How exactly to import AWS IoT Gadget Defender audit results into Security Hub
AWS Protection Hub offers a comprehensive see of the protection alerts and security position in your accounts. In this website post, we show ways to import AWS IoT Gadget Defender audit results into Safety Hub . After that you can view and organize Web of Things (IoT) safety findings in Protection Hub as well as findings from additional incorporated AWS services , such as for example Amazon GuardDuty , Amazon Inspector , Amazon Macie , AWS Identity and Gain access to Administration (IAM) Entry Analyzer , AWS Techniques Manager , and much more. You'll gain a centralized protection look at across both IoT and business types of workloads, and also have an aggregated watch of AWS IoT Gadget Defender audit results. This solution can assistance AWS Accounts maintained by AWS Organizations . <p>In this article, you’ll understand how the integration of IoT safety findings into Safety Hub works, and you will < download;a href="http://aws.amazon.com/cloudformation" focus on="_blank" rel="noopener noreferrer">AWS CloudFormation</the> templates to carry out the perfect solution is. After you deploy the answer, every failed audit check out will be recorded as a Protection Hub finding. The findings within Safety Hub has an AWS IoT Gadget Defender finding severity degree and direct connect to the AWS IoT Gadget Defender console to enable you to take possible remediation activities. If you deal with the underlying results or suppress the results utilizing the AWS IoT Gadget Defender console, the perfect solution is function shall automatically archive any related findings in Protection Hub whenever a new audit occurs.</p>
Alternative scope
Because of this alternative, we assume that you will be familiar with how exactly to create an IoT atmosphere and setup AWS IoT Gadget Defender. For more information how to create your environment, start to see the AWS tutorials, such as for example Getting started off with AWS IoT Greengrass and Establishing AWS IoT Gadget Defender
The perfect solution is is supposed for AWS accounts with less than 10,000 findings per scan. If AWS IoT Gadget Defender has a lot more than 10,000 findings, the restriction of 15 minutes throughout the serverless AWS Lambda function may be exceeded, depending on the system delay, and the event shall fail.
The answer is made for AWS Areas where AWS IoT Device Defender, serverless Lambda Security and functionality Hub can be found; for more information, notice AWS Regional Solutions. The China (Beijing) and China (Ningxia) Areas and the AWS GovCloud (US) Regions are usually excluded from the answer scope.
Answer overview
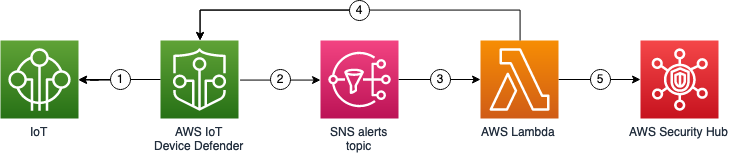
The templates that people provide will provision an < here;a href=”http://aws.amazon.com/sns” focus on=”_blank” rel=”noopener noreferrer”>Amazon Basic Notification Services (Amazon SNS) subject notifying you once the AWS IoT Gadget Defender report is prepared, and a Lambda functionality that imports the results from the document into Security Hub. Shape 1 shows the perfect solution is architecture.

Figure 1: Remedy architecture
The perfect solution is workflow is really as follows:
- AWS IoT Gadget Defender performs an audit of one’s environment. You should setup a normal audit as referred to in Audit guideline: Enable audit checks.
- AWS IoT Gadget Defender sends an SNS notification with a listing of the audit statement.
- The Lambda functionality named import-iot-defender-findings-to-security-hub is set off by the SNS subject.
- The Lambda function gets the facts of the findings from AWS IoT Device Defender.
- The Lambda function imports the brand new findings to Safety archives and Hub the prior report findings. A good example of findings in Protection Hub is demonstrated in Body 2.

Figure 2: Security Hub findings illustration
Prerequisites
- You’ll want Security Hub fired up in your community where you’re deploying the answer.
- You’ll want your IoT atmosphere set also, see step-by-step tutorial at Getting started off with AWS IoT Greengrass
- You’ll want AWS IoT Gadget Defender audit checks fired up also. Figure out how to configure recurring audit checks across all of your IoT devices through the use of this tutorial.
Deploy the answer
You will have to deploy the solution as soon as in each AWS Region where you intend to integrate IoT security findings into Security Hub.
To deploy the solution
- Choose Start Stack to release the AWS CloudFormation system with the prepopulated CloudFormation demo template.

In addition, you can the most recent solution program code from < download;a href=”https://github.com/aws-samples/iot-device-defender-integration-with-securityhub” rel=”noopener noreferrer” focus on=”_blank”>GitHub.
- (Optional) Inside the CloudFormation console, you’re offered the template parameters before you deploy the stack. It is possible to customize these parameters or keep carefully the defaults:
- S3 bucket with sources: This bucket includes all of the solution sources, like the Lambda templates and function. You can keep carefully the default textual content if you’re not really customizing the resources.
- Prefix for S3 bucket with resources: The prefix for all your solution sources. It is possible to keep carefully the default if you’re not really customizing the resources.
- Visit the AWS IoT Primary console and create an SNS alert notification parameter for the audit record. To get this done, in the left routing pane of the system, under Defend, select Configurations, and choose < then;strong>Edit to edit the SNS alert. The answer creates the SNS topic stack and named iot-defender-report-notification.

Figure 3: SNS alert configurations for AWS IoT Gadget Defender
Check the remedy
To check the solution, it is possible to simulate an “AWS IoT plans are permissive” finding by creating an insecure plan overly.
To generate an insecure plan
- Visit the AWS IoT Core gaming console. In the left routing pane, under Secure, select Plans.
- Choose Create. For Title, enter InsecureIoTPolicy.
- For Activity, choose iot:*. For Assets, enter *. Choose Allow declaration, and select Create.
Following, run a fresh IoT security audit by choosing IoT Primary > Defend > Audit > Outcomes > Create and selecting the choice Work audit now (As soon as).
Following the audit is completed, you’ll see audit reviews in the AWS IoT Core console, like the ones shown in Figure 4. Among the reports implies that the IoT policies are usually permissive overly. Exactly the same findings are imported into Security Hub as proven in Figure 2 also.

Figure 4: AWS IoT Gadget Defender review
Troubleshooting
To troubleshoot the perfect solution is, utilize the Amazon CloudWatch Logs of the Lambda functionality import-iot-defender-findings-to-security-hub. The perfect solution is can fall short if:
- Safety Hub isn’t fired up in your Area
- Service control guidelines (SCPs) are preventing usage of AWS IoT Gadget Defender audit reviews
- The incorrect SNS topic is configured in the AWS IoT Device Defender settings
- The Lambda function times because you can find a lot more than 10 out,000 findings
To get these presssing issues, visit the CloudWatch console, choose Log Team, and choose /aws/lambda/import-iot-defender-findings-to-security-hub.
Bottom line
In this article, you’ve learned how exactly to integrate AWS IoT Gadget Defender audit results with Protection Hub to get a centralized see of security findings throughout both your IoT and business workloads. When you have more queries about IoT, it is possible to get to to the < out;a href=”https://forums.aws.amazon.com/discussion board.jspa?forumID=210″ target=”_blank” rel=”noopener noreferrer”>AWS IoT discussion board, and when you have questions around Security Hub, go to the AWS Safety Hub forum. If you want AWS experts to assist you plan, create, or optimize your infrastructure, get in touch with AWS Professional Providers.
Should you have feedback concerning this post, submit remarks in the Remarks area below.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.

You must be logged in to post a comment.