How Security Operation Facilities may use Amazon GuardDuty to detect malicious behavior
The Security Operations Middle (SOC) includes a tough job. As clients modernize and change to cloud architectures, the opportunity to monitor, detect, and react to risks poses different problems.
In this article we address how Amazon GuardDuty may address some common worries of the SOC concerning the number of security equipment and the overhead to integrate and manage them. The GuardDuty is explained by us service, how the SOC may use GuardDuty risk lists, filtering, and suppression guidelines to tune detections and decrease sound, and the intentional design utilized to define and categorize GuardDuty getting forms to quickly give comprehensive information about detections.
Today, the normal SOC has between 10 and 60 tools for managing protection. Some larger SOCs might have more than 100 tools, which are point solutions that don’t integrate with one another mostly.
The security marketplace is flush with niche security tools it is possible to deploy to keep track of, detect, and react to events. Each device has operational and specialized overhead by means of designing system uptime, sensor deployment, information aggregation, device integration, deployment plans, software and server maintenance, and licensing.
Tuning your detection techniques can be an example of an activity with both operational plus technical overhead. To boost your signal-to-sound ratio (S/N), the security techniques you deploy need to be tuned to your atmosphere also to emerging risks which are relevant to your atmosphere. Improving the S/N issues for SOC teams since it reduces effort and time spent on actions that don’t bring worth to an organization. Hanging out tuning detection techniques reduces the exhaustion elements that effect your SOC analysts. Tuning is technical highly, yet it’s furthermore operational because it’s an activity that proceeds to evolve, therefore you have to manage the procedures and upkeep lifecycle of the infrastructure and equipment that you utilize in tuning your detections.
Amazon GuardDuty
GuardDuty is really a core area of the modern FedRAMP-certified cloud SOC, since it provides SOC analysts with an easy range of cloud-particular detective capabilities without requiring the overhead of a large numbers of security tools.
GuardDuty is really a continuous security supervising program that analyzes and procedures data from Amazon Virtual Private Cloud (VPC) Flow Logs, AWS CloudTrail event logs that report Amazon Web Providers (AWS) API calls, and DNS logs to supply detection and analysis making use of threat intelligence feeds, signatures, anomaly recognition, and machine learning inside the AWS Cloud. GuardDuty allows you to protect your computer data stored inside S3 also. GuardDuty continually monitors and profiles S3 data access events (generally known as data plane functions) and S3 configurations (handle plane APIs) to detect suspicious routines. Detections include uncommon geo-place, disabling of preventative handles such as for example S3 block public accessibility, or API call styles consistent with an effort to find misconfigured bucket permissions. For a complete set of GuardDuty S3 danger detections, see GuardDuty S3 finding sorts. GuardDuty integrates risk cleverness feeds from CrowdStrike, Proofpoint, and AWS Protection to detect API and system activity from known malicious IP addresses and domains. It uses machine understanding how to identify unfamiliar and unauthorized and malicious activity inside your AWS environment potentially.
The GuardDuty team continually monitors and manages the tuning of detections for threats linked to contemporary cloud deployments, however your SOC may use trusted IP and threat lists and suppression guidelines to implement your personal custom tuning to suit your unique environment.
GuardDuty is integrated with AWS Organizations, and customers may use AWS Organizations to associate associate accounts with the GuardDuty management accounts. AWS Companies helps automate the procedure of allowing and disabling GuardDuty at the same time across several AWS accounts which are in your handle. Note that, around this writing, you could have one management account also to 5 up,000 member accounts.
Operational overhead is close to zero. You can find no sensors or agents to deploy or manage. You can find no servers to create, deploy, or manage. There’s nothing at all to patch or improve. There aren’t any kind of available architectures to create highly. You have to purchase a registration to a threat cleverness provider don’t, manage the influx of danger data and most significantly, you don’t need to invest in normalizing all the datasets to facilitate correlation. Your SOC may enable GuardDuty with an individual API or click contact. This is a multi-account service where one can develop a management account, in the security account typically, that may read all findings info from the known associate accounts for quick centralization of detections. When deployed in a Management/Member design, GuardDuty offers a flexible model for centralizing your enterprise threat detection capability. The management account can control certain member settings, like upgrade intervals for Amazon CloudWatch Events, usage of threat and trusted lists, creation of suppression rules, opening tickets, and automating remediations.
Filter systems and suppression guidelines
When GuardDuty detects potential malicious activity, it runs on the standardized finding format to communicate the facts concerning the specific finding. The facts in a finding could be queried in filter systems, displayed as saved guidelines, or useful for suppression to improve presence and reduce analyst exhaustion.
Suppress results from vulnerability scanners
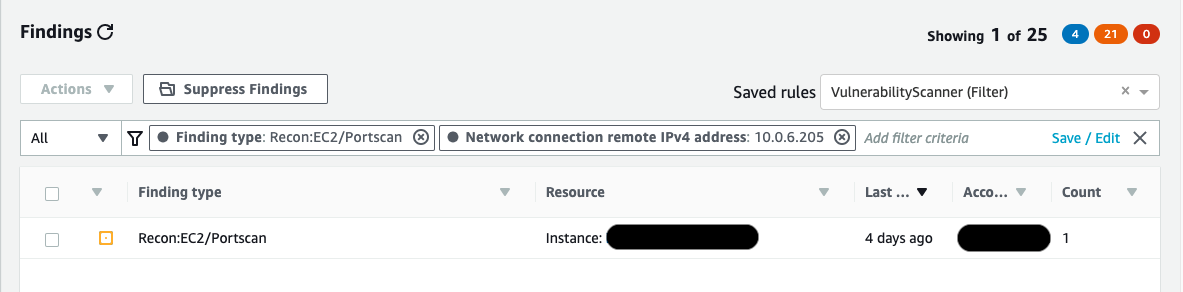
A common exemplory case of tuning your GuardDuty deployment is by using suppression rules to automatically archive new Recon:EC2/Portscan findings from vulnerability assessment tools in your accounts. It is a best practice made to reduce analyst and S/N fatigue.
The initial criteria in the suppression rule should utilize the Getting type attribute with a value of Recon:EC2/Portscan. The next filter criteria should match up the instances or instance that host these vulnerability assessment tools. You may use the Example image ID attribute, the System connection remote IPv4 tackle, or the Tag value attribute based on what criteria is definitely identifiable with the situations that host these equipment. In the instance shown in Figure 1, we utilized the remote control IPv4 address.
 Body 1: GuardDuty filter for vulnerability scanners
Body 1: GuardDuty filter for vulnerability scannersFilter on activity that has been not blocked by safety NACL
or groups
If you would like visibility in to the GuardDuty detections that weren’t blocked by precautionary measures such as a system ACL (NACL) or protection group, you can filtration system by the attribute Network link blocked = False, as shown in Figure 2. This may provide visibility into possible adjustments in your filtering technique to reduce your risk.
 Amount 2: GuardDuty filter for action not blocked by safety groups on NACLs
Amount 2: GuardDuty filter for action not blocked by safety groups on NACLsFilter on particular malicious IP addresses
Some customers desire to track particular malicious IP addresses to see if they are generating results. If you need to see whether an individual source IP deal with is in charge of CloudTrail-based findings, it is possible to filter by the API caller IPv4 tackle attribute.

Figure 3: GuardDuty filter for particular malicious IP deal with
Filter on particular threat provider
Maybe you wish to know just how many findings are generated from the threat intelligence service provider or your personal threat lists. It is possible to filtration system by the attribute Threat list name to notice if the possible attacker will be on a threat checklist from CrowdStrike, Proofpoint, AWS, or your risk lists that you uploaded to GuardDuty.
 Determine 4: GuardDuty filter for specific threat cleverness list provider
Determine 4: GuardDuty filter for specific threat cleverness list provider< h3>Finding formats and types
Now that you understand a little more around GuardDuty and tuning results through the use of suppression and filters guidelines, let’s dive in to the finding types which are generated by way of a GuardDuty detection. The very first thing to understand is that GuardDuty findings utilize the following model:
This model is supposed to communicate core information to security teams on the type of the potential risk, the AWS resource types which are impacted, and the threat family name, variants, and artifacts of the detected activity in your account. The Threat Purpose field describes the principal reason for a threat or perhaps a potential try on your environment.
Let’s take the Backdoor:EC2/C&CActivity.B!DNS acquiring as an example.
The Backdoor threat purpose indicates an effort to bypass normal security controls on a particular Amazon Elastic Compute Cloud (EC2) instance. In this illustration, the EC2 example in your AWS atmosphere can be querying a domain title (DNS) of a known order and control (C&CActivity) server. It is a high-intensity finding, because you can find good enough indicators that malware will be on your sponsor and performing with malicious intent.
GuardDuty, at the proper time of the writing, supports the next finding types:
- Backdoor finding varieties
- Behavior finding forms
- CryptoCurrency finding sorts
- PenTest finding varieties
- Persistence finding forms
- Policy finding sorts
- PrivilegeEscalation finding varieties
- Recon finding forms
- ResourceConsumption finding sorts
- Stealth finding varieties
- Trojan finding forms
- Unauthorized finding sorts
OK, you know concerning the model for GuardDuty results now, but so how exactly does GuardDuty work?
Once you enable GuardDuty, the ongoing service evaluates events within both a stateless and stateful way, which allows us to utilize device learning and anomaly recognition along with signatures and threat cleverness. Some stateless for example the Backdoor:EC2/C&CActivity.B!DNS or the CryptoCurrency:EC2/BitcoinTool.B getting types, where GuardDuty just needs to visit a single DNS query, VPC Flow Log access, or CloudTrail report to detect potentially malicious activity.
Stateful detections are motivated by anomaly machine and detection learning models that identify behaviors that deviate from the baseline. The device learning detections generally require more time to teach the models and possibly use multiple activities for triggering the recognition.
The normal triggers for behavioral detections vary in line with the log source and the recognition in question. The behavioral detections find out about typical consumer or network activity to create a baseline, and the anomaly detections differ from a learning setting to a dynamic mode. In active setting, you only see results generated from these detections if the ongoing provider observes behavior that indicates a deviation. Some examples of device learning-based detections are the Backdoor:EC2/DenialOfService.Dns, UnauthorizedAccess:IAMUser/ConsoleLogin, and Behavior:EC2/NetworkPortUnusual finding types.
Exactly why does this issue?
The SOC is well known by us gets the tough work of keeping companies secure with limited assets, and with a higher amount of operational and complex overhead because of large portfolio of equipment. This can influence the opportunity to detect and react to security events. For instance, CrowdStrike tracks the idea of breakout time-the windowpane of time from when another celebration first gains unauthorized usage of an endpoint machine, to if they start moving across your system laterally. They identified typical breakout periods are between 19 mins and 10 hours. If the SOC will be overburdened with undifferentiated operational and specialized overhead, it can battle to improve monitoring, recognition, and response. To do something quickly, we need to decrease detection period and the overhead burden on the SOC due to the many tools used. The ultimate way to decrease detection time has been threat machine and intelligence studying. Threat intelligence can offer context to alerts and provides a broader viewpoint of cyber risk. Device learning makes use of baselines to identify what normal appears like, enabling recognition of anomalies in source or user behavior, and heuristic threats that modification over time. The easiest method to decrease SOC overhead would be to share the strain so that AWS solutions manage the undifferentiated large lifting, as the SOC targets more specific duties that add worth to the organization.
GuardDuty is really a cost-optimized service that’s in scope for the FedRAMP and DoD compliance programs in america commercial and GovCloud Areas. It leverages threat device and intelligence understanding how to provide detection features without you needing to manage, maintain, or patch any manage or infrastructure just one more security tool. With a 30-day trial period, there is absolutely no risk to judge the ongoing service and find out how it could support your cyber risk strategy.
In order to receive automated updates about GuardDuty, it is possible to subscribe to an SNS notification which will email you whenever fresh features and detections are released.
When you have feedback concerning this post, submit remarks in the Comments section below. Should you have questions concerning this post, start a brand-new thread on the Amazon GuardDuty forum or contact AWS Support.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.
