How to use Regional AWS STS endpoints
This blog post provides recommendations that you can use to help improve resiliency in the unlikely event of disrupted availability of the global (now legacy) AWS Security Token Service (AWS STS) endpoint. Although the global (legacy) AWS STS endpoint https://sts.amazonaws.com is highly available, it’s hosted in a single AWS Region—US East (N. Virginia)—and like other endpoints, it doesn’t provide automatic failover to endpoints in other Regions. In this post I will show you how to use Regional AWS STS endpoints in your configurations to improve the performance and resiliency of your workloads.
<p>For authentication, it’s best to <a href="https://docs.aws.amazon.com/wellarchitected/latest/framework/sec_identities_unique.html" target="_blank" rel="noopener">use temporary credentials</a> instead of long-term credentials to help reduce risks, such as inadvertent disclosure, sharing, or theft of credentials. With AWS STS, trusted users can request temporary, limited-privilege credentials to <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp.html#sts-introduction" target="_blank" rel="noopener">access AWS resources</a>.</p>
<p>Temporary credentials include an access key pair and a session token. The access key pair consists of an access key ID and a secret key. AWS STS generates temporary security credentials dynamically and provides them to the user when requested, which eliminates the need for long-term storage. Temporary security credentials have a limited lifetime so you don’t have to manage or rotate them.</p>
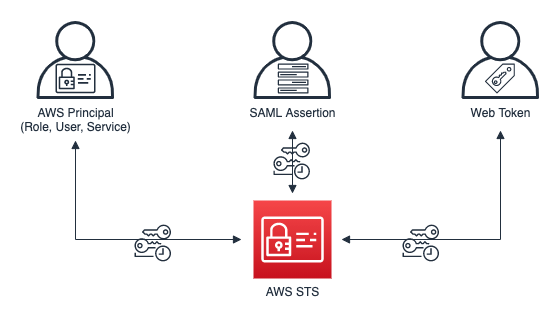
<p>To get these credentials, you can use several different methods: </p>
<div id="attachment_33324" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33324" src="https://infracom.com.sg/wp-content/uploads/2024/02/img1-2.png" alt="Figure 1: Methods to request credentials from AWS STS" width="560" height="319" class="size-full wp-image-33324">
<p id="caption-attachment-33324" class="wp-caption-text">Figure 1: Methods to request credentials from AWS STS</p>
</div>
<h2>Global (legacy) and Regional AWS STS endpoints</h2>
<p>To connect programmatically to an AWS service, you use an <em>endpoint</em>. An <a href="https://docs.aws.amazon.com/general/latest/gr/rande.html" target="_blank" rel="noopener">endpoint</a> is the URL of the entry point for AWS STS.</p>
<p>AWS STS provides Regional endpoints in every Region. AWS initially built AWS STS with a global endpoint (now legacy) <code>https://sts.amazonaws.com</code>, which is hosted in the US East (N. Virginia) Region (<span>us-east-1</span>). Regional AWS STS endpoints are activated by default for <a href="https://docs.aws.amazon.com/accounts/latest/reference/manage-acct-regions.html" target="_blank" rel="noopener">Regions that are enabled by default</a> in your AWS account. For example, <code>https://sts.us-east-2.amazonaws.com</code> is the US East (Ohio) Regional endpoint. By default, AWS services use Regional AWS STS endpoints. For example, <a href="https://docs.aws.amazon.com/rolesanywhere/latest/userguide/introduction.html#first-time-user" target="_blank" rel="noopener">IAM Roles Anywhere</a> uses the Regional STS endpoint that corresponds to the <a href="https://docs.aws.amazon.com/rolesanywhere/latest/userguide/getting-started.html" target="_blank" rel="noopener">trust anchor</a>. For a complete list of AWS STS endpoints for each Region, see <a href="https://docs.aws.amazon.com/general/latest/gr/sts.html" target="_blank" rel="noopener">AWS Security Token Service endpoints and quotas</a>. You can’t activate an AWS STS endpoint in a Region that is disabled. For more information on which AWS STS endpoints are activated by default and which endpoints you can activate or deactivate, see <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp_enable-regions.html#id_credentials_region-endpoints" target="_blank" rel="noopener">Regions and endpoints</a>.</p>
<p>As noted previously, the global (legacy) AWS STS endpoint <code>https://sts.amazonaws.com</code> is hosted in a single Region — US East (N. Virginia) — and like other endpoints, it doesn’t provide automatic failover to endpoints in other Regions. If your workloads on AWS or outside of AWS are configured to use the global (legacy) AWS STS endpoint <code>https://sts.amazonaws.com</code>, you introduce a dependency on a single Region: US East (N. Virginia). In the unlikely event that the endpoint becomes unavailable in that Region or connectivity between your resources and that Region is lost, your workloads won’t be able to use AWS STS to retrieve temporary credentials, which poses an availability risk to your workloads.</p>
<p>AWS recommends that you use Regional AWS STS endpoints (<code>https://sts..amazonaws.com</code>) instead of the global (legacy) AWS STS endpoint.</p>
<p>In addition to improved resiliency, Regional endpoints have other benefits:</p>
<ul>
<li><strong>Isolation and containment</strong> — By making requests to an AWS STS endpoint in the same Region as your workloads, you can minimize cross-Region dependencies and align the scope of your resources with the scope of your temporary security credentials to help address availability and security concerns. For example, if your workloads are running in the US East (Ohio) Region, you can target the Regional AWS STS endpoint in the US East (Ohio) Region (<span>us-east-2</span>) to remove dependencies on other Regions.</li>
<li><strong>Performance</strong> — By making your AWS STS requests to an endpoint that is closer to your services and applications, you can access AWS STS with lower latency and shorter response times.</li>
</ul>
<p>Figure 2 illustrates the process for using an AWS principal to assume an <a href="https://aws.amazon.com/iam/" target="_blank" rel="noopener">AWS Identity and Access Management (IAM)</a> role through the AWS STS <a href="https://docs.aws.amazon.com/STS/latest/APIReference/API_AssumeRole.html" target="_blank" rel="noopener">AssumeRole API</a>, which returns a set of temporary security credentials:</p>
<div id="attachment_33327" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-33327" src="https://infracom.com.sg/wp-content/uploads/2024/02/img2-4.png" alt="Figure 2: Assume an IAM role by using an API call to a Regional AWS STS endpoint" width="780" class="size-full wp-image-33327">
<p id="caption-attachment-33327" class="wp-caption-text">Figure 2: Assume an IAM role by using an API call to a Regional AWS STS endpoint</p>
</div>
<h2>Calls to AWS STS within the same Region</h2>
<p>You should configure your workloads within a specific Region to use only the Regional AWS STS endpoint for that Region. By using a Regional endpoint, you can use AWS STS in the same Region as your workloads, removing cross-Region dependency. For example, workloads in the US East (Ohio) Region should use only the Regional endpoint <code>https://sts.us-east-2.amazonaws.com</code> to call AWS STS. If a Regional AWS STS endpoint becomes unreachable, your workloads shouldn’t call AWS STS endpoints outside of the operating Region. If your workload has a multi-Region resiliency requirement, your other active or standby Region should <a href="https://docs.aws.amazon.com/whitepapers/latest/aws-fault-isolation-boundaries/global-services.html#services-that-use-default-global-endpoints" target="_blank" rel="noopener">use a Regional AWS STS endpoint</a> for that Region and should be deployed such that the application can function despite a Regional failure. You should direct STS traffic to the STS endpoint within the same Region, <a href="https://docs.aws.amazon.com/wellarchitected/latest/reliability-pillar/use-fault-isolation-to-protect-your-workload.html" target="_blank" rel="noopener">isolated and independent from other Regions</a>, and remove dependencies on the global (legacy) endpoint.</p>
<h2>Calls to AWS STS from outside AWS</h2>
<p>You should configure your workloads outside of AWS to call the appropriate Regional AWS STS endpoints that offer the lowest latency to your workload located outside of AWS. If your workload has a multi-Region resiliency requirement, build failover logic for AWS STS calls to other Regions in the event that Regional AWS STS endpoints become unreachable. Temporary security credentials obtained from Regional AWS STS endpoints are <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp_enable-regions.html#sts-regions-activate-deactivate" target="_blank" rel="noopener">valid globally</a> for the default <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_temp_request.html#stsapi_comparison" target="_blank" rel="noopener">session duration</a> or duration that you specify.</p>
<h2>How to configure Regional AWS STS endpoints for your tools and SDKs</h2>
<p>I recommend that you use the latest major <a href="https://docs.aws.amazon.com/sdkref/latest/guide/feature-sts-regionalized-endpoints.html#feature-sts-regionalized-endpoints-sdk-compat" target="_blank" rel="noopener">versions</a> of the <a href="https://docs.aws.amazon.com/cli/" target="_blank" rel="noopener">AWS Command Line Interface (CLI)</a> or <a href="https://docs.aws.amazon.com/sdkref/latest/guide/overview.html" target="_blank" rel="noopener">AWS SDK</a> to call AWS STS APIs.</p>
<h3>AWS CLI</h3>
<p>By default, the <a href="https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-welcome.html#welcome-versions-v2" target="_blank" rel="noopener">AWS CLI version 2</a> sends AWS STS API requests to the Regional AWS STS endpoint for the currently configured Region. If you are using AWS CLI v2, you don’t need to make additional changes.</p>
<p>By default, the AWS CLI v1 sends AWS STS requests to the global (legacy) AWS STS endpoint. To check the version of the AWS CLI that you are using, run the following command: <code>$ aws –version</code>.</p>
<p>When you run AWS CLI commands, the AWS CLI looks for credential configuration in a <a href="https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-configure.html#configure-precedence" target="_blank" rel="noopener">specific order</a>—first in shell environment variables and then in the local AWS configuration file (<code>~/.aws/config</code>).</p>
<h3>AWS SDK</h3>
<p>AWS SDKs are available for a <a href="https://aws.amazon.com/developer/tools/" target="_blank" rel="noopener">variety of programming languages</a> and environments. Since July 2022, major new versions of the AWS SDK default to Regional AWS STS endpoints and use the endpoint corresponding to the currently configured Region. If you use a major version of the AWS SDK that was released after July 2022, you don’t need to make additional changes. </p>
<p>An AWS SDK looks at various <a href="https://docs.aws.amazon.com/sdkref/latest/guide/settings-reference.html#precedenceOfSettings" target="_blank" rel="noopener">configuration locations</a> until it finds credential configuration values. For example, the AWS SDK for Python (<a href="https://boto3.amazonaws.com/v1/documentation/api/latest/guide/configuration.html" target="_blank" rel="noopener">Boto3</a>) adheres to the following lookup order when it searches through sources for configuration values:</p>
<ol>
<li>A configuration object created and passed as the AWS configuration parameter when creating a client</li>
<li>Environment variables</li>
<li>The AWS configuration file <code>~/.aws/config</code></li>
</ol>
<p>If you still use AWS CLI v1, or your AWS SDK version doesn’t default to a Regional AWS STS endpoint, you have the following options to set the Regional AWS STS endpoint:</p>
<h3>Option 1 — Use a shared AWS configuration file setting</h3>
<p>The <a href="https://docs.aws.amazon.com/cli/latest/userguide/cli-configure-files.html" target="_blank" rel="noopener">configuration file</a> is located at <code>~/.aws/config</code> on Linux or macOS, and at <code>C:UsersUSERNAME.awsconfig</code> on Windows. To use the Regional endpoint, add the <code>sts_regional_endpoints</code> parameter.</p>
<p>The following example shows how you can set the value for the Regional AWS STS endpoint in the US East (Ohio) Region (<span>us-east-2</span>), by using the default profile in the AWS configuration file:</p>
<div class="hide-language">
<pre class="unlimited-height-code"><code class="lang-text">[default]
region = us-east-2
sts_regional_endpoints = regional
The valid values for the AWS STS endpoint parameter (<span>sts_regional_endpoints</span>) are:</p>
<ul>
<li><span>legacy</span> (default) — Uses the global (legacy) AWS STS endpoint, sts.amazonaws.com.</li>
<li><span>regional</span> — Uses the AWS STS endpoint for the currently configured Region.</li>
</ul>
<blockquote>
<p><strong>Note</strong>: Since July 2022, major new versions of the AWS SDK default to Regional AWS STS endpoints and use the endpoint corresponding to the currently configured Region. If you are using AWS CLI v1, you must use version 1.16.266 or later to use the AWS STS endpoint parameter.</p>
</blockquote>
<p>You can use the <code>--debug</code> option with the AWS CLI command to receive the debug log and validate which AWS STS endpoint was used.</p>
<div class="hide-language">
<pre class="unlimited-height-code"><code class="lang-text">$ aws sts get-caller-identity
$ –region us-east-2
$ –debug
If you search for UseGlobalEndpoint in your debug log, you’ll find that the UseGlobalEndpoint parameter is set to False, and you’ll see the Regional endpoint provider fully qualified domain name (FQDN) when the Regional AWS STS endpoint is configured in a shared AWS configuration file or environment variables:
For a list of AWS SDKs that support shared AWS configuration file settings for Regional AWS STS endpoints, see Compatibility with AWS SDKS.
Option 2 — Use environment variables
Environment variables provide another way to specify configuration options. They are global and affect calls to AWS services. Most SDKs support environment variables. When you set the environment variable, the SDK uses that value until the end of your shell session or until you set the variable to a different value. To make the variables persist across future sessions, set them in your shell’s startup script.
The following example shows how you can set the value for the Regional AWS STS endpoint in the US East (Ohio) Region (us-east-2) by using environment variables:
Linux or macOS
You can run the command $ (echo $AWS_DEFAULT_REGION; echo $AWS_STS_REGIONAL_ENDPOINTS) to validate the variables. The output should look similar to the following:
Windows
The following example shows how you can configure an STS client with the AWS SDK for Python (Boto3) to use a Regional AWS STS endpoint by setting the environment variable:
You can use the metadata attribute sts_client.meta.endpoint_url to inspect and validate how an STS client is configured. The output should look similar to the following:
For a list of AWS SDKs that support environment variable settings for Regional AWS STS endpoints, see Compatibility with AWS SDKs.
Option 3 — Construct an endpoint URL
You can also manually construct an endpoint URL for a specific Regional AWS STS endpoint.
The following example shows how you can configure the STS client with AWS SDK for Python (Boto3) to use a Regional AWS STS endpoint by setting a specific endpoint URL:
Use a VPC endpoint with AWS STS
You can create a private connection to AWS STS from the resources that you deployed in your Amazon VPCs. AWS STS integrates with AWS PrivateLink by using interface VPC endpoints. The network traffic on AWS PrivateLink stays on the global AWS network backbone and doesn’t traverse the public internet. When you configure a VPC endpoint for AWS STS, the traffic for the Regional AWS STS endpoint traverses to that endpoint.
By default, the DNS in your VPC will update the entry for the Regional AWS STS endpoint to resolve to the private IP address of the VPC endpoint for AWS STS in your VPC. The following output from an Amazon Elastic Compute Cloud (Amazon EC2) instance shows the DNS name for the AWS STS endpoint resolving to the private IP address of the VPC endpoint for AWS STS:
After you create an interface VPC endpoint for AWS STS in your Region, set the value for the respective Regional AWS STS endpoint by using environment variables to access AWS STS in the same Region.
The output of the following log shows that an AWS STS call was made to the Regional AWS STS endpoint:
Log AWS STS requests
You can use AWS CloudTrail events to get information about the request and endpoint that was used for AWS STS. This information can help you identify AWS STS request patterns and validate if you are still using the global (legacy) STS endpoint.
An event in CloudTrail is the record of an activity in an AWS account. CloudTrail events provide a history of both API and non-API account activity made through the AWS Management Console, AWS SDKs, command line tools, and other AWS services.
Log locations
- Requests to Regional AWS STS endpoints
sts..amazonaws.comare logged in CloudTrail within their respective Region. - Requests to the global (legacy) STS endpoint
sts.amazonaws.comare logged within the US East (N. Virginia) Region (us-east-1).
Log fields
- Requests to Regional AWS STS endpoints and global endpoint are logged in the tlsDetails field in CloudTrail. You can use this field to determine if the request was made to a Regional or global (legacy) endpoint.
- Requests made from a VPC endpoint are logged in the vpcEndpointId field in CloudTrail.
The following example shows a CloudTrail event for an STS request to a Regional AWS STS endpoint with a VPC endpoint.
The following example shows a CloudTrail event for an STS request to the global (legacy) AWS STS endpoint.
To interactively search and analyze your AWS STS log data, use AWS CloudWatch Logs Insights or Amazon Athena.
CloudWatch Logs Insights
The following example shows how to run a CloudWatch Logs Insights query to look for API calls made to the global (legacy) AWS STS endpoint. Before you can query CloudTrail events, you must configure a CloudTrail trail to send events to CloudWatch Logs.
The query output shows event details for an AWS STS call made to the global (legacy) AWS STS endpoint https://sts.amazonaws.com.

Figure 3: Use a CloudWatch Log Insights query to look for STS API calls
Amazon Athena
The following example shows how to query CloudTrail events with Amazon Athena and search for API calls made to the global (legacy) AWS STS endpoint.
The query output shows STS calls made to the global (legacy) AWS STS endpoint https://sts.amazonaws.com.

Figure 4: Use Athena to search for STS API calls and identify STS endpoints
Conclusion
In this post, you learned how to use Regional AWS STS endpoints to help improve resiliency, reduce latency, and increase session token usage for the operating Regions in your AWS environment.
AWS recommends that you check the configuration and usage of AWS STS endpoints in your environment, validate AWS STS activity in your CloudTrail logs, and confirm that Regional AWS STS endpoints are used.
If you have questions, post them in the Security Identity and Compliance re:Post topic or reach out to AWS Support.
Want more AWS Security news? Follow us on X.
<!-- '"` -->

You must be logged in to post a comment.