Merging signing and encryption with AWS KMS asymmetric keys
In this article, I discuss how exactly to use AWS Key Management Service (KMS) to mix asymmetric digital signature and asymmetric encryption of exactly the same data.
The addition of assistance for asymmetric keys in AWS KMS has exciting use cases for customers. The opportunity to generate, manage, and make use of public and private important pairs with KMS allows you to perform electronic signing operations using RSA and Elliptic Curve Cryptography (ECC) keys. AWS KMS asymmetric keys may be used to perform digital encryption functions using RSA keys furthermore. You may use these functions to digitally sign and encrypt exactly the same data together.
Another significant property of AWS KMS asymmetric keys is definitely they enable disconnected use situations. For instance AWS KMS asymmetric keys may be used to cryptographically verify an electronic signature client-side with no need for a network connection. AWS KMS asymmetric keys furthermore enable scenarios where clients may use KMS to safely manage decryption of information that is encrypted by way of a partner’s system that will not integrate with AWS APIs or get access to AWS accounts credentials. With regard to simplicity, however, the illustration that I discuss in this article describes a connected make use of situation where all cryptographic activities are performed server-aspect in AWS KMS making use of AWS credentials. The usage of AWS KMS asymmetric keys throughout this write-up allows the overall method of end up being adapted to disconnected and/or non-AWS-integrated make use of cases.
Overview
This post contains three basic steps.
- Create and configure AWS asymmetric consumer master keys (CMK), AWS Identity and Access Management (IAM) functions, and key guidelines.
- Use your own asymmetric CMKs to encrypt and signal an example message in the function of the sender.
- Use AWS KMS to decrypt and verify the information signature of the sample information archive you generated in the last procedure making use of your asymmetric CMKs inside the role of the receiver.
Prerequisites
The commands I take advantage of in this tutorial were tested using AWS Command Line Interface (AWS CLI) version 2.50 on Amazon Linux 2. To be able to run these instructions in your is likely to local environment make sure that you have initial installed and up-to-date the AWS CLI.
I suppose you have a minumum of one administrator identity accessible to you which has broad rights for creating functions, assuming roles, along with creating, using plus managing KMS keys. This is often a federated identity (for instance, from your own corporate identity service provider or from the social identification), or it could be an AWS IAM consumer. Where no AWS identification is mentioned, I suppose you will be accessing the AWS Management Console or even the AWS CLI by using this administrator identity.
For simplicity, The KMS is established by me keys in exactly the same region as one another. You need to specify an AWS Area with all the AWS CLI, either or even by setting the default Region explicitly. Before beginning, you need to select an AWS Region to function in such like US East (N. Virginia). Should you have not really configured the AWS CLI in your atmosphere please review the Configuration basics portion of the AWS Command Line Interface User Guidebook for instructions. You might revert this configuration when you have finished if you don’t wish to continue utilizing a default Region together with your AWS CLI. Observe your selected area. When employed in the AWS System, if you don’t see sources, such as for example AWS KMS keys, that you anticipate you might like to confirm that you’re viewing resources in your selected Region. To find out more on selecting your Area in the AWS Gaming console see Choosing an area in AWS Management Console STARTING OUT Guide.
Create and configure assets
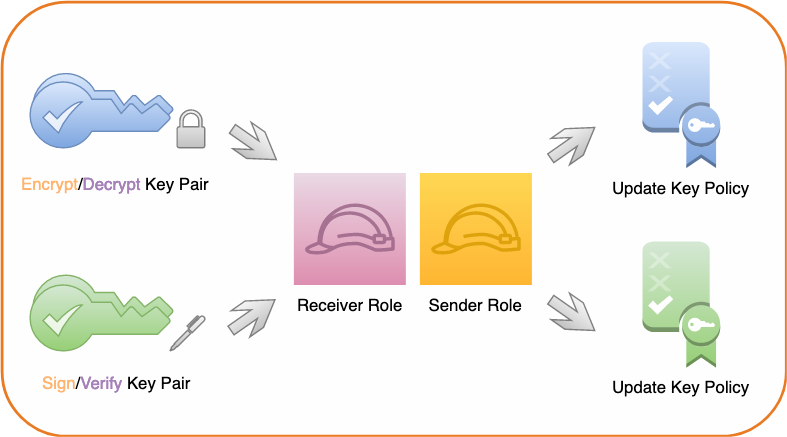
In the initial phase of the tutorial you configure and create two asymmetric AWS KMS CMKs, two AWS IAM functions, and configure the main element policies for each of one’s KMS CMKs to grant permissions to the functions. Shown in the next shape.

Figure 1: Create keys, functions, and key plans
Create asymmetric signing and encryption crucial pairs
In step one, you create two asymmetric grasp keys (CMK). One is configured for verifying and signing digital signatures as the additional is configured for encrypting and decrypting data.
Note: The CMKs configured because of this post are illustrations. RSA and Elliptic curve CMKs essential specs can differ in a number of measurements. The RSA or elliptic curve important spec that you select might be dependant on your security specifications or the requirements of one’s task. Different CMK crucial specs are priced in different ways and are at the mercy of different request quotas since they each have various performance profiles. Generally, use ECC or even RSA keys with the highest security level that’s practical and affordable for the task. To learn more on CMK configuration choices, please review the How to select your CMK configuration portion of the KMS Developer Guide.
To develop a CMK for decryption
and encryption
- Make use of the KMS CreateKey API. Pass RSA_4096 for the CustomerMasterKeySpec parameter and ENCRYPT_DECRYPT for the KeyUsage parameter in the AWS CLI instance command below to be able to generate a RSA 4096 key set for signature development and verification making use of AWS KMS.
Note: If successful, this control returns a KeyMetadata object. Observe the KeyID value in this item.
- As a best exercise, assign an alias for the key. Utilize the following order to assign an alias of sample-encrypt-decrypt-key to your freshly developed CMK (replace the target-key-id worth of 1234abcd-12ab-34cd-56ef-1234567890ab together with your KeyID). Mapping a human-readable alias to the KeyID shall ensure it is easier to identify, use, and manage.
To develop a CMK for verification
and signature
- Make use of the KMS CreateKey API. Pass ECC_NIST_P521 for the CustomerMasterKeySpec parameter and Indication_VERIFY for the KeyUsage parameter in the AWS CLI illustration command below to be able to generate an elliptic curve (ECC) key set for signature development and verification making use of AWS KMS.
Note: If successful, this control returns a KeyMetadata
object. Observe the KeyID value.
- Use the following order to assign an alias of sample-sign-verify-essential to your newly made CMK (change the target-key-id worth of 1234abcd-12ab-34cd-56ef-1234567890ab together with your KeyID).
Create sender and receiver functions
For the next phase of the tutorial, you create two AWS principals. Utilize the methods that follow to generate two roles-a sender principal and a receiver principal. Later, you’ll grant permissions to execute private key operations (indication and decrypt) and open public key procedures (verify and encrypt) to these functions.
To create and configure the functions
-
- Navigate to the AWS Identity and Access Management (IAM) Create role console dialogue which allows entities inside a specified accounts to assume the part. Enter your Accounts ID and choose Up coming, as proven in the next figure.
Note: In the event that you don’t find out you AWS accounts ID, please read Finding you AWS account ID in the AWS IAM User Tutorial for help with how to obtain these details.

Shape 2: Enter your accounts ID to begin developing a role inside AWS IAM
- Select Following through another two displays.
Note: By clicking following through these dialogues you don’t attach a good IAM permissions plan or a tag to the new role.
- On the ultimate screen, get into a Role name of SenderRole and a Role description of one’s choice, as demonstrated in the following number.

Number 3: Create the sender role
- Choose Create role to complete creating the sender role.
- Navigate to the AWS Identity and Access Management (IAM) Create role console dialogue which allows entities inside a specified accounts to assume the part. Enter your Accounts ID and choose Up coming, as proven in the next figure.
create the receiver part
- To, repeat the preceding function creation process. Nevertheless, in step three 3, substitute the real name ReceiverRole intended for SenderRole.
Configure key plan permissions
Best practice would be to stick to the principle of minimum privilege and offer each AWS principal with the minimal permissions essential to perform its duties. The sender and receiver functions that you produced in the last step now have no permissions in your accounts. For this situation, the receiver principal should be granted authorization to verify electronic signatures and decrypt information in AWS KMS making use of your asymmetric CMKs and the sender principal should be granted permission to generate electronic signatures and encrypt information in KMS making use of your asymmetric CMKs.
To provide access handle permissions for AWS KMS actions to your AWS principals, attach an integral policy to all of your CMKs.
Modify the CMK essential policy
For the sample-encrypt-decrypt-key CMK, grant the IAM part for the sender principal (SenderRole) kms:Encrypt permissions and the IAM function for the receiver principal (ReceiverRole) kms:Decrypt permissions in the CMK important policy.
To modify the CMK crucial policy (console)
- Navigate to the AWS KMS page in the AWS Console and choose customer-managed keys.
- Select your sample-encrypt-decrypt-important CMK.
- In the key policy area, choose edit.
- To allow your receiver principal to utilize the CMK to decrypt information encrypted under that CMK, append the next statement to the main element policy (replace the accounts ID worth of 111122223333 with your personal).
- To allow your sender principal to utilize the CMK to encrypt information, append the next statement to the main element policy (replace the accounts ID worth of 111122223333 with your personal):
- Choose Save changes.
Be aware: The kms:Encrypt permission is enough allowing the sender principal to encrypt smaller amounts of arbitrary information making use of your CMK directly.
Grant signal and verify permissions to the CMK essential policy
For the sample-sign-verify-key CMK, grant the IAM part for the sender principal (SenderRole) kms:Indication permissions inside the CMK important policy and the IAM function for the receiver principal (ReceiverRole) kms:Verify permissions in the CMK crucial policy.
To grant signal and verify permissions
- Using exactly the same process since above, demand essential policy edit dialog to get the sample-sign-verify-essential CMK within the AWS gaming console.
- To allow your sender principal to utilize the CMK to generate digital signatures, append the next statement to the main element policy (replace the accounts ID worth of 111122223333 with your personal).
- To allow your receiver principal to utilize the CMK to verify signatures developed by that CMK, append the next statement to the main element policy (replace the accounts ID worth of 111122223333 with your personal):
- Choose Save changes.
Key permissions overview
When these key plan edits have already been completed the sender principal:
- Will possess permissions to encrypt information using the sample-encrypt-decrypt-key CMK and generate digital signatures utilizing the sample-sign-verify-key CMK.
- Will not possess permissions to decrypt or even to verify signatures utilizing the CMKs.
The receiver principal:
- Will possess permissions to decrypt information which includes been encrypted utilizing the sample-encrypt-decrypt-key CMK also to verify signatures made out of the sample-sign-verify-key CMK.
- Will not have got permissions to encrypt or even to generate signatures utilizing the CMKs.

Figure 4: Overview of key plan permissions
encrypting and
Signing an example message
Up to now, you’ve created two asymmetric CMKs, created a couple of receiver and sender functions, and configured permissions for all those roles in all of your CMK essential policies. In the next phase of the tutorial, you believe the part of sender and make use of your asymmetric signature and verification CMK to indication a sample message. Afterward you bundle the sample information and its own corresponding digital signature collectively into an archive and make use of your encryption and decryption asymmetric CMK to encrypt the archive.

Figure 5: Developing a information signature and encrypting the information alongside its signature
Notice: The purchase of operations inside this technique is that the information is very first signed and the signature and the information are encrypted jointly. This purchase is intentional. Whenever a message is definitely signed and encrypted, neither the contents nor the identification of the sender will be open to unauthorized 3rd parties. If the purchase of functions were reversed, nevertheless, and a note was 1st encrypted and signed it might leak information regarding the sender’s identification to unauthorized 3rd celebrations. Moreover, when a information can be encrypted and signed, an unauthorized third party with usage of the data files could discard the genuine signature developed by the sender and replace it with a legitimate signature created by their very own essential. This creates the prospect of a third party to deceptively create the looks they are the reputable sender of the information and exploit that misperception more.
Believe the sender function
Begin by assuming the sender part. To be able to successfully assume a job you must authenticate being an IAM principal which includes permission to execute sts:AssumeRole. If the main you’re authenticated as lacks this permission you shall unable to assume the sender function.
To assume the sender part
- Run the next command, but make sure to substitute the account ID worth of 111122223333 together with your account ID:
- The return value for an access is supplied by this command important ID, secret crucial, and session token. Alternative them to their respective locations in the next commands and execute:
- Confirm that you’ve successfully assumed the sender part by issuing:
Note: If the result of this command provides the text assumed-function/SenderRole, then you’ve successfully assumed the sender role.
Create a message
Now, develop a sample information file called information.json.
To develop a message
Run the next command to produce a message with the next content:
Create an electronic signature
Creating and verifying an electronic signature pertaining to the message provides self-confidence that the message contents haven’t been changed after getting sent. This characteristic is called integrity. Furthermore, when usage of a signing key will be scoped to a specific principal, verifying and developing a electronic signature for the information provides confidence inside the sender’s identity. This characteristic is called authenticity. Finally, a higher amount of confidence in both integrity and authenticity of a note limits the plausible capability of a sender to fraudulently deny getting signed a note. This characteristic is well known a non-repudiation.
To develop a digital signature
Run the next command to produce a electronic signature for message.json:
This generates an unbiased digital signature file, message.sig, for information.json. Any modification to the contents of information.json, such as for example changing the message or even sender fields, may cause signature validation of message now.sig to fail for message.json.
Encrypt the signature
and message
Even with the advantages of an electronic signature, the message could possibly be viewed by any party with usage of the file still. To be able to provide self-confidence that the information contents aren’t subjected to unauthorized parties, it is possible to encrypt the information. This characteristic is called confidentiality. To be able to retain the great things about your digital signature it is possible to encrypt the information and corresponding signature collectively within a package.
To encrypt the signature
and information
- Combine your own message and signature into an archive. For instance, with the GNU Tar utility it is possible to issue the next:
This will develop a new archive file named message.tar.gz containing both your information and message signature.
- Encrypt the archive using AWS KMS. To take action, issue the next command:
This can output a message.enc document containing an encrypted duplicate of the information.tar.gz archive.
verifying and
Decrypting an example message
Given that you’ve created, signed, and encrypted a note, let’s modification gears and notice what dealing with this information.enc document is similar to from the viewpoint of a receiving celebration. In the ultimate phase of the tutorial you presume the part of receiver and make use of your asymmetric CMKs to decrypt the encrypted information archive and verify the electronic signature that you developed. Finally, you shall look at your message. The process is proven in the following body.

Body 6: Decrypting a note archive and verifying the message signature
Presume the receiver function
Assume the receiver part to enable you to simulate finding a encrypted and signed message. As before, to be able to believe the receiver role you need to authenticate being an IAM principal which includes permission to execute sts:AssumeRole. If the main you’re authenticated as lacks this permission you shall unable to assume the receiver function.
To assume the receiver part
- Duplicate the information.enc file to a fresh directory to produce a clean working room and navigate there inside a terminal program.
- Believe your receiver function. To take action, execute the next command, replacing the accounts ID worth of 111122223333 with your personal:
- The return value because of this command has an access essential ID, secret important, and session token. Alternative them to their respective areas in the next commands and execute:
- Confirm which you have successfully assumed the receiver function by issuing:
If the output of the command provides the text assumed-part/ReceiverRole you possess successfully assumed the receiver role after that.
Decrypt the encrypted message archive in AWS KMS
Decrypt the encrypted message archive to gain access to the plaintext of the message and message signature documents.
To decrypt the encrypted information archive
- Issue the next command:
- This will generate an unencrypted message.tar.gz document that you could unpack with:
This, subsequently, will broaden the archive contents message.message and sig.json inside your working directory.
Verify the message signature
To verify the signature on the information issue the next command:
In the reaction you should note that SignatureValid is marked true indicating that the signature has been verified utilizing the specified sample-sign-verify-key that you granted the sender principal permission to create signatures with.
Look at the message
Lastly, open message.json and watch the file’s contents by issuing the next command:
So as to the contents of the file haven’t been modified but still read:
Note: Be careful in order to avoid making any kind of adjustments to the contents of the file. Even a minimal modification of the information contents will compromise the integrity of the information and cause future tries at signature validation making use of your message.sig document to fail.
Summary
In this tutorial, you signed and encrypted information using two AWS KMS asymmetric CMKs and afterwards decrypted and verified your signature using those CMKs.
You created two asymmetric CMKs in AWS KMS first, 1 for verifying and creating digital signatures and another for encrypting and decrypting information. You configured key plan permissions for the sender and receiver principals then. Acting simply because your sender principal, you signed a note in AWS KMS digitally, additional the message and signature in order to an archive and encrypted that archive within AWS KMS then. After that you assumed your receiver function and decrypted the archive in AWS KMS, seen your information, and verified its signature in AWS KMS.
To learn more concerning the asymmetric keys function of AWS KMS, please browse the AWS KMS Developer Guide. In case you have questions concerning the asymmetric keys function, please start a brand-new thread on the AWS KMS forum. For those who have feedback concerning this post, submit remarks in the Remarks section below.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.

You must be logged in to post a comment.