Introducing the AWS WAF traffic overview dashboard
For many network security operators, protecting application uptime can be a time-consuming challenge of baselining network traffic, investigating suspicious senders, and determining how best to mitigate risks. Simplifying this process and understanding network security posture at all times is the goal of most IT organizations that are trying to scale their applications without also needing to scale their security operations center staff. To help you with this challenge, AWS WAF introduced traffic overview dashboards so that you can make informed decisions about your security posture when your application is protected by AWS WAF.
<p>In this post, we introduce the new dashboards and delve into a few use cases to help you gain better visibility into the overall security of your applications using AWS WAF and make informed decisions based on insights from the dashboards.</p>
<h2>Introduction to traffic overview dashboards</h2>
<p>The traffic overview dashboard in AWS WAF displays an overview of security-focused metrics so that you can identify and take action on security risks in a few clicks, such as adding <a href="https://docs.aws.amazon.com/waf/latest/developerguide/waf-rule-statement-type-rate-based-request-limiting.html" target="_blank" rel="noopener">rate-based rules</a> during distributed denial of service (DDoS) events. The dashboards include near real-time summaries of the <a href="https://aws.amazon.com/cloudwatch/" target="_blank" rel="noopener">Amazon CloudWatch</a> metrics that AWS WAF collects when it evaluates your application web traffic.</p>
<p>These dashboards are available by default and require no additional setup. They show metrics—total requests, blocked requests, allowed requests, bot compared to non-bot requests, bot categories, CAPTCHA solve rate, top 10 matched rules, and more—for each web access control list (web ACL) that you monitor with AWS WAF.</p>
<p>You can access default metrics such as the total number of requests, blocked requests, and common attacks blocked, or you can customize your dashboard with the metrics and visualizations that are most important to you.</p>
<p>These dashboards provide enhanced visibility and help you answer questions such as these:</p>
<ul>
<li>What percent of the traffic that AWS WAF inspected is getting blocked?</li>
<li>What are the top originating countries for the traffic that’s getting blocked?</li>
<li>What are common attacks that AWS WAF detects and protects me from?</li>
<li>How do my traffic patterns from this week compare with last week?</li>
</ul>
<p>The dashboard has native and out-of-the-box integration with CloudWatch. Using this integration, you can navigate back and forth between the dashboard and CloudWatch; for example, you can get a more granular metric overview by viewing the dashboard in CloudWatch. You can also add existing CloudWatch widgets and metrics to the traffic overview dashboard, bringing your tried-and-tested visibility structure into the dashboard.</p>
<p>With the introduction of the traffic overview dashboard, one AWS WAF tool—Sampled requests—is now a standalone tab inside a web ACL. In this tab, you can view a graph of the rule matches for web requests that AWS WAF has inspected. Additionally, if you have enabled request sampling, you can see a table view of a sample of the web requests that AWS WAF has inspected.</p>
<p>The sample of requests contains up to 100 requests that matched the criteria for a rule in the web ACL and another 100 requests for requests that didn’t match rules and thus had the default action for the web ACL applied. The requests in the sample come from the protected resources that have received requests for your content in the previous three hours.</p>
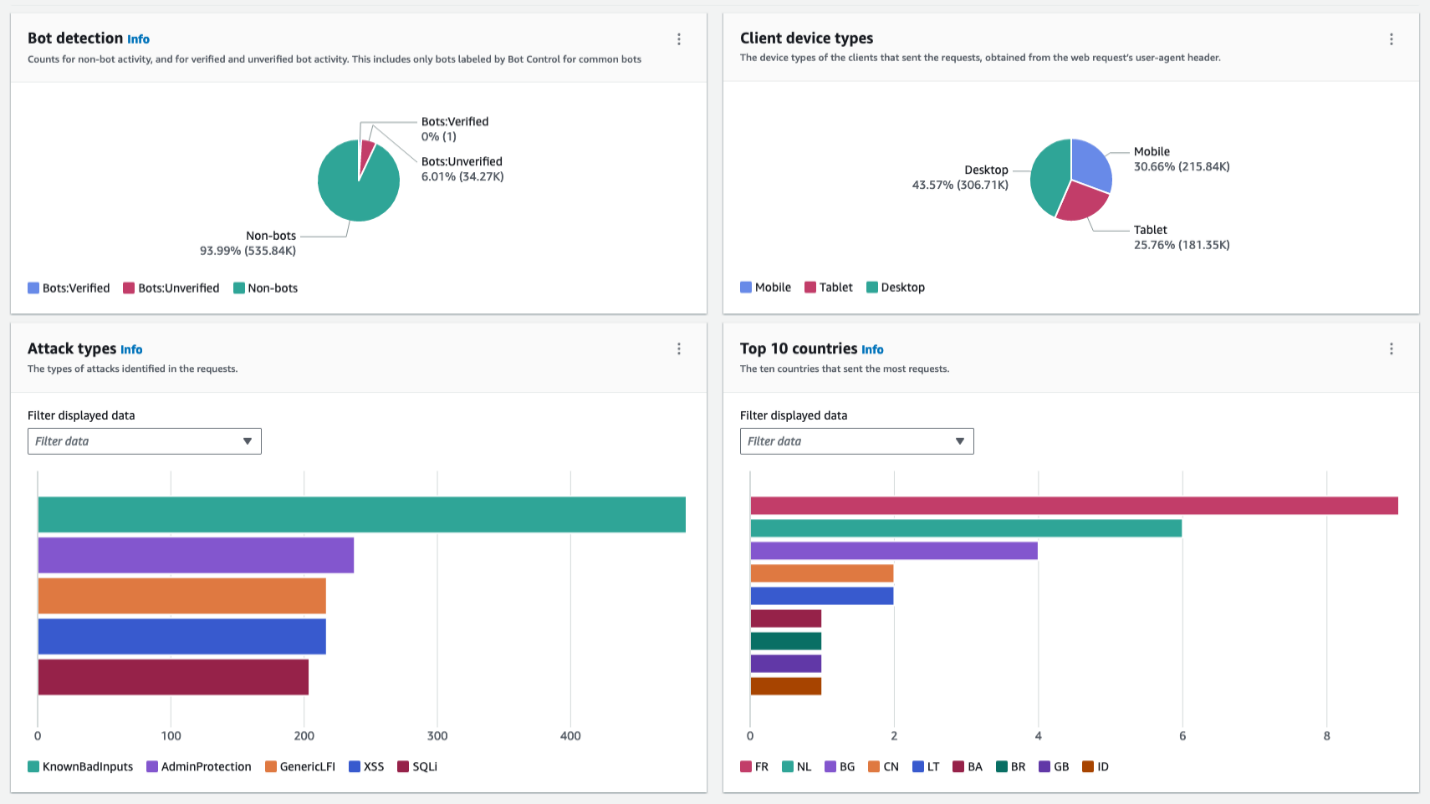
<p>The following figure shows a typical layout for the traffic overview dashboard. It categorizes inspected requests with a breakdown of each of the categories that display actionable insights, such as attack types, client device types, and countries. Using this information and comparing it with your expected traffic profile, you can decide whether to investigate further or block the traffic right away. For the example in Figure 1, you might want to block France-originating requests from mobile devices if your web application isn’t supposed to receive traffic from France and is a desktop-only application.</p>
<div id="attachment_33499" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33499" src="https://infracom.com.sg/wp-content/uploads/2024/03/img1-7.png" alt="Figure 1: Dashboard with sections showing multiple categories serves as a single pane of glass" width="780" class="size-full wp-image-33499">
<p id="caption-attachment-33499" class="wp-caption-text">Figure 1: Dashboard with sections showing multiple categories serves as a single pane of glass</p>
</div>
<h2>Use case 1: Analyze traffic patterns with the dashboard</h2>
<p>In addition to visibility into your web traffic, you can use the new dashboard to analyze patterns that could indicate potential threats or issues. By reviewing the dashboard’s graphs and metrics, you can spot unusual spikes or drops in traffic that deserve further investigation.</p>
<p>The top-level overview shows the high-level traffic volume and patterns. From there, you can drill down into the web ACL metrics to see traffic trends and metrics for specific rules and rule groups. The dashboard displays metrics such as allowed requests, blocked requests, and more.</p>
<p>Notifications or alerts about a deviation from expected traffic patterns provide you a signal to explore the event. During your exploration, you can use the dashboard to understand the broader context and not just the event in isolation. This makes it simpler to detect a trend in anomalies that could signify a security event or misconfigured rules. For example, if you normally get 2,000 requests per minute from a particular country, but suddenly see 10,000 requests per minute from it, you should investigate. Using the dashboard, you can look at the traffic across various dimensions. The spike in requests alone might not be a clear indication of a threat, but if you see an additional indicator, such as an unexpected device type, this could be a strong reason for you to take follow-up action.</p>
<p>The following figure shows the actions taken by rules in a web ACL and which rule matched the most.</p>
<div id="attachment_33500" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33500" src="https://infracom.com.sg/wp-content/uploads/2024/03/img2-4.png" alt="Figure 2: Multidimensional overview of the web requests" width="780" class="size-full wp-image-33500">
<p id="caption-attachment-33500" class="wp-caption-text">Figure 2: Multidimensional overview of the web requests</p>
</div>
<p>The dashboard also shows the top blocked and allowed requests over time. Check whether unusual spikes in blocked requests correspond to spikes in traffic from a particular IP address, country, or user agent. That could indicate attempted malicious activity or bot traffic.</p>
<p>The following figure shows a disproportionately larger number of matches to a rule indicating that a particular vector is used against a protected web application.</p>
<div id="attachment_33501" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33501" src="https://infracom.com.sg/wp-content/uploads/2024/03/img3-4.png" alt="Figure 3: The top terminating rule could indicate a particular vector of an attack" width="780" class="size-full wp-image-33501">
<p id="caption-attachment-33501" class="wp-caption-text">Figure 3: The top terminating rule could indicate a particular vector of an attack</p>
</div>
<p>Likewise, review the top allowed requests. If you see a spike in traffic to a specific URL, you should investigate whether your application is working properly.</p>
<h3>Next steps after you analyze traffic</h3>
<p>After you’ve analyzed the traffic patterns, here are some next steps to consider:</p>
<ul>
<li>Tune your AWS WAF rules to better match legitimate or malicious traffic based on your findings. You might be able to fine-tune rules to reduce false positives or false negatives. Tune rules that are blocking legitimate traffic by adjusting <a href="https://docs.aws.amazon.com/waf/latest/developerguide/waf-regex-pattern-support.html" target="_blank" rel="noopener">regular expressions</a> or conditions.</li>
<li>Configure <a href="https://docs.aws.amazon.com/waf/latest/developerguide/logging.html" target="_blank" rel="noopener">AWS WAF logging</a>, and if you have a dedicated security information and event management (SIEM) solution, integrate the logging to enable automated alerting for anomalies.</li>
<li>Set up AWS WAF to automatically block known malicious IPs. You can maintain an IP block list based on identified threat actors. Additionally, you can use the <a href="https://docs.aws.amazon.com/waf/latest/developerguide/aws-managed-rule-groups-ip-rep.html" target="_blank" rel="noopener">Amazon IP reputation list managed rule</a> group, which the Amazon Threat Research Team regularly updates.</li>
<li>If you see spikes in traffic to specific pages, check that your web applications are functioning properly to rule out application issues driving unusual patterns.</li>
<li>Add new rules to block new attack patterns that you spot in the traffic flows. Then review the metrics to help confirm the impact of the new rules.</li>
<li>Monitor source IPs for DDoS events and other malicious spikes. Use AWS WAF rate-based rules to help mitigate these spikes.</li>
<li>If you experience traffic floods, implement additional layers of protection by using CloudFront with DDoS protection.</li>
</ul>
<p>The new dashboard gives you valuable insight into the traffic that reaches your applications and takes the guesswork out of traffic analysis. Using the insights that it provides, you can fine-tune your AWS WAF protections and block threats before they affect availability or data. Analyze the data regularly to help detect potential threats and make informed decisions about optimizing.</p>
<p>As an example, if you see an unexpected spike of traffic, which looks conspicuous in the dashboard compared to historical traffic patterns, from a country where you don’t anticipate traffic originating from, you can create a <a href="https://docs.aws.amazon.com/waf/latest/developerguide/waf-rule-statement-type-geo-match.html" target="_blank" rel="noopener">geographic match rule statement</a> in your web ACL to block this traffic and prevent it from reaching your web application.</p>
<p>The dashboard is a great tool to gain insights and to understand how AWS WAF managed rules help protect your traffic.</p>
<h2>Use case 2: Understand bot traffic during onboarding and fine-tune your bot control rule group </h2>
<p>With <a href="https://docs.aws.amazon.com/waf/latest/developerguide/waf-bot-control.html" target="_blank" rel="noopener">AWS WAF Bot Control</a>, you can monitor, block, or rate limit bots such as scrapers, scanners, crawlers, status monitors, and search engines. If you use the targeted inspection level of the rule group, you can also challenge bots that don’t self-identify, making it harder and more expensive for malicious bots to operate against your website.</p>
<p>On the traffic overview dashboard, under the <strong>Bot Control</strong> overview tab, you can see how much of your current traffic is coming from bots, based on request sampling (if you don’t have Bot Control enabled) and real-time CloudWatch metrics (if you do have Bot Control enabled).</p>
<p>During your onboarding phase, use this dashboard to monitor your traffic and understand how much of it comes from various types of bots. You can use this as a starting point to customize your bot management. For example, you can enable common bot control rule groups in count mode and see if desired traffic is being mislabeled. Then you can add rule exceptions, as described in <a href="https://docs.aws.amazon.com/waf/latest/developerguide/waf-bot-control-example-allow-blocked-bot.html" target="_blank" rel="noopener">AWS WAF Bot Control example: Allow a specific blocked bot</a>.</p>
<p>The following figure shows a collection of widgets that visualize various dimensions of requests detected as generated by bots. By understanding categories and volumes, you can make an informed decision to either investigate by further delving into logs or block a specific category if it’s clear that it’s unwanted traffic.</p>
<div id="attachment_33502" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33502" src="https://infracom.com.sg/wp-content/uploads/2024/03/img4-5.png" alt="Figure 4: Collection of bot-related metrics on the dashboard" width="780" class="size-full wp-image-33502">
<p id="caption-attachment-33502" class="wp-caption-text">Figure 4: Collection of bot-related metrics on the dashboard</p>
</div>
<p>After you get started, you can use the same dashboard to monitor your bot traffic and evaluate adding targeted detection for sophisticated bots that don’t self-identify. Targeted protections use detection techniques such as browser interrogation, fingerprinting, and behavior heuristics to identify bad bot traffic. AWS WAF tokens are an integral part of these enhanced protections.</p>
<p>AWS WAF creates, updates, and encrypts tokens for clients that successfully respond to silent challenges and CAPTCHA puzzles. When a client with a token sends a web request, it includes the encrypted token, and AWS WAF decrypts the token and verifies its contents.</p>
<p>In the Bot Control dashboard, the token status pane shows counts for the various token status labels, paired with the rule action that was applied to the request. The <strong>IP token absent thresholds</strong> pane shows data for requests from IPs that sent too many requests without a token. You can use this information to fine-tune your AWS WAF configuration.</p>
<p>For example, within a Bot Control rule group, it’s possible for a request without a valid token to exit the rule group evaluation and continue to be evaluated by the web ACL. To block requests that are missing their token or for which the token is rejected, you can add a rule to run immediately after the managed rule group to capture <a href="https://docs.aws.amazon.com/waf/latest/developerguide/waf-tokens-block-missing-tokens.html" target="_blank" rel="noopener">and block requests that the rule group doesn’t handle</a> for you. Using the <strong>Token status</strong> pane, illustrated in Figure 5, you can also monitor the volume of requests that acquire tokens and decide if you want to rate limit or block such requests.</p>
<div id="attachment_33503" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33503" src="https://infracom.com.sg/wp-content/uploads/2024/03/img5-4.png" alt="Figure 5: Token status enables monitoring of the volume of requests that acquire tokens" width="780" class="size-full wp-image-33503">
<p id="caption-attachment-33503" class="wp-caption-text">Figure 5: Token status enables monitoring of the volume of requests that acquire tokens</p>
</div>
<h2>Comparison with CloudFront security dashboard</h2>
<p>The AWS WAF traffic overview dashboard provides enhanced overall visibility into web traffic reaching resources that are protected with AWS WAF. In contrast, the <a href="https://aws.amazon.com/blogs/networking-and-content-delivery/introducing-cloudfront-security-dashboard-a-unified-cdn-and-security-experience/" target="_blank" rel="noopener">CloudFront security dashboard</a> brings AWS WAF visibility and controls directly to your CloudFront distribution. If you want the detailed visibility and analysis of patterns that could indicate potential threats or issues, then the AWS WAF traffic overview dashboard is the best fit. However, if your goal is to manage application delivery and security in one place without navigating between service consoles and to gain visibility into your application’s top security trends, allowed and blocked traffic, and bot activity, then the CloudFront security dashboard could be a better option.</p>
<h2>Availability and pricing</h2>
<p>The new dashboards are available in the AWS WAF console, and you can use them to better monitor your traffic. These dashboards are available by default, at no cost, and require no additional setup. CloudWatch logging has a separate pricing model and if you have full logging enabled you will incur CloudWatch charges. <a href="https://aws.amazon.com/cloudwatch/pricing/" target="_blank" rel="noopener">See here</a> for more information about CloudWatch charges. You can customize the dashboards if you want to tailor the displayed data to the needs of your environment.</p>
<h2>Conclusion</h2>
<p>With the AWS WAF traffic overview dashboard, you can get actionable insights on your web security posture and traffic patterns that might need your attention to improve your perimeter protection.</p>
<p>In this post, you learned how to use the dashboard to help secure your web application. You walked through traffic patterns analysis and possible next steps. Additionally, you learned how to observe traffic from bots and follow up with actions related to them according to the needs of your application.</p>
<p>The AWS WAF traffic overview dashboard is designed to meet most use cases and be a go-to default option for security visibility over web traffic. However, if you’d prefer to create a custom solution, see the guidance in the blog post <a href="https://aws.amazon.com/blogs/security/deploy-dashboard-for-aws-waf-minimal-effort/" target="_blank" rel="noopener">Deploy a dashboard for AWS WAF with minimal effort</a>.</p>
<p> <br>If you have feedback about this post, submit comments in the<strong> Comments</strong> section below. If you have questions about this post, <a href="https://console.aws.amazon.com/support/home" target="_blank" rel="noopener noreferrer">contact AWS Support</a>.</p>
<!-- '"` -->
