How to enforce a security baseline for an AWS WAF ACL across your organization using AWS Firewall Manager
Most organizations prioritize protecting their web applications that are exposed to the internet. Using the AWS WAF service, you can create rules to control bot traffic, help prevent account takeover fraud, and block common threat patterns such as SQL injection or cross-site scripting (XSS). Further, for those customers managing multi-account environments, it is possible to enforce security baselines for AWS WAF access control lists (ACLs) across the whole organization by using AWS Firewall Manager.
<p>In a previous <a href="https://aws.amazon.com/blogs/security/centrally-manage-aws-waf-api-v2-and-aws-managed-rules-at-scale-with-firewall-manager/" target="_blank" rel="noopener">AWS Security Blog post</a>, there is a good explanation about how to create Firewall Manager policies to deploy AWS WAF ACLs across multiple accounts. In addition, this <a href="https://aws.amazon.com/blogs/architecture/operating-models-for-web-app-security-governance-in-aws/" target="_blank" rel="noopener">AWS Architecture Blog post</a> goes deeper, describing operating models for web applications security governance in <a href="https://aws.amazon.com/" target="_blank" rel="noopener">Amazon Web Services (AWS)</a>. This post will show, in a central or hybrid operating model, how to create a policy to enforce a security baseline in your AWS WAF ACLs while still allowing application administrators or developers to apply specific ACL rules for their particular use case.</p>
<h2>Centrally manage firewall policies</h2>
<p>It’s a common scenario that a security team in an organization wants to implement a security baseline, consisting of a set of rules, across multiple applications that are distributed in multiple accounts. Those rules are not always applicable for all workloads because different applications might have different needs for protection or exposure to the public. Furthermore, sometimes local teams responsible for managing applications have permissions to create their own rules and decide not to follow policies mandated by the organization.</p>
<p>AWS Firewall Manager solves this problem by allowing you to centrally configure and manage firewall policies, deploy preconfigured AWS WAF rules across your organization, and automatically enforce them in existing and newly created resources.</p>
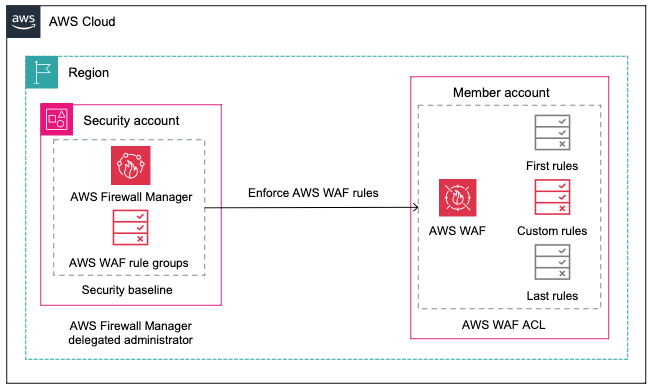
<p>The following architecture diagram describes how you can design a Firewall Manager policy from a central security account, establishing a security baseline that will be enforced within other member accounts in your organization. To do so, you create a managed AWS WAF ACL with the first and last group rules not editable, but allowing a custom rule group to be modified by administrators of member accounts.</p>
<div id="attachment_34124" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-34124" src="https://infracom.com.sg/wp-content/uploads/2024/05/img1-2.png" alt="Figure 1: AWS Firewall Manager enforcing security baseline for AWS WAF" width="648" height="388" class="size-full wp-image-34124">
<p id="caption-attachment-34124" class="wp-caption-text">Figure 1: AWS Firewall Manager enforcing security baseline for AWS WAF</p>
</div>
<h2>Firewall Manager delegated administrators</h2>
<p>At the time of writing this post, Firewall Manager supports up to 10 administrators who can manage firewall resources in your organization by applying scope conditions. For example, you can define an administrator for specific accounts or even a complete organization unit (OU), AWS Region, or policy type. Using this <a href="https://docs.aws.amazon.com/waf/latest/developerguide/fms-administrators.html" target="_blank" rel="noopener">feature</a>, you can enforce the principle of least privilege access, in addition to assigning administrators to enforce security baselines for your AWS ACL rules across your organization in a more granular way. This delegation needs to be completed from the <a href="https://aws.amazon.com/organizations/" target="_blank" rel="noopener">AWS Organizations</a> management account, as shown in Figure 2.</p>
<div id="attachment_34125" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-34125" loading="lazy" src="https://infracom.com.sg/wp-content/uploads/2024/05/img2-2.png" alt="Figure 2: AWS Firewall Manager administrator account delegation" width="650" height="735" class="size-full wp-image-34125">
<p id="caption-attachment-34125" class="wp-caption-text">Figure 2: AWS Firewall Manager administrator account delegation</p>
</div>
<h2>Firewall Manager policies</h2>
<p>A Firewall Manager policy contains the rule groups that will be applied to your protected resources. The service creates a web ACL in each account where the policy is enforced. Account administrators can add rules or rule groups to the resulting web ACL in addition to the rules groups defined by the Firewall Manager policy.</p>
<h3>Rules groups</h3>
<p>AWS WAF ACLs that are managed by Firewall Manager policies contain three sets of rules that provide a higher level of prioritization in the ACL. AWS WAF evaluates rule groups in the following order:</p>
<ol>
<li>Rule groups that are defined in the Firewall Manager policy with the highest priority</li>
<li>Rules that are defined by the account administrator in the web ACL after the first rule group</li>
<li>Rule groups that are defined in Firewall Manager to be evaluated at the end</li>
</ol>
<p>Within each rule set, AWS WAF evaluates rules according to their priority settings, evaluating the rules from the lowest number up until either finds a match that terminates the evaluation or exhausts all of the rules.</p>
<h2>Security baseline policy</h2>
<p>Figure 3 shows an example of a Firewall Manager policy that will serve as the security web ACL baseline across your organization. This policy should be created in a delegated administrator account and enforced across all or specific accounts in your organization where the administrator has permissions. Refer to the <a href="https://docs.aws.amazon.com/waf/latest/developerguide/get-started-fms-create-security-policy.html" target="_blank" rel="noopener">service documentation</a> for additional guidance on setting up this type of policy.</p>
<div id="attachment_34126" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-34126" loading="lazy" src="https://infracom.com.sg/wp-content/uploads/2024/05/img3-2.png" alt="Figure 3: AWS Firewall Manager policy rules acting as the security baseline" width="711" height="695" class="size-full wp-image-34126">
<p id="caption-attachment-34126" class="wp-caption-text">Figure 3: AWS Firewall Manager policy rules acting as the security baseline</p>
</div>
<h3>First rule group</h3>
<p>The first rule group in the policy will contain the following:</p>
<ul>
<li><strong>Organization-level blocked list</strong> – Known bad IP addresses by organization.</li>
<li><strong>AWS IP reputation list</strong> – Recommended AWS managed rules for IP addresses with a bad reputation.</li>
<li><strong>AWS Anonymous IP list</strong> – Recommended AWS managed rules for anonymous IP addresses.</li>
<li><strong>Organization-level rate limit</strong> – A high-level rate limit defined by the organization.</li>
</ul>
<h3>Last rule group</h3>
<p>The last rule group in the policy will contain the following:</p>
<ul>
<li><strong>Organization-level allowed list</strong> – Even if these are well-known IP addresses, they still need to be evaluated against the set of rules enforced by the organization and specific rules per application. If a “good” IP address is supplanted, it might hide the real source identity, bypassing AWS WAF rules.</li>
<li><strong>AWS bot control</strong> – Recommended if you want to enforce bot control across your organization or a set of accounts managed by an administrator.</li>
</ul>
<p>This configuration will allow individual account administrators to define and include their own rules to protect applications based on specific use cases and the expected number of requests.</p>
<p>When designing your own security baselines, take into consideration that some managed rules, such as bot control, might have additional cost, and enforcing them across your organization would increase the overall cost of the service.</p>
<h3>Policy scope</h3>
<p>The policy scope for your security baseline defines where the policy applies. It can apply to all accounts and resources in your organization or just a subset of accounts and resources. Based on the settings selected, Firewall Manager will apply policy for accounts in scope by using the following options:</p>
<ol>
<li>All accounts in your organization</li>
<li>Only a specific list of accounts and organization units</li>
<li>All accounts and OUs except a specific list of those to exclude</li>
</ol>
<p>On the other hand, when selecting the scope for resources, you can use the following options:</p>
<ol>
<li>All resources</li>
<li>Resources that have all of the specified tags</li>
<li>All resources except those that have all the specified tags</li>
</ol>
<p>For delegated administrators, scope definition will apply only for accounts, Regions, or OUs defined during the delegation process. Figure 4 shows an example of the scope definition for a policy.</p>
<div id="attachment_34131" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-34131" loading="lazy" src="https://infracom.com.sg/wp-content/uploads/2024/05/img4-2.png" alt="Figure 4: Firewall Manager scope definition" width="650" height="536" class="size-full wp-image-34131">
<p id="caption-attachment-34131" class="wp-caption-text">Figure 4: Firewall Manager scope definition</p>
</div>
<h2>Use case–specific rule groups</h2>
<p>Figure 5 is an example of a specific use case, where AWS WAF administrators in a member account within the Firewall Manager policy scope want to protect their web application by using the following rules.</p>
<div id="attachment_34132" class="wp-caption aligncenter">
<img aria-describedby="caption-attachment-34132" src="https://infracom.com.sg/wp-content/uploads/2024/05/img5.png" alt="Figure 5: Web ACL managed by Firewall Manager containing rules in a member account" width="780" class="size-full wp-image-34132">
<p id="caption-attachment-34132" class="wp-caption-text">Figure 5: Web ACL managed by Firewall Manager containing rules in a member account</p>
</div>
<h3>Middle rule group</h3>
<p>The middle rule group is configured in each account within the ACL deployed by Firewall Manager. The examples from Figure 5 are rules oriented to apply protection that is specific for the application where the ACL is assigned:</p>
<ul>
<li><strong>App-level blocked list</strong> – Known IP addresses blocked by the administrator.</li>
<li><strong>App-level rate limit</strong> – The rate limit supported by the application.</li>
<li><strong>Core rule set</strong> – The recommended rule set, focused on OWASP Top Ten vulnerabilities.</li>
<li><strong>Technology-specific protection</strong> – An example for PHP applications.</li>
<li><strong>App-level allowed list</strong> – Well-known IP addresses that still need to be evaluated against some rules but bypass others, such as fraud prevention.</li>
<li><strong>Account takeover prevention</strong> – This managed rule needs specific configuration per application to work as expected. However, it is recommended that you use it after the bot control managed rule to optimize cost. Take that into consideration when building your own security baseline.</li>
</ul>
<p>This rule group will be second priority between the first and the last rule groups coming from the Firewall Manager policy. This configuration provides account administrators the ability to design their set of rules to cover the specific use case for their application and also the possibility to override rules evaluated in a lower priority (last rule group). For example, having a higher rate limit in the app-level rule than the org-level rule would have no impact on the traffic being filtered, since the org-level rule in the first group of the policy will have priority. However, having more granular bot control rules at the app-level will supersede the org-level rules contained in the last group of the policy. Take that logic into consideration when you decide which rules need to be in the first and last groups of your Firewall Manager policies.</p>
<h2>Recommended approach for testing</h2>
<p>Before you deploy your web ACL implementation for production, test and tune it in a staging or testing environment until you are comfortable with the potential impact on your traffic. Then, test and tune the rules in count mode with your production traffic before enabling them.</p>
<ol>
<li>Prepare the environment for testing:
<ol>
<li>Enable <a href="https://docs.aws.amazon.com/waf/latest/developerguide/web-acl-testing-prep.html" target="_blank" rel="noopener">logging</a> and web request sampling for your ACL.</li>
<li>Set the protection to count mode.</li>
<li>Associate the ACL with a resource.</li>
</ol> </li>
<li>Monitor and tune in the test environment:
<ol>
<li><a href="https://docs.aws.amazon.com/waf/latest/developerguide/web-acl-testing-activities.html" target="_blank" rel="noopener">Monitor traffic</a> and rules matching by using logs, metrics, the <a href="https://aws.amazon.com/blogs/security/introducing-the-aws-waf-traffic-overview-dashboard/" target="_blank" rel="noopener">dashboard</a>, or sampled requests.</li>
<li>Configure mitigation rules such as false positive, matching, scope-down, and label match.</li>
</ol> </li>
<li>Enable protection in production:
<ol>
<li>Remove any additional rules that are no longer needed.</li>
<li>Enable rules in production accounts.</li>
<li>Closely monitor your application behavior to be sure requests are being handled as expected.</li>
</ol> </li>
</ol>
<h2>Cleanup</h2>
<p>To avoid unexpected charges in your accounts, delete any unnecessary policies and resources. You can do that from the console by following these steps.</p>
<ol>
<li>On the Firewall Manager policies page, choose the radio button next to the policy name, and then choose <strong>Delete</strong>.</li>
<li>In the <strong>Delete</strong> confirmation box, select <strong>Delete all policy resources</strong>, and then choose <strong>Delete</strong> again.</li>
</ol>
<p>AWS WAF removes the policy and any associated resources, like web ACLs, that it created in your account. The changes might take a few minutes to propagate to all accounts.</p>
<h2>Conclusion</h2>
<p>By using Firewall Manager, you can take advantage of native cloud features to enforce security baseline configurations for your AWS WAF rules in a multi-account environment across your organization. It is possible to centrally design policies with broad rule groups to protect workloads from a high-level perspective while allowing application administrators to design custom rules to protect, for instance, web applications from specific use cases such as OWASP Top Ten or technology-related vulnerabilities.</p>
<p>The examples provided in this post can be further customized and adapted to align with your organization’s needs. Design policies to comply with security requirements and specific use cases to protect your workloads.</p>
<p>If you want to learn more, visit the <a href="https://aws.amazon.com/solutions/implementations/automations-for-aws-firewall-manager/" target="_blank" rel="noopener">Automations for AWS Firewall Manager</a> webpage, which provides a solution with preset rules to create a quick security baseline to protect against distributed denial of service (DDoS).</p>
<p> <br>If you have feedback about this post, submit comments in the<strong> Comments</strong> section below. If you have questions about this post, <a href="https://console.aws.amazon.com/support/home" target="_blank" rel="noopener noreferrer">contact AWS Support</a>.</p>
<p><strong>Want more AWS Security news? Follow us on <a title="Twitter" href="https://twitter.com/AWSsecurityinfo" target="_blank" rel="noopener noreferrer">X</a>.</strong></p>
<!-- '"` -->
