How to make use of AWS KMS RSA keys for offline encryption
This website post discusses ways to use AWS Key Administration Service (AWS KMS) RSA public keys at a time clients or gadgets and encrypt data, then subsequently decrypt data through the use of private keys which are secured in AWS KMS.
<pre> <code> <p>Asymmetric cryptography is really a cryptographic system that uses <em>essential pairs</em>. Each pair includes a public key, which may be observed or accessed by anyone, and an exclusive key, which may be accessed just by authorized people. This technique includes a useful property, that is that anything encrypted with a open public key can only just become decrypted by the corresponding personal key. A popular way for generating essential pairs and encrypting information may be the <a href="https://sobre.wikipedia.org/wiki/RSA_(cryptosystem)" focus on="_blank" rel="noopener noreferrer">RSA</the> cryptosystem and algorithm.</p>
<p>For key pairs RSA, calculating the private essential from the general public key sometimes appears as computationally infeasible, and for that reason RSA key pairs may be used for both authentication and encryption. The top features of asymmetric encryption allow divided parties to talk about info across an untrusted domain, like the internet, without needing to pre-share any secrets. However, this kind of encryption poses a concern of keeping the personal key secure, as the private key gets the capacity to decrypt all communications which are transmitted by a large numbers of customers.</p>
<p><a href=”https://aws.amazon.com/kms/” focus on=”_blank” rel=”noopener noreferrer”>AWS KMS</a> provides easy APIs which you can use to securely generate, shop, and manage keys, which includes RSA essential pairs inside hardware protection modules (HSMs). Important pairs are created within FIPS 140-2 validated HSMs which are handled by AWS. After that you can use these personal keys through APIs to accomplish actions such as for example decrypt ciphertexts, and therefore plaintext private keys in no way leave the HSM, which gives assurances of personal privacy for the private essential. Extra APIs allow a person to retrieve a plaintext duplicate of the corresponding general public key, that allows disconnected or offline utilizes of RSA open public keys.</p>
<h2>Limitations of asymmetric cryptography</h2>
<p>An integral drawback to asymmetric cryptography may be the proven fact that you cannot encrypt big pieces of data. If you have a 2048-bit RSA key set and encrypt something utilizing the cipher RSAES_OASEP_SHA_256, the biggest amount of information that you could encrypt will be 190 bytes.</p>
<p>On the other hand, symmetric encryption ciphers that work with a chained or counter-mode procedure don’t have this limit, and they allow one to encrypt data in the tens-of-gigabytes. Symmetric encryption algorithms like the <a href=”https://www.nist.gov/publications/advanced-encryption-standard-aes” focus on=”_blank” rel=”noopener noreferrer”>Advanced Encryption Regular (AES)</the> also reap the benefits of faster information encryption speeds because of smaller key dimensions and less complex procedures that can be included in hardware.</p>
<p>By merging both of these algorithms in a <a href=”https://sobre.wikipedia.org/wiki/Hybrid_cryptosystem” focus on=”_blank” rel=”noopener noreferrer”>hybrid cryptosystem</the>, you give finish clients with a general public key the opportunity to encrypt large bits of information. Litigant generates a random 256-bit AES key, that ought to be from the secure supply such as <period>/dev/urandom</span> or perhaps a devoted embedded chip. Your client then encrypts its big payload with a <a href=”https://sobre.wikipedia.org/wiki/Block_cipher_mode_of_procedure” focus on=”_blank” rel=”noopener noreferrer”>mode of procedure</a> such as for example AES-GCM or AES-CBC through the use of that 256-little bit AES key. Next, your client encrypts that 256-bit AES key utilizing the RSA public important (see stage 5 in Figure 1). End clients after that transmit only encrypted information across insecure channels, maintaining personal privacy of the payload information.</p>
<p>Challenging that customers often encounter is that they desire to use AWS KMS because of its security properties, but additionally want to entry their KMS keys from products that don’t have AWS credentials embedded within them. Without AWS credentials, a tool can’t contact AWS APIs. This website post shows ways to work with a hybrid cryptosystem where RSA general public keys could be downloaded or embedded into gadgets to overcome this problem.</p>
<h2>Prerequisites and initial factors</h2>
<p>This walkthrough assumes you have some knowledge of RSA ciphers and symmetric encryption schemes such as for example <a href=”https://www.nist.gov/publications/advanced-encryption-standard-aes” focus on=”_blank” rel=”noopener noreferrer”>AES</the>. The walkthrough utilizes OpenSSL for demonstration of the encryption procedure, but similar libraries may be used on a client-side gadget.</p>
<p>The walkthrough also assumes which you have an <a href=”http://aws.amazon.com/iam” focus on=”_blank” rel=”noopener noreferrer”>AWS Identification and Access Administration (IAM)</the> consumer with <a href=”https://docs.aws.amazon.com/kms/best and newest/developerguide/iam-policies.html” focus on=”_blank” rel=”noopener noreferrer”>permissions to the AWS KMS provider</the>, and the <a href=”https://aws.amazon.com/cli/” focus on=”_blank” rel=”noopener noreferrer”>AWS Command Collection User interface (AWS CLI)</the> <a href=”https://docs.aws.amazon.com/cli/most recent/userguide/getting-started-install.html” focus on=”_blank” rel=”noopener noreferrer”>installed</the> with the related credentials.</p>
<p>Once you develop a KMS key, additionally, you will generate a <a href=”https://docs.aws.amazon.com/kms/current/developerguide/key-policies.html” focus on=”_blank” rel=”noopener noreferrer”>key plan</the> that defines usage of it. The default crucial policy allows all customers in your accounts with AWS KMS activities within their IAM policies to gain access to the KMS essential. The main element policy for confirmed KMS key may be the primary way for <a href=”https://docs.aws.amazon.com/kms/newest/developerguide/determining-access-key-policy.html” focus on=”_blank” rel=”noopener noreferrer”>determining gain access to</the>.</p>
<blockquote>
<p><strong>Important</strong>: You’ll incur costs for the ongoing services found in this example. The cost are available by you of every service on the corresponding service pricing page. For more information, discover <a href=”https://aws.amazon.com/kms/pricing/” focus on=”_blank” rel=”noopener noreferrer”>AWS KMS Prices</the>.</p>
</blockquote>
<h2>Architectural overview</h2>
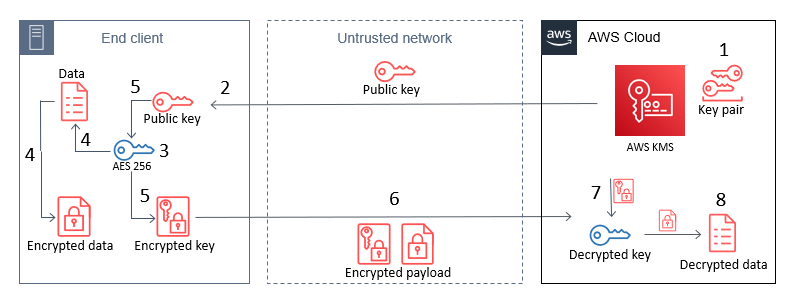
<p>This post contains procedures for completing the next operations, which are shown in Physique 1:< also;/p>
<ol>
<li>Create an RSA major pair inside AWS KMS.</li>
<li>Download or even pre-install the AWS KMS open public key to a good end-client gadget.</li>
<li>Generate an AES 256-bit key on an last end client.</li>
<li>Encrypt a big payload of information on the finish client utilizing the AES 256-bit key.</li>
<li>Encrypt the AES 256-bit key with the AWS KMS community key.</li>
<li>Exchange the encrypted major and payload.</li>
<li>Decrypt the AES 256-bit key through the use of AWS KMS.</li>
<li>Decrypt the payload data utilizing the now-shared AES 256-bit key.</li>
</ol>
<div id=”attachment_25291″ course=”wp-caption aligncenter”>
<img aria-describedby=”caption-attachment-25291″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/05/24/picture1-2.png” alt=”Number 1: The tips for hybrid encryption” width=”798″ height=”305″ course=”size-full wp-picture-25291″>
<p id=”caption-attachment-25291″ course=”wp-caption-text”>Figure 1: The actions for hybrid encryption</p>
</div>
<p>This diagram shows an final end client device, an untrusted network like a cellular network, and the AWS Cloud. An RSA essential pair is produced in AWS KMS, and the public key could be embedded ultimately client either, or pulled by the finish customer through HTTP(S) or various other remote means. In every circumstances, only the general public key persists on the ultimate end client, meaning that no techniques are stored on these devices.</p>
<p>The way you host the general public key on your own end clients depends upon what system access they have. For instance, an embedded <a href=”https://sobre.wikipedia.org/wiki/Web_of_things” focus on=”_blank” rel=”noopener noreferrer”>Internet of Items (IoT)</the> gadget for mining automobiles might hook up to the internet, but could talk to a central system by way of a private 5G system. In this circumstance, you’ll host this public essential within that system for retrieval. For some other disconnected IoT products that may connect to the web, such as smart-home devices, you might like to host the public essential on a internet server at a predefined URL or via an API.</p>
<blockquote>
<p><strong>Notice:</strong> Once you vend open public keys over an untrusted channel, such as for example when you vend the general public key via an API, factors to consider that the key could be verified for some reason to verify that it hasn’t already been tampered with. That is completed by vending keys over an HTTPS link typically, where in fact the integrity of the keys is usually supplied by the X.509 certificate that has been found in the TLS connection. The X.509 certificate verifies a link with the key-pair owner also, by domain name typically.</p>
</blockquote>
<h2>Carry out the option</h2>
<p>The next steps may be used as a proof-of-concept to help you through implementing a hybrid-cryptosystem with a KMS public key on a good example device.</p>
<h3>Create keys inside AWS KMS</h3>
<p>In step one of the solution, you create an RSA asymmetric key set in AWS KMS (step one 1 in the architectural overview). With AWS KMS, it is possible to create key pairs in a number of dimensions in accordance with your security standards or even requirements. For more information, find <a href=”https://docs.aws.amazon.com/kms/recent/developerguide/key-types.html” focus on=”_blank” rel=”noopener noreferrer”>Selecting a KMS key style</the> in the AWS KMS documentation.</p>
<p>To produce a key pair within AWS KMS, utilize the <a href=”https://docs.aws.amazon.com/kms/most recent/APIReference/API_CreateKey.html” focus on=”_blank” rel=”noopener noreferrer”>CreateKey API</a>. Because of this example, you shall create an RSA key pair with <span>RSA_2048</period> for the <period>CustomerMasterKeySpec</period> < and parameter;period>ENCRYPT_DECRYPT</period> for the <period>KeyUsage</period> parameter in the <a href=”https://aws.amazon.com/cli/” focus on=”_blank” rel=”noopener noreferrer”>AWS CLI</a>. This write-up uses 2048-little bit keys, but remember that AWS KMS enables larger key sizes. The CLI shall come back a <period>KeyId</period> worth that identifies the KMS type in your account uniquely, which you should observe.</p>
<p><strong>To produce a KMS key utilizing the CLI</strong></p>
<ul>
<li>Enter the next command inside the AWS CLI.
<div course=”hide-language”>
<pre><code class=”lang-text”>aws kms create-essential –key-spec RSA_2048
–key-usage ENCRYPT_DECRYPT
–description “Illustration RSA Encryption Key Set”</program code></pre>
</div> </li>
</ul>
<p>The < could be followed by you;a href=”https://docs.aws.amazon.com/kms/most recent/developerguide/asymm-create-key.html” focus on=”_blank” rel=”noopener noreferrer”>Generating asymmetric KMS keys</the> documentation to observe how to utilize the <a href=”https://aws.amazon.com/console/” focus on=”_blank” rel=”noopener noreferrer”>AWS Management Gaming console</a> to produce a KMS key set with exactly the same properties as shown right here.</p>
<blockquote>
<p><strong>Take note:</strong> Whenever a KMS key is established, it will be logged by <a href=”https://aws.amazon.com/cloudtrail/” focus on=”_blank” rel=”noopener noreferrer”>AWS CloudTrail</a>, a continuing support that monitors and information activity inside your account. All API phone calls to the AWS KMS services are usually <a href=”https://docs.aws.amazon.com/kms/most recent/developerguide/logging-using-cloudtrail.html” focus on=”_blank” rel=”noopener noreferrer”>logged within CloudTrail</a>, used to audit usage of KMS keys.</p>
</blockquote>
<p>To permit your KMS essential to end up being identified by way of a human-readable string instead of <period>KeyId</period>, it is possible to assign an alias for the KMS essential (replace the <period>target-key-id</period> worth of <period><1234abcd-12ab-34cd-56ef-1234567890ab></span> together with your <period>KeyId</period>). This helps it be easier to make use of and manage.</p>
<p><strong>To produce a KMS essential alias for the key utilizing the CLI</strong></p>
<ul>
<li>Enter the next command inside the AWS CLI.
<div course=”hide-language”>
<pre><code class=”lang-text”>aws kms create-alias
–alias-name alias/example-rsa-key
–target-key-id <period><1234abcd-12ab-34cd-56ef-1234567890ab></span>
<pre> <code> <h3>Download the general public essential from AWS KMS </h3>
Good results of asymmetric encryption will be you could distribute a public important to a big, untrusted system, and the general public key can just be utilized for encryption. Decryption of these messages can only just be performed by the corresponding personal key. The < may be used by you;a href=”https://docs.aws.amazon.com/kms/newest/APIReference/API_Encrypt.html” focus on=”_blank” rel=”noopener noreferrer”>AWS KMS Encrypt API</the> to encrypt information with a KMS essential pair (specifically the general public key). However, as the AWS APIs are usually authenticated with a <a href=”https://docs.aws.amazon.com/general/best and newest/gr/signing_aws_api_requests.html” focus on=”_blank” rel=”noopener noreferrer”>signature</the>, you’ll want usage of AWS credentials to utilize these APIs, which you might not want to accomplish on untrusted devices. Additionally, in an exclusive 5G network, you might not are capable to call the <a href=”https://docs.aws.amazon.com/general/most recent/gr/kms.html” focus on=”_blank” rel=”noopener noreferrer”>AWS KMS API endpoints</the> from the finish clients. Instead, it is possible to download the general public key from the local resource or embed that in to the end client during manufacture.</p>
<p>To retrieve a duplicate of the general public key from your own AWS KMS key set, the < may be used by you;a href=”https://docs.aws.amazon.com/kms/newest/APIReference/API_GetPublicKey.html” focus on=”_blank” rel=”noopener noreferrer”>GetPublicKey API</a>. The next example shows how exactly to utilize this with the AWS CLI control <a href=”https://docs.aws.amazon.com/cli/most recent/reference/kms/get-public-crucial.html” focus on=”_blank” rel=”noopener noreferrer”>get-public-key</the> and reference the main element alias you earlier collection.</p>
<p><strong>To see the public essential for the KMS key pair utilizing the CLI</strong></p>
<ul>
<li>Enter the next command inside the AWS CLI.
<div course=”hide-language”>
<pre><program code>aws kms get-public-key –key-id alias/example-rsa-key</program code></pre>
</div> </li>
</ul>
<p>The return value out of this API shall contain several elements, including the <period>PublicKey</period>. The came back <period>PublicKey</period> value may be the DER-encoded X.509, and because you’re utilizing the AWS CLI, it really is base64-encoded for readability reasons. Utilizing the AWS CLI, it is possible to query the < simply;period>PublicKey</period> return value, bottom64-decode it, and save the main element to a document on disk then, the following.</p>
<p><strong>To utilize the AWS CLI to query just the public key, foundation64 decode it and result it to a file< then;/strong></p>
<ul>
<li>Enter the next command inside the AWS CLI.
<div course=”hide-language”>
<pre><code class=”lang-text”>aws kms get-public-key
–key-id alias/example-rsa-important
–output textual content
–query PublicKey | base64 –decode > public_crucial.der
In this example, the neighborhood machine where in fact the public_key was saved by you. der file may represent the end-client gadget.
Note: In the event that you contact this API through the use of among the AWS SDKs, such as for example boto3 , then your PublicKey value isn’t base64-encoded.
Create an AES 256-little bit symmetric key on the ultimate end client
Even though end client now includes a copy of the general public essential from the related KMS private key, the general public key can’t be utilized for encrypting information that you intend on transmitting, because of the size limitations on data which can be encrypted. Rather, you may use symmetric encryption. Generally, symmetric keys are usually smaller sized than asymmetric keys, the ciphers are usually faster when encrypting information, and the resulting ciphertext is comparable in dimension to the initial data.
generate a symmetric important
To, a source ought to be utilized by you of random entropy. Some os’s offer block usage of hardware-based resources of random amounts, such as for example /dev/hwrng . To supply a good example process in this website post, you will utilize the OpenSSL rand utility , which runs on the cryptographically protected pseudo random generator (CSPRNG) seeded by /dev/urandom . In creation systems, you might have stronger resources of entropy to depend on, or compliance needs for random number era. In hardware-constrained conditions, you need to take extra treatment to make certain that resources of entropy are usually cryptographically secure. The next order uses OpenSSL to generate an AES 256-little bit (32 bytes) crucial and bottom64-encode it, conserve it to disk within plaintext as essential then.b64 .
Note: A person with usage of this file system could have access to this essential.
To utilize the OpenSSL rand control to produce a symmetric key and result it to a document
- Enter the next command.
Encrypt the info to be delivered from the ultimate end client
Given that you have two various key types on the ultimate end client, you may use a hybrid cryptosystem to encrypt a big text file. First, you shall generate an example file to encrypt on your own system. By outputting some bytes from /dev/urandom , this file could be created by one to the size you need. The following order outputs 200 random bytes, foundation64-encodes the document, and writes that to disk in a document called encrypt.me personally .
generate an example file from random information
To, which is encrypted afterwards
- Enter the next command.
Next, you’ll encrypt the freshly created document with the AES 256-bit essential that you created previous (that is base64-encoded). Utilizing the OpenSSL command series, you shall encrypt the file about disk and develop a new file called encrypt.me personally.enc .
Notice: For demonstration purposes, this alternative uses OpenSSL to perform the encryption process. Nevertheless, the command collection OpenSSL enc utility doesn’t permit the cipher aes-256-gcm . Galois Counter Setting (GCM) is preferred when encrypting and delivering data, because it contains authentication , in order that that the ciphertext can’t end up being tampered with in transit. Instead, because of this demonstration, you shall make use of aes-256-cbc , which is not really authenticated.
To utilize the OpenSSL enc control to encrypt your sample document with a symmetric crucial
- • Enter the next command.
Encrypt the AES 256-bit essential
So the data can once again be decrypted, you shall have to share exactly the same AES 256-bit key with the recipient. To talk about that with just the person who may use the KMS personal essential that you created previous, it is possible to encrypt the symmetric important ( crucial.b64 ) with the RSA general public essential that you retrieved previous ( public_essential.der ).
Again, you’ll use OpenSSL to observe how this ongoing functions and the mandatory cipher options. When decrypting or encrypting with a KMS RSA essential pair, you can use 1 of 2 encryption algorithms , either RSAES_OAEP_SHA_256 or RSAES_OAEP_SHA_1 . These identify the cipher suites found in encryption which are supported by AWS KMS for encryption currently.
To utilize the OpenSSL pkeyutl order to encrypt your symmetric essential with your local duplicate of one’s KMS public important
- Enter the next command.
This control creates a new document on disk known as essential.b64.enc . This document may be the encrypted AES 256-bit key, which may be transported safely across an insecure system now, like the internet. The final two choices in the order define the padding setting utilized ( OAEP ) and along the information digest ( SHA-256 ), which align with your options available to decrypt once the AWS can be used by you KMS APIs.
Take note: You need to securely delete both original payload document ( encrypt.myself ) and the plaintext AES 256-bit key ( important.b64 ) in order to prevent other people from accessing these data files. At this point, you should have three documents on disk: public_essential.der , encrypt.me personally.enc , and essential.b64.enc . In order to verify the decryption procedure in this example later on, keep these data files.
In production, you might write these ideals to disk never. Instead, it is possible to keep all ideals in memory and just write the encrypted information (ciphertext) to disk, clearing memory from then on process has finished.
Now you can use the approach to your choice to exchange the encrypted documents across an unsecured system without compromising the personal privacy of these files. For smart-house appliance use cases, it is possible to upload the encrypted data files in Amazon Simple Storage Services (Amazon S3) , a durable storage system which can be accessed from the web highly, remember the preventative security procedures that AWS recommends. Later, another ongoing assistance can pull these documents from S3, sufficient reason for the right permissions for the KMS crucial, can decrypt the data files utilizing the AWS KMS Decrypt API .
Decrypt the files
With usage of the decrypt procedure for the KMS essential and the encrypted documents, it is possible to retrieve the plaintext information file again now. To do this, you shall replicate the preceding methods, but in invert. This calls for decrypting the AWS 256-bit key utilizing the AWS KMS API, and using that lead to decrypt the encrypted information then. You shall need usage of the AWS KMS API to perform these actions, because the private important exists in plaintext just within the AWS KMS HSMs.
To decrypt the data files
- The initial step would be to decrypt the AWS 256-bit key. You shall have to utilize the AWS CLI to submit the key.b64.enc document to the AWS KMS API, and specify the algorithm you used to encrypt the document ( RSAES_OAEP_SHA_256 ). Utilize the following control to retrieve the AES 256-bit type in plaintext. Once again, you’re utilizing the -query selector to output just the plaintext, and decode the base64 worth then.
–ciphertext-blob fileb://essential.b64.enc –encryption-algorithm RSAES_OAEP_SHA_256 –output text –query ‘Plaintext’ | base64 –decode > decrypted_important.b64
- The final part of decrypting the data would be to invert the CBC encryption procedure you found in OpenSSL. If another setting of symmetric encryption had been used, such as for example AES-GCM, after that you would have to decrypt through the use of that algorithm and the insight AES 256-bit key. Utilize the following OpenSSL order to retrieve the initial plaintext payload.
Conclusion
In this article, you learned how exactly to blend AWS KMS asymmetric essential pairs with locally developed symmetric keys to encrypt and talk about data that exceeds 190 bytes, without storing a key on litigant device. By taking benefit of the RSA cryptosystem for offline encryption, it is possible to reduce the direct exposure of plaintext strategies or data to gadgets beyond your control, and and never have to complete complex essential exchanges. Utilizing the ways in this solution, it is possible to more share huge amounts of data securely, such as for example update configuration or documents settings. To learn more concerning the asymmetric keys function of AWS KMS, make reference to the AWS KMS Developer Guideline . Should you have questions concerning the asymmetric keys function, connect to us through AWS re:Write-up .
In case you have feedback concerning this post, submit remarks in the Comments area below. For those who have questions concerning this post, get in touch with AWS Help .
Want more AWS Safety news? Stick to us on Twitter .
<pre> <code> <!-- '"` -->
</code> </pre>
