How exactly to integrate third-party IdP making use of developer authenticated identities
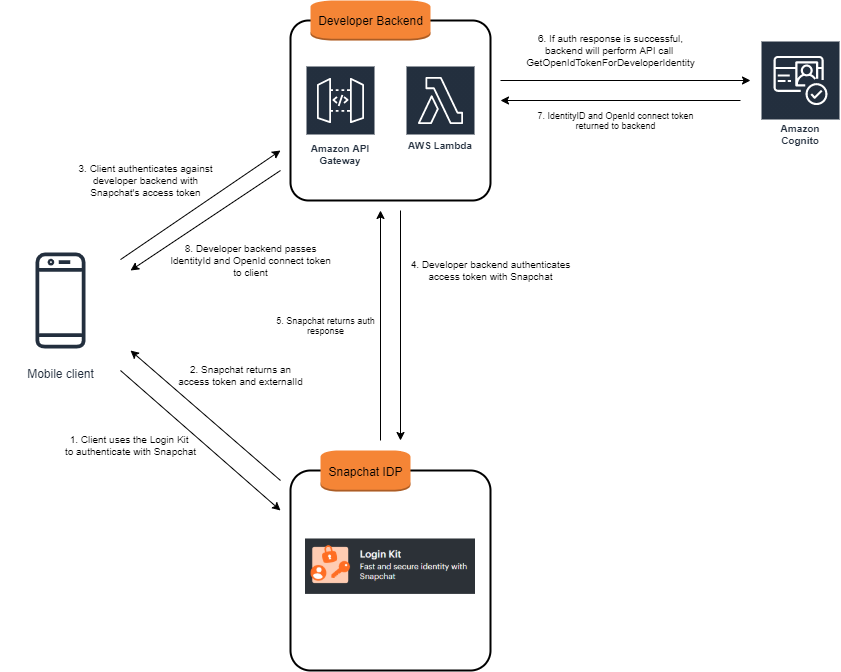
Amazon Cognito identification pools allow you to create and manage special identifiers for the users and offer temporary, limited-privilege credentials to the application to gain access to AWS resources. Presently, there are several from the box external identification suppliers (IdPs) to integrate with Amazon Cognito identification pools, including Facebook, Search engines, and Apple company. If your application’s major users make use of another social media marketing network such as for example Snapchat and you wish to ensure it is easier to allow them to authenticate together with your application, you would have to use programmer authenticated interface and identities making use of their third-party IdP. This website post shall describe what's required from the third-party IdP, developing a scalable backend for authentication, and how exactly to access AWS providers from the client. <p>For example, this post shall use <a href="https://package.snapchat.com/login-kit" focus on="_blank" rel="noopener noreferrer">Snapchat’s Login Package</the> to integrate with Amazon Cognito. The entire authentication circulation for the integration will be shown in Number 1.</p>

Figure 1: Overall authentication stream of integration
Prerequisites
Listed below are the prerequisites for integrating third-party IdP using programmer authenticated identities.
- Your client SDK to authenticate with third-party IdP. This can handle client access and authentication token retrieval. In the illustration in this article, we make use of Snapchat’s Login Package.
- A strategy to authenticate access tokens which are retrieved from the third-party IdP. Because of this blog post, An endpoint has been used by me supplied by Snapchat that will retrieve user information by passing in entry tokens. An effective query of user information indicates the accessibility token is legitimate.
- Programmer authenticated identities (identity pool) configured in Amazon Cognito. You shall have to note the identity pool ID and the programmer provider name you specify.
Customer SDK
Adhere to the third-special event client SDK directions for applying authentication in the application. Snapchat’s Login Package has an SDK to install a login key in your app, also to permit you to authenticate against your Snapchat accounts credentials. Following a consumer clicks on the login switch, they will be redirected to Snapchat to login. After logging in successfully, they’ll be redirected to the application having an access token back. The handleResponseCallback is where you can implement an API contact to your programmer backend, to move your gain access to token to retrieve credentials from Amazon Cognito to gain access to AWS services. The next code instance mounts a login key on your own application, to allow an individual to authenticate with Snapchat and retrieve an entry token.
var loginButtonIconId = "<HTML div id>";
// Mount Login Button
snap.loginkit.mountButton(loginButtonIconId,
clientId: ” “,
redirectURI: ” “,
scopeList: [
“user.display_name”,
“user.bitmoji.avatar”,
“user.external_id”,
],
handleResponseCallback: function (token)
);
<h2>Programmer backend</h2>
The programmer backend is in charge of authenticating accessibility tokens from the third-celebration IdP and exchanging them for an OpenID Connect token which you can use to gain access to AWS services. Because of this example, you shall use Amazon API Gateway with AWS Lambda with the IAM permissions to contact getOpenIdTokenForDeveloperIdentity.
The next is really a code example to authenticate access tokens with Snapchat.
let outcome = await axios(
method: 'post',
url: 'https://package.snapchat.com/v1/me',
headers: 'Content-Kind': 'application/json',
'Authorization': 'Bearer ' + entire body.access_token,
data: "query":"medisplayName bitmojiavatar externalId"
);
successful authentication
After, next you contact getOpenIdTokenForDeveloperIdentity with the identity swimming pool ID and logins map. The logins map includes a mapping of the programmer provider title to an exterior ID from the IdP. An OpenID Connect token and the Amazon Cognito identifier (identification ID) will undoubtedly be returned from the decision, which can be delivered to the application. The identity token and ID may be used to access AWS services. The following is really a code illustration to retrieve AWS credentials after authenticating with Snapchat.
Considerations
Listed below are factors about Amazon Cognito identification pools that you ought to remember when building your remedy.
- The identification ID came back by getOpenIdTokenForDeveloperIdentity will be mapped to the exterior ID supplied in the logins map. This mapping is kept in Amazon Cognito. After that you can utilize the identity ID to recognize who’s calling AWS services, that is ideal for auditing purposes especially.
- This solution would work for multi-regional deployments. All that’s needed is is that the identification is copied simply by you pool to some other AWS Region. Please be aware that the identification ID changes in each Area, but which should not affect efficiency.
Conclusion
Through the use of developer authenticated identities, it is possible to integrate the application with Amazon Cognito and a third-celebration IdP with the correct prerequisites. For more types of using programmer authenticated identities, notice Programmer Authenticated Identities (Identification Pools) in the Amazon Cognito Programmer Guide. For those who have feedback concerning this post, submit remarks in the Comments area below or take up a new thread using one of our community forums .
Want more AWS Safety how-to content, information, and feature announcements? Stick to us on Twitter .
