How exactly to revoke federated users’ dynamic AWS sessions
By using a centralized identity service provider (IdP) for human consumer access, changes an identity administrator helps make to a consumer within the IdP won’t invalidate the user’s existing active Amazon Web Services (AWS) sessions. That is because of the nature of program durations which are configured on assumed functions. Challenging is presented by this example for identity administrators.
<pre> <code> <p>In this article, you’ll learn to revoke usage of specific users’ periods on AWS assumed functions by using <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/accessibility_policies.html" focus on="_blank" rel="noopener">AWS Identity and Accessibility Management (IAM) plans</the> and <a href="https://docs.aws.amazon.com/organizations/newest/userguide/orgs_manage_policies_scps.html" focus on="_blank" rel="noopener">service control guidelines (SCPs)</the> via <a href="https://aws.amazon.com/organizations/" focus on="_blank" rel="noopener">AWS Organizations</the>.</p>
<h2>Program duration overview</h2>
<p>Once you configure IAM functions, the choice is had by you of configuring a <a href=”https://docs.aws.amazon.com/IAM/most recent/UserGuide/id_functions_use.html#id_functions_use_view-role-max-session” focus on=”_blank” rel=”noopener”>maximum program duration</the> that specifies what sort of session is valid very long. By default, the short-term credentials provided to an individual shall last for just one hour, but you can transform this to a value of to 12 hours up.</p>
<p>Whenever a user assumes a job in AWS through the use of their IdP credentials, that role’s credentials shall remain valid for along their session duration. It’s convenient for customers to get a maximum session length set to 12 hrs, because this prevents their classes from timing out and requiring re-login frequently. However, a session timeframe also poses challenging if you longer, being an identity administrator, try to revoke or change a user’s usage of AWS from your own IdP.</p>
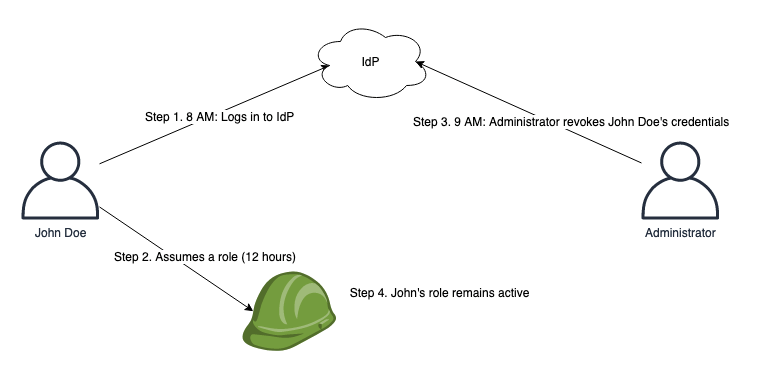
<p>For instance, user SOMEONE IN PARTICULAR is leaving the business and you desire to verify that John has his privileges within AWS revoked. If John provides access to IAM functions with long-session durations, he then might have residual usage of AWS despite getting his program revoked or his consumer identification deleted within the IdP. Maybe John assumed a job for his daily just work at 8 AM and you revoked his credentials within the IdP at 9 AM. Because John got assumed an AWS function already, he would still get access to AWS during that role throughout the configured session, 8 PM if the program was configured for 12 hours. For that reason, as a security greatest practice, AWS recommends you don’t set the session period length much longer than is necessary. This illustration is displayed in Shape 1.</p>
<div id=”attachment_28066″ course=”wp-caption alignnone”>
<img aria-describedby=”caption-attachment-28066″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/12/22/Picture1.png” alt=”Figure 1: Session duration overview” width=”759″ height=”368″ course=”size-full wp-picture-28066″>
<p id=”caption-attachment-28066″ course=”wp-caption-text”>Figure 1: Session duration review</p>
</div>
<p>To be able to restrict access regardless of the session duration being energetic, you can update the roles which are assumable from an IdP with a deny-all policy or delete the part entirely. However, it is a disruptive actions for the users which have access to this function. If the part has been deleted or the plan was up-to-date to deny all, then customers would no longer have the ability to assume the gain access to or function their AWS environment. Instead, the recommended method would be to revoke access in line with the specific user’s <period>principalId</period> or <period>sourceIdentity</period> ideals.</p>
<p>The <period>principalId</period> may be the unique identifier for the entity that produced the API contact. When requests are created with short-term credentials, such as for example assumed functions through IdPs, this worth includes the session title, such as for example <a href=”mailto:JohnDoe@example.com” focus on=”_blank” rel=”noopener”>JohnDoe@instance.com</the>. The <period>sourceIdentity</period> identifies the initial user identity that’s making the request, like a user who’s authenticated through SAML federation from an IdP. As a greatest exercise, AWS recommends that you configure this worth within the IdP, because this boosts traceability for user periods within AWS. You will find more information with this functionality in your blog blog post, <a href=”https://aws.amazon.com/blogs/security/how-to-integrate-aws-sts-sourceidentity-with-your-identity-provider/” target=”_blank” rel=”noopener”>How exactly to integrate AWS STS SourceIdentity together with your identity provider</the>.</p>
<h2>Recognize the <period>principalId</period> and <period>sourceIdentity</period> through the use of CloudTrail</h2>
<p>You may use <a href=”https://aws.amazon.com/cloudtrail/” focus on=”_blank” rel=”noopener”>AWS CloudTrail</the> to examine the activities taken by way of a user, part, or AWS service which are recorded as activities. In the next procedure, you shall use CloudTrail to recognize the <period>principalId</period> and <period>sourceIdentity</period> within the CloudTrail report contents for the IdP assumed function.</p>
<p><strong>To recognize the <period>principalId</period> and <period>sourceIdentity</period> through the use of CloudTrail</strong></p>
<ol>
<li>Assume a job in AWS simply by signing in during your IdP.</li>
<li>Perform an activity like a <a href=”https://docs.aws.amazon.com/AmazonS3/most recent/userguide/create-bucket-overview.html” focus on=”_blank” rel=”noopener”>creating a good S3 bucket</the>.</li>
<li>Demand CloudTrail services<strong>.</strong></li>
<li>In the routing pane, choose <strong>Occasion Background</strong>.</li>
<li>For <strong>Lookup features</strong>, select <strong>Event title</strong>. For <strong>Occasion title</strong>, enter CreateBucket.</li>
<div id=”attachment_28065″ course=”wp-caption alignnone”>
<img aria-describedby=”caption-attachment-28065″ loading=”lazy” src=”https://infracom.com.sg/wp-content/uploads/2023/01/Image-2-7.png” alt=”Figure 2: Finding out about the CreateBucket event inside the CloudTrail event background” width=”1430″ height=”331″ class=”size-full wp-image-28065″>
<p id=”caption-attachment-28065″ course=”wp-caption-text”>Figure 2: Finding out about the CreateBucket event inside the CloudTrail event background</p>
</div>
<li>Choose the corresponding event document and review the function details. An example displaying the userIdentity element is really as follows.</li>
</ol>
<div course=”hide-language”>
<pre><code class=”lang-text”>
“userIdentity”:
“type”: “AssumedRole”,
“principalId”:
“AROATVGBKRLCHXEXAMPLE:JohnDoe@example.com”,
“arn”: “arn:aws:sts::111122223333:assumed-
role/roleexample/JohnDoe@example.com”,
“accountId”: “111122223333”,
“accessKeyId”: “ASIATVGBKRLCJEXAMPLE”,
“sessionContext”:
“sessionIssuer”:
“type”: “Role”,
“principalId”: “AROATVGBKRLCHXEXAMPLE”,
“arn”:
“arn:aws:iam::111122223333:role/roleexample”,
“accountId”: “111122223333”,
“userName”: “roleexample”
,
“webIdFederationData”: ,
“attributes”:
“creationDate”: “2022-07-05T15:48:28Z”,
“mfaAuthenticated”: “false”
,
“sourceIdentity”: “JohnDoe@illustration.com”
<pre> <code> In this event report, you can view that <period>principalId</period> is <period>“AROATVGBKRLCHXEXAMPLE:JohnDoe@instance.com”</period> and <period>sourceIdentity</period> had been specified as <period>“JohnDoe@illustration.com”</period>. You have these values now, let’s explore ways to revoke access through the use of IAM and SCP plans.</p>
<h2>Make use of an SCP to deny customers based on IdP consumer revoke or title session token</h2>
<p>First, you shall create an SCP, a policy which can be put on an organization to provide central handle of the utmost available permissions over the accounts in the business. More info on SCPs, including measures to generate and apply them, are available in the <a href=”https://docs.aws.amazon.com/organizations/newest/userguide/orgs_manage_policies_scps.html” focus on=”_blank” rel=”noopener”>AWS Organizations User Guideline</the>.</p>
<p>The SCP shall possess a deny-all statement with a disorder for <period>aws:userid</span>, that may evaluate the <period>principalId industry</period>; and a disorder for <period>aws:SourceIdentity</span>, that will evaluate the <period>sourceIdentity industry</period>. In the next example SCP, the customers John Mary and Doe Main are avoided from accessing AWS, in member accounts, of these session duration regardless, because each motion shall check out against their <period>aws:userid</period> and <period>aws:SourceIdentity</span> values and accordingly end up being denied.</p>
<p><strong>SCP to deny entry predicated on IdP user title</strong></p>
<div course=”hide-language”>
<pre><code class=”lang-text”>
"Version": "2012-10-17",
"Statement": [
"Effect": "Deny",
"Action": " <em> ",
"Resource": " </em> ",
"Condition":
"StringLike":
"aws:userid": [
" <em> :JohnDoe@instance.com",
" </em> :MaryMajor@illustration.com"
]
,
"Effect": "Deny",
"Action": " <em> ",
"Resource": " </em> ",
"Condition":
"StringEquals":
"aws:SourceIdentity": [
"JohnDoe@example.com",
"MaryMajor@example.com"
]
]
</code> </pre>
</div>
<h2> Make use of an IAM plan to revoke accessibility in the AWS Agencies management account </h2>
<p> SCPs usually do not affect customers or functions in the AWS Institutions management account and rather only affect the associate accounts in the business. Therefore, utilizing an SCP in order to deny access might not be sufficient alone. However, identification administrators can revoke gain access to similarly of their management account utilizing the following procedure. </p>
<p> <strong> To generate an IAM plan in the management accounts </strong> </p>
<ol>
<li> Register to the <a href="https://console.aws.amazon.com/console/home" target="_blank" rel="noopener"> AWS Management Gaming console </a> through the use of your AWS Organizations administration account credentials. </li>
<li> Stick to <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_create-console.html#access_policies_create-json-editor" target="_blank" rel="noopener"> these tips to utilize the JSON plan editor to generate an IAM plan </a> . Utilize the JSON of the SCP proven in the preceding area, <strong> SCP to deny access predicated on IdP user title </strong> , in the IAM JSON editor. </li>
<li> Adhere to <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_manage-attach-detach.html#add-policies-console" target="_blank" rel="noopener"> these actions to include the IAM plan to functions </a> that IdP customers may presume within the accounts. </li>
</ol>
<h2> Revoke energetic sessions when part chaining </h2>
<p> As of this true point, the user activities on the IdP assumable functions within the AWS corporation have already been blocked. However, there's still an advantage case if the prospective users make use of <a href="https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_terms-and-concepts.html#iam-term-role-chaining" target="_blank" rel="noopener"> function chaining </a> (make use of an IdP <span> assumedRole </span> credential to assume another role) that runs on the various <span> RoleSessionName </span> compared to the one designated by the IdP. In a job chaining situation, the users shall still have admission utilizing the cached credentials for the next role. </p>
<p> That's where the <span> sourceIdentity </span> industry is valuable. Following a source identity is defined, it is within requests for AWS activities that are taken through the role session. The worthiness that's set persists whenever a role can be used to believe another part (role chaining). The worthiness that is set can't be changed through the role session. Thus, it’s suggested that you configure the <span> sourceIdentity </span> industry within the IdP as described previously. This idea is shown in Body 3. </p>
<div id="attachment_28064" class="wp-caption alignnone">
<img aria-describedby="caption-attachment-28064" loading="lazy" src="https://infracom.com.sg/wp-content/uploads/2023/01/Image-3-6.png" alt="Figure 3: Role chaining with sourceIdentity configured" width="945" height="372" class="size-full wp-image-28064" />
<p id="caption-attachment-28064" class="wp-caption-text"> Figure 3: Function chaining with sourceIdentity configured </p>
</div>
<p> A consumer assumes an IAM function via their IdP (#1), and the CloudTrail report shows <span> sourceIdentity: JohnDoe@instance.com </span> (#2). Once the user assumes a fresh role within AWS (#3), that CloudTrail report continues to show <span> sourceIdentity: JohnDoe@illustration.com </span> regardless of the <span> principalId </span> changing (#4). </p>
<p> However, in case a second part is usually assumed in the accounts through function chaining and the <span> sourceIdentity </span> isn't set, then it’s suggested that you revoke the released session tokens for the next role. To carry out this, you may use the SCP plan at the ultimate end of the section, <strong> SCP to revoke active classes for assumed functions </strong> . When this plan can be used by you, the issued credentials linked to the functions specified will undoubtedly be revoked for the customers currently with them, and only customers who were not really denied through the prior SCP or IAM guidelines restricting their <span> aws:userid </span> can reassume the mark roles to secure a new short-term credential. </p>
<p> If this process is used by you, you shall have to use an SCP to use across the firm’s member accounts. The SCP will need to have the human-assumable functions for role chaining detailed and a token concern period set to a particular time when you wish users’ access revoked. (Usually, this right time windows would be set for this time and energy to immediately revoke access, but there could be circumstances where you intend to revoke the entry at another date, such as whenever a user moves to a fresh team or project and for that reason requires different access ranges.) In add-on, you will have to follow the same treatments in your management accounts by developing a customer-managed policy utilizing the exact same JSON with the problem declaration for <span> aws:PrincipalArn </span> taken out. Then attach the client managed plan to the average person roles which are human-assumable through part chaining. </p>
<p> <strong> SCP to revoke energetic sessions for assumed functions </strong> </p>
<div class="hide-language">
<pre> <code class="lang-text">
"Version": "2012-10-17",
"Statement": [
"Sid": "RevokeActiveSessions",
"Effect": "Deny",
"Action": [
" <em> "
],
"Resource": [
" </em> "
],
"Condition":
"StringEquals":
"aws:PrincipalArn": [
"arn:aws:iam:: <em> </em> :function/ <em> </em> ",
"arn:aws:iam:: <em> </em> :part/ <em> </em> "
]
,
"DateLessThan":
"aws:TokenIssueTime": "2022-06-01T00:00:00Z"
]
</code> </pre>
</div>
<h2> Bottom line and final suggestions </h2>
<p> In this website post, I demonstrated ways to revoke a federated user’s active AWS periods through the use of SCPs and IAM plans that restrict the usage of the aws:userid and <span> aws:SourceIdentity </span> problem keys. I furthermore shared ways to handle a job chaining circumstance with the <span> aws:TokenIssueTime </span> condition essential. </p>
<p> This workout demonstrates the significance of configuring the program duration parameter on IdP assumed functions. As a security greatest practice, you need to set the session length to no more than what is had a need to perform the function. In some situations, which could mean an full hr or less in a manufacturing environment and an extended session in a growth environment. Regardless, it’s vital that you understand the influence of configuring the utmost session timeframe in the user’s atmosphere and to have proper techniques set up for revoking a federated user’s accessibility. </p>
<p> This posting also covered the suggestion to create the <span> sourceIdentity </span> for assumed functions through the IdP. This value can't be changed during role sessions and persists whenever a user conducts role chaining therefore. Third , recommendation minimizes the chance that a user may have assumed another part with another session name compared to the one designated by the IdP and aids in preventing the edge case situation of revoking active classes predicated on <span> TokenIssueTime </span> . </p>
<p> Opt for other security guidelines, referred to in the <a href="https://docs.aws.amazon.com/wellarchitected/latest/security-pillar/welcome.html" target="_blank" rel="noopener"> Protection Pillar of the AWS Well-Architected Framework </a> , once you revoke customers’ AWS access. For instance, rotating credentials such as for example IAM gain access to keys in situations where IAM entry keys are regularly utilized and shared among customers. The example options in this post wouldn't normally have avoided a user from executing AWS activities if that user acquired IAM accessibility keys configured for another IAM user in the surroundings. Organizations should limitation long-lived safety credentials such as for example IAM keys and rather rotate them frequently or avoid their make use of altogether. Also, the idea of minimum privilege is very important to control the access that customers have got and scope it exclusively to certain requirements that are had a need to perform their work functions. Lastly, you need to adopt a centralized identification provider in conjunction with the <a href="https://docs.aws.amazon.com/singlesignon/?id=docs_gateway" target="_blank" rel="noopener"> AWS IAM Identity Middle (successor to AWS Individual Sign-On) </a> service to be able to centralize identity administration and avoid the necessity for several credentials for customers. </p>
<p> When you have feedback concerning this post, submit remarks in the <strong> Comments </strong> area below. Should you have questions concerning this post, start a brand-new thread on <a href="https://repost.aws/tags/TAO7Z4bI5hQVWMiYFs34QhIA/aws-identity-and-access-management"> the AWS Identification and Access Administration re:Write-up </a> or <a href="https://console.aws.amazon.com/support/home" target="_blank" rel="noopener"> get in touch with AWS Help </a> . </p>
<p> <strong> Want more AWS Safety news? Stick to us on <a title="Twitter" href="https://twitter.com/AWSsecurityinfo" target="_blank" rel="noopener noreferrer"> Twitter </a> . </strong>
<pre> <code> <!-- '"` -->
</code> </pre>
