suitable for mass consumption.
The official Windows 10 release information page still lists it as “Semi-Annual Channel (Targeted),” which is old terminology but with a judicious nod and wink – and with a dearth of additional reassurances – it’s clear that Microsoft isn’t yet recommending that businesses move onto the latest and greatest.
Hard to say when that’ll happen, but there’s lots of pressure to brand Win10 1809 as “ready for business” (CBB, SAC, SP1, VGBS, whatever) before Win10 1903 arrives…. which should be in 3… 2… 1…
Keep up on the parts of Windows that matter on the AskWoody Lounge.

January 2019
In general, the January patches look relatively benign, but for some folks in some situations they can bite. Hard.
On the surface we’ve seen the usual Patch Tuesday Cumulative Updates and secondary Cumulative Updates for all versions of Windows 10. Microsoft calls the secondary Cumulative Updates “optional” because you only get them if you click “Check for updates.”
Windows 7 and 8.1 got their usual Monthly Rollups, but there’s a problem. Specifically, this month’s Win7 Monthly Rollup has a couple of bugs that are only fixed if you install the preview of February’s Monthly Rollup. Which makes no sense at all, but that’s Microsoft. There’s another Win7 Monthly Rollup bug that’s fixed by installing a different “silver bullet” patch.
A Win10 version 1809 .NET patch, KB 4481031, rolled out as a Preview when it wasn’t. Some folks woke up one morning to a notification that their PC was no longer activated. That was a bug on Microsoft’s side. Oops.
Office 2010 took one on the chin. Two, actually. And it looks like the Japanese calendar problem’s still there, with “fixes” bringing Word, Excel and Access to a halt.
And then there’s a reprisal of the mysterious KB 4023057 “update reliability” patch, throwing error 0x80070643 on some machines.
It’s been a patch pokin’ month.
Windows 10
All of the extant versions of Windows 10 got Patch Tuesday cumulative updates this month, and then the usual second round of cumulative updates. The former came down the Automatic Update chute; the latter lie in wait unless you click “Check for updates.” That’s been the common, infuriating, behavior for several months. Nothing new.
What isnew is the remarkable delay in releasing the second patch for Win10 version 1809 – the KB 4476976 “October 2019 Update.” Microsoft held onto that patch for an extra week, putting it through an unusual second round of beta tests in the Windows Insider Preview Ring. That’s great news: It shows Microsoft’s taking its time to push out the 1809 updates.
It remains to be seen if the new-found restraint will result in less-buggy patches, but slowing down the gauntlet certainly rates as a step in the right direction.
The two major bugs in all of this month’s Win10 patches are the acknowledged ones:
- Applications that use a Microsoft Jet database with the Microsoft Access 97 file format may fail to open if the database has column names greater than 32 characters. The database will fail to open with the error, “Unrecognized Database Format”.
- After installing KB4480966, some users report that they cannot load a webpage in Microsoft Edge using a local IP address. Browsing fails or the webpage may become unresponsive.
The first bug strikes (old!) applications written in Access 97 and in other database packages. There’s a manual solution, but it isn’t pretty, and it requires you to convert the database to a newer format. That’s not welcome news to anyone who’s nursing an old database.
The second bug has a simple workaround: Don’t use Edge. As if you needed me to tell you that.
Win10 version 1809 .NET patch KB 4481031
This was yet another Keystone Kops patch. Microsoft originally released KB 4481031 with a KB article that said it was a “Preview of Cumulative Update.” It was actually a real patch. Microsoft pushed KB 4481031 out the Windows Update chute. That, we were told two days later, was a mistake. Right now, I’m told, KB 4481031 is a for-real cumulative update that’s only being pushed to people who click “Check for updates.”
Windows 7 and 8.1
I don’t believe the conspiracy theories – that Microsoft’s intentionally planting bugs in Win7 patches to prod people on to Win10. But I do believe the complacency theories – that Microsoft’s focusing on Win10 efforts to the detriment of Win7 users, in particular.
This month we saw two big bugs introduced in the Win7 Monthly Rollup, along with the Access 97 file format problem in Win10:
- Local users who are part of the local “Administrators“ group may not be able to remotely access shares on Windows Server 2008 R2 and Windows 7 machines after installing the Jan. 8 security updates. This does not affect domain accounts in the local “Administrators” group.
- Some programs don’t display F1 Help correctly.
The first problem is pretty specific: You have to be running a peer-to-peer network, and the person trying to get to the shared folders has to have an administrator account on the shared folder’s PC. Microsoft released a “Silver Bullet” patch for this specific problem, KB 4487345. Susan Bradley has a more detailed explanation – and advice if KB 4487345 doesn’t work – in her Patch Watch column.
The second problem (which isn’t acknowledged in the Monthly Rollup KB article) can be fixed by installing the preview of next month’sWin7 Monthly Rollup, KB 4480955.
There’s an additional problem. Installing KB 4480970 (this month’s Monthly Rollup) or KB 4480960 (security-only) breaks RDP on Server 2008 R2 systems. It looks like installing the Silver Bullet patch KB 4487345 also fixes this problem.
Patch Tuesday also brought an embarrassing barrage of activation failures and “Not genuine” / ”counterfeit copy of Windows” notifications on Win7 machines with volume licenses. Microsoft has confirmed that the problem isn’t with this month’s update, it’s with Microsoft’s activation servers. Which have since been fixed. Supposedly.
Windows 8.1 continues its admirable stretch as the most stable version of Windows yet.
KB 4023057 reappears
Now in its 50th-or-so incarnation, KB 4023057, the “update reliability improvement” rolled out to Win10 1507, 1511, 1607, 1703, 1709 and 1803 machines. Microsoft still hasn’t said what KB 4023057 actually does, the KB article is a baffling bit of bull… pablum.
Speculation is that KB 4023057 blasts away any impediments you’ve set to the automatic installer. @ch100 on AskWoody has offered the only explanation that makes sense to me:
KB4023057 was and still is one of the most weird and unexplained updates in the recent times. This update has never been offered to WSUS, but only to Windows Update. This would indicate that it [was] meant for unmanaged end-users and unmanaged small business users…
This patch may be harmless, but why it was released and where it actually applies, it is still a mystery.
More Office 2010 messes
Patch Tuesday also brought KB 4461614, an Office 2010 security update. Unfortunately, as soon as you install that patch, Access and Excel stop working. Ten days later, Microsoft issued a replacement, KB 4462157. Now we have notices that KB 4462157 breaks Office 2010 entirely on Windows XP machines.
Pro tip: If you’re still running XP, you have worse things to worry about.
We’ll keep you posted on patches on the AskWoody Lounge.

December 2018
Just when you’re ready to settle in for some egg and nog and whatever may accompany, Windows starts throwing poison frog darts. This month, a fairly boring patching regiment has turned topsy turvey with an unexplained emergency patch for Internet Explorer (you know, the browser nobody uses), combined with an Outlook 2013 patch that doesn’t pass the smell test.
Mysterious bug fix for IE
Microsoft set off the shower of firecrackers on Dec. 19 when it released a bevy of patches for Internet Explorer:
Win10 1809 – KB 4483235 – build 17763.195
Win10 1803 – KB 4483234 – build 17134.472
Win10 1709 – KB 4483232 – build 16299.847
IE 11 on Win7 and 8.1 – KB 4483187
As Gregg Keizer explains in his Computerworld analysis:
Microsoft issued a rare emergency security update to plug a critical vulnerability in the still-supported IE9, IE10 and IE11. The flaw was reported to Microsoft by Google security engineer Clement Lecigne. According to Microsoft, attackers are already exploiting the vulnerability, making it a classic “zero-day” bug.
That’s what Microsoft claimed; from the description it sounds like a drive-by hole, where you can get infected by merely looking at a bad website. But in spite of dire warnings from many corners, there’s exactly no information about the vulnerability making the rounds. In a situation like this, one would expect some sort of detailed explanation from Microsoft, Google or Lecigne. As of early Friday morning, we’ve seen nothing.
Perhaps all the explainers are already beset with visions of sugarplums, but it’s mighty odd for an emergency patch to hit the offal fan with nary a hint of what’s wrong, or why it needs to be fixed with such abandon. This isn’t a garden variety “C” or “D” week non-security patch. It’s a full 10-claxon call to arms at a time when most people are taking an early vacation. Or at least a languid liquid lunch.
To add to the urgency, Microsoft Thursday night issued a similar tiny IE patch for the latest beta test round of the next version of Win10 – KB 4483187 brings the “19H1” beta build up to 18305.1003. So something’s afoot, but we don’t know what.
As most of you know, patching IE isn’t just for people who actually use IE. Microsoft has woven IE into the fabric of Windows – and it’s still there despite a decade-or-so of extraction effort. An IE patch is an important event because a hole in IE can manifest itself in many ways. But in this case, with no clear explanation, we don’t know what ways, or whether you’re only at risk if you actually use IE.
It gets worse.
I’m seeing reports that the Win7 patch, KB 4483187, triggers random crashes. Removing the update restores the machines. But with the holidays about to go into full swing, it’s hard to say if that’s an isolated incident or a lump of cantankerous coal.
Outlook 2013 patch Three Card Monty
Also on Thursday, Microsoft released yet another mysterious patch, KB 4011029, the “December 20, 2018, update for Outlook 2013.” According to the KB article, it fixes a bug where Mail delivery rules stop working. When you try to open the “Manage Rules & Alerts” dialog box in Outlook 2013, you receive the following error message:
The operation failed because of a registry or installation problem. Restart Outlook and try again. If the problem persists, reinstall.
Nice little holiday bug for anyone using rules in Outlook 2013. But, again, there’s more to the story.
Three days ago, Microsoft acknowledged a bug in Outlook that’s identical to the one described in the KB 4011029 article, but it affects three different “perpetual” (which is to say, bought and installed) versions of Outlook – Outlook 2010, 2013 and 2016 — plus bugs in four different subscription (which is to say, rented versions) releases of Office 365:
Version 1810 build 11001.20108
Version 1808 build 10730.20205
Version 1803 build 9126.2315
Version 1708 build 8431.2329
Apparently, the bug was introduced in the November security patches, but hadn’t been acknowledged until three days ago.
I’ve found no explanation for why Outlook 2013 has been patched, but the other six versions have not. It’s possible that there are five more patches waiting in the wings. It’s possible that this one patch is actually intended for other versions of Office. All we know for sure is that somebody’s left us hanging out to dry – no explanation, no release plan.
Sounds like a pretty common state of affairs, eh?
The 1809-pound elephant in the room
All of this is happening against a backdrop of Microsoft’s newly restored zeal in pushing Win10 version 1809 on all Win10 users. Reports on 1809 have been good, in general – although the new feature set won’t wow anyone but the most diehard Windows (and Notepad) fans – but Microsoft itself hasn’t yet declared version 1809 as fit for businesses.
Those who click “Check for updates” are most likely to get the new version, but it’ll get pushed on non-seekers soon enough.
The bottom line
I’ve seen exactly zero reports of machines being taken over by the Internet Explorer bug, zero detailed descriptions of the problem (or its solution), zero bonafide cause for alarm, but the “Sky is Falling – Patch Right Now!” cry continues to ring throughout the blogosphere. That could mean one of two things:
- The problem is so bad that people in the know don’t want to let the cat out of the bag, or,
- It’s a typical zero-day that’ll have to be patched eventually unless you’re the target of well-heeled nation state scoundrels and the people who do the explaining are taking the weekend off
I’m convinced the latter is far more likely. But your level of paranoia may well differ. Hey, you may actually enjoy putting your PC through the wringer while the world’s taking a well-deserved break.
We’ll keep a watchful eye through the holidays on the AskWoody Lounge.

November 2018
By far the most important reason for this month’s relative patching calm: Microsoft decided to wait and get the Windows 10 (version 1809) patch right instead of throwing offal against a wall and seeing what sticks.
What remains is a hodge-podge of Windows patches, some mis-identified .NET patches, a new Servicing Stack Update slowly taking form, a bunch of Office fixes – including two buggy patches that have been pulled and one that’s been fixed – the usual array of Flash excuses and Preview patches.
Win10 version 1809 – patching done right
In a day that will live in patching infamy, Microsoft released Windows 10 version 1809 on Oct. 2, then pulled it on Oct. 5, responding to cries of anguish and deleted data. Win10 1809 was officially re-released on Nov. 13, but very few people took the bait, and it appears as if Microsoft isn’t pushing 1809 onto any machines. Although I remain skeptical of their sampling method, AdDuplex reports that version 1809 now runs on 2.8% of all Win10 machines.
The most important patching news this month – indeed, I would argue, the most important patching news this year – is that Microsoft has finally (re-) discovered the Windows Insider Release Preview Ring. Some folks would have you believe that the Insider Release Preview Ring was designed for testing new versions of Windows. But that isn’t the way it was designed.
Here’s what Microsoft’s official Insider Program overview documentation says:
Release Preview Ring
If you want to be on the current public release of Windows 10 but still get early access to updates, applications, and drivers without taking the risk of moving to the Development Branch, the Release Preview Ring is your best option. The Release Preview Ring is only visible when your Windows build version is the same as the current Production Branch. The easiest way to go between the Development Branch to the current Production Branch is to reinstall Windows using the Media Creation Tool, see .
Now we’re seeing builds of the Windows 10 September-October-November-soon-to-be-December 2018 Update going through a proper test cycle. Not surprisingly, Microsoft has uncovered (and apparently fixed) tons of bugs in 1809, including the notorious filename extension bug and mapped drive bug. While Microsoft once said that its fixes would arrive in late November, the official status page now says they’ll arrive in early December.
At the same time, other companies have had time to get their products ready for 1809. Apple has a new version of iCloud that works with 1809. Trend Micro says it has new versions of its products either in place, or coming soon, to fix its incompatibilities. That said, upgrade blocks are still in place for AMD Radeon HD2000 and HD4000 graphics cards, with no resolution yet identified; for F5 VPN clients; and for certain new Intel display drivers.
Short version: It would be, ahem, quite foolish to install 1809 until Microsoft has figured out and released its latest cumulative update. Yes, that means the Win10 September 2018 Update won’t arrive in moderately usable form until December. So be it.
Other Windows patches
Win10 1809 is being patched in a reasonable, steady way – with beta test versions of the cumulative updates appearing in the Insider Release Preview Ring, where they can be pounded appropriately.
Alas, we aren’t so lucky with the other versions of Win10, where untested non-security bug fixes continue to appear as monthly second-round cumulative updates. We had a bunch of those this month:
- Win10 version 1803— KB 4467682 brings the build up to 17134.441. Lots and lots of little bug fixes, plus a fix for the filename association bug. 1803 still shows two known issues: The SqlConnection exception in .Net (“will provide an update in an upcoming release”), and the Seek Bar is broken in Windows Media Player (“a solution will be available mid-December 2018”).
- Win10 version 1709— KB 4467681 brings the build up to 16299.820. Another big list of bugs, same acknowledged problems.
- Win10 version 1703— KB 4467699 brings Enterprise and Education users up to build 15063.1478.
- Win10 version 1607and Server 2016— KB 4467684 brings Server and LTSC users up to build 14393.2639.
Yes, that means Microsoft is currently supporting seven different versions of Windows – Windows 7, 8.1, Win10 1607, 1703, 1709, 1803, 1809 – plus Server versions, Xbox, Mobile (sorta), Embedded, IoT, Holographic, and heaven knows what all.
It now appears as if Microsoft is installing the second monthly Cumulative Updates for seekers – those who click Check for Updates. Ouch. I thought Microsoft had backed off that particular form of insanity.
There are also new Intel microcode updates, explained in KB 4465065 (thx @ep, @ch100), as well as a new beta test version of the Win10 1809 Servicing Stack Update, which will likely appear at the same time as the Win10 September-October-November-December 2018 Update.
As things stand now, I haven’t heard any loud screams of pain stemming from the Win10 Cumulative Updates, second monthly Cumulative Updates, or the Win7 or 8.1 Monthly Rollups.
More .NET shennanigans
The .NET patches this month have provided an ongoing source of amusement. First, we were treated to an apparent typo in the description of the Win7 Monthly Rollup for .NET 3.5.1… 4.7.2 (see this thread by FanJ in the Wilders Security Forums – thx @cesmart4125). Now we have three .NET patches for Win7/8.1 in Windows Update (thx @abbodi86):
- An apparently undocumented re-issue of KB 4457920, the old 2018-09 Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows 8.1. (No indication as yet if the analogous patch for Win7, KB 4457918, has re-appeared.)
- The usual Monthly Rollup (KB 4467240 for Win7 and KB 4467242 for Win 8.1)
- The usual Preview Monthly Rollup (KB 4467224 for Win7, KB 4467226 for Win 8.1)
I’m not showing any significant problems with any of those – and no indication what’s been changed (if anything) with the 2018-09 patches.
Oh, Office
As I explained on Nov. 19, this month’s big bunch of Office patches included two non-security patches, KB 4461522 and KB 2863821, that trigger Entry Point errors in various Office 2010 products. Microsoft’s current advice is to uninstall the patches. They aren’t being distributed and haven’t been fixed.
A Patch Tuesday security update marvel, KB 4461529, crashes 64-bit Outlook 2010 on startup. Not many people use the 64-bit version of Office 2010 because it’s so buggy. Think of this as exhibit 314159. Microsoft “fixed” the bug a couple of days ago by releasing a second patch, KB 4461585, whose sole purpose appears to be fixing the crashes caused by the original.
The bottom line
The past five months have shown, repeatedly, that you’d have to be crazy – or ignorant of the past– to continue applying Windows patches as soon as they’re released. July patching was an unmitigated disaster. After some initial mis-steps, August fared substantially better. September saw a bunch of “v2” patches that got yanked suddenly, but it all worked out in the end. If you waited long enough. October fell all over itself delivering bad news. November’s better, primarily because Microsoft put the brakes on Win10 1809 and decided to actually test things before releasing them. Novel concept, that.
If you’re in charge of protecting state secrets, the pressure’s on to get the patches installed come hell or high water. Susan Bradley’s Master PatchList remains relatively calm, if you take into consideration the problems explored in this article.
As best I can tell, the biggest threat still lies in a resurgence in Equation Editor exploits. That particular Office bug was fixed (and re-fixed) almost a year ago.
November’s almost over and, with the return of sanity in Win10 1809 patching, it may just be a turning point. Things really couldn’t get much worse.
Patching pains? Join us on the AskWoody Lounge.

October 2018
This month’s bad patches made headlines. Lots of headlines. For good reason.
You have my sympathy if you clicked “Check for updates” and got all of the files in your Documents and Photos folders deleted. Even if you didn’t become a “seeker” (didn’t manually check for updates) your month may have been filled with blue screens, odd chicken-and-egg errors, and destroyed audio drivers — and Edge and your UWP (“Metro” Store) apps might have been kicked off the internet.
You didn’t need to lift a finger.
Worst Windows 10 rollout ever
Hard to believe that Windows 10 version rollouts could get any worse, but this month hit the bottom of a nearly bottomless barrel. Some folks who clicked “Check for updates” wound up with a brand spanking new copy of Win10 version 1809 — and all of the files in their Documents, Pictures, Music, Videos and other folders disappeared. I have a series of articles on that topic, arranged chronologically:
Word to the Win10 wise: Don’t click ‘Check for updates’ — Microsoft has unilaterally given itself permission to upgrade your Win10 PC to the brand-new version 1809, if you have the temerity to click “Check for updates.”
How to block the Windows 10 October 2018 Update, version 1809, from installing — the best ways to ensure you install 1809 when you’re ready, even in the face of recent forced updates from Microsoft.
Did you upgrade to Win10 1809 and lose all of your documents and pictures? — If, in spite of my warnings, you upgraded to the latest version of Win10, and you lost all of your Documents, Pictures, Music, Videos or other folders, DON’T DO ANYTHING until you’ve tried this fix.
Microsoft yanks buggy Win10 1809 upgrade, leaving zapped files in its wake — It took four days of complaints about deleted Documents, Photos and other files and late Friday, Microsoft finally pulled the Win10 1809 upgrade. Microsoft has known about the bug for months.
Now that we’re in October’s “C Week” — the week containing the third Tuesday of the month — version 1809 is back in beta testing, there are new patches for those who want to continue with 1809, Microsoft hasn’t come up with a fix for the deleted files, and a whole lot of people are in a whole lot of hurt.
Rule #1: Don’t trust Microsoft.
Rule #2: Don’t click “Check for updates.” In Microsoft-speak, “check for updates” means “install most (but not necessarily all) available updates.”
Rule #3: Refer to Rule #1.
Windows 7 Monthly Rollup patching sequence logic still screwed up
Microsoft vowed that it would fix the bizarre error where the patch installer isn’t smart enough to update itself prior to installing new patches. The primary symptom is an Error 0x8000FFF when installing the Monthly Rollup.
The Servicing Stack Update sequencing problem is so bad, it looks like Microsoft stopped pushing the Monthly Rollup at the end of “B Week.”
We’ve had many conflicting reports about the Monthly Rollup itself, KB 4462923, appearing in the Windows Update list checked (and thus pushed through Windows Update), unchecked and, in some cases, missing entirely. WSUS has been spinning. Patch Lady Susan Bradley puts it succinctly:
Metadata and patch dependency is totally screwed up on Windows 7 platform and because of that the October security updates detection are screwed up.
Bad driver #1 — HP keyboards
I still see reports that Microsoft pushed a buggy update to Win10 version 1809 that caused the WDF_VIOLATION blue screens that brought some systems to their knees. That’s not true. The blue screens are triggered by a bad HP keyboard driver, version 11.0.3.1, which was distributed via Windows Update to Win10 version 1803 and 1809 machines. The buggy driver causes blue screens on the latest builds of 1803 and 1809, although it’s unclear whether the driver triggers BSODs on earlier builds.
Microsoft released a “silver bullet” update that deletes the driver if it’s sitting in your PC’s queue waiting for reboot — which doesn’t do a whole lot of good, especially if you’re stuck in a BSOD loop.
Bad driver #2 — Intel audio
As if the pushed buggy HP keyboard driver weren’t enough, Microsoft also pushed a second bad driver. Some folks running Win10 1709, 1803 or 1809 with Automatic Update turned on discovered that after installing this month’s updates, the sound stopped working, with the message “No Audio Output Device Is Installed.”
Fer heaven’s sake. Why let Windows Update push its buggy drivers onto your machine? There’s a fairly straightforward procedure for telling Windows to stop pushing drivers along with its other dicey updates. At least, the steps are straightforward for those who own Win10 Pro or Education. Home users get to futz with a Registry setting.
Edge can’t find the internet
Speaking of weird Win10 version 1809 behavior… if you’re trying to run Edge (I know, I know) in Win10 version 1809, you may not be able to connect to the internet. UWP (“Metro” Store) apps might not be able to connect, either. This happens even if you have a working internet connection.
The problem? You need to turn on IPv6. Lawrence Abrams on Bleepingcomputer has a step-by-step solution.
Some day this will all go away. The latest version of the dominant Chrome browser doesn’t have that IPv6 problem, and with newfound, fledgling support for Progressive Web Apps, we’re likely looking at the beginning of the end of UWP apps. I, for one, won’t miss them.
JET database patch doesn’t work
Trend Micro’s Zero Day Initiative found a bug in the Jet Database Engine — an ancient (early ‘90s) bug-ridden database precursor to today’s SQL Server. Microsoft didn’t fix it in the ZDI-allotted 120-day fix window, so they published full details. On Day 154, this month’s Patch Tuesday, Microsoft released a fix for what is now known as CVE-2018-8423.
Except Microsoft’s CVE-2018-8423 fix doesn’t fix the whole problem. You can read the gory details on Mitja Kolsek’s 0patch Team blog.
0patch is in the business of providing short-term “micropatches” for bugs that Microsoft doesn’t fix. They initially published a micropatch when Microsoft missed the ZDI deadline. Now they’ve issued a re-patch for the still-unfixed CVE-2018-8423 bug.
I rarely recommend third-party fixes for Microsoft bugs because of the potential for problems. But when Microsoft can’t fix its own bugs, well, it gives me pause.
The bottom line
The past four months have shown, repeatedly, that you’d have to be crazy — or ignorant of the past — to continue applying Windows patches as soon as they’re released. July patching was an unmitigated disaster. After some initial missteps, August fared substantially better. September saw a bunch of “v2” patches that got yanked suddenly, but it all worked out in the end — if you waited long enough. Now October is back to the same-old same-old.
If you’re in charge of protecting state secrets, the pressure’s on to get the patches installed come hell or high water. But for most folks, there’s precious little reason to subject your machine to patching problems right away. That said, Susan Bradley’s Master PatchList remains relatively calm, if you take into consideration the problems explored in this article.
As best I can tell, the biggest threat at this point lies in a resurgence in Equation Editor exploits. That particular Office bug was fixed (and re-fixed) almost a year ago. Yes, you have to install security patches sooner or later.
This month is the first month with an “E Week” — there are five Tuesdays in October. It’ll be the first “E Week” since Microsoft adopted the “A Week” / “B Week” bafflegab. With five Tuesdays now open to official attack, we may be entering a new stage of enlightenment.
Patching problems? Join us on the AskWoody Lounge.

September 2018
As we near the end of patching’s “C Week” (which is to say, the week that contains the third Tuesday of the month), there are no show-stopping bugs in the Windows and Office patches and just a few gotchas. As long as you avoid Microsoft’s patches for Intel’s Meltdown/Spectre bugs, you should be in good shape.
Why a Patch Monday?
On Sept. 17, Microsoft released two very-out-of-band cumulative updates for Windows 10:
- KB 4464218 brings Win10 1803 up to build 17134.286
- KB 4464217 brings Win10 1709 up to build 16299.666
Both of the cumulative updates fix a bug that was introduced in the July 24 cumulative updates. The bug causes Microsoft’s Intune to stutter because it looks in the wrong place for user profiles. The second cumulative update also fixes an obscure VPN bug.
I have no idea why Microsoft released those patches on a Monday. They certainly could’ve waited until Tuesday – the “C Week” Tuesday traditionally being used to fix bugs introduced on Patch Tuesday. Somebody clearly jumped the gun, and folks who patch for a living aren’t really happy about having their chains jerked.
We never did get a cumulative update for Win10 1703. Maybe it wasn’t affected by the July 24 bug. Maybe it’s just too long in the tooth, with support for 1703 due to expire next month.
We also got a way-out-of-band cumulative update for Windows 7 Internet Explorer, KB 4463376, on a “B Week” Friday afternoon.
Second Win10 cumulative updates
If September follows the precedent set this year, we’ll probably see another set of Win10 cumulative updates during “D Week” – next Tuesday, Sept. 25. At the same time, we’ll likely see sets of Monthly Rollup Previews for Win7 and 8.1. Of course, you should ignore them.
More firmware updates
We’re getting more and more firmware updates for Microsoft Surface devices. In the past month, there’ve been firmware/driver patches for the Surface Pro 3, Surface Pro 4, Surface Pro 2017, Surface Book, and even the Surface Studio. It’s an across-the-board makeover (or massive fix) that hasn’t been extended to the Surface Laptop, Book 2, or Go. Yet.
Meanwhile, I’m still hearing complaints about the Surface Pro 4 update.
More Intel microcode fixes
While there has yet to be any credible Meltdown or Spectre threat (Spectre v 1, 1.1, 1.2, 1.3, 1.4, 1.5, 1.6, 1.7, 1.8, 2, 3, 3a, 4 or 5), Microsoft continues to release microcode updates for Intel processors on machines running Win10 version 1709 and 1803. Sometimes the installers try to install the Intel updates on AMD processors, but what the hay.
I go back to Helen Bradley’s statement last month:
Unless you are a nation state, have a key asset in a cloud server, or are running for a government office, I think we are spending way, way more time worrying about this than we should. I still think that attackers will nail me with malware, attack me with phishing, ransomware, etc., etc. way more than someone will use these side channel attacks to gain information from me. Remember that the attacker has to get on your system first and I still think they will use the umpteen other ways to attack me easier than this attack. Also keep in mind that we won’t really have a full fix for this issue for several years. Intel and AMD will need to redesign the chips to ultimately get fixed.
If you’re concerned about such things, do yourself a favor and go to Intel (probably via your PC’s manufacturer) and install the specific patches that you need. And remember that they won’t completely solve the problem.
If you insist on using the Microsoft approach to microcode, abandon all hope, and follow Bradley’s advice here.
The bottom line
July patching was an unmitigated disaster. August fared substantially better. Now, although the month isn’t yet over, September seems to be doing well – if you ignore the Patch Monday gaffe and throw up your hands over Meltdown and Spectre.
In spite of several Chicken Little warnings this month, there haven’t been any widespread attacks that warrant rushing out and installing any of the September patches just yet.
Susan Bradley’s Master PatchList looks relatively serene.
There’s something to look forward to. In October we get an “E Week” – there are five Tuesdays in October. It’ll be the first “E Week” since Microsoft adopted the “A Week” “B Week” bafflegab. What wonders await?
Thx to @sb and @PKCano
Patching problems? Join us on the AskWoody Lounge.

August 2018
So far this month we’ve only seen one cumulative update for each version of Windows 10, and one set of updates (Security only, Monthly Rollup) for Win7 and 8.1. With a few notable exceptions, those patches are going in rather nicely. What a difference a month makes.
We’ve also seen a massive influx of microcode updates for the latest versions of Windows 10, running on Intel processors. Those patches, released on Aug. 20 and 21, have tied many admins up in knots, with conflicting descriptions and iffy rollout sequences.
Big problems for small niches
At this point, I’m seeing complaints about a handful of patches:
- The original SQL Server 2016 SP2 patch, KB 4293807, was so bad Microsoft yanked it — although the yanking took almost a week. It’s since been replaced by KB 4458621, which appears to solve the problem.
- The Visual Studio 2015 Update 3 patch, KB 4456688, has gone through two versions — released Aug. 14, pulled, then re-released Aug. 18 — and the re-released version still has problems. There’s a hotfix available from the KB article, but you’d be well advised to avoid it.
- Outlook guru Diane Poremsky notes on Slipstick that the version of Outlook in the July Office 365 Click-to-Run won’t allow you to start Outlook if it’s already running. “Only one version of Outlook can run at a time” — even if the “other version” is, in fact, the same version.
- The bug in the Win10 1803 upgrade that resets TLS 1.2 settings persists, but there’s an out-of-the-blue patch KB 4458116 that fixes the problem for Intuit QuickBooks Desktop.
- The Win10 1803 cumulative update has an acknowledged bug in the way the Edge browser interacts with Application Guard. Since about two of you folks use that combination, I don’t consider it a big deal. The solution, should you encounter the bug, is to uninstall the August cumulative update, manually install the July cumulative update, and then re-install the August cumulative update — thus adding a new dimension to the term “cumulative.”
- The Win7 Monthly Rollup has an old acknowledged bug about “missing file (oem.inf).” Although Microsoft hasn’t bothered to give us any details, it looks like that’s mostly a problem with VMware.
The rest of the slate looks remarkably clean. Haven’t seen that in a long while.
Second Win10 cumulative updates
If August follows the precedent set this year, we’ll probably see another set of Win10 cumulative updates next Tuesday, “dee” Tuesday, Aug. 28. At the same time we’ll likely see sets of Monthly Rollup Previews for Win7 and 8.1. Of course, you should ignore them.
More firmware updates
In the past couple of months, Microsoft has released massive firmware/driver updates for almost all of the latest Surface devices.
At this point, I’m still seeing problems with the July 26 set of fixes for the Surface Pro 4, which have been blamed for touchscreens that don’t touch, pens that don’t pen, batteries that go out to lunch, and all sorts of boorish behavior.
Of course, there have been no solutions.
More Intel microcode fixes
Microsoft released oodles and gobs (that’s a technical term) of microcode fixes for Win10 1803 and 1709, passing along Intel’s fixes for the Meltdown and Spectre V1, 2, 3, and 4 security holes. People have been pulling their hair out by the roots. Susan Bradley has a great birds-eye view:
Unless you are a nation state, have a key asset in a cloud server, or are running for a government office, I think we are spending way way more time worrying about this than we should. I still think that attackers will nail me with malware, attack me with phishing, ransomware, etc etc, way more than someone will use these side channel attacks to gain information from me. Remember that the attacker has to get on your system first and I still think they will use the umpteen other ways to attack me easier than this attack. Also keep in mind that we won’t really have a full fix for this issue for several years. Intel and AMD will need to redesign the chips to ultimately get fixed.
If you’re concerned about such things, do yourself a favor and go to Intel (probably via your PC’s manufacturer) and install the specific patches that you need. And remember that they won’t completely solve the problem.
If you insist on using the Microsoft approach to microcode, abandon all hope, and follow Bradley’s advice here. No matter which approach you take, make sure that you don’t publish any before-and-after performance data, which Intel has unilaterally declared verboten. See Bruce Perens’s article Intel Publishes Microcode Security Patches, No Benchmarking Or Comparison Allowed!
The bottom line
After all the problems last month, it’s a relief to have only a handful of glaring problems this month. I suggest you wait another day or two before installing the August patches.
The only significant breach of a recently patched security hole that I’ve found involves North Korea, Internet Explorer 11, VBScript, and China. That’s probably not a combination that’ll keep you up at night — and there’s little reason to rush into installing the August patches unless you’re in a Chinese organization that’s run afoul of the North Korean government.
I continue to recommend that you keep 1803 off your Win10 machines. No reason to go there until you’re forced. Susan Bradley’s Master PatchList has details for individual patches.
Thx to @sb, @abbodi86 and @PKCano
Patching problems? Join us on the AskWoody Lounge.

July 2018
If you ever wondered why people — and organizations — are taking longer and longer to willfully install patches, take a look at what happened this month. After a disastrous start, Windows 10 patches seem to be OK, but .NET and Server patches still stink.
For most of the year, we’ve seen two big cumulative updates every month for each of the supported Win10 versions. This month, so far, we’ve had three. Microsoft’s claim that it will install the Win7 and Win8.1 Monthly Rollups defies logic. The .NET patches are in such bad shape that the .NET devs have thrown in the towel. And here we sit not knowing exactly which way is up.
Three Win10 cumulative updates for each version in July
On Patch Tuesday, July 10, as usual, Microsoft rolled out cumulative updates for all of the supported versions of Windows 10. Almost immediately we heard screams of pain as four big bugs, later officially acknowledged, hit the fan. Six days later, Microsoft released a second set of cumulative updates, again for all versions of Win10. Those updates were specifically designed to fix the bugs introduced by the original updates. The build numbers in the Knowledge Base articles didn’t match the build numbers that people actually installed but, well, that’s Microsoft.
A week after that, on July 24, Microsoft released a third set of cumulative updates, again for all versions of Win10. At least, I think they were released on July 24. The dates in the Update Catalog and on the files themselves don’t line up. But we definitely have three cumulative updates for every version, so far this month. Beefy bug fixes.
It’s still too early to tell whether the third round of patches is viable. We’ve only had them for two days.
Win7 and Win8.1 get their fair share
As usual, Win7/Server 2008 R2 and Win8.1/Server 2012 R2 both received a single Monthly Rollup (along with a Security-only patch) on July 10. Both contained three of the four bugs introduced in the Win10 Patch Tuesday security patches, including the Stop 0xD1 bug. Microsoft released manual download-only fixes for the bugs for Win7 and 8.1 on July 16.
Then, on July 18, Microsoft released Monthly Rollup Previews for both Win7/Server 2008 R2 and Win8.1/Server 2012 R2, which apparently contain the manual download-only fixes. Like all good Monthly Rollup Previews, they’re released as Optional patches, so you have to specifically check them in order to get them — a procedure I never recommend.
Except, golly gee, on July 24, Microsoft announced:
The Windows Update classification for the following update packages has been changed from Optional to Recommended: KB 4338821 (Preview Monthly Rollup for Win7/Server 2008 R2), KB 4338816 (Preview Monthly Rollup for Server 2012), KB 4338831 (Preview Monthly Rollup for Win 8.1/Server 2012 R2). These packages will be installed automatically if the operating system is configured to receive automatic updates.
It’s a setting that, as best I know, is completely unprecedented in the history of Monthly Rollup Previews. Hard to imagine a Preview — by definition, a fix that isn’t ready for prime time — that’s pushed onto all machines. As of today, I haven’t seen those Previews pushed onto Win7 or 8.1 machines with automatic update enabled. It appears as if the announcement only applies to Servers — but that’s just conjecture at this point.
A poster named Francis says:
Since only the server preview rollups are updated in the catalog, I think Microsoft is not telling us the whole truth. Probably only the server preview rollups will be installed automatically if the operating system is configured to receive automatic updates AND the option to receive recommended updates is set in the Windows Update client settings
That corresponds to what I’ve seen. (If you aren’t confused, you haven’t been following along.)
.NET’s nuts
The .NET patches released on Patch Tuesday were bad. They were so bad that Microsoft itself has disavowed any knowledge of their actions. On July 20 — 10 days late and $10 short — ‘Softie Rich Lander posted on the official .NET blog:
The July 2018 Security and Quality Rollup updates for .NET Framework was released earlier this month. We have received multiple customer reports of applications that fail to start or don’t run correctly after installing the July 2018 update… We have stopped distributing the .NET Framework July 2018 updates on Windows Update and are actively working on fixing and re-shipping this month’s updates. If you installed the July 2018 update and have not yet seen any negative behavior, we recommend that you leave your systems as-is but closely monitor them and ensure that you apply upcoming .NET Framework updates.
Since that time, we’ve seen some fancy footwork to stop the disease from spreading. It now appears as if the patches are either not available or, if available through Windows Update, aren’t checked for automatic installation. The official apology hasn’t been updated with any word of a fix.
Office
Microsoft pulled the bad Office 2016 non-security patch KB 4018385 on July 12, nine days after its release on the first Tuesday of the month. As I explained at the time:
What we’re seeing is a non-security patch for a bug in three-month-old security patch that crashed Office … and the new non-security patch also crashes Office. That’s progress.
No word on a fix.
Massive firmware updates
If you have a Surface Pro 4 or a Surface Laptop, Microsoft has released dozens of firmware/driver fixes for your machine. Some of the “new” drivers are a year or more old. I hold out some hope that the fixes will cure some of the outstanding problems we’ve seen with the Surface Pro 4, especially with flakey keyboards and super slow write speeds.
More Intel microcode fixes
On July 24, we saw another bunch of Intel microcode fixes, specifically targeting the Spectre v2 vulnerability. There are separate patches for Win10 version 1803 and 1709— and no new updates, so far at least, for earlier versions. Microsoft’s summary post for the microcode KBs contains links.
The bottom line
Just about every aspect of patching this month revealed significant screw-ups. If your machine is set to automatically install new updates as soon as they’re released, you were likely stung at least once. Add to that the stunning lack of transparency and obvious documentation inconsistencies, and you have one of the worst patching months in recent memory. Let’s hope it doesn’t get worse.
I continue to recommend that you keep 1803 off your Win10 machines. The volume (and quality!) of patches doesn’t bode well. Of course, the other Win10 versions weren’t much better this month. Susan Bradley’s Master PatchList has details for individual patches.
Thx to @sb, @abbodi86 and @PKCano
Problems with patches? Yeah, join the club. Visit us on the AskWoody Lounge.

June 2018
Microsoft’s patches in June took on some unexpected twists.
Windows 7 owners with older, 2002-era Pentium III machines got their patching privileges revoked without warning or explanation (and a documentation cover-up to boot), but there’s little sympathy in the blogosphere for elderly PCs.
Win10 1803 was declared fully fit for business, a pronouncement that was followed weeks later by fixes for a few glaring, acknowledged bugs — and stony silence for other known problems.
We’re continuing the two-big-cumulative-updates-a-month pace for all supported versions of Windows 10. The second cumulative update frequently fixes bugs introduced by the first cumulative update.
Win10 version 1803 still rough around the edges
Microsoft may think that Win10 (1803) is ready for widespread deployment, but there are a few folks who would take issue with that stance.
Yesterday, Microsoft finally released a fix for two big bugs that have dogged Win10 1803 since its inception. In theory, patch KB 4284848 fixes these acknowledged bugs:
- Some users running Windows 10 version 1803 may receive the error “An invalid argument was supplied” when accessing files or running programs from a shared folder using the SMBv1 protocol.
- Microsoft Edge may stop working when it initializes the download of a font from a malformed (not RFC compliant) URL.
In practice, life isn’t so simple. WSUS (the Windows Update Server software) isn’t “seeing” KB 4284848, as of late Wednesday afternoon – which may be a good thing.
Along with the second cumulative update this month, there are additional releases to fix the Servicing Stack, and a new “Compatibility update” that, per the documentation, is designed to make it easier to upgrade Win10 1803 Enterprise to Win10 1803 Enterprise (not a typo).
Old problems remain in abundance. There are many reports of munged Intel NICs and VLAN problems after installing 1803. Josh Mayfield (whom you may recall from GWX days) reports that you’re forced to set up a PIN during fresh installs. The ancient problem with restore partitions getting assigned drive letters on install remains. Chrome continues its indigestion with 1803, although Microsoft claims the latest patch cures all ills. None of this is acknowledged anywhere I can see.
One problem that has been acknowledged – but only by a Microsoft Agent on an Answers Forum post – says that installing 1803 can clobber your peer-to-peer network. That certainly matches my experience. With earlier versions of Win10, I’d fire up the Homegroup Troubleshooter and that usually solved the problem. Unfortunately, Microsoft discontinued Homegroups in version 1803.
On the positive side, WindowsCentral’s Zac Bowden reports that yesterday’s 1803 patch fixes lagging/stuttering issues on his Surface Book 2 – a problem that’s neither acknowledged, nor described in the list of fixes.
If you think Win10 1803 is ready for prime time, you’re welcome to give it a try.
Multiple patches for supported versions of Win10
- Version 1803 saw patches on June 5 (for a QuickBooks bug), June 12 (which introduced the Edge font bug) and June 26 (see the above);
- Version 1709 was patched on June 12 and June 21. Now up to build 16299.522, it appears to be relatively stable. I haven’t upgraded to it, but will try to find time over the July 4 holiday;
- Version 1703 was also patched on June 12 and June 21.
Win7 continues to draw attention
We still have an acknowledged bug, introduced by the Win7 patches in March:
There is an issue with Windows and a third-party software that is related to a missing file (oem.inf). Because of this issue, after you apply this update, the network interface controller will stop working.
As noted by an anonymous poster last month:
It’s not only KB4103718 (May 8, 2018—KB4103718 (Monthly Rollup)) that has been updated with the missing oem.inf issue. The problem seems to date back to the March 2018 Security-Only and Monthly Rollup updates.
All of the following knowledge base articles were updated with similar warnings on May 25, 2018:
- KB4088875: March 13, 2018—KB4088875 (Monthly Rollup);
- KB4088878: March 13, 2018—KB4088878 (Security-only update);
- KB4088881: March 23, 2018—KB4088881 (Preview of Monthly Rollup);
- KB4093118: April 10, 2018—KB4093118 (Monthly Rollup);
- KB4093113: April 17, 2018—KB4093113 (Preview of Monthly Rollup);
- KB4103718: May 8, 2018—KB4103718 (Monthly Rollup);
- KB4103713: May 17, 2018—KB4103713 (Preview of Monthly Rollup).
Microsoft won’t say which vendor(s) and/or which network card(s) are getting cracked by the patch. There’s speculation that the bad card is from Intel, but we really don’t know. Your only real recourse is to create a full backup prior to applying this month’s patches, or to accept the possibility that you’ll have to manually re-install them. Susan Bradley has detailed instructions.
The bottom line
Windows 8.1 continues to hold the title as the most stable version of Windows. Hard to believe.
This month’s Office patches seem to be working, although there are many individual problems listed in the Office Fixes or Workarounds list.
Stay tuned.
Thx to @sb and @PKCano
Struggling with other problems? Join us on the AskWoody Lounge.

May 2018
Once more we have a monthly Windows/Office patch scorecard that needs a guidebook. Or two. And we just got a handful of buried warnings about problems in old patches, plus a brand new way to fry your network interface card.
Thus continues the tradition of two cumulative updates per month for all of the supported Windows 10 versions – that’s eight cumulative updates in total – in addition to bobs and weaves and a very long list of acknowledged bugs introduced by recent security patches in Windows 7.
Conflicts with Remote Desktop
The strange behavior of the CredSSP update – where the Patch Tuesday fixes for all versions of Windows seemed to break Remote Desktop Protocol with a strange error message: “This could be due to CredSSP encryption oracle remediation” has been resolved.
Patch Lady Susan Bradley notes (about all versions of Windows and Remote access):
Be aware — if you are seeing RDP issues post patch Tuesday, the underlying issue is that there is a mismatch between patch levels. The updates for the RDP/credssp came out in March and slowly Microsoft has been adjusting the mandate of the update. In May, the full “you must have a patch on both ends” kicked in. So if you haven’t updated your servers, but your workstations got patched you’ll see the CredSSP error message.
While there is a registry key to allow patched systems to connect to unpatched systems, it’s much wiser to patch your servers. Note that if you held off patching your servers because of the networking side effects/bugs, those were patched in the April.
That’s how you solve a CredSSP encryption oracle remediation problem. Obviously. Ahem.
Win10 version 1803 approaches ‘usable’ status
The unpaid beta testers for Windows 10 April 2018 Update (better known as version 1803) earned their salaries this month, with triple overtime. The embarrassing bug in the original 1803 (released April 30) bricked any computer with an Intel SSD6 drive– including some of Microsoft’s own Surface Pro 2017 computers.
A similar, but different, bug dogged PCs with Toshiba SSDs. The bug persisted in the first cumulative update for Win10 1803, but was finally put to sleep last week with the second cumulative update, which finally made 1803 installable on most common PCs.
Installable, mind you. Not stable. For example, there are many reports of 1803 driving batteries nuts. I’ve seen discussions of the Surface Studio mouse and keyboard lock-ups after installing 1803, but no solutions – and there may be a similar problem with earlier versions of Win10. The Reddit 1803 megathread is up to 1,800 comments– not all of which are glowing reports of happiness in 1803 land.
The greatest malfeasance, in my opinion, is Microsoft’s continuing push to install Win10 1803 on machines that are set to specifically avoid it. Win10 1709 Home users get hit the worst. AskWoody reader IG puts it this way:
I have found that (at least in my situation with my Lenovo and HP laptops) the best way to avoid the latest feature update for Windows 10 Home, is to not only set your connection to metered, but to also install the Windows update tool, (wushowhide). Despite being on a metered connection, the 1803 upgrade eventually showed up ‘available to download’ this week. Along with the 1803 update a 1709 update also showed up but required a ‘retry.’ Using the update tool I hid the 1803 upgrade, and the next time Windows automatically checked for updates, it was no longer available to download. I was also able to retry and install the current 1709 update without any issues.
I continue to strongly recommend that you not hobnob with the cannon fodder and wait for Microsoft to show some restraint. Or at least some fixes. My original recommendations for blocking 1803 still work, but you have to use all of them, altogether, all the time.
Multiple patches for all versions of Windows 10
If you’re using Windows 10, you saw big multiple patches in April:
- Version 1709– the Fall Creators Update — the initial Patch Tuesday patch, KB 4103727, had the usual round of complaints about failure to install, random bluescreens and the like. The second cumulative update, KB 4103714, seems to be stable.
- Version 1703— the Creators Update — got its first cumulative update, KB 4103731, on Patch Tuesday, and a second huge cumulative update, KB 4103722a week later.
- Version 1607— the Anniversary Update (only for Win10 1607 Enterprise and Education) also got two cumulative updates.
Version 1703 remains stable (although there’s a whole lotta patchin’ goin’ on) and 1709 has finally found some maturity. About a month too late.
The ongoing Windows 7/Server 2008 R2 saga
Windows 7 continues to be singled out for back-breaking patch-induced bugs. Microsoft officially acknowledges both of these bugsin the latest Win7/Server 2008 R2 patch, KB 4103718:
- A stop error occurs on computers that don’t support Streaming Single Instructions Multiple Data (SIMD) Extensions 2 (SSE2). A long-standing problem, still with no solution.
- There is an issue with Windows and a third-party software that is related to a missing file (oem.inf). Because of this issue, after you apply this update, the network interface controller will stop working.That announcement appeared out of the blue on May 26. There’s no indication which “third-party software” is at fault – or who should avoid the patch – but such are the vagaries of Windows patching. There’s an in-depth discussion going on the AskWoody Lounge.
As it turns out, the missing oem.inf issue dates back to the March patches. According to an anonymous poster:
It’s not only KB4103718 (May 8, 2018—KB4103718 (Monthly Rollup)) that has been updated last Friday with the missing oem.inf issue. The problem seems to date back to the March 2018 Security-Only and Monthly Rollup updates.
All of the following knowledge base articles were updated with similar warnings on May 25:
- KB4088875: March 13, 2018—KB4088875 (Monthly Rollup)
- KB4088878: March 13, 2018—KB4088878 (Security-only update)
- KB4088881: March 23, 2018—KB4088881 (Preview of Monthly Rollup)
- KB4093118: April 10, 2018—KB4093118 (Monthly Rollup)
- KB4093113: April 17, 2018—KB4093113 (Preview of Monthly Rollup)
- KB4103718: May 8, 2018—KB4103718 (Monthly Rollup)
- KB4103713: May 17, 2018—KB4103713 (Preview of Monthly Rollup)
We’re stuck between a rock and a hard place. Microsoft won’t say which vendor(s) and/or which network card(s) are getting cracked by the patch. There’s speculation that the bad card is from Intel, but we really don’t know. Your only real recourse is to create a full backup prior to applying this month’s patches, or to accept the possibility that you’ll have to manually re-install them. Susan Bradley has detailed instructions.
That same anonymous poster goes on to advise:
Also, there is a new, never heard before issue with the Win7 March 2018 Security-only update (KB4088878):
Symptom: A 32-bit (x86) computer won’t boot or keeps restarting after applying this security update.
Workaround: Before applying this security update and subsequent security updates, uninstall the following external drivers until they are fixed by the vendor that owns them:
- HASP Kernel Device Driver (a.k.a. Haspnt.sys)
- Hard Lock Key Drivers (a.k.a. hardlock.sys)
It’s not at all clear if that warning is only for 32-bit computers.
If you want to see something scary, take a look at the current version of the “Known issues” list for the Win7 Security-only patch, KB 4088878. I count nine acknowledged bugs introduced in that one Security-only patch.
Windows 8.1 / Server 2012 R2 continues to look good. By any objective measure, 8.1 is Microsoft’s most stable version of Windows. By a long shot.
Office patches keep rolling along
I don’t know of any pressing problems with this month’s Office patches. Susan Bradley’s Master Patchwatch List gives them a clean bill of health, and @PKCano’s list of non-security patches looks clean, too, although there are a number of acknowledged problems listed on the official Fixes pages.
Stay tuned.
Thx to @PKCano, @sb and the Mentats-in-Training.
Join us for the latest on the AskWoody Lounge

April 2018
People think I’m joking when I refer to bug fixing as Microsoft’s next billion-dollar business. I’m not. This month woefully demonstrated why patching Windows has become much bigger – and more critical – than developing new versions. Microsoft’s hell-bent move to bring out new versions of Windows twice a year “as a service” makes things worse, but quality control problems dog patches to every version of Windows. Except, arguably, Windows 8.1.
In April, we’ve seen a return to two massive cumulative updates per month for all supported versions of Windows 10. The second cumulative update, with luck, fixes the bugs in the first cumulative update. Windows 7 turned into a fiery pit when it was discovered in late March that every patch to Win7 (and Server 2008R2) pushed out this year enables the Total Meltdown bug. Fortunately, by April 23, we finally saw some stability return to the process.
Multiple patches for all versions of Windows 10
If you’re using Windows 10, you saw big multiple patches in April:
- Version 1709 – the Fall Creators Update – the initial Patch Tuesday patch, KB 4093112, had the usual round of complaints about failure to install, random bluescreens and the like. It took a few days for info to surface about changes in pen behavior, which resulted in pen movements in major program (such as Adobe Photoshop) dragging the canvas. Turns out, beta testers in Win10 1803 liked the new feature so much that Microsoft decided to drop it into Win10 1709, without warning or (apparently) testing. The second cumulative update, KB 4093105, which went out on the night of April 23, fixed the aberrant pen behavior and promises to not re-install Candy Crush Soda Saga on version upgrades. We’ll see.
- Version 1703– the Creators Update – got its first cumulative update, KB 4093107, on Patch Tuesday, and a second huge cumulative update, KB 4093117, a week later.
- Version 1607– the Anniversary Update – received its first cumulative update, KB 4093119, on Patch Tuesday, April 10, the scheduled End of Life date for Win10 1607 Pro and Home. Version 1607 received a second monthly cumulative update a week later, KB 4093120 – but only for Win10 1607 Enterprise and Education.
There was yet another update for Win10 1709, 1703 and 1607 released on April 24. KB 4078407 is supposed to be the software side of the fix for Spectre variant 2. It has to be combined with microcode updates to work and it’s only available by download from the Microsoft Update Catalog. We’re following its progress closely on AskWoody.
Of course we’re all waiting for Win10 version 1803 to appear. There’s still no word on when that might happen, or what it’ll be called. (Inveterate leaker Faikee points to a Chinese-language letter to dealers saying it’ll be released May 9.)
The ongoing Windows 7/Server 2008 R2 saga
Two words: Total Meltdown. We now know that every 64-bit Windows 7 and Server 2008 R2 patch released this year, up to March 29, contained a bug that opens a security hole dubbed Total Meltdown. Microsoft spent most of April in Keystone Kops patching mode, where one patch after another introduced more and different bugs, and new patches replaced older patches at a truly mind-boggling rate.
As the month’s now winding down, there’s a bit of good news. As of Monday night, it appears as if the (re-re-re-released) April Monthly Rollup, KB 4093118, has lost its boorish tendency to re-re-re-install itself. That means, to a first approximation, Win7 and Server 2008 R2 users can install one patch and wipe out the Total Meltdown threat.
All of this is unfolding as a real, live working Total Meltdown exploit is in the works. Of course, Meltdown (as opposed to Total Meltdown) and Spectre have absolutely no known exploits. None.
Those who insist on installing Security-only patches, eschewing the Monthly Rollups, face an unanswered question: If you’ve installed the earlier, buggy version of the NIC and static-IP defending patch KB 4099950, do you need to uninstall it before proceeding? The official documents are mum. We’re also following that question on AskWoody.
There continue to be reports from people who installed this month’s updates and had to struggle with recovering their user profile. Microsoft acknowledged the problem, of and on, and even posted a Knowledge Base article with workaround steps.
Office patches keep rolling along
There don’t appear to be any pressing problems with this month’s Office patches. Susan Bradley’s Master Patchwatch List gives them a clean bill of health, although there are a number of acknowledged problems listed on the official Fixes pages.
In short, it looks like Microsoft has fixed the problems that it introduced earlier in the month. The fixes to security holes Microsoft installed with this year’s Win7 and Server 2008 R2 are almost ready. We just have a couple of niggling problems before it’s time to get the April patches installed.
Stay tuned.
Join us for the latest on the AskWoody Lounge.

March 2018
An enormous number of patches spewed out of Microsoft this month, with two ponderous cumulative updates for each version of Windows 10, a third “bonus” bug fix for Win10 Fall Creators Update (version 1709), and a just-described bug in Windows 7 that’ll leave you begging for a Win7 patch that works.
There’s also a bit of comic relief with a patch for Win10 1709, KB 4094276, that “makes improvements to ease the upgrade experience to Windows 10 Version 1709.” That’s a wonderful example of a self-referential fix.
Multiple patches for all versions of Win10
If you’re running Win10, you saw multiple big patches in March:
- Version 1709 – the Fall Creators Update — saw an emergency fix, KB 4090913, on March 5, which fixed a bug introduced in the February round of patches (and rendered some machines unbootable); a “regular” Patch Tuesday patch, KB 4088776 on March 13; and a big out-of-out-of-band patch KB 4089848 on Thursday, March 22. The biggest complaints involve the usual chorus of patches that refuse to install, and driver problems. Reports of INACCESSIBLE_BOOT_DEVICE bluescreens are tapering off.
- Version 1703 – the Creators Update — also got a bug fix, KB 4092077, on March 8, which fixed an earlier patch that crashed the user interface. 1703 also saw two big cumulative updates, KB 4088782 on Patch Tuesday and KB 4088891 on the really-out-of-band patch date: March 22.
- Version 1607 and Server 2016 – the Anniversary Update — also got two big cumulative updates, KB 4088787 on Patch Tuesday and a big booster KB 4088889 on the way-out-of-band Thursday. Just a reminder that, unless you’re using 1607 Enterprise or Education, your version runs out of support (as it were) on April 10.
March also presented us with the third, uh, opportunity to get forcibly pushed from Win10 1703 to 1709 – even on systems specifically set to block the upgrade.
At various points in March, users also saw updates to the Servicing Stacks for all three Win10 versions. Apparently, they resolved the race condition-related bugs that left USB drivers, in particular, dead in the water. If you’re installing the Win10 cumulative updates manually, make sure you install the respective Servicing Stack Update before you install the cumulative update.
A little bit of Word poison
Microsoft released a buggy Office 2016 security patch, KB 4011730, which left Word 2016 in such a bad state that it couldn’t save – or sometimes even open – files. We discovered later that if you install the March non-security patch for Office 2016, KB 4018295, Word 2016 suddenly got its mojo back.
Microsoft is researching this problem and will post more information in this article when the information becomes available.
Of course.
Windows 7: To patch or not to patch
All of which serves as prelude to the massive cluster-cluck that engulfed Windows 7 in March.
Win7 and Server 2018 R2 received a relatively modest Monthly Rollup, KB 4088875, and the obligatory Security-only, manually installed patch, KB 4088878, on Patch Tuesday, March 13. Almost immediately, we started seeing reports of networking problems with the patches, and some bluescreens. Shortly afterward, two specific problems with broken manual IP addresses and disabled Network Interface Cards (vNICs) bubbled up.
At first, Microsoft didn’t acknowledge the bugs; instead it stopped the Monthly Rollup from installing automatically (for those of you naïve enough to have Automatic Update enabled). As days passed, Microsoft finally published a detailed list of “known issues in this update.”
At this point, some users report that KB 4088875 appears in Windows Update as an “important” update that isn’t checked, and which doesn’t install by default. But there’s more. Others say it’s off the Windows Update list, but apparently it’s still being pushed out via WSUS servers.
Microsoft released, then re-released, an ad-hoc VBScript program that was supposed to fix the problem. But the script has raised all sorts of questions. Poster MrBrian reports that the script was changed on March 27, with no notification. Poster abbodi86 has an improved version posted on Pastebin.
But there’s more to the story.
Yesterday, security researcher UlfFrisk posted a report about a new big security hole in Windows 7. Bucking the recent trend, UlfFrisk avoided a massive publicity campaign, replete with pre-defined exploit names and cute logos, but his “Total Meltdown” exploit almost defies imagination. As Günter Born says:
Microsoft’s Meltdown updates shipped in January 2018 and February for Windows 7 (and Server 2008 R2) intended to mitigate the Meltdown vulnerability rip open a huge security hole. This allows any process under Windows 7 to read and write to any memory area without exploits…
Unfortunately, an accident happened in the January 2018 [Win7] patch (and also in February 2018 patch) when… if a (user) process has read/write access to the page tables, it is [trivial] to access the entire physical memory.
This isn’t “Sky is Falling” time. But it means that if you’re running Win7 64-bit or 2008R2 64-bit on an Intel machine, and you installed either the January or February Win7 Monthly Rollups or Security-only patches, Microsoft flipped the wrong bit, and you now have a big hole in your machine that will let any running program look at and change everything in memory. Note that you have to be running a destructive program in the first place – Total Meltdown doesn’t make it easier to run bad programs – but the security hole appears to be massive, by any estimation.
The problem is solved by the March Win7 patches, but…, well, you can see what a mess those have become.
Thx to @PKCano, @sb, @MrBrian, @abbodi86.
Having problems with this month’s patches? Join us on the AskWoody Lounge.

February 2018
The January 2018 Microsoft patching cycle may have been the worst and most invasive set of Microsoft releases in recent memory. The February updates, by marked contrast, only clobber a limited number of machines. How many? We don’t know — and Microsoft isn’t saying.
Bad Win10 Fall Creators Update patch
What we do know for sure is that the buggy Win10 Fall Creators Update cumulative update KB 4074588 tossed many PCs into bluescreen hell and disabled USB devices of various stripes. That’s quite an accomplishment for version 1709 which, according to AdDuplex, is now said to run on 85% of all Windows 10 machines. To look at it a different way, Microsoft blew the cumulative update to the most-used version (1709) of the most-used Windows (Win10 now surpasses Win7).
It took Microsoft 10 days to admit to the bugs. Finally, on Feb. 23, it appended these items to the KB article. There’s no additional notification, of course – if you figured out what caused your problem, and figured the KB article would have some information, here’s what you eventually got:
After installing this update, some USB devices and onboard devices, such as a built-in laptop camera, keyboard or mouse, may stop working. This may occur when the windows update servicing stack incorrectly skips installing the newer version of some critical drivers in the cumulative update and uninstalls the currently active drivers during maintenance.
Microsoft is working on a resolution and will provide an update in an upcoming release. Workaround steps are available in KB4091240.
After installing this update, some devices may fail to boot with INACCESSIBLE_BOOT_DEVICE.
This issue occurs when the windows update servicing stack incorrectly skips installing the newer version of some critical drivers in the cumulative update and uninstalls the currently active drivers during maintenance.
Microsoft is working on a resolution and will provide an update in an upcoming release. Workaround steps are available in KB4075150.
As you might imagine, both manual workarounds require an advanced degree in Microsoft Patch bugology.
More fixes for Win10
Late last week, on Feb. 22, we saw new cumulative updates for Win10 1703 (the Creators Update) and 1607 (the Anniversary Update). Both were the second cumulative updates this month for the respective versions. What we didn’t see was a second cumulative update for 1709. Although there’s been no official word, I think it’s likely that the 1709 second cumulative update was held because of problems with the patch – and I’d be willing to bet my eye teeth that the problems have to do with the bluescreen and USB issues.
We’ll reportedly see the second February cumulative update for Win10 1709 on Tuesday.
In spite of its 85% lead, I’m still not moving from the Creators Update (1703) to the Fall Creators Update (1709), and suggest that you resist, too, until Microsoft has shown it can reliably keep 1709 alive and well.
Or, you can join the swelling ranks of the unpaid beta testers. Millions already have.
Win7 reboot to black
The other major problem this month is with the Windows 7 Monthly Rollups. Many users report that, after installing a Win7 Monthly Rollup, their systems no longer restart properly: Clicking through the Start / Restart sequence lands these PCs on a black screen, with the computer and fans still running. The only way to get their system working again involves a nearly-hard-restart, typically by punching the restart button on the front of a desktop or pushing and holding the power button on a laptop.
It’s not clear whether the problem affects Intel (Sandy Bridge? Ivy Bridge?) or AMD processors, or all of them – and maybe more.
It’s also not clear whether the problem started with January’s Monthly Rollup, or if it just emerged in February. I have a report that the problem didn’t occur after the January Monthly Rollup. But then again I have a report that it did.
Ben1907 on the Microsoft Answers forum has had some success, without uninstalling the patch:
I checked my C-State settings on my ASUS P8P67-M motherboard and they were set to the default settings in the ASUS manual.
- C1E [enabled]
- C3 Report [disabled]
- C6 Report [enabled]
Playing around by setting different combinations, I found the C1E enabled/disabled did not matter, so left it enabled. However, by setting C6 Report to DISABLED, I have now been able to perform a normal restart/reboot from Windows 7. Tried at least half dozen times and all good so far.
Thanks for investigating this and putting me on the right path to correct this issue. Microsoft has caused me so many lost hours of troubleshooting problems they inject with updates you wonder if they have any quality control.
Two NET Previews bite the dust
On Thursday, Microsoft released a gaggle (or perhaps it’s a murder?) of Preview patches at the the same time it released a bunch of optional Windows patches (see Susan Bradley’s list). Two of those Previews were doomed from the get-go:
KB 4074805 – the February 2018 Preview of Quality Rollups for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, and 4.7.1 for Windows 7 SP1 and Server 2008 R2 SP1 – set Quickbooks Enterprise 2017 crashing at startup
KB 4073701 – the February 2018 Preview of Quality Rollup for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, and 4.7.1 for Windows 7 SP1 and Server 2008 R2 SP1 and for .NET Framework 4.6 on Server 2008 SP2 has also been implicated.
Intuit, the owner of Quickbooks, has some choice comments about the bug:
Consult your IT professional to remove patch KB4074805. If you are still experiencing the issue, you may have to uninstall patch KB 4073701 as well.
Microsoft apparently pulled the patches, although the KB articles fail to mention the bug – or the fact that KB 4074805 and KB 4073701 are no longer available.
There’s a reason why you should never install a Preview.
What are we fighting for?
Every month, I look back and try to figure out whether the damage caused by Microsoft’s patches outweighs the undeniable benefit of more-secure systems. This month’s Anubis weigh-in shows, once again, that lots of people are getting clobbered – and there’s very little benefit to the February patches at this point.
One important point for the patching-inclined: As I made clear shortly after this month’s Patch Tuesday, there’s a very real threat for folks with the installed (“MSI”) version of Office:
If you’re using Outlook 2007, 2010, 2013, or 2016 – the installed versions – you’ll be vulnerable to drive-by email attacks by previewing a bad email or just by downloading a rigged email. No, you don’t need to open the email. It just infects.
As best I can tell, there aren’t any known exploits. But anyone with installed versions of Outlook should seriously consider installing the patch for Outlook 2007 (KB 4011200, four months beyond its end-of-support date), Outlook 2010 (KB 4011711), Outlook 2013 (KB 4011697), and/or Outlook 2016 (KB 4011682).
If you use Office 2016 Click-to-Run, the patches will appear the next time CtR updates itself, with version 1708 build 8431.2215 in the Semi-Annual Channel and 1705 build 8201.2258 in the Deferred Channel.
I’m also seeing reports that last month’s Outlook 2010 patch, KB 4011273, is making Contacts View in Microsoft’s Dynamics CRM 2011 fail. This isn’t the first report of problems with KB 4011273.
Other than that, and a disclosed (but not particularly infectious) exploit in Edge (CVE-2018-0771), and ongoing, perennial threats through Flash (if you use Flash, you have nobody to blame but yourself), there are no immediate threats from the exploits fixed this month that I know about. In particular, there are no known attacks that use Meltdown or Spectre. None.
What to do now
If you’re motivated to sift through individual patches, patching guru Susan Bradley has watchlists for the February Patch Tuesday patches, the February Optional Updates, and last week’s Feb. 22 releases.
If you’d rather wait until the coast is clear, and prefer not to sweat the small stuff, make sure you have Outlook fixed if you need to then go get a cup of coffee. Check back again in a few days, to see whether Microsoft has finally given us a version of Win10 1709 that actually, you know, works – and if there are any further problems with the second cumulative updates for 1703 and 1611. Don’t expect a fix for the Win7 boot to black screen problem.
Have a problem? Don’t we all. Join us on the AskWoody Lounge.

January 2018
On the heels of a relatively benevolent December Patch Tuesday, the stream of patches pouring out of Microsoft (and Intel!) in January reached epic proportions. To be fair, it looks as if Microsoft got drawn into releasing its Meltdown/Spectre barrage early – on Jan. 3 – but they were so buggy they were withdrawn for AMD processors on Jan. 8, and gradually re-released in phases over the next two weeks.
If you had Automatic Update turned on, and you’re running an AMD machine that’s more than a couple of years old, chances are good that you woke up to a blue screen, and restoring your system took two magic incantations and an Act of Congress. Tens of thousands – possibly hundreds of thousands – of AMD machines may have been bricked by this month’s patches. But be of good cheer. Microsoft released KB 4073578 (“Unbootable state for AMD devices in Windows 7 SP1 and Windows Server 2008 R2 SP1”) and KB 4073576 (same for Win8.1 and Server 2012 R2) to fix your problem. Of course, you have to be able to boot your computer to install the updates.
Never mind.
Then there’s .NET.
So far this month, we’ve seen patches roll out like this:
That is an enormous pile of patches; even the folks who are paid to watch patches full time are confused.
Intel BIOS/UEFI patch recalls
Not to be outdone by Microsoft, Intel created mayhem by releasing, then yanking, its Meltdown/Spectre BIOS and UEFI firmware patches for almost every Intel computer released in the past five years. Intel’s documentation rivals that of Microsoft for ambiguity, hyperbole, and obfuscation.
Here are the latest links to BIOS/UEFI Meltdown/Spectre recall advice from the major hardware manufacturers:
If you have new information about any of those vendors, please let me know on the AskWoody Lounge.
Windows patches
No matter which version of Windows you patch, you need to get your antivirus program to signal to Windows that it’s compatible with this month’s updates.
The Win10 Fall Creators Update patch on Jan. 18 seems to have shaken out the major problems with Win10 1709.
The Win10 Creators Update patch on Jan. 17, similarly, seems to fix the outstanding problems with this month’s changes to Win10 1703.
The Win10 Anniversary Update patch on Jan. 17 – again, manual install only – fixes a bunch of bugs in Win10 1607, but it also clobbers Windows Defender Credential Guard (which you probably don’t use).
With the release of KB 4077561 on Jan. 24, Microsoft has fixed many of the acknowledged problems with this month’s Monthly Rollup and Security-Only (manual installation) patches for Win8.1. That said, there’s still a great deal of debate about the proper installation sequence of patches, re-patches and old patches. As usual, Microsoft hasn’t said anything.
.NET patches
This looks like a mess. You can get the details in my Jan. 19 column, but the basic idea is that the original .NET patches for .NET 4.6/4.6.1/4.6.2/4.7/4.7.1 were all bad, and have to be augmented by additional patches. The font problems in the original patches have been fixed in general, but only if you install these latest patches.
Then there’s the Fixit tool KB 4074906 that fixes “Windows Presentation Foundation (WPF) applications that request a fallback font or a character that is not included in the currently selected font.”
Office patches
It appears as if the Office 2016 patch KB 3178662 throws an installation error 0x8007006e. The Office folks, who are usually good about acknowledging problems, haven’t picked this one up yet. Solution? Uninstall “Microsoft Office Proofing Tools Kit Compilation 2016.”
There’s a laundry list of acknowledged problems with Outlook: To-Do Bar and Task List view not displaying events; Unable to “Save All Attachments” to a shared network drive; No Search results found when using All Mailboxes; Find Related option does not show results; Outlook 2010 will not start on WinXP after January updates. The bug that prevented Outlook 2016 from forwarding files attached to text messages was fixed on Jan. 24.
What to do now
Wait.
If you have an irresistible urge to click “Enable Edits” on bogus Word documents, you can disable Equation Editor with a quick registry hack. Other than that, as long as you don’t use IE or Edge, there’s absolutely no reason to dive into the roiling mess of January updates.
In spite of the “Sky is falling” screams online, there’s no sign a single PC has been compromised by the Meltdown or Spectre vulnerabilities. Contrast that to the multitudes of machines that’ve been bricked by bad patches, and the untold users wondering why they have to unwind this month’s firmware updates.
The long and short of it: If you installed any of this month’s patches from Microsoft or your PC manufacturer, you joined the swelling ranks of unpaid beta testers. If your machine’s still working, thank your lucky stars.
There’s a reason why I recommend you turn off Automatic Update and wait for carnage to clear before installing the latest missives.
Group therapy for patchers continues on the AskWoody Lounge.

December 2017
It’s hard to remember the last time we had a Patch Tuesday as inoffensive as this month’s. February 2017 comes to mind — but then again, we didn’t have a Patch Tuesday in February, as Microsoft called it off.
Part of the reason for the relatively easy going this month, I’m convinced, is the lack of attention showered on Windows 7 and earlier versions of Windows 10 (including the Creators Update, version 1703, which has become more-or-less fully baked and remains my version of choice). Aside from a few lackluster security patches, the December update for Win10 1607 fixed the “CDPUserSvc_XXXX has stopped working” bug introduced in a security patch two months ago, and the rest is largely routine.
The exception, of course, is Windows 10 Fall Security Update, version 1709. If you succumbed to the pressure (or the forced upgrade) and installed the latest version of Win10, you were rewarded for your trust by a series of unfortunate patching events worthy of Lemony Snicket. If you’re hell-bent on installing this month’s updates on a Win10 1709 machine, make sure you read the Computerworld synopsis of problems and sometime-solutions. Or, better, forget about it until next month.
The only major problem with the Office December patches that I’ve seen involves the blocking of Word {DDEAUTO} fields — an arcane topic that I covered yesterday. You’ll only notice the difficulty if you have a Word document that needs to update itself every time you open it. Thus, if you install this month’s Office patches, then open a Word doc, and it no longer responds correctly (by, say, pulling data from an Excel spreadsheet and putting the data in the doc), you need to slog through the manual workarounds, edit the registry, and put DDE right again.
As a long-time advocate of powerful documents, I’m sorry to see the “Auto” functions go. At the same time, I can understand why their days were numbered. I hate to admit it, but Microsoft made the right choice in cutting off “Auto” updating.
Bitten by a bug? Bite back. Drop by the AskWoody Lounge.

November 2017
There are so many issues with this month’s security patches that it’s hard to decide where to begin. Let’s start with the problems that have been acknowledged, then move into the realm of what’s not yet fully defined.
Forced upgrades
Many users have remarked about how much the forced 1703-to-1709 Windows 10 upgrades feel like Microsoft’s detested forced upgrades from Win 7 and 8.1 to 10 – the “Get Windows X” campaign. Although the situation’s different on the surface, the net result is the same. Many people who were happily using Windows 10 Fall Update – version 1703 – were forcibly upgraded this month to the Fall Creators Update – version 1709 – even on systems that were not supposed to be upgraded.
At first, Microsoft ignored the uproar. But last week it quietly owned up to the move by putting this notification in the description for November’s Win 10 1703 Patch Tuesday cumulative update:
Known issues in this update:
Windows Pro devices on the Current Branch for Business (CBB) will upgrade unexpectedly.
Microsoft is working on a resolution and will provide an update in an upcoming release.
On the same day, Nov. 22, Microsoft released another cumulative update for 1703, KB 4055254, which doesn’t mention the problem. I’m going to guess it was fixed.
Those who were forcibly upgraded from 1703 to 1709 are now in limbo; if you allowed Win10 to automatically update itself, and the 1709 installer decided to take over, you’re stuck on 1709. Users had 10 days to roll back to the older version, and those days are gone.
That’s not good news if you hit problems with 1709, like the folder permissions problem or the autostart after boot problem. Those who got hit were upgraded without warning.
Broken Epson dot matrix printers
There are lots and lots of Epson dot matrix (and POS terminal) printers alive and well, thank you very much.
To recap, this month’s Patch Tuesday patches broke the Epson dot matrix driver for every supported version of Windows: Win10 1709, Win10 1703, Win10 1607/Server 2016, Win10 1511 Enterprise, Win10 1507 LTSC, Win 8.1/Server 2012 R2, Server 2012, and Win7/Server 2008 R2. (It’s quite remarkable: Microsoft is now actively supporting 11 versions of Windows – 14 if you count the Server versions separately.)
As noted yesterday, there are now fixes for six of those versions: Win 8.1/Server 2012 R2, Server 2012, and Win7/Server 2008 R2 and Win10 1703. There was a fleeting fix for Win10 1709, but it disappeared. As of this morning, there’s a spot reserved for a Win10 1709 cumulative update, KB 4051963 for build 16299.96, but there’s no KB article as yet and no reports of it rolling out. Presumeably, it’ll include a fix for the Epson printing bug.
But there’s still no word on Epson printer fixes for Win10 1511 Enterprise or for Win10 1507 LTSC.
.NET patches appear, disappear, then reappear
Microsoft released four .NET Framework patches on Patch Tuesday:
- 2017-11 Quality Rollup for .Net Framework 3.5.1 on Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2 (KB 4049016)
- 2017-11 Quality Rollup for .Net Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7 on Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB 4049017)
- 2017-11 Quality Rollup for .Net Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7 on Windows Embedded 8 Standard and Windows Server 2012 (KB 4049018)
- 2017-11 Quality Rollup for .Net Framework 2.0 on Windows Server 2008 (KB 4049019)
The company then pulled all of them down before Thanksgiving. There was no official notice, just a string of comments on the MSDN TechNet blog that said, in effect, Microsoft hadn’t handled the supercedence chain on the patches properly and would fix the problem sometime after the U.S. holiday.
Sure enough, they were re-released yesterday.
CDPUserSvc_XXXX has stopped working
This bug, introduced in the Win10 1607 October cumulative update and both of the November 1607 cumulative updates, was finally acknowledged a little over a week ago. The three cumulative updates now contain this notice:
After installing KB4041688, KB4052231, or KB4048953, the error “CDPUserSvc_XXXX has stopped working” appears. Additionally, Event ID 1000 is logged in the Application event log. It notes that svchost.exe_CDPUserSvc_XXXX has stopped working and the faulting module name is “cdp.dll”.
Microsoft is working on a resolution and will provide an update in an upcoming release.
Until then, follow the steps in the Per-user services in Windows 10 and Windows Server article.
To be clear, the bug has not been fixed, although it’s been well documented for six weeks. It even appears in the Win10 1703 Cumulative Update, KB 4051033, which was released on Nov. 27. Expect a real fix in the December Patch Tuesday crop.
Win10 1709 group policy setting incorrectly blocking cumulative updates
In Win10 1709 Fall Creators Update, adjusting the setting “After a Preview Build or Feature Update is released, defer receiving it for this many days” may, in fact, defer cumulative updates (which Microsoft insists on calling “quality updates”).
Poster Klaasklever who first described the bug on the TechNet, pointed to “reports that this issue is also caused by setting to defer Feature Updates in the Windows Update Settings within the normal Windows Settings App.”
It’s clearly a bug in Win10 1709, though it’s not clear which versions are afflicted – and there’s a possibility that the not-yet-released Win10 1709 cumulative update, KB 4051963 for build 16299.96, may fix it. As noted, there’s no KB article as yet, and no reports of it rolling out.
‘Unexpected error from external database driver’ bug resolved
This bug, introduced in Microsoft’s October security patch release, led to Microsoft pushing out five patches in early November:
- KB 4052234 for Windows 7 SP1 and Server 2008 R2 SP1
- KB 4052235 for Windows Server 2012
- KB 4052233 for Windows 8.1 and Server 2012 R2
- KB 4052232 for Windows 10 Fall (“November”) Update, version 1511
- KB 4052231 for Windows 10 Anniversary Update, version 1607, and Server 2016
Users who installed those patches (they had to be manually downloaded and installed) soon discovered that they all brought back old Windows security patches which themselves had bugs. Those buggy patches were yanked a few days later, and all mention of them was scrubbed as if they never existed.
In their stead, the Patch Tuesday Win7 and 8.1 Monthly Rollups and Security-only Updates and the Patch Tuesday patches for Win10 1709, 1703, 1607, 1511 and 1507 all claim to solve the problem.
Equation Editor bug resolved
Two weeks ago, I talked about the Equation Editor bug, CVE-2017-11882. There are a few exploits out in the wild at this point. If you’re concerned about them, you can bypass Equation Editor and eliminate the security hole by changing two Registry entries described in the Embedi article on the subject.
Good news? The HP Spyware update doesn’t appear to be a Windows problem. It’s all on HP.
Special thanks to @MrBrian, @abbodi86 and @PKCano
Did I miss a bug? Need a scorecard? I sympathize! Drop by the AskWoody Lounge.

October 2017
Microsoft’s foray into quantum computing sure sounds neat, but those of us stuck with real programs on real computers have been in something of a quandary. Once again this month, we’ve hit a bunch of stumbling blocks, many of which were pushed down the Automatic Update chute.
Before we dissect the creepy-crawlies this month, it’s important to remember that you have to get the .Net patches installed, unless you fastidiously refrain from clicking the “Enable Editing” button in Word.
Windows 10
After telling us that Windows 10 Creators Update, version 1703, is “the most performant and reliable version of Windows 10 ever!” you might expect some stability with version 1703 patches. This month, that didn’t happen. After releasing cumulative update KB 4038788 on Patch Tuesday, we got a new out-of-band fix for bugs introduced by that same update. The new cumulative update, KB 4040724, appeared in Windows Update on Monday, Sept. 25. It brings 1703 up to build 15063.632. So far, I haven’t heard of any problems with the new cumulative update — but it’s been less than a day.
The situation with Win10 Anniversary Update, version 1607, isn’t as straightforward. Apparently, there were a host of problems that appeared after this month’s Patch Tuesday cumulative update, KB 4038782. It isn’t clear if that update introduced bugs of its own, but the situation’s bad enough that we got a second cumulative update this month, again on Monday. KB 4038801 brings Win10 version 1607 to build 14393.1736. It’s a hotfix; it isn’t distributed via Automatic Update. You have to download KB 4038801 and install it manually. I haven’t seen a detailed analysis of the security holes fixed by this odd Monday patch – but to date I haven’t seen any complaints, either. The day is still young.
For reasons as yet unexplained, KB 4038801 is only for Win10 1607; it’s explicitly not released for Server 2016.
There’s a note on the 1607 patch site that says:
Windows Update Client Improvement
Microsoft will release an update directly to the Windows Update Client to improve Windows Update reliability. It will only be offered to devices that have not installed any recent cumulative updates and are not currently managed (e.g., domain joined).
As noted by @abbodi86 on AskWoody.com:
The note means [they] are going to release a separate “small” update for WUC, similar to this one for version 1507. They could also release the update directly as a SelfUpdate for WUC like they used to do with Windows prior [to] Windows 8 (for example, latest for Windows 7 is v7.6.7600.320 before they shifted to separate WUC updates starting with KB2990214).
Windows Server 2016
When you run the Get-PhysicalDisk cmdlet, some disks may display an operational status of “In Maintenance Mode.” The Get-VirtualDisk cmdlet may also display the operational status of the virtual disk as “Degraded.” There’s a manual workaround described in KB 4043361.
On Windows Server 2016, when you try to download updates by using Windows Update (stand-alone or WSUS), the process hangs at 0 percent completion. Microsoft has a description of the problem and two manual overrides in KB 4039473.
Windows 8.1
Everyone’s favorite whipping boy just took another lash. Many folks report that, after installing KB 4038792 — the September Monthly Rollup for Win 8.1 — they can no longer log on to their computers with a Microsoft account. I posted the details yesterday. Still no word from Microsoft – not even an acknowledgment of the problem on the KB article.
Windows 7
There’s a well-publicized problem with Internet Explorer 11 suddenly sprouting a search box on the address bar after installing KB 4038777 (the Windows 7 Monthly Rollup) or KB 4036586 (the September Internet Explorer Security-only patch). For a detailed look at what’s happening, with screenshots, see ElderN’s post on the Microsoft Answers forum. Turns out up the flim-flammery is a result of font sizes changed behind the scenes and a possible undocumented switcheroo in one of the IE settings. See @PKCano’s post.
Poster Richard has also identified a problem with starting IE 11 after this month’s Windows 7 updates — and he found a solution. Again, it’s related to undocumented changes in the Tab View settings and in font size. See post 8 on the AskWoody Lounge.
Office
I’ve seen no change from the sorry state we were in a week ago: Microsoft pulled the September Outlook 2007 security patch KB 4011086 and replaced it with KB 4011110, but you have to manually uninstall the bad patch before you install the new one. Microsoft posted incorrect information about the uninstallation method. Both that patch and the Outlook 2010 patch, KB 4011089, have a nasty habit of changing languages in menus.
.Net
The .NET Security and Quality Rollups make certain custom images turn black. As Microsoft puts it: “After you install the September 12, 2017, .NET Security and Quality Rollups that apply to the .NET Framework 4.6, 4.6.1, 4.6.2, and 4.7, you experience rendering issues in Windows Presentation Foundation (WPF) applications that use WPF types in a Windows service.”
There’s a description of the problem on the Visual Studio forum and a workaround in KB 4043601. The workaround suggests that you uninstall the Security and Quality Rollup and install the Security-only patch.
In addition, Microsoft has released a preview of next month’s .Net Framework patches.
Recommendations
Assuming you don’t click “Enable Editing” in Word, there are no immediately pressing September patches. I say it’s wise to wait and see if any of the outstanding bugs get fixed — and wait to see if the patches-of-patches generate new problems of their own.
Remember when patching was easy?
Please join us for an ongoing Patch Festschrift on the AskWoody Lounge.

September 2017
September’s retinue of Microsoft patches includes one very important .NET fix that blocks a security hole brought to life when you open an RTF file in Word. So far, it’s only been seen in the wild in a Russian-language RTF document, apparently generated by NEODYMIUM, allegedly used by a nation-state to snoop on a Russian-speaking target.
Several researchers have found ways to leverage the security hole, and it’s only a matter of time before some enterprising folks come up with ways to turn it into a widespread infection vector. Bottom line: If you can’t keep your finger off the “Enable Editing” button in Word, you better get this month’s security patches installed.
- The Win10 Creators Update cumulative update, KB 4038788, brings Win10 1703 up to build 15063.608. It contains 25 security patches as well as dozens of plain old bug fixes. I’m seeing a number of complaints about Edge misbehaving after the update: behind-the-scenes crashes showing in Event Viewer and Reliability Monitor, and occasional stops with an application error event id of 1000. So far, there aren’t enough reports to confirm that there’s a bona fide problem with Edge, but it’s a concern.
- The bug in Word and Outlook that I described earlier this week, Buggy Word 2016 non-security patch KB 4011039 can’t handle merged cells, is still around. That’s the same bug I wrote about a couple of weeks ago in Word, Outlook merged-cell problem arises after install of patch KB 3213656. Microsoft has (finally!) confirmed both of the bugs. The only solution offered:
- “You can uninstall both KBs and your tables will return to normal,” Microsoft said. “We anticipate releasing the fix for this issue in the next monthly update, tentatively scheduled for October 3, 2017.”
- Excel 2016’s security patch KB 4011050 can put spurious black borders around rows or cells. If you’re getting unexpected black borders, download and manually install KB 4011165. As best I can tell, that bug isn’t listed on the official Fixes or workarounds for recent issues in Excel for Windows site.
- Multiple language problems with the Outlook 2007 security patch KB 4011086. Reports of Hungarian switched to Swedish, Italian to Portuguese, Slovenian to Swedish, Italian to Spanish, Dutch to Swedish, and who-knows-what-else. The solution, offered by TechNet poster Sitz-AIR:
- 1) uninstall KB4011086. If you have two of them listed, uninstall both of them.
A general reminder: If you have trouble installing Windows 10 updates, make sure you go through the list at Windows 10 install issues — and what to do about them.
For up-to-the-second notices, see the Patch Alert update on AskWoody

August 2017
One week after Patch Tuesday, and would-be Windows Updaters are facing a handful of bugs. Some will find them minor annoyances. Others … not so much. Here are the known bugs, and where we stand in the struggle to resolve the problems.
Worthy of note: Microsoft is now acknowledging many bugs that in the past would’ve gone without comment. There’s hope.
Here are the known, significant buggy security patches:
- Windows 10 Anniversary Update, version 1607 – Cumulative update KB 4034658 wipes out Update History, unhides hidden updates, and effectively disconnects some updated computers from WSUS. Microsoft has acknowledged all three of those bugs in the KB 4034658 article with the usual “Microsoft is investigating this issue and will provide an update as soon as possible.”
- The first undocumented buggy driver this month for the Surface Pro 4, “Surface – System – 7/21/2017 12:00:00 AM – 1.0.65.1,” was released on August 1. It was replaced by a second driver “Surface – System – 7/31/2007 12:00:00 AM – 1.0.75.1” on August 4. The second one was documented. But then we saw four more undocumented Surface Pro 4 drivers — “Intel driver update for Intel(r) Dynamic Platform and Thermal Framework Generic Participant,” “Power Participant,” Processor Participant” and “Manager” — all released on Saturday, August 12. Sometime late on August 14, Microsoft posted information about two of the drivers.
- Both the Windows 7 August Monthly rollup KB 4034664 and the manually installed security-only patch KB 4034679 are causing problems with two-screen systems: The second screen starts showing gibberish with many applications, including Office. The problem has been widely reported — even replicated with a Proof of Concept program — but Microsoft hasn’t yet acknowledged it.
- The only bug reported by Microsoft in its August Windows 7 security patches is an old bug, continuing from July, in which a buggy LDAP plugs up TCP dynamic ports. That bug hasn’t been fixed.
- The Windows 8.1 Monthly rollup listing mentions a known bug: NPS authentication may break, and wireless clients may fail to connect. The solution is to manually set a registry entry on the server.
Dozens of patches were made to Office earlier this month but, so far, I’m not aware of any bugs.
Depending on which version of Windows you’re using, and how you’re using it, those bugs may be important or they may be annoyances.
I continue to recommend that you hold off on applying this month’s patches. I haven’t seen any malware outbreaks that are blocked by the August patches, and we may get some surprises — good, bad or indifferent — later today.
Have a question or a bug report? Drop by the AskWoody Lounge.
