How to customize habits of AWS Managed Guidelines for AWS WAF
AWS Managed Rules for AWS WAF offers a group of rules developed by AWS you can use help protect you against common application vulnerabilities along with other unwanted usage of your systems and never have to write your personal rules. AWS Threat Research Team updates AWS Managed Rules to react to an ever-changing threat landscape to be able to protect your applications.Recently, AWS WAF launched four new features which are devoted to rule customization:
- Labels – Metadata that may be put into web requests whenever a rule is matched. Labels may be used to alter the default or behavior action of managed rules.
- Version management – It is possible to decide on a specific version of a managed rule group. Versioning may be used to go back to tested versions previously.
- Scope-down statements – Use to narrow the scope of the requests a rule group evaluates.
- Custom responses – Send a custom HTTP response back again to your client from AWS WAF whenever a rule blocks a link request.
In this website, we proceed through four use cases to show ways to use these features to boost your security posture by customizing managed rules.
Case 1: Control automatic updates for a managed rule group by choosing the specific version
Automagically, managed rule groups are updated as updates become available automatically. This ensures you have the most recent protection when it’s available. With the version management feature, it is possible to choose to stick to a specific version, and therefore it won’t update and soon you move to a more recent version explicitly. This allows one to test a fresh version and promote it to your online ACL when you’re ready, also to go back to a tested version if necessary previously.
Note: It’s recommended that you utilize a version as as you possibly can to the most recent close.
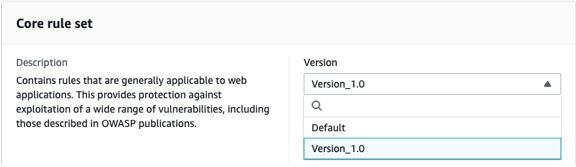
To choose a managed rule group version
- In your AWS WAF console, demand web ACL where you’ve added a managed rule group.
- Choose the managed rule group whose version you intend to set, and choose Edit.
- In the Version selection drop down, choose the version you intend to use. You’ll stick to this version before version expires or you decide on another version-you’ll learn to manage version expiration later in this article.
Note: In the event that you automatically desire to receive updates, select Default because the version.
- Choose Save Rule to save lots of the configuration.
 Figure 1: Console screenshot showing the AWS Managed Rules version drop down
Figure 1: Console screenshot showing the AWS Managed Rules version drop down
Setup notifications
You should use Amazon Simple Notification Service (Amazon SNS) to obtain notifications of updates to a managed rule group. It is possible to sign up to the SNS topic utilizing the ARN of the managed rule group. Every SNS notification for AWS Managed Rules updates uses exactly the same message format, which lets you programmatically consume these updates. For additional information on the SNS notification message format, see Getting notified of new updates and versions to a managed rule group.
To create email notifications on new rule updates through Amazon SNS
- In your AWS WAF console, demand web ACL where you added the managed rule group.
- Choose the managed rule group that you would like to get notifications for, and choose Edit.
- On the Core rule set page, search for the Amazon SNS topic ARN. Choose the link to go directly to the Amazon SNS console. Take note of the topic ARN to utilize in step 4.
 Figure 2: Console screenshot highlighting the SNS topic ARN
Figure 2: Console screenshot highlighting the SNS topic ARN
- On the Create subscription page, enter the next information:
Topic ARN: Enter the SNS topic ARN from step three 3.
Protocol: Select Email.
Endpoint: Enter the e-mail address where you need notifications sent.
 Figure 3: SNS Create subscription console screenshot
Figure 3: SNS Create subscription console screenshot
- Choose Create subscription.
- Watch out for a confirmation email from Amazon SNS. Pick the confirm subscription link in the e-mail to perform the subscription.
Create a version expiration alert utilizing a CloudWatch alarm
Once you stay on a particular version of managed rule group for a long period, there’s a risk that you may miss important updates. To ensure you don’t stick to a stale version for very long time, you should create an alarm to alert you whenever a version is near expiring. Whenever a version expires, the managed rule group switches to the default version automatically. To be notified whenever a version is approximately to expire, setup an alert utilizing an Amazon CloudWatch alarm predicated on DaysToExpiry. You should use the following procedure to create a notification 60 days before a particular version of the rule set you’re using expires.
To create a CloudWatch alarm
This can notify you 60 days before a particular version of a rule set expires
- Demand CloudWatch console.
- Select All metrics from the left navigation pane, and select < then;strong>WAFV2 from the set of namespaces.
- Choose ManagedRuleGroup, Region, Vendor, Version.
- Choose the managed rule group whose expiration you intend to monitor. This example uses AWSManagedRulesCommonRuleSet and Version_1.0.
- Select Graphed metric and choose the bell alarm icon on the low right, under Actions. Selecting this icon shall take one to the CloudWatch alarms console.
 Figure 4: CloudWatch Graphed metrics tab
Figure 4: CloudWatch Graphed metrics tab
- Configure the CloudWatch alarm with the next details, and choose < then;strong>Next:
Statistic: Select Minimum
Period: Select 5 minutes
Threshold Type: Select Static
Operator: Select Lower/Equal (<=threshold)
Threshold: Enter the worthiness as 60
Datapoints to alarm: Enter the low value as 1 and higher value as 1
Missing data treatment: Select Treat missing data nearly as good (not breaching threshold) - Choose the SNS topic that you would like to be launched once the configured alarm would go to ALARM state and choose Next.
- Enter a genuine name and description for the Alarm. Choose Next to preview the configuration and choose Create Alarm to perform the CloudWatch alarm creation process.
Additional tips
- If the version of a managed rule group that you’re using has expired, AWS WAF shall prevent any configuration change to the net ACL until you decide on a valid version. You need to move onto the most recent version as as you possibly can which means you are covered contrary to the latest threats soon.
- You shall only have the DaysToExpiry metric if you find traffic flowing during your web ACL.
- You should use two different versions of a managed rule group in a web ACL. This is useful if you wish to test two different versions simultaneously to observe how they’ll affect your traffic once deployed-for example, have one version in count mode and another in block mode.
Note: This workflow is supported through the JSON rule API and editor, however, not through the console.
Case 2: Use labels to mitigate false positives the effect of a rule in a managed rule group
A label is metadata a rule can truly add to matching web requests, of the action from the rule regardless. The most recent version of AWS Managed Rules supports labels. By creating custom rules that match requests which have labels, it is possible to change the default or behavior action of rules in the managed rule group.
For instance, when you have a rule that’s causing a false positive in a managed rule group, it is possible to mitigate it by overriding the managed rule to Count and writing a custom rule with logic like the following:
IF (Statement 1) AND NOT (Statement 2) THEN Block
Statement 1 matches on the label generated from the rule causing a false positive.
Statement 2 contains exception conditions for once you don’t want the rule to judge because it’s causing false positives.
Look at a scenario where redirection requests to the application are blocked because of the rule GenericRFI_QUERYARGUMENTS in the managed rule group you’re using. This rule inspects the worthiness of most query parameters and blocks requests that try to exploit remote file inclusion (RFI) in web applications, such as for example :// embedded by way of a URL midway. An example of the best redirection request that might be blocked because of the characters :// within the query argument scope could possibly be the following:
https://ourdomain.com/sso/complete?scope=email profile https://www.redirect-domain.com/auth/email https://www.redirect-domain.com/auth/profile
To avoid similar legitimate requests from being blocked, it is possible to write a custom rule to complement in line with the label.
Step one 1: Set the precise managed rule group to count mode
Step one is to set the precise managed rule to count mode, in order that labels are put into the matching requests. Next, the priority of the managed rule should be set greater than the priority of the custom rule.
To create the precise managed rule group to count mode
- In your AWS WAF console, navigate to your online ACL and choose the Rules tab. Choose Add Rule, and select Add managed rule groups.
- Select AWS managed rule groups.
- Under Rule groups< free;/strong>, search for Core rule set and add it to your online ACL by selecting the toggle Increase web ACL.
- Choose Edit.
- From the set of rules, set the rule generating false positives to the Count action, by selecting the Count beside the rule toggle. The action is changed by this example for the rule GenericRFI_QUERYARGUMENTS to Count. This means that all of the matching requests are delivered to the next WAF rules to be able of priority and adds the label awswaf:managed:aws:commonruleset:GenericRFI_QueryArguments whenever there’s a matching request.
- Choose on Save rule.
- Choose Add rules again to visit the next window where you are able to set the rule priority. The managed rule will need to have a higher priority compared to the custom rule that you’ll create within the next steps.
- Choose Save to save lots of the configuration.
Step two 2: Put in a custom rule to the net ACL with lower priority compared to the managed rule
Develop a custom rule in the net ACL that blocks requests if it gets the label that you will be searching for and doesn’t have the exception condition that caused the false positive. The priority of the custom rule ought to be set less than the managed rule.
To include a custom rule with lower priority compared to the managed rule
- In your AWS WAF console, navigate to your online ACL Rules tab and choose Add Rule and choose Add my very own rule and rules groups.
- Select Rule Builder for the rule type.
- Enter a Rule Name and choose Regular Rule because the Type.
- Utilize the In case a request drop right down to select matches all of the statements (AND).
- Statement 1 checks if the request gets the label that you’re searching for. In this example it really is configured with the next details:
Inspect: Select Includes a label
Labels: Select Label
Match key: Select awswaf:managed:aws:commonruleset:GenericRFI_QueryArguments - All subsequent statements should be negated so the requests don’t match the statement criteria and you will be treated as legitimate requests. In this example, we set NOT Statement 2, that checks if the request contains https://www.redirect-domain.com/ in its query string:
Enable: Select Negate statement results
Inspect: Select All query parameters
Match type: Select Contains string
String to Match: Enter https://www.redirect-domain.com/
Text transformation: Select None - Under Action, select Block and choose Add rule.
- In the Set rule Priority window, set the rule priority of one’s custom rule to lessen compared to the AWS Managed Rules rule.
- Choose Save.
Case 3: Work with a scope-down statement to narrow the scope of traffic matching a managed rule group
A scope-down statement could be put into any rule group to narrow the scope of the requests a rule group evaluates. This enables one to either filter in the requests that you would like the rule group to inspect or filter any requests that doesn’t meet the requirements.
Look at a case where you’ve got a list of trusted Ip that you don’t desire to be evaluated against AmazonIPReputationList. It is possible to avoid blocking these trusted IP addresses with a scope-down statement to exclude the traffic from evaluation.
Step one 1: Create the IP set for allowed set of IPs
Step one would be to create an IP set which has the allowed set of IPs. The IP set could be created for a specific AWS Region, or could be global if the net ACL is connected with an Amazon CloudFront distribution.
To create an IP set
- Choose IP sets in the AWS WAF console and choose < then;strong>Create IP set.
- In IP set name enter Allowed IPs. Enter the IPs that you would like to permit in IP addresses. Choose Create IP set when done.
 Figure 5: Console screenshot creating an IP set
Figure 5: Console screenshot creating an IP set
Step two 2: Put in a scope-down statement to the managed rule group
You have created the IP set once, you can include a scope down statement in your managed rule group in order that traffic from the IPs in the IP set aren’t evaluated contrary to the rules in the managed rule group.
To include a scope-down statement
- On the Rules tab of you your online ACL, choose Add Rule and choose Add managed rule groups.
- Select AWS managed rule groups.
- Under Free rule groups, start Amazon IP reputation list to include it to the net ACL and choose Edit.
- Select Enable scope-down statement.
 Figure 6: Console screenshot showing enabling the scope-down statement
Figure 6: Console screenshot showing enabling the scope-down statement
- Add the problem in order that only the requests that don’t result from the allowed IPs list created earlier are evaluated because of this rule group. Utilize the In case a request drop right down to select doesn’t match the statements (NOT).
Inspect: Select Hails from an Ip in
IP set: Select Allowed-IPs
Ip to use because the originating address: Select Source IP address
 Figure 7: Scope down statement configuration console screenshot
Figure 7: Scope down statement configuration console screenshot
- Choose Save rule to include this rule to your online ACL.
Case 4: Use custom responses to improve the default block action for a managed rule group
AWS WAF sends back response code 403 (forbidden) when it blocks an incoming request. You should use the custom response feature to instead send a custom HTTP reaction to the client once the rule blocks access back. Utilizing the custom response, it is possible to customize the status code, response headers, and response body.
Let’s say you intend to respond back to litigant who may be connecting to the application over VPN. You intend to use a custom reaction to inform the user that behavior is discouraged, by sending error code 400 (Bad Request) and a static body message (“Please don’t make an effort to connect over a VPN”). To get this done, you should use the AWS Managed Rule group AWSManagedRulesAnonymousIpList and create custom rules utilizing the label < then;span>awswaf:managed:aws:anonymous-ip-list:AnonymousIPList.
Step one 1: Develop a custom response body
Step one in developing a custom response would be to develop a custom response body. This is actually the message which will be shown once the custom response is sent.
To make a custom response body
- In the AWS WAF console, open your online ACL and choose the Custom response bodies tab.
- Choose Create custom response body.
- In Response body object name, enter a genuine name because of this response-for example, Custom-body-IP-list.
- Select a Content type for the response body.
- In Response body, enter the response that you would like to send to your client back.
- Choose Save.
 Figure 8: Custom response body creation on the AWS WAF console
Figure 8: Custom response body creation on the AWS WAF console
Step two 2: Override what of the managed rule group
The rule you utilize to send your custom response ought to be in count mode. This can ensure that all of the matching requests are delivered to the next WAF rules in priority order. In the next example, the rule AnonymousIPList in the managed rule group AWSManagedRulesAnonymousIpList is defined to count mode. For additional information on how best to override the action of a managed rule group, see Overriding what of a rule group or its rules.
 Figure 9: console screenshot overriding an AWS Managed Rules rule
Figure 9: console screenshot overriding an AWS Managed Rules rule
Step three 3: Develop a rule to block the request and send a custom response back again to the client
You’ll utilize the AWS WAF labels feature because of this step. As explained in the event 2 above, you will need to make a custom rule that matches the label generated by the managed rule. In cases like this the, custom rule ought to be configured to send your custom response.
To make a custom rule
- Expand the Custom response section and choose Enable.
- Under Response code, enter the custom HTTP status code you intend to send to your client back.
- (Optional) Utilize the Response headers section if you want to put in a custom response header
- Under Choose the way you wish to specify the response body, choose the custom response body you created in Step one 1.
- (Optional) If you want to generate additional labels to track activity in logs, you should use Add label.
- Choose Add rule.
- Set the rule priority of one’s custom rule to lessen compared to the AWS Managed Rules rule.
- Choose Save.
 Figure 10: Console screenshot configuring a custom response body for a rule
Figure 10: Console screenshot configuring a custom response body for a rule
Summary
In this article, we demonstrated the way the new AWS WAF features such as for example labels, version management, scope-down statements, and custom responses might help you customize the behavior of AWS Managed Rules to safeguard your online applications and minimize risk. You should use these features in a variety of ways, such as for example customizing AWS Managed Rules by combining labels and request properties to permit or block requests, and using labels to greatly help filter logs.
It is possible to find out about AWS WAF in other AWS WAF-related Security Blog posts.
When you have feedback concerning this post, submit comments in the Comments section below.
Want more AWS Security news? Follow us on Twitter.

You must be logged in to post a comment.