Microsoft 365 Enterprise Application Authentication
Over the last several years, Microsoft has worked on APIs and authentication methods to help organizations mitigate security concerns around compromised credentials. These advances include Azure Vault, MFA, Ephemeral accounts, enterprise applications and more. In many security best practices, the goal is to migrate away from using username and password authentication for automated process and application access using APIs. This also becomes a constraint when rolling out MFA in an organization because the user must be present for the application authentication. A bridge in this scenario was the addition of app passcodes that could be used with user accounts to authenticate, but this still came with potential security concerns. Enterprise applications have now become the better method for this problem, allowing a dedicated application in Azure to be scoped in with the proper API permissions. Read on to learn about the benefits of enterprise applications, the benefits of using app-only authentication methods and what changes will need to be made when Microsoft deprecates access to basic authentication (username and password) access method later this year.
Microsoft 365 and MFA
Microsoft 365 incorporates Multi-Factor Authentication (MFA), a vital security feature. MFA adds an extra layer of protection to user accounts, requiring additional verification steps. This could involve fingerprint scans, mobile device codes or biometric authentication. MFA is crucial in today’s evolving digital landscape, safeguarding accounts from credential weaknesses or theft. Unfortunately, this security feature does not work well regarding application management since the user needs to be present for the authentication process. As a stopgap to this problem, users could use app passcodes, which would give access to resources without user interaction — but inherently opens the account to be compromised if the code was exposed. This is not ideal, leading to the modern authentication method with enterprise applications.
Deprecation of Microsoft 365 Basic Authentication
Over the last several years, Microsoft has been building out the Graph API. The Graph API is an abstraction layer protocol that was developed with the sole purpose of stitching together connecting points for their SaaS application. This API is important because, without a central connector, there was an API sprawl between application access methods and release cycles. This may not seem like much to a user, but to developers, this consistency makes all the difference.
In developing the Graph API, Microsoft has worked to connect to all Microsoft 365 products and build out a modern authentication aspect. This modern authentication allows for authentication and access to Microsoft applications through more secure methods like enterprise applications and certificates. With the more secure options available, Microsoft has started to depreciate the legacy authentication methods that use usernames and passwords. This means you will need to configure an enterprise application for products you still wish to manage Microsoft 365 data.
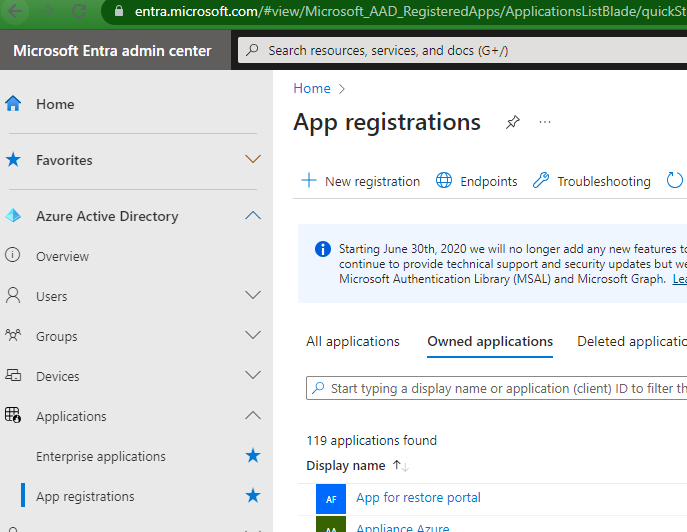
How To Add New API Permissions
This section will cover manually creating enterprise applications and adding an API scope. Keep in mind that some products, like Veeam, will allow for convenient ways to deploy and configure this application directly from the console.
Delegated vs. Application Permissions
A number one question about enterprise applications, outside the required scope, regards the difference between delegated and application permissions. The primary difference between these methods is how the permissions are leveraged. Delegated access is used when authentication access is performed with a user present; application permission is used in scenarios where the application can act without user intervention. The permissions for modern app-only authentication in Veeam Backup for Microsoft 365 can be found in the user guide.
Create and Modify an Enterprise Application
Enterprise applications are created and modified using the Entra admin center, which you can find through the admin portal on the left-hand side or directly accessed from https://entra.microsoft.com/. Once in the Entra admin center, navigating on the left-hand side to Azure Active Directory, then App registrations.
Step 1: navigate Entra Admin Portal
To create a new application, select “+ New Application.” If you desire to update an application, then select the application from the list and skip to Step 3.
Step 2: create new application
On the “Register an application” page, give the app a name that can be identified later and use the supported account types to be “Accounts in this organizational directory only (company org),” then click “Register” at the bottom.
The new app should take less than a minute to register.
Step 3: add permissions to application
Add permissions to the app by navigating to API permissions and selecting “+ Add a Permission.”
From the blade on the right-hand side, select the permission type needed.
Either by scrolling or using the search box, select all permissions needed for this API, then click “Add permissions.”
Once all permissions have been added, consent will need to be granted by an admin using the “Grant admin consent for [company]” button. If the account is an admin with permissions to grant consent, then use the button and select “Yes” to activate the API permissions. Even after consent is granted, this can take some time to update in the cloud and be used.
Quick troubleshooting step: If the app still cannot be used in software after 20 minutes, double check permissions against the user guide or create a ticket with support if the problem persists.
Use Veeam To Manage Enterprise Applications
Unless it is necessary to deploy the application manually, the preferred convenience method is to deploy and update enterprise applications directly through Veeam Backup for Microsoft 365. This process can be done when first adding the organization or updating with the same organization wizard.
Option 1: new organization
If you are adding a new organization and want the application to be deployed for you with the right permissions, select “Register a new Azure AD application automatically” on the Microsoft 365 connection settings page.
Option 2: if this is an existing organization, then you can right click on the organization and select edit organization to get back to the organization wizard. In the wizard, select “Use an existing Azure AD application” and use the check box for “Grant this application required permissions and register its certificate in Azure AD.” When finishing with the wizard, the updated permissions will automatically be assigned.
When deploying a new application or updating an existing application, the process will take you to a Microsoft authentication page where you will use a single-use application code. Veeam uses native Microsoft 365 authentication, which will leverage existing security enhancements implemented by your organization, like MFA.
Conclusion
In conclusion, Microsoft has made significant progress in addressing security concerns by developing various APIs and authentication methods to reduce reliance on user credentials for application authentication. Despite serving as a bridge for basic authentication, app passcodes still pose potential security risks. Embracing enterprise applications enables organizations to enhance security and mitigate risks associated with compromised credentials and more granular permission assignments.











You must be logged in to post a comment.