IAM policy varieties: How so when to use them
You manage gain access to in AWS by creating guidelines and attaching them to AWS Identity and Access Administration (IAM) principals (roles, users, or sets of users) or AWS sources. AWS evaluates these plans when an IAM principal can make a request, such as for example uploading an item to an Amazon Simple Storage Support (Amazon S3) bucket. Permissions in the policies determine if the request is permitted or denied.
<pre> <code> <p>In this website post, we shall walk you by way of a scenario and explain once you should use which plan type, and who should own and manage the plan. Become familiar with when to utilize the more prevalent policy types: identity-based guidelines, resource-based plans, permissions boundaries, and <a href="https://aws.amazon.com/organizations/" focus on="_blank" rel="noopener noreferrer">AWS Businesses</a> support control guidelines (SCPs).</p>
<h2>Various policy types so when to utilize them</h2>
<p>AWS has different plan types offering you with powerful versatility, and it’s vital that you know how so when to utilize each policy kind. It’s also important that you should understand how to framework your IAM policy possession in order to avoid a centralized group from learning to be a bottleneck. Explicit policy possession makes it possible for your teams to go more quickly, while remaining within the safe guardrails that are described centrally.</p>
<h3>Services control policies summary</h3>
<p><a href=”https://docs.aws.amazon.com/businesses/most recent/userguide/orgs_manage_policies_scps.html” focus on=”_blank” rel=”noopener noreferrer”>Service control plans (SCPs)</the> are a function of <a href=”https://aws.amazon.com/organizations/” focus on=”_blank” rel=”noopener noreferrer”>AWS Companies</a>. AWS Agencies is a services for grouping and centrally controlling the AWS accounts your business owns. SCPs are guidelines that specify the utmost permissions for a business, organizational device (OU), or a person accounts. An SCP can control permissions for principals in associate accounts, like the AWS account root consumer.</p>
<p>SCPs are usually meant to be utilized as coarse-grained guardrails, plus they don’t directly grant entry. The principal function of SCPs would be to enforce <em>protection invariants</em> across AWS accounts and OUs within an organization. <em>Protection invariants</em> are handle goals or configurations that you connect with multiple accounts, OUs, or the complete AWS organization. For instance, <a href=”https://docs.aws.amazon.com/organizations/most recent/userguide/orgs_manage_policies_scps_examples_general.html#example-scp-leave-org” target=”_blank” rel=”noopener noreferrer”>you may use an SCP to avoid member accounts from leaving your business</the> or <a href=”https://docs.aws.amazon.com/organizations/most recent/userguide/orgs_manage_policies_scps_examples_general.html#example-scp-deny-region” focus on=”_blank” rel=”noopener noreferrer”>to enforce that AWS assets can only just be deployed to certain Areas</the>.</p>
<h3>Permissions boundaries review</h3>
<p><a href=”https://docs.aws.amazon.com/IAM/latest/UserGuide/access_plans_boundaries.html” focus on=”_blank” rel=”noopener noreferrer”>Permissions boundaries</a> are a sophisticated IAM feature where you set the utmost permissions an identity-based plan can grant to an IAM principal. Once you arranged a permissions boundary for a principal, the principal is capable of doing only the actions which are permitted by both its identity-based guidelines and its own permissions boundaries.</p>
<p>The permissions boundary is really a type of identity-based plan that doesn’t directly grant access. Instead, as an SCP, a permissions boundary functions as a guardrail for the IAM principals which allows one to set coarse-grained accessibility controls. A permissions boundary is normally used to <a href=”https://docs.aws.amazon.com/IAM/current/UserGuide/access_plans_boundaries.html#access_policies_boundaries-delegate” target=”_blank” rel=”noopener noreferrer”>delegate the development of IAM principals</the>. Delegation enables some other people in your accounts to generate fresh IAM principals, but limitations the permissions which can be given to the brand new IAM principals.</p>
<h3>Identity-dependent policies overview</h3>
<p><a href=”https://docs.aws.amazon.com/IAM/latest/UserGuide/access_guidelines_identity-vs-resource.html” focus on=”_blank” rel=”noopener noreferrer”>Identity-centered policies</the> are policy files that you put on a principal (roles, customers, and sets of users) to regulate what activities a principal is capable of doing, on which sources, and under what problems. Identity-based policies could be additional categorized into <a href=”https://docs.aws.amazon.com/IAM/most recent/UserGuide/access_policies_managed-vs-inline.html#aws-managed-policies” focus on=”_blank” rel=”noopener noreferrer”>AWS managed plans</the>, <a href=”https://docs.aws.amazon.com/IAM/most recent/UserGuide/access_policies_managed-vs-inline.html#customer-managed-policies” focus on=”_blank” rel=”noopener noreferrer”>customer managed guidelines</the>, and <a href=”https://docs.aws.amazon.com/IAM/most recent/UserGuide/access_policies_managed-vs-inline.html#inline-policies” focus on=”_blank” rel=”noopener noreferrer”>inline plans</a>. AWS handled guidelines are reusable identity-based plans which are created and maintained by AWS. You may use AWS managed guidelines as a starting place for building your personal identity-based policies which are specific to your company. Customer managed plans are reusable identity-based guidelines that can be mounted on multiple identities. Client managed policies are of help when you have several principals with identical gain access to requirements. Inline plans are identity-based policies which are mounted on a single principal. Make use of inline-policies when you wish to generate least-privilege permissions which are specific to a specific principal.</p>
<p>You should have many identity-based guidelines in your AWS account which are used make it possible for access in scenarios such as for example human access, application access, machine learning workloads, and deployment pipelines. These plans should be fine-grained. You utilize these policies to straight apply minimum privilege permissions to your IAM principals. You need to write the guidelines with permissions for the precise task that the main must accomplish.</p>
<h3>Resource-based plans overview</h3>
<p><a href=”https://docs.aws.amazon.com/IAM/latest/UserGuide/access_guidelines_identity-vs-resource.html” focus on=”_blank” rel=”noopener noreferrer”>Resource-based plans</the> are policy paperwork that you put on a source such as for example an S3 bucket. These guidelines grant the specified principal authorization to perform specific activities on that reference and define under what circumstances this authorization applies. Resource-based plans are inline guidelines. For a summary of AWS solutions that support resource-based plans, observe <a href=”https://docs.aws.amazon.com/IAM/most recent/UserGuide/reference_aws-services-that-work-with-iam.html” focus on=”_blank” rel=”noopener noreferrer”>AWS providers that use IAM</the>.</p>
<p>Resource-based guidelines are optional for most workloads that don’t span several AWS accounts. Fine-grained entry inside a single AWS account is normally granted with identity-based plans. <a href=”https://aws.amazon.com/kms/” focus on=”_blank” rel=”noopener noreferrer”>AWS Key Administration Assistance (AWS KMS)</the> <a href=”https://docs.aws.amazon.com/kms/recent/developerguide/key-policies.html” focus on=”_blank” rel=”noopener noreferrer”>keys</the> and <a href=”https://docs.aws.amazon.com/IAM/best and newest/UserGuide/id_functions_terms-and-concepts.html#phrase_trust-policy” focus on=”_blank” rel=”noopener noreferrer”>IAM role have confidence in policies</the> are usually two exceptions, and both these resources will need to have a resource-based plan even though the main and the KMS essential or IAM role come in the same accounts. IAM functions and KMS keys behave in this manner as an extra coating of protection that will require who owns the resource (important or part) to explicitly permit or deny principals from utilizing the resource. For additional resources that assistance resource-based guidelines, here are a few use cases where they’re most commonly utilized:</p>
<ol>
<li><a href=”https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_plans_evaluation-logic-cross-account.html” focus on=”_blank” rel=”noopener noreferrer”>Granting cross-account usage of your AWS useful resource.</the></li>
<li>Granting an AWS service usage of your resource once the AWS service utilizes an AWS support principal. For example, when working with <a href=”https://www.amazonaws.cn/en/cloudtrail/” focus on=”_blank” rel=”noopener noreferrer”>AWS CloudTrail</a>, you need to <a href=”https://docs.aws.amazon.com/awscloudtrail/most recent/userguide/create-s3-bucket-policy-for-cloudtrail.html” focus on=”_blank” rel=”noopener noreferrer”>explicitly grant the CloudTrail service principal usage of write files to an Amazon S3 bucket</the>.</li>
<li>Using broad access guardrails in order to your AWS assets. You can observe some examples in your blog article <a href=”https://aws.amazon.com/sites/security/iam-makes-it-easier-to-manage-permissions-for-aws-services-accessing-resources/” focus on=”_blank” rel=”noopener noreferrer”>IAM helps it be easier so that you can manage permissions for AWS solutions accessing your sources</the>.</li>
<li>Applying yet another layer of protection with regard to resources that store delicate data, such as for example <a href=”https://aws.amazon.com/secrets-supervisor/” target=”_blank” rel=”noopener noreferrer”>AWS Strategies Manager</the> strategies or an S3 bucket with delicate data. You may use a resource-based plan to deny usage of IAM principals that shouldn’t get access to sensitive information, even if granted accessibility by an identity-based plan. <a href=”https://docs.aws.amazon.com/IAM/most recent/UserGuide/reference_policies_evaluation-logic.html” focus on=”_blank” rel=”noopener noreferrer”>An explicit deny within an IAM policy usually overrides an allow.</the></li>
</ol>
<h2>How exactly to implement different policy sorts</h2>
<p>In this area, we shall walk you via an exemplory case of a design which includes all of the plan types described in this article.</p>
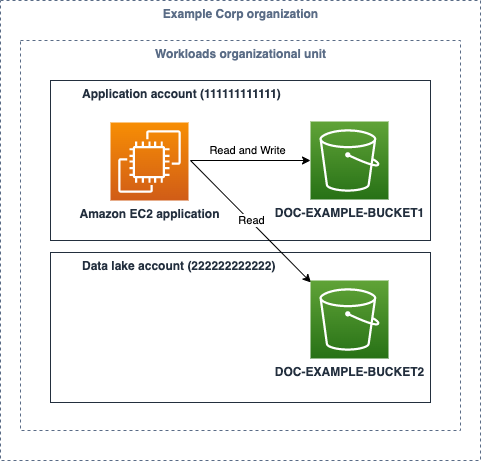
<p>The example that follows shows a credit card applicatoin that runs on an <a href=”http://aws.amazon.com/ec2″ focus on=”_blank” rel=”noopener noreferrer”>Amazon Elastic Compute Cloud (Amazon EC2)</a> example and must read from and create documents to an S3 bucket in exactly the same account. The application furthermore reads (but doesn’t compose) data files from an S3 bucket in another account. The business in this example, Example Corp, runs on the <a href=”https://docs.aws.amazon.com/whitepapers/latest/organizing-your-aws-atmosphere/organizing-your-aws-environment.html” focus on=”_blank” rel=”noopener noreferrer”>multi-accounts strategy</the>, and each software has its AWS accounts. The architecture of the application form is shown in Physique 1.</p>
<div id=”attachment_25372″ course=”wp-caption aligncenter”>
<img aria-describedby=”caption-attachment-25372″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/05/31/picture1-5.png” alt=”Determine 1: Sample program architecture that must access S3 buckets inside two various AWS accounts” width=”481″ height=”461″ course=”size-full wp-picture-25372″>
<p id=”caption-attachment-25372″ course=”wp-caption-text”>Figure 1: Sample app architecture that must access S3 buckets inside 2 different AWS accounts</p>
</div>
<p>You can find three teams that take part in this example: the Central Cloud Team, the application form Team, and the info Lake Team. The Main Cloud Team is in charge of the overall safety and governance of the AWS atmosphere across all AWS accounts at Instance Corp. THE APPLICATION FORM Team is in charge of building, deploying, and operating their software within the application form account (111111111111) they personal and manage. Similarly, the Data Lake Group owns and manages the info lake accounts (222222222222) that hosts a data lake at Illustration Corp.</p>
<p>With that background at heart, we shall walk you via an implementation for every of the four plan types you need to include an explanation which team we recommend own each plan. The policy owner may be the team that is in charge of creating and keeping the policy.</p>
<h3>Program control guidelines</h3>
<p>The Main Cloud Group owns the implementation of the security controls which should apply broadly to all or any of Instance Corp’s AWS accounts. At Example Corp, the Main Cloud Group has two security needs they want to connect with all accounts within their organization:</p>
<ol>
<li>All AWS API phone calls should be encrypted in transit.</li>
<li>Accounts can’t leave the business by themselves.</li>
</ol>
<p>The Main Cloud Group chooses to implement these security invariants making use of SCPs and applies the SCPs to the main of the organization. The initial statement in Policy 1 <a href=”https://docs.aws.amazon.com/IAM/current/UserGuide/reference_plans_condition-keys.html#condition-keys-securetransport” focus on=”_blank” rel=”noopener noreferrer”>denies all requests that aren’t sent making use of SSL (TLS)</the>. The next statement in Policy 1 prevents a merchant account from leaving the business.</p>
<p>That is just a subset of the SCP statements that Illustration Corp uses. Instance Corp runs on the <a href=”https://docs.aws.amazon.com/organizations/recent/userguide/orgs_manage_policies_scps_strategies.html#orgs_guidelines_denylist” focus on=”_blank” rel=”noopener noreferrer”>deny listing strategy</the>, and presently there must be an accompanying declaration with an Aftereffect of Allow at every degree of the business that isn’t demonstrated in the SCP in Plan 1.</p>
<h4>Plan 1: SCP mounted on AWS Organizations corporation root</h4>
<div course=”hide-language”>
<pre><code class=”lang-text”>
“Id”: “ServiceControlPolicy”,
“Version”: “2012-10-17”,
“Statement”: [
“Sid”: “DenyIfRequestIsNotUsingSSL”,
“Effect”: “Deny”,
“Action”: “*”,
“Resource”: “*”,
“Condition”:
“BoolIfExists”:
“aws:SecureTransport”: “false”
,
"Sid": "PreventLeavingTheOrganization",
"Effect": "Deny",
"Action": "organizations:LeaveOrganization",
"Resource": "*"
]
<pre> <code> <h3>Permissions boundary plans</h3>
The Central Cloud Group wants to ensure that they don’t turn into a bottleneck for the application form Team. They would like to allow the Application Group to deploy their very own IAM principals and guidelines for their applications. The Central Cloud Group also wants to be sure that any principals developed by the Application Group can only make use of AWS APIs that the Main Cloud Group has authorized.</p>
<p>At Illustration Corp, the application form Team deploys with their manufacturing AWS environment by way of a <a href=”https://aws.amazon.com/getting-started/hands-on/set-up-ci-cd-pipeline/” target=”_blank” rel=”noopener noreferrer”>continuous integration/constant deployment (CI/CD) pipeline</the>. The pipeline itself provides broad usage of create AWS resources had a need to run programs, including permissions to generate additional IAM functions. The Central Cloud Group implements a handle that requires that IAM roles developed by the pipeline will need to have a permissions boundary connected. This enables the pipeline to generate additional IAM functions, but limitations the permissions that the recently created roles might have to what is permitted by the permissions boundary. This delegation strikes a stability for the Main Cloud Team. They are able to avoid learning to be a bottleneck to the application form Group by allowing the application form Group to create their very own IAM functions and policies, while making certain those IAM functions and policies aren’t overly privileged.</p>
<p>A good example of the permissions boundary policy that the Main Cloud Team attaches to IAM functions developed by the CI/CD pipeline is shown below. This exact same permissions boundary policy could be centrally handled and mounted on IAM roles developed by various other pipelines at Instance Corp. The plan describes the utmost possible permissions that extra roles created by the application form Team are permitted to have, and it limitations those permissions for some Amazon S3 and <a href=”https://aws.amazon.com/sqs/” focus on=”_blank” rel=”noopener noreferrer”>Amazon Basic Queue Provider (Amazon SQS)</the> data access activities. It’s typical for a permissions boundary plan to add data access activities when utilized to delegate function creation. It is because most apps only want permissions to learn and write data (for instance, writing an item to an S3 bucket or reading through a note from an SQS queue) and only sometimes want permission to change infrastructure (for instance, producing an S3 bucket or deleting an SQS queue). As Illustration Corp adopts extra AWS services, the Main Cloud Team up-dates this permissions boundary with activities from those services.</p>
<h4>Plan 2: Permissions boundary plan mounted on IAM roles developed by the CI/CD pipeline</h4>
<div course=”hide-language”>
<pre><code class=”lang-text”>
“Id”: “PermissionsBoundaryPolicy”,
“Version”: “2012-10-17”,
“Statement”: [<br />
“Impact”: “Allow”,<br />
“Action”: [
“s3:PutObject”,
“s3:GetObject”,
“sqs:ChangeMessageVisibility”,
“sqs:DeleteMessage”,
“sqs:ReceiveMessage”,
“sqs:SendMessage”,
“sqs:PurgeQueue”,
“sqs:GetQueueUrl”,
“logs:PutLogEvents”<br />
],<br />
“Source”: “<em>”
]
</em> </code> </pre>
</div>
<p> Within the next section, become familiar with how to enforce that permissions boundary is mounted on IAM roles developed by your CI/CD pipeline. </p>
<h3> Identity-based plans </h3>
<p> In this example, teams at Instance Corp are only permitted to modify the creation AWS atmosphere through their CI/CD pipeline. Write usage of the production environment isn't allowed otherwise. To support the various personas that require to possess access to a credit card applicatoin account in Illustration Corp, three baseline IAM functions with identity-based guidelines are created in the application form accounts: </p>
<ul>
<li> A job for the CI/CD pipeline to utilize to deploy application assets. </li>
<li> A read-only part for the Main Cloud Team, with an activity for temporary elevated gain access to. </li>
<li> A read-only role for users of the application form Team. </li>
</ul>
<p> All three of the baseline functions are owned, maintained, and deployed by the Main Cloud Team. </p>
<p> The Main Cloud Team is provided a default read-only function ( <span> CentralCloudTeamReadonlyRole </span> ) which allows read usage of all sources within the account. That is achieved by attaching the <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_managed-vs-inline.html" target="_blank" rel="noopener noreferrer"> AWS handled ReadOnlyAccess plan </a> to the Central Cloud Team part. You may use the <a href="https://console.aws.amazon.com/iam/home#policies/arn:aws:iam::aws:policy/ReadOnlyAccess" target="_blank" rel="noopener noreferrer"> IAM console to add the ReadOnlyAccess plan </a> , which grants read-only usage of all services. When a person in the team must perform an action that's not included in this policy, they adhere to a <a href="https://aws.amazon.com/blogs/security/managing-temporary-elevated-access-to-your-aws-environment/" target="_blank" rel="noopener noreferrer"> short-term elevated access procedure </a> to ensure that this access will be valid and documented. </p>
<p> A read-only role can be directed at developers in the application form Group ( <span> DeveloperReadOnlyRole </span> ) for evaluation and troubleshooting. At Instance Corp, developers are permitted to have read-only usage of Amazon EC2, Amazon S3, Amazon SQS, <a href="https://aws.amazon.com/cloudformation/" target="_blank" rel="noopener noreferrer"> AWS CloudFormation </a> , and <a href="https://aws.amazon.com/cloudwatch/" target="_blank" rel="noopener noreferrer"> Amazon CloudWatch </a> . The needs you have for read-only entry might differ. Several AWS services offer you their very own read-only managed plans, and addititionally there is the earlier mentioned <a href="https://console.aws.amazon.com/iam/home#policies/arn:aws:iam::aws:policy/ReadOnlyAccess" target="_blank" rel="noopener noreferrer"> AWS maintained ReadOnlyAccess plan </a> that grants read only usage of all providers. To customize read-only accessibility within an identity-based policy, you may use the AWS handled guidelines as a starting place and limit what to the services your firm uses. The personalized identity-based policy for instance Corp’s <span> DeveloperReadOnlyRole </span> function is proven below. </p>
<h4> Policy 3: Identity-based policy mounted on a developer read-only part to support human gain access to and troubleshooting </h4>
<div class="hide-language">
<pre> <code class="lang-text">
"Id": "DeveloperRoleBaselinePolicy",
"Version": "2012-10-17",
"Statement": [
"Effect": "Allow",
"Action": [
"cloudformation:Describe",
"cloudformation:Obtain <em> ",
"cloudformation:Listing </em> ",
"cloudwatch:Describe <em> ",
"cloudwatch:Obtain </em> ",
"cloudwatch:Listing <em> ",
"ec2:Describe </em> ",
"ec2:Obtain <em> ",
"ec2:Listing </em> ",
"ec2:Research <em> ",
"s3:Describe </em> ",
"s3:Obtain <em> ",
"s3:Listing </em> ",
"sqs:Obtain <em> ",
"sqs:Listing </em> ",
"logs:Describe <em> ",
"logs:FilterLogEvents",
"logs:Obtain </em> ",
"logs:Listing <em> ",
"logs:StartQuery",
"logs:StopQuery"
],
"Resource": " </em> "
]
</code> </pre>
</div>
<p> The CI/CD pipeline function has broad usage of the account to generate resources. Usage of deploy through the CI/CD pipeline ought to be firmly controlled and monitored. The CI/CD pipeline will be allowed to create brand-new IAM roles for make use of with the application form, but those functions are limited by only what allowed by the formerly talked about permissions boundary. The functions, policies, and EC2 example profiles that the pipeline produces should also be limited to particular <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_identifiers.html#identifiers-friendly-names" target="_blank" rel="noopener noreferrer"> part paths </a> . This permits one to enforce that the pipeline can only just modify roles and plans or <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_use_passrole.html" target="_blank" rel="noopener noreferrer"> move functions </a> that it has generated. This helps avoid the pipeline, and functions developed by the pipeline, from elevating privileges by modifying or moving a far more privileged role. Pay out attention to the function and plan paths in the Reference element of the next CI/CD pipeline part policy (Plan 4). The CI/CD pipeline role policy furthermore provides some instance statements that permit the passing and development of a limited group of <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/using-service-linked-roles.html" target="_blank" rel="noopener noreferrer"> service-linked functions </a> (which are manufactured in the road <span> /aws-service-function/ </span> ). You can include other service-linked functions to these statements as your company adopts additional AWS solutions. </p>
<h4> Policy 4: Identity-based policy mounted on CI/CD pipeline part </h4>
<div class="hide-language">
<pre> <code class="lang-text">
<span> "Id" </span> : <span> "CICDPipelineBaselinePolicy" </span> ,
<span> "Edition" </span> : <span> "2012-10-17" </span> ,
<span> "Declaration" </span> : [
<span> "Impact" </span> : <span> "Allow" </span> , <br />
<span> "Actions" </span> : [
<span> "ec2: <em> " </em> </span> ,
<span> "sqs:" </span> ,
<span> "s3: <em> " </em> </span> ,
<span> "cloudwatch:" </span> ,
<span> "cloudformation: <em> " </em> </span> ,
<span> "logs:" </span> ,
<span> "autoscaling: <em> " </em> </span> <br />
],
<span> "Useful resource" </span> : <span> "" </span>
,
<span> "Impact" </span> : <span> "Allow" </span> ,
<span> "Activity" </span> : <span> "ssm:GetParameter <em> " </em> </span> ,
<span> "Source" </span> : <span> "arn:aws:ssm:::parameter/aws/assistance/ <em> " </em> </span>
,
<span> "Impact" </span> : <span> "Allow" </span> ,
<span> "Motion" </span> : [
<span> "iam:CreateRole" </span> ,
<span> "iam:PutRolePolicy" </span> ,
<span> "iam:DeleteRolePolicy" </span>
],
<span> "Reference" </span> : <span> "arn:aws:iam::111111111111:role/application-functions/" </span> ,
<span> "Situation" </span> :
<span> "ArnEquals" </span> :
<span> "iam:PermissionsBoundary" </span> : <span> "arn:aws:iam::111111111111:plan/PermissionsBoundary" </span>
<br />
,
<span> "Impact" </span> : <span> "Allow" </span> ,
<span> "Actions" </span> : [
<span> "iam:AttachRolePolicy" </span> ,
<span> "iam:DetachRolePolicy" </span>
],
<span> "Useful resource" </span> : <span> "arn:aws:iam::111111111111:role/application-functions/ <em> " </em> </span> ,
<span> "Problem" </span> :
<span> "ArnEquals" </span> :
<span> "iam:PermissionsBoundary" </span> : <span> "arn:aws:iam::111111111111:plan/PermissionsBoundary" </span>
,
<span> "ArnLike" </span> :
<span> "iam:PolicyARN" </span> : <span> "arn:aws:iam::111111111111:policy/application-role-guidelines/" </span>
<br />
,
<span> "Impact" </span> : <span> "Allow" </span> ,
<span> "Activity" </span> : [
<span> "iam:DeleteRole" </span> ,
<span> "iam:TagRole" </span> ,
<span> "iam:UntagRole" </span> ,
<span> "iam:GetRole" </span> ,
<span> "iam:GetRolePolicy" </span>
],
<span> "Source" </span> : <span> "arn:aws:iam::111111111111:role/application-functions/*" </span>
,
<pre> <code>
<span>"Impact"</period>: <period>"Allow"</period>,
<span>"Motion"</span>: [
<period>"iam:CreatePolicy"</span>,
<period>"iam:DeletePolicy"</span>,
<period>"iam:CreatePolicyVersion"</span>,
<period>"iam:DeletePolicyVersion"</span>,
<period>"iam:GetPolicy"</span>,
<period>"iam:TagPolicy"</span>,
<period>"iam:UntagPolicy"</span>,
<period>"iam:SetDefaultPolicyVersion"</span>,
<period>"iam:ListPolicyVersions"</span>
],
<span>"Reference"</period>: <period>"arn:aws:iam::111111111111:policy/application-role-plans/*"</span>
,
<span>"Impact"</period>: <period>"Allow"</period>,
<span>"Actions"</span>: [
<period>"iam:CreateInstanceProfile"</span>,
<period>"iam:AddRoleToInstanceProfile"</span>,
<period>"iam:RemoveRoleFromInstanceProfile"</span>,
<period>"iam:DeleteInstanceProfile"</span>
],
<span>"Useful resource"</period>: <period>"arn:aws:iam::111111111111:instance-profile/application-instance-profiles/*"</span>
,
<span>"Impact"</period>: <period>"Allow"</period>,
<span>"Activity"</period>: <period>"iam:PassRole"</span>,
<span>"Source"</span>: [
<period>"arn:aws:iam::111111111111:role/application-functions/*"</span>,
<period>"arn:aws:iam::111111111111:role/aws-service-function/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling*"</span>
]
,
<span>"Impact"</period>: <period>"Allow"</period>,
<span>"Motion"</period>: <period>"iam:CreateServiceLinkedRole"</span>,
<span>"Reference"</period>: <period>"arn:aws:iam::111111111111:role/aws-service-part/*"</span>,
<span>"Situation"</span>:
<period>"StringEquals"</period>:
<period>"iam:AWSServiceName"</span>: <period>"autoscaling.amazonaws.com"</span>
,
<span>"Impact"</period>: <period>"Allow"</period>,
<span>"Actions"</span>: [
<period>"iam:DeleteServiceLinkedRole"</span>,
<period>"iam:GetServiceLinkedRoleDeletionStatus"</span>
],
<span>"Useful resource"</period>: <period>"arn:aws:iam::111111111111:role/aws-service-function/autoscaling.amazonaws.com/AWSServiceRoleForAutoScaling*"</span>
,
<span>"Impact"</period>: <period>"Allow"</period>,
<span>"Activity"</period>: <period>"iam:ListRoles"</span>,
<span>"Source"</period>: <period>"*"</period>
,
<span>"Impact"</period>: <period>"Allow"</period>,
<span>"Motion"</period>: <period>"iam:GetRole"</span>,
<span>"Reference"</span>: [
<period>"arn:aws:iam::111111111111:role/application-functions/*"</span>,
<period>"arn:aws:iam::111111111111:role/aws-service-part/*"</span>
]
]
</code> </pre>
</div>
<p> As well as the three baseline functions with identity-based policies set up that you’ve seen up to now, there’s one extra IAM function that the application form Team creates utilizing the CI/CD pipeline. This is actually the part that the application working on the EC2 instance use to obtain and put items from the S3 buckets in Number 1. Explicit possession allows the application form Team to generate this identity-based plan that fits their requirements without needing to wait and be determined by the Central Cloud Group. As the CI/CD pipeline can only just create roles which have the permissions boundary plan attached, Plan 5 cannot grant even more access compared to the permissions boundary plan allows (Plan 2). </p>
<p> In the event that you evaluate the identity-based policy mounted on the EC2 instance’s function (Plan 5 on remaining) with the permissions boundary plan described previously (Plan 2 on the proper), you can observe that the actions permitted by the EC2 instance’s role may also be permitted by the permissions boundary plan. Actions must be permitted by both guidelines for the EC2 example to execute the <span> s3:GetObject </span> and <span> s3:PutObject </span> actions. Access to develop a bucket will be denied even though the role mounted on the EC2 example was given permission to execute the <span> s3:CreateBucket </span> action as the <span> s3:CreateBucket </span> actions exceeds the permissions permitted by the permissions boundary. </p>
<table width="100%">
<tbody>
<tr>
<td width="50%"> Policy 5: Identity-based plan bound by permissions boundary and mounted on the application’s EC2 example
<div class="hide-language">
<pre> <code class="lang-text">
“Id”: “ApplicationRolePolicy”,
“Version”: “2012-10-17”,
“Statement”: [
“Impact”: “Allow”,
“Action”: [
“s3:PutObject”,
“s3:GetObject”
],
“Useful resource”: “arn:aws:s3:::DOC-EXAMPLE-
BUCKET1/ ”
,
“Impact”: “Allow”,
“Action”: [
“s3:GetObject”
],
“Source”: “arn:aws:s3:::DOC-EXAMPLE-
BUCKET2/ ”
]
Policy 2: Permissions boundary policy mounted on IAM roles developed by the CI/CD pipeline.
“Impact”: “Allow”,
“Action”: [ “s3:PutObject”, “s3:GetObject”, “sqs:ChangeMessageVisibility”, “sqs:DeleteMessage”, “sqs:ReceiveMessage”, “sqs:SendMessage”, “sqs:PurgeQueue”, “sqs:GetQueueUrl”, “logs:PutLogEvents”
],
“Resource”: ” ” ]
Resource-based plans
The only real resource-based plan needed in this illustration is mounted on the bucket in the accounts exterior to the application form account (DOC-EXAMPLE-BUCKET2 in the info lake account in Shape 1). Both identity-based plan and resource-based plan must grant usage of an activity on the S3 bucket for usage of be permitted in a cross-account situation . The bucket policy below just enables the GetObject motion to end up being performed on the bucket, whatever permissions the application’s part ( ApplicationRole ) is given from its identity-based plan (Plan 5).
This resource-based plan is possessed by the info Lake Group that owns and manages the info lake accounts (222222222222) and the plan (Policy 6). This enables the info Lake Team to possess complete handle over what teams exterior with their AWS account can entry their S3 bucket.
Policy 6: Resource-based policy mounted on S3 bucket in exterior data lake account (222222222222)
“Action”: [ “s3:GetObject” ],
“Reference”: “arn:aws:s3:::DOC-EXAMPLE-BUCKET2/” ]
No resource-based policy is necessary on the S3 bucket in the application form account (DOC-EXAMPLE-BUCKET1 in Body 1). Entry for the application form is given to the S3 bucket in the application form accounts by the identity-based plan alone. Access can be given by either an identity-based policy or perhaps a resource-based plan when access is at the same AWS accounts.
Putting everything together
Figure 2 displays the architecture and consists of the seven various policies and the assets they are mounted on. The table that comes after summarizes the many IAM policies which are deployed to the Illustration Corp AWS atmosphere, and specifies what group is responsible for each one of the policies.

Figure 2: Sample program architecture with CI/CD pipeline utilized to deploy infrastructure
The numbered policies in Figure 2 match the policy figures in the next table.
Policy quantity
Policy explanation
Policy kind
Policy proprietor
Mounted on
1
Enforce SSL and stop member accounts from leaving behind the organization for several principals in the business
Service handle policy (SCP)
Main Cloud Team
Business root
2
Restrict optimum permissions for roles developed by CI/CD pipeline
Permissions boundary
Main Cloud Team
All functions developed by the pipeline ( ApplicationRole )
3
Scoped read-only plan
Identity-based plan
Main Cloud Team
DeveloperReadOnlyRole IAM role
4
CI/CD pipeline plan
Identity-based plan
Main Cloud Team
CICDPipelineRole IAM role
5
Policy utilized by running application to learn and create to S3 buckets
Identity-based plan
Application Group
ApplicationRole on EC2 example
6
Bucket plan in data lake accounts that grants usage of a job in application accounts
Resource-based plan
Information Lake Team
S3 Bucket in data lake accounts
7
Wide read-only policy
Identity-based plan
Main Cloud Team
CentralCloudTeamReadonlyRole IAM role
Conclusion
In this website post, you learned all about four different plan types: identity-based guidelines, resource-based policies, service handle plans (SCPs), and permissions boundary guidelines. You saw types of circumstances where each policy kind is commonly applied. Then, you walked by way of a real-life instance that describes an execution that uses these plan types.
You may use this blog write-up as a starting place for building your organization’s IAM strategy. You may decide that you don’t need all the policy types explained in this article, and that’s OK. Don’t assume all organization must use every policy kind. You may want to implement policies in a different way in a production atmosphere when compared to a sandbox environment. The important ideas to eliminate from this post will be the circumstances where each policy kind is applicable, and the significance of explicit policy possession. We also recommend benefiting from plan validation in AWS IAM Accessibility Analyzer when writing IAM plans to validate your guidelines against IAM plan grammar and guidelines.
To find out more, including the plans described in this answer and the sample app, start to see the how-and-when-to-use-aws-iam-policy-blog-samples GitHub respository. The repository walks via an example implementation utilizing a CI/CD pipeline with AWS CodePipeline .
In case you have any questions, please blog post them in the AWS Identification and Access Administration re:Post subject or get in touch with AWS Help .
Want more AWS Safety news? Adhere to us on Twitter .
<pre> <code> <!-- '"` -->
</code> </pre>

You must be logged in to post a comment.