IAM helps it be easier so that you can manage permissions for AWS providers accessing your resources
Amazon Internet Services (AWS) clients are usually storing an unprecedented quantity of information on AWS for a variety of use cases, including information analytics and lakes, machine learning, and business applications. Customers protected their information by implementing data protection controls including accessibility and identity management, network safety, and encryption. For non-public, sensitive data, clients want to ensure that it’s only obtainable by authorized customers from known locations. Clients implement identity and system based data loss avoidance controls to make sure that usage of sensitive data is fixed to reliable identities, such as for example your authorized corporate customers, and expected network areas, such as for example your corporate system or your Amazon VPC. Some AWS services have to access your sources using their very own identities and from beyond your network places. In this article, we show ways to make use of aws:PrincipalIsAWSService , a fresh worldwide AWS Identification and Access Administration (IAM) condition crucial , to create policies that restrict usage of your computer data from untrusted identities and unforeseen network locations while properly granting usage of AWS solutions. We discuss how exactly to utilize the new condition essential, provide sample plans that show its use, and show ways to incorporate it into your organization’s data security technique. <h2>New global IAM condition important</h2>
aws:PrincipalIsAWSService is really a worldwide IAM condition crucial that simplifies resource-centered policies (such as for example an Amazon S3 bucket plan) when granting usage of AWS services. It offers you a shorthand for enabling AWS services to gain access to your resources and will be utilized alongside other desired limitations, such as restricting usage of your networks. Because the purpose of this problem key would be to simplify how AWS providers connect to your resources, the examples in this article cover resource-dependent policies primarily. We make use of AWS CloudTrail to illustrate how this problem key may be used. With CloudTrail, it is possible to log, monitor continuously, and retain account action linked to activities across your AWS infrastructure. CloudTrail enables you to develop a trail, enabling continuous delivery of activities as log data files to an Amazon Basic Storage Services (Amazon S3) bucket that you specify. Look at a scenario where you intend to allow CloudTrail to create information to your S3 bucket straight from its service accounts but additionally want to make sure that all other gain access to from your identities is fixed to your system, such as for example your Amazon VPC, as illustrated in Figure 1.

Figure 1: Access from trusted system and from CloudTrail
The brand new aws:PrincipalIsAWSService condition essential may be used to put into action a bucket plan that limits usage of your information from your own VPC while safely granting usage of an AWS program, such as for example CloudTrail. Replace <my-logs-bucket>, <AccountNumber>, and <vpc-111bbb22> together with your details in the following illustration.
<CloudTrail regular cross accounts bucket policy configuration>
… "Sid":"expected-network+service-principal",
"Effect":"Deny",
"Principal":"*",
"Action":[
"s3:PutObject*",
"s3:GetObject*",
"s3:ListBucket"
],
"Reference":"arn:aws:s3:::<em><period><period><my-logs-bucket></span></period></em>/AWSLogs/<em><period><period><AccountNumber></period></period></em>/*",
"Condition":
"StringNotEquals":
"aws:SourceVpc":"<em><period><period><vpc-111bbb22></period></period></em>"
,
"Bool":
"aws:PrincipalIsAWSService":"false"
The aforementioned policy statement limitations s3:PutObject and s3:GetObject activities to the VPC while exempting AWS solutions from this situation. The <period>aws:PrincipalIsAWSService</span> condition important works together with <a href="https://docs.aws.amazon.com/IAM/newest/UserGuide/reference_policies_elements_condition_operators.html#Circumstances_Boolean" focus on="_blank" rel="noopener noreferrer">Boolean condition operators</a> that restrict access predicated on comparing an integral to false or real. In the preceding declaration, usage of the bucket that contains CloudTrail data is fixed unless the request hails from the specified VPC (<em><period><period><vpc-111bbb22></period></period></em>) or from an AWS provider (CloudTrail in cases like this).</p>
Notice: the entire policy, including the essential Enable statements for cross-account access, is covered in this article later.
aws:PrincipalIsAWSService within a information perimeter
You have find out about the brand new < just;period>aws:PrincipalIsAWSService global problem key and its own basic usage. Continue reading to learn ways to utilize the new condition essential to determine a data perimeter. Put simply, a information perimeter is a group of preventive guardrails that means that only clients’ identities are usually accessing their own information in the cloud from anticipated network locations. Among the key information perimeter controls would be to configure your assets to be accessible just by trusted identities and from anticipated network areas. Let’s assume you have got sensitive information stored within an S3 bucket. Within establishing a information perimeter, you would like to restrict usage of that data to system locations-like as your VPC or on-premises network. Let’s observe how it is possible to restrict access predicated on four common information access patterns while safely exempting AWS providers that should also access your sources from beyond your network. Knowing the various data access designs shall help you realize when and how exactly to utilize this new condition key, and also other IAM situation keys, to exempt AWS services securely.
1. Immediate access of one’s identities to information
The standard data access pattern is when among your IAM principals (roles or users) from your own AWS account straight accesses data in a S3 bucket. For instance, a user logs into the AWS Management Gaming console to upload an item to an S3 bucket as proven in Body 2.

Figure 2: Immediate access of one’s identities to data (information access design 1)
With this particular access pattern, your bucket policy can constrain the permissions you have given as follows already. Replace <my-data-bucket> and <203.0.113.0/24> together with your information.
“Version”:”2012-10-17″,
“Id”:”S3BucketPolicyId1″,
“Statement”:[
"Sid":"expected-network",
"Effect":"Deny",
"Principal":" ",
"Action":[
"s3:ListBucket",
"s3:PutObject ",
"s3:GetObject "
],
"Resource":[
"arn:aws:s3::: <my-data-bucket> ",
"arn:aws:s3::: <my-data-bucket> / "
],
"Condition":
"NotIpAddress":
"aws:SourceIp":" <203.0.113.0/24> "
]
With the aws:SourceIp problem in the preceding plan, users are denied usage of list, put, and obtain items in or from the S3 bucket unless the API contact originates from of their corporate network.
Take note: This and subsequent examples work with a Deny declaration to constrain the permissions you have previously granted to greatly help illustrate a highly effective data perimeter plan. The principals additionally require an identity-based plan with the correct Allow permissions to create to the bucket, which isn’t depicted in the examples. Likewise, for cross-account access, suitable Allow statements should be put into the bucket plan for certified principals.
The plans add a subset of s3 data access actions rather than s3: to avoid unintentional lockout from your own bucket, that could occur if you edit bucket guidelines beyond your specified network places. You might consider expanding the activity list to add other actions such as for example DeleteObject , RestoreObject , or PutBucketPolicy , based on your requirements, as well as s3: so long as you is capable of doing all actions from inside your defined system perimeter.
2. Immediate access to data through an AWS support
This 2nd access pattern applies once you access the info via an AWS services and that assistance takes subsequent actions with respect to the IAM principal. A standard exemplory case of this access design is usually Amazon Athena . Athena can be an interactive query program that enables you to use regular SQL to query information in Amazon S3. To keep the preceding instance, let’s assume you need to restrict customers from accessing the S3 bucket unless the API contact originates from of their corporate network but additionally permit them to query the info via Athena as demonstrated in Amount 3.

Figure 3: Immediate access to data through an AWS service (information access design 2)
The bucket policy in the last example prevents the power of customers to query the info with Athena, because the phone calls to Amazon S3 are produced from the Athena service rather than from your own corporate network. To take into account this access pattern, it is possible to update your bucket plan by adding the problem crucial aws:CalledViaFirst to StringNotEquals , as proven in the next example:
We’ve a Deny declaration with two negated situation keys now. Which means that both circumstances must resolve to genuine to result in the Deny impact. The problem declaration in the preceding plan now reads the following: deny the three S3 actions unless they result from your corporate system ( NotIpAddress with aws:SourceIp ) or via the Athena provider ( StringNotEquals with aws:CalledViaFirst ). We have been making use of aws:CalledViaFirst (an individual value key) rather than aws:CalledVia (a multivalued key), just because a single worth key is simpler to cause about when used in combination with a StringNotEquals problem. For more information on how best to make use of aws:CalledViaFirst (and aws:CalledVia ), notice How exactly to define least-privileged permissions for activities called by AWS solutions . See furthermore Developing a condition with several keys or ideals for additional information on the assessment logic.
3. Intermediate IAM roles for information access
A 3rd common pattern is by using an AWS service function . In this scenario, confirmed AWS support assumes a ongoing services role that you intended to perform actions in your stead. Since the AWS assistance is utilizing a service role than implementing on the principal’s behalf rather, you cannot utilize the aws:CalledViaFirst condition essential from the prior example. This access design has two variations that will regulate how we grant AWS providers access to your assets.
3a. API call hails from your VPC
The foremost is once the API call hails from within your expected system, such as for example within your VPC. Among that is AWS Glue . AWS Glue is really a serverless information integration service that means it is easier to discover, get ready, and combine information for analytics, device learning, and application growth. To continue more with the preceding illustration, let’s assume you wish to restrict customers from accessing the info in your S3 bucket unless the API contact originates from inside your corporate network but additionally allow them to utilize AWS Glue to crawl the info to upgrade the schema in the AWS Glue Information Catalog. In the entire situation of AWS Glue, it is possible to configure the crawler to utilize your system with system link with Amazon S3 by specifying the required VPC ID, subnet IDs, and security team as shown in Physique 4.

Figure 4: Intermediate IAM roles for data access from customer’s VPC (data access pattern 3a)
With this particular pattern, you merely extend your computer data perimeter to add your VPC network with the addition of the aws:SourceVpc condition to StringNotEquals , as shown in the next example. Replace each <placeholder> together with your values.
The preceding policy adds the aws:SourceVPC condition in exactly the same block because the aws:CalledViaFirst condition that has been added earlier. We’ve a Deny statement with three negated condition keys now. Which means that all three conditions must resolve to true to trigger the Deny effect. Therefore, a call is denied by this policy to Amazon S3 only when the call will not result from your on-premises network, isn’t made via the Athena service, and will not result from your VPC network.
3b. API call hails from beyond your VPC
Although some AWS services that work with a service role access your resources directly from your own VPC such as for example AWS Glue, there’s another variation of the access pattern whenever a service role must access the data within an S3 bucket from beyond your VPC. Among this type of pattern is Amazon Translate asynchronous batch processing. Amazon Translate is really a text translation service that uses advanced machine learning technologies to supply high-quality translation on demand. To translate large collections of documents, you should use the Amazon Translate asynchronous batch processing operation to translate documents stored within an S3 bucket. In the event that you apply the preceding bucket policy, the translate job will fail with a no read access error. This is really because the calls to Amazon S3 are created by Amazon Translate from outside the VPC. That is shown in Figure 5.

Figure 5: Intermediate IAM roles for data access from beyond Customer’s VPC (data access pattern 3b)
To take into account this access pattern, it is possible to update your bucket policy to add the aws:PrincipalArn condition key within the StringNotEquals statement as shown in the next example. Replace each <placeholder> together with your values.
With the preceding policy, you’re effectively excluding the Amazon Translate service role- <AmazonTranslateServiceRole-myjobs> -associated with the translation job from the SourceVpc and SourceIp restrictions. You may make this exception as the Amazon Translate service role is configured with a trust policy which allows only the Amazon Translate service to assume it-only translate.amazonaws.com can assume the role. This is a best practice to use the principle of least privilege to make sure that only authorized users are permitted to modify the trust policy of the role also to pass the role within translation job configuration.
4. AWS services with immediate access to your resources
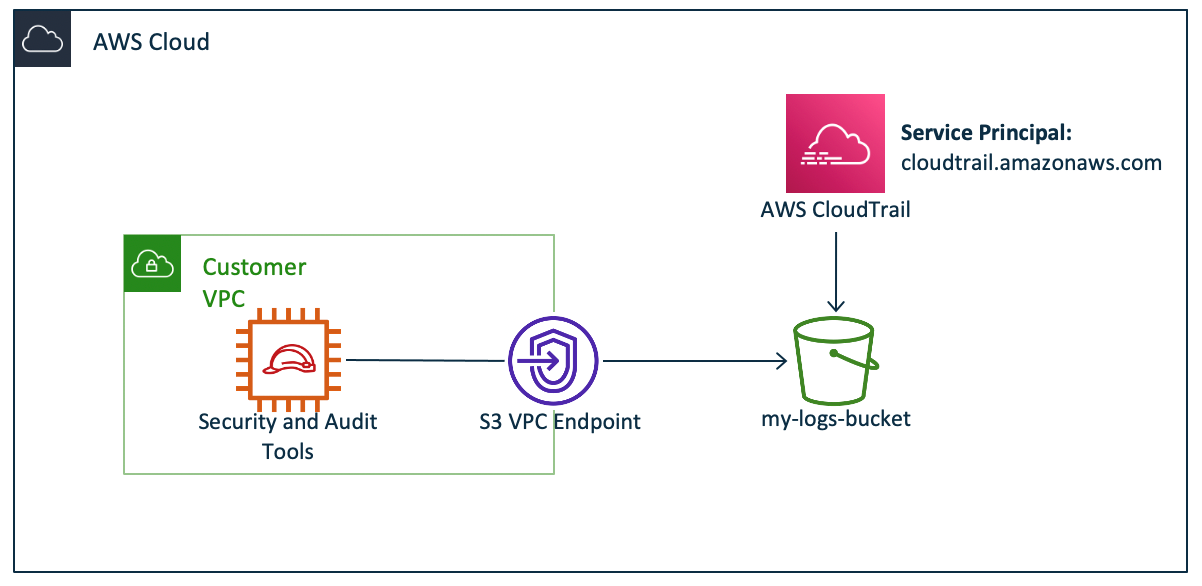
In the last three examples, data in the bucket is accessed by your trusted identity directly, directly via an AWS service (Athena), or by way of a trusted intermediary service role (AWS Glue and Amazon Translate). However, there’s one final access pattern where in fact the AWS service uses its identity-a service principal -to perform an action with respect to the customer. Among this access pattern may be the CloudTrail use case we introduced in the beginning of this post, shown in Figure 6.

Figure 6: AWS services with immediate access to your resources (data access pattern 4)
Let’s assume your computer data perimeter objective would be to restrict usage of the logs in your S3 bucket from either your VPC or the CloudTrail service. If you craft a bucket policy that restricts usage of only your VPC using aws:SourceVpc condition alone, you prevent CloudTrail from writing data to your bucket effectively. You cannot use aws:CalledViaFirst to exclude CloudTrail as shown in data access pattern #2 above because CloudTrail is which consists of own service principal to create data to your bucket (Note: although within the CalledVia condition additionally you specify something principal, such as for example athena.amazonaws.com, CalledVia only applies once the ongoing service is implementing with respect to the calling principal, instead of CloudTrail, where in fact the service is directly writing data to your bucket). Additionally you cannot use aws:PrincipalArn as shown in data access pattern #3b because CloudTrail runs on the service principal rather than an ARN. With the addition of the brand new aws:PrincipalIsAWSService condition to your bucket policy, it is possible to reach your data objective the following perimeter. Replace each <placeholder> together with your values.
The initial two Allow statements in the preceding bucket policy are area of the standard cross account bucket policy configuration for CloudTrail . The final statement- expected-network+service-principal -uses a variety of aws:SourceVpc and the newly launched aws:PrincipalIsAWSService conditions to deny access unless the decision hails from your VPC network, or is manufactured by an AWS service principal, such as for example CloudTrail.
Data perimeter policy for common data access patterns
Given that you have reviewed the normal data access patterns and different IAM condition keys, like the new aws:PrincipalIsAWSService , let’s look at a data perimeter policy. This sample policy could be appended to all of one’s buckets or other resource based policies. Replace each <placeholder> together with your values.
Note: appending policies to existing resources could cause an unintended disruption to the application. Consider testing your policies in lower environments before applying them to production resources.
The preceding policy includes two statements. The initial statement- network-data-perimeter -sets the expected network data perimeter. Let’s examine every one of the condition elements in this statement:
| Condition key | Usage | Example data access pattern |
| aws:SourceIp | Use to restrict usage of public IP ranges of one’s expected network once the request doesn’t originate over a VPC endpoint. | Console access from an on-premises corporate network as discussed in data access pattern #1. |
| aws:SourceVpc | Use to restrict usage of specific VPC IDs of one’s expected network if the request originates over a VPC endpoint. | A credit card applicatoin running on Amazon Elastic Compute Cloud (Amazon EC2) instance utilizing an instance profile, a Lambda function deployed inside a VPC, or an AWS Glue crawler configured with VPC network connection as discussed previously in data access pattern #3a. |
| aws:PrincipalArn | Lets you exclude a principal, like a service role for an AWS service once the request doesn’t result from your network. | Amazon Translate in data access pattern #3b. |
| aws:PrincipalIsAWSService | Offers a straightforward solution to allow usage of an AWS service once the service uses its service principal to gain access to your bucket from its network. Can’t be used once the AWS service makes a request with respect to the IAM principal (such as for example in data access pattern #2, then you need to use aws:CalledVia instead). | CloudTrail in data access pattern #4. |
| aws:ViaAWSService | This problem key is comparable to aws:CalledVia and aws:CalledViaFirst , but rather of being limited by a particular AWS service (i.e. Athena), it could be used to permit or deny usage of any AWS service (hence it’s either set to true or false) which makes a request with respect to the IAM principal to gain access to your resources as discussed in data access pattern #2.
You typically wouldn’t use aws:CalledVia and aws:ViaAWSService in exactly the same bucket policy. Instead, use aws:CalledVia for policies scoped to a particular AWS service and aws:ViaAWSService when you wish to permit or deny any AWS service which makes a request with respect to the IAM principal. |
Amazon Athena in data access pattern 2. |
The next statement- identity-data-perimeter -in the preceding policy sets the trusted identity data perimeter. Let’s examine both conditions in this statement:
| Condition key | Usage | Data access pattern |
| aws:PrincipalOrgID | Restricts usage of trusted principals that participate in your AWS Organizations . Start to see the blog post A less strenuous way to control usage of AWS resources utilizing the AWS organization of IAM principals for additional use cases because of this powerful condition key. | Found in resource based policies such as for example bucket policies and VPC endpoint policies. |
| aws:PrincipalIsAWSService | Like the first statement in the preceding policy, you should use this condition key to permit AWS service to gain access to your bucket from its network which consists of own service principal. | CloudTrail in data access pattern #4. |
Next steps
The newly launched aws:PrincipalIsAWSService condition key simplifies resource-based policies by giving a straightforward solution to limit usage of trusted identities and expected networks while at the same time granting usage of AWS services that use their very own service principal from beyond your network locations. You can even utilize this condition key within an easy data perimeter strategy over the common data access patterns we discussed in this website post. When you have any relevant questions, comments, or concerns, contact AWS Support or take up a new thread on the AWS Identity and Access Management forum .
Thanks for reading concerning this new feature. When you have feedback concerning this post, submit comments in the Comments section below.
Want more AWS Security how-to content, news, and show announcements? Follow us on Twitter .

You must be logged in to post a comment.