How to protect the self-managed DNS services against DDoS attacks making use of AWS Global AWS and Accelerator Shield Advanced
In this website post, I demonstrate how to enhance the distributed denial of provider (DDoS) resilience of one’s self-managed Domain Name Program (DNS) service through the use of AWS Global Accelerator and AWS Shield Advanced. You may use those services to include a few of the techniques utilized by Amazon Route 53 to safeguard against DDoS attacks.
DNS routes customers to the application by translating the human-readable domain title to a machine-readable Ip quickly. When protecting the option of the application against DDoS assaults, it’s vital that you consider every section of the stack, which includes domain title resolution. The recommended greatest practice would be to create hosted zones on Path 53, a scalable, highly available DNS support that’s protected against huge DDoS episodes and query floods. Path 53 utilizes anycast routing to assist DNS queries from a lot more than 150 advantage locations around the world. With anycast routing, DNS queries are usually served from locations which are closer to your customers and the globally distributed DDoS mitigation capability of Amazon Web Services (AWS) reduces the influence of attacks.
Optionally, you can even build your personal DNS service on Amazon Elastic Compute Cloud (Amazon EC2). For instance, you can operate your personal proprietary DNS server to benefit from custom functions that you wrote to integrate having an existing DNS services that isn’t working on AWS. Once you sign up a domain title, you’re usually necessary to provide at the very least two title servers that can react to queries from your own users. It’s achievable to create a DNS assistance on only two situations, but that delivers limited DDoS resilience.
Solution overview
To safeguard your self-managed DNS program using this solution, you will need a strong knowledge of DNS and how exactly to operate a distributed, self-managed DNS service upon Amazon EC2. This solution improves upon a preexisting self-managed DNS service by enhancing its capability to withstand DDoS attacks significantly. There are two elements that you increase your application:
- You use Global Accelerator to supply the application with two static IP addresses that become a fixed entry way to Amazon EC2 situations in multiple AWS Areas. Global Accelerator utilizes anycast to path your visitors to a spot of entry near to the way to obtain the traffic. Along with providing performance and accessibility benefits, this gives you usage of global DDoS mitigation capability through AWS.
- You use Shield Advanced to monitor the option of the application and automatically engage the AWS Shield Reaction Group (SRT) if its availability is suffering from a DDoS attack. Once you associate a Route 53 health check to your safeguarded sources, Shield Advanced uses the fitness of the application being an insight for detection so when a sign to SRT to get hold of your operations center when needed. You can even engage with SRT to create custom mitigations for the application. For the self-managed DNS service make use of case, this can consist of mitigations like DNS packet validation and suspicion scoring that provides an increased priority to queries which are more prone to be legitimate visitors for the application.
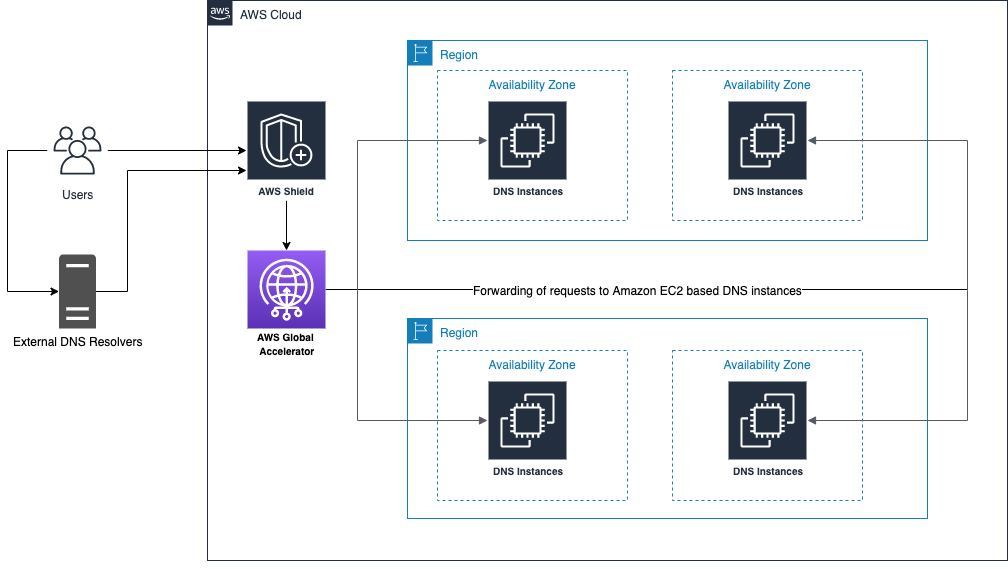
Within this solution, you’ll create a DNS canary that uses Amazon CloudWatch to update the standing of a Route 53 health verify if your own self-managed DNS provider stops giving an answer to queries. A good example architecture using Amazon EC2 based DNS behind Worldwide Shield and Accelerator is shown in determine 1.

Number 1: Amazon EC2 based DNS behind Worldwide Accelerator and Shield
configure and
Create an accelerator
To begin with, create an accelerator and increase your existing DNS servers simply because endpoints. The recently created accelerator shall receive queries and forward them to your DNS service.
To configure and create an accelerator
Phase 1: Create a good accelerator
- Navigate to the AWS Global Accelerator dashboard.
- Choose Create accelerator.
- Enter a genuine name for the accelerator.
- Choose Following.
Step 2: Put listeners
Since DNS uses both UDP and TCP protocols, you need to create separate listeners to take care of requests for every protocol.
At the Add Listeners step, get into the following:
- Ports: 53
- Protocol: TCP
- Client affinity: None
Choose Add listener again to include the UDP listener. Enter the next:
- Ports: 53
- Protocol: UDP
- Client affinity: None
- Choose Following
To learn more concerning the different options obtainable in this task, see To develop a listener in Getting started with AWS Global Accelerator.
Step 3: Increase endpoint groups
You start with the TCP listener, get into the following settings:
- Region: Select a Region your DNS instances can be found in, for instance, us-east-1.
- Visitors dial: 100
- If you possess additional DNS situations in another AWS Region, choose Add endpoint team and repeat measures a) and b), getting into the correct Region.
- Repeat steps the) through c) to include endpoint groupings for the UDP listener, and choose Next then.
To learn more concerning the different options obtainable in this step, for instance, Traffic dial, start to see the Add endpoint groups in Getting started with AWS Global Accelerator.
Step 4: Include endpoints
You start with the TCP listener, get into the following in the proper execution boxes for each Area specified in the last step:
- Endpoint type: Select EC2 instance from the drop-down listing.
- Endpoint: Select the DNS example from the drop-down checklist.
- Weight: 128
Should you have additional DNS situations in your community, choose Add endpoint and do it again the preceding tips, but decide on a DNS example that hasn’t been added being an endpoint.
Repeat all the preceding actions for the UDP listener, choose Create accelerator then.
To learn more concerning the different options obtainable in this step, start to see the Add endpoints in Getting started with AWS Global Accelerator.
Stage 5: Verification
When you pick the Create accelerator button, you’re redirected to a worldwide Accelerator console web page that lists all of the accelerators in your account. With this page, you will see the worldwide DNS and IPs title allocated to your freshly created accelerator, as well as the current status.
Wait until the position of the accelerators adjustments to Deployed before proceeding along with any tests.
Configure Shield Shield and Advanced Advanced proactive engagement
Protect your accelerator along with Shield Advanced, monitor the ongoing wellness of your application, and configure proactive engagement. Once you start proactive engagement, the SRT will straight get in touch with you if an Amazon Route 53 health check connected with your protected useful resource becomes harmful during a meeting that’s detected by Shield Advanced.
To configure proactive engagement
Step 1: Develop a Route 53 health check out
If you curently have a Route 53 health be sure monitors the ongoing wellness of one’s DNS service, you can check out step 2 2 of the section. In the event that you don’t have a wellness check yet, you may use this AWS CloudFormation template to generate one. The template shall
- Create a Lambda functionality that queries your DNS server through the accelerator global IPs. This functionality posts metrics to CloudWatch to point if the query was successful or even not.
- Create the CloudWatch alarm which will identify when DNS queries fall short.
- Create a Path 53 health be sure tracks the CloudWatch alarm and shifts status to harmful once the alarm shifts to the Alarm condition.
Step 2: Sign up to Shield Advanced
Please be aware that with AWS Shield Advanced, you pay the monthly fee of $3,monthly per organization 000. In addition, additionally you purchase AWS Shield Advanced Information Transfer usage costs for AWS assets enabled for advanced security.
- Navigate to the AWS Shield console.
- In the AWS Shield routing bar, choose Finding started, and choose Subscribe to Shield Advanced.
- On the Subscribe to Shield Advanced page, browse the terms of agreement, and select all the check boxes to point that the terms are usually accepted by you.
- Choose Subscribe to Shield Advanced.
Step 3: Add sources to protect
- Do among the following, depending on in the event that you were subscribed to Shield Sophisticated already.
- If you subscribed to Shield Advanced by completing Step two 2 above just, choose Add assets to protect.
- If you’re subscribed to Shield Advanced already, open the Shield gaming console and choose Protected Resources, and choose Put resources to protect then.
- In the Choose resources to safeguard with Shield Advanced page, choose the resource and Areas types that you would like to protect, then choose Load resources.
- Select the resources you want to protect, and choose Protect along with Shield Advanced.
- In the Configure health check out based DDoS detection page, beneath the Protected sources section, decide on a Route 53 wellness check out to add-either one which you created previously, or a ongoing health check created by the AWS CloudFormation template-as the Associated Health Check.
- Choose Following and soon you reach the Evaluation and configure DDoS mitigation and visibility page, and review the configurations and choose End configuration then.
Step 4: Include contacts
- Navigate to the Overview tab associated with the AWS Shield gaming console.
- In the Proactive engagements and contacts section, choose Edit beneath the Contacts heading.
- In the Add contact form, increase the contact’s E-mail, Phone amount, and Information.
- Choose Save.
Step 5: Demand proactive engagement
- Choose Edit proactive engagement feature.
- Select Enable.
- Choose Save.
Step 6: Configuration evaluation with the SRT
After you allow proactive engagement, hawaii will undoubtedly be Proactive engagement requested and pending.
SRT shall contact one to schedule a construction review. The review includes overview of your Route 53 health check construction and an appointment about custom mitigations which can be configured to aid your DNS use situation. Following this review, SRT shall complete your request make it possible for proactive engagement.
Summary
DNS is really a foundational area of the user knowledge for just about any application that’s accessed via a individual readable domain name. Your DNS service ought to be available highly, DDoS resilient, and obtainable to your customers with minimal latency. If you run your personal DNS service on Amazon EC2, it is possible to enhance the DDoS resiliency making use of Global Accelerator and Shield Advanced. This option provides your customers with a minimal latency way to your DNS support and you with a number of the DDoS mitigation that shields Route 53. For more information about DDoS guidelines, see AWS Best Practices for DDoS Resiliency.
In case you have feedback concerning this post, submit remarks in the Comments section below. For those who have questions concerning this post, start a brand-new thread on the AWS Shield forum or contact AWS Support.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.
