How to implement trusted identity propagation for applications protected by Amazon Cognito
Amazon Web Services (AWS) recently released AWS IAM Identity Center trusted identity propagation to create identity-enhanced IAM role sessions when requesting access to AWS services as well as to trusted token issuers. These two features can help customers build custom applications on top of AWS, which requires fine-grained access to data analytics-focused AWS services such as Amazon Q Business, Amazon Athena, and AWS Lake Formation, and Amazon S3 Access Grants. You can use AWS services compatible with trusted identity propagation to grant access to users and groups belonging to IAM Identity Center instead of solely relying on AWS Identity and Access Management (IAM) role permissions. With a trusted token issuer, you can propagate identities that you have authenticated in your custom application to the underlying AWS services. In the case of an Amazon Q Business application, you can create a different web experience or integrate an Amazon Q Business application as an assistant into an existing web application to help your workforce.
These two features rely on the OAuth 2.0 protocol to exchange user information. For the identity to be consumable by AWS services, your custom application’s identity provider needs to be able to issue OAuth 2.0 tokens for your users.
This blog post from November 2023 covers how to interconnect with an OAuth 2.0 compatible identity provider such as Microsoft Entra ID, Okta, or PingFederate.
In this post, I show you how to use an Amazon Cognito user pool as a trusted token issuer for IAM Identity Center. You will also learn how to use IAM Identity Center as a federated identity provider for a Cognito user pool to provide a seamless authentication flow for your IAM Identity Center custom applications. Note that this content doesn’t cover building a custom application for Amazon Q Business. If needed, you can find more details in Build a custom UI for Amazon Q Business.
IAM Identity Center concepts
IAM Identity Center is the recommended service for managing your workforce’s access to AWS applications. It supports multiple identity sources, such as an internal directory, external Active Directory, or a SAML-compliant identity provider (IdP) with optional SCIM integration.
With trusted identity propagation, a user can sign in to an application, and that application can pass the user’s identity context when creating an identity-enhanced AWS session to access data in AWS services. Because access is now tied to the user’s identity in IAM Identity Center, AWS services can rely on both the IAM role permissions to authorize access as well as the user’s granted scopes and group memberships.
Trusted token issuers are OAuth 2.0 authorization servers that create signed tokens and enable you to use trusted identity propagation with applications that authenticate outside of AWS. With trusted token issuers, you can authorize these applications to make requests on behalf of their users to access AWS managed applications. The trusted token issuers feature is completely independent from the authentication feature of IAM Identity Center and doesn’t need to be the same identity provider as is used for authenticating into IAM Identity Center.
When performing a token exchange, the token must contain an attribute that maps to an existing user in IAM Identity Center, such as an email address or external ID. A token can be exchanged only once.
On the other side, an Amazon Cognito user pool is a user directory and an OAuth 2.0 compliant identity provider (IdP). From the perspective of your application, a Cognito user pool is an OpenID Connect (OIDC) IdP. Your application users can either sign in directly through a user pool, or they can federate through a third-party IdP. When you federate Cognito to a SAML IdP, or OIDC IdPs, your user pool acts as a bridge between multiple identity providers and your application.
Overview of solution
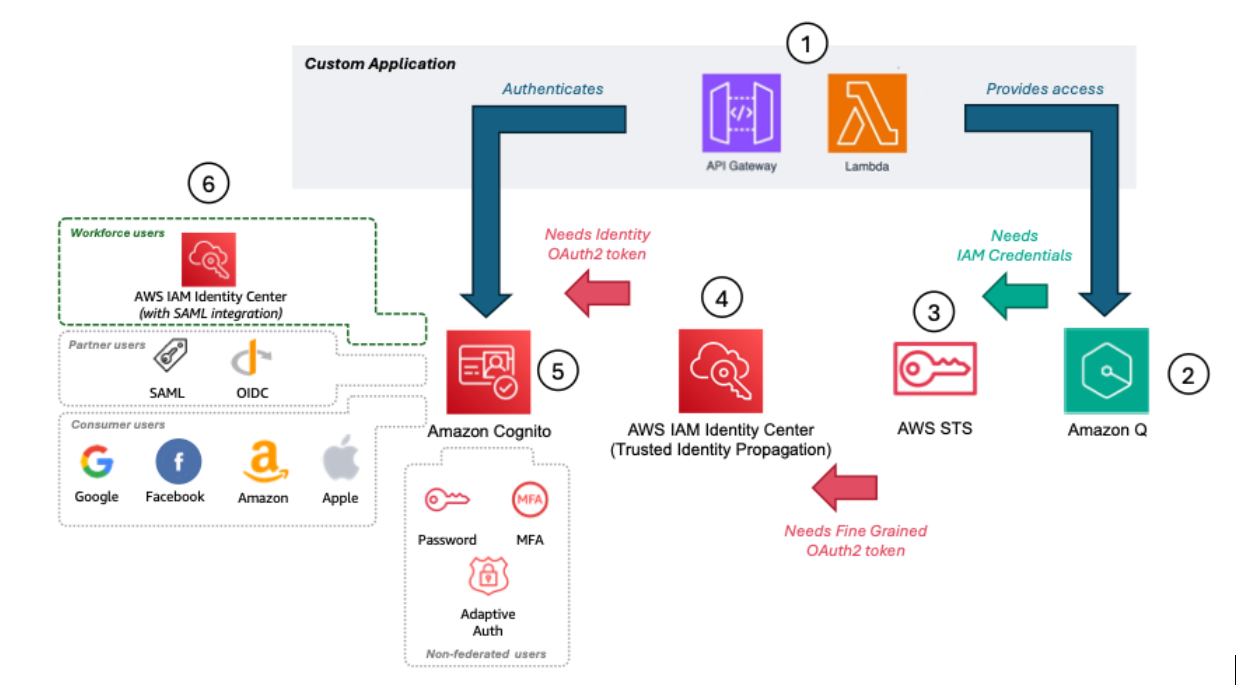
The solution architecture includes the following elements and steps and is depicted in Figure 1.
- The custom application: The custom application provides access to the Amazon Q Business application through APIs. Users are authenticated using Amazon Cognito as an OAuth 2.0 IdP.
- Amazon Q Business: The Amazon Q Business application requires identity-enhanced AWS credentials issued by AWS Security Token Service (AWS STS) to authorize requests from the custom application.
- AWS STS: STS issues identity-enhanced AWS credentials to the custom application through the
setContextandAssumeRoleAPI calls.SetContextrequires the user’s identity context to be passed from a JSON web token (JWT) issued by IAM Identity Center. - IAM Identity Center: To issue a JWT, IAM Identity Center requires the custom application to perform a token exchange operation from a trusted IAM role and a trusted token issuer (Cognito).
- Amazon Cognito user pool: The user pool authenticates users into the custom application. The user pool uses SAML federation to delegate authentication to Identity Center. Users are automatically created in the user pool when the federated authentication is successful. The user pool returns a JWT to the custom application.
- SAML-based customer managed application (when IAM Identity Center is acting as a SAML identity provider): By using the SAML customer managed application in IAM Identity Center, you can delegate the authentication from Cognito to IAM Identity Center. One benefit of using IAM Identity Center is to help guarantee that the user exists in IAM Identity Center before authenticating to Cognito, as long as IAM Identity Center is the only way to authenticate to the client application. User existence is a requirement to perform the token exchange operation.

Figure 1: Solution architecture
Walkthrough
The focus of this post is steps 3–6 of the architecture, which follow a three-step approach.
- Creation and initial configuration of the Amazon Cognito user pool and domain
- Configuration of the OAuth integration for trusted identity propagation
- Configuration of the SAML federation trust between IAM Identity Center and Cognito
Prerequisites
For this walkthrough, you need the following prerequisites:
- An AWS account
- An organization instance of IAM Identity Center
- An Amazon Q Business application setup (optional)
- Administrative access to the AWS account
- AWS Command Line Interface (AWS CLI)
Step 1: Create the Cognito user pool, the user pool domain and the user pool client
The following bash script sets up the Amazon Cognito user pool, user pool domain, and user pool client and outputs the issuer URL and audience that you need to set up IAM Identity Center.
Note: The Cognito user pool domain prefix must be unique across all AWS accounts for a given AWS Region. Replace
with a unique prefix for your user pool domain.
Step 2: Create the OAuth integration for trusted identity propagation
To create the OAuth integration, you need to set up a trusted token issuer and configure the OAuth customer managed application.
Configure a trusted token issuer
Start by configuring IAM Identity Center to trust tokens issued by the Amazon Cognito user pool.
Configure OAuth customer managed application
Create the OAuth customer managed application, which will allow your AWS account to exchange tokens issued for the Cognito user pool client.
Step 3: Create the SAML federation trust between IAM Identity Center and Cognito
The SAML integration between IAM Identity Center and Amazon Cognito is useful when your source of identity is IAM Identity Center. In this scenario, SAML integration helps ensure that users will authenticate with IAM Identity Center credentials before being authenticated to your Cognito user pool. When using federated identities, the Cognito user pool will automatically create user profiles, so you don’t need to maintain the user directory separately.
Configure IAM Identity Center
- Sign in to the AWS Management Console and navigate to IAM Identity Center.
- Choose Applications from the navigation pane.
- Choose Add application.
- Select I have an application I want to set up, select SAML 2.0, and then choose Next.
- For Display name, enter
DemoSAMLApplication. - Copy the IAM Identity Center SAML metadata file URL for later use.
- For Application properties, leave both fields blank.
- For Application ACS URL, enter
https://.auth..amazoncognito.com/saml2/idpresonse. Replacewith the domain you chose in Step 1 andwith the Region in which you created the Cognito user pool. - For Application SAML audience, enter
urn:amazon:cognito:sp:. Replacewith the ID of the Cognito user pool you created in Step 1. - Choose Submit.
Configure mapping attributes
- Choose Actions and select Edit attribute mappings.
- Enter
${user:email}for the field Maps to this string value or user attribute in IAM Identity Center. - Select Persistent for Format.
- Choose Save changes.
Configure Cognito user pool
- Navigate to the Amazon Cognito console and choose User pools from the navigation pane.
- Select the user pool created in Step 1.
- Choose the Sign-in experience tab.
- Under Federated identity provider sign-in, choose Add identity provider.
- Select SAML.
- Under Provider name, enter
IAMIdentityCenter. - Under Metadata document source, select Enter metadata document endpoint URL and paste the URL copied from step 6 of Configure IAM Identity Center
- Under SAML attribute, enter
Subject. - Choose Add Identity Provider.
Configure app integration to use IAM Identity Center
- Choose the App integration tab.
- Under App clients and analytics, choose TTI.
- Under Hosted UI, choose Edit.
- For Identity providers, select IAMIdentityCenter.
- Choose Save changes.
Architecture diagram
Figure 2 shows the authentication flow from the user connecting to the web application up to the chat interaction with Amazon Q Business APIs.
Note: The AWS resources can be in the same Region, but it’s not required for Amazon Cognito and IAM Identity Center.
- The application redirects the user to Amazon Cognito for authentication.
- Cognito redirects the user to IAM Identity Center for authentication.
- Cognito parses the SAML assertion from IAM Identity Center.
- Cognito returns a JWT to the application.
- The application exchanges the token with IAM Identity Center.
- The application assumes an IAM role and sets the context using the IAM Identity Center token.
- The application invokes the Amazon Q Business APIs with the context-aware STS session.

Figure 2: Authentication flow
Clean up
To avoid future charges to your AWS account, delete the resources you created in this walkthrough. The resources include:
- The Amazon Cognito user pool (deleting this will also delete sub resources such as the user pool client)
- The SAML application in IAM Identity Center
- The OAuth application in IAM Identity Center
- The trusted token issuer configuration in IAM Identity Center
Conclusion
In this post, we demonstrated how to implement trusted identity propagation for applications that are protected by Amazon Cognito. We also showed you how to authenticate Cognito users with IAM Identity Center to help ensure that users are authenticating using the correct mechanisms and policies and to reduce the operational burden of managing the Cognito directory by automatically provisioning users as they sign in.
Using Amazon Cognito as a trusted token issuer is useful when your application is already secured with a user pool, and you want to implement data functionalities such as Amazon Q Business chat capabilities or secure access to S3 buckets using S3 Access Grants.
If your users are authenticating with different identity providers, the solution in this post can reduce the work needed for identity integration by enabling you to add multiple identity providers to a single user pool. By using this solution, you will need to configure the trusted token issuer in IAM Identity Center only for Amazon Cognito and not for every token provider.
This walkthrough doesn’t include a demo web application because I wanted to dive into the integration of IAM Identity Center and Amazon Cognito. I recommend reading Build a custom UI for Amazon Q Business, which shows you how to implement a custom user interface for an Amazon Q Business application using Amazon Cognito for user authentication.
Because trusted identity propagation is becoming more prevalent within AWS services, I recommend the following blog posts to learn more about using it with various services.
- How to develop a user-facing data application with IAM Identity Center and S3 Access Grants (in two parts)
- Simplify workforce identity management using IAM Identity Center and trusted token issuers
- Simplify access management with Amazon Redshift and AWS Lake Formation for users in an External Identity Provider
- AWS analytics services streamline user access to data, permissions setting, and auditing
- Access AWS services programmatically using trusted identity propagation
If you have feedback about this post, submit comments in the Comments section below.

You must be logged in to post a comment.