How exactly to deploy AWS Network Firewall to greatly help protect your system from malware
Protecting your computers and network from security events requires multi-level strategies, and you may use network level traffic filtration as you degree of defense. Users need usage of the web for business reasons, however they can download malware inadvertently, that may impact data and network security. This post describes how exactly to use custom Suricata Rules with AWS Network Firewall to include protections that prevent users from downloading malware. You should use your personal internal list, or perhaps a list from open-source or commercial threat intelligence feeds.
Network Firewall is really a managed service that means it is an easy task to deploy essential network protection for several of one’s Amazon Virtual Private Cloud (Amazon VPC) Infrastructure. Network Firewall’s flexible rules engine enables you to define rules firewall, providing you fine-grained control over network traffic, such as for example blocking outbound requests to avoid the spread of potential malware.
Top features of Network Firewall
This section describes top features of Network Firewall that assist in improving the overall security of one’s network.
Network Firewall:
- Is really a managed Amazon Web Services (AWS) service, which means you don’t need to build and keep maintaining the infrastructure to host the network firewall.
- Integrates with AWS Firewall Manager, that allows one to centrally manage security policies and automatically enforce mandatory security policies across existing and newly created accounts and virtual private clouds (VPCs).
- Protects application availability by filtering inbound internet traffic using tools such as for example access control list (ACL) rules, stateful inspection, protocol detection, and intrusion prevention.
- Provides URL, Ip, and domain-based outbound traffic filtering to assist you meet compliance requirements, stop potential data leaks, and block communication with known malware hosts.
- Offers you control and visibility of VPC-to-VPC traffic to split up networks that host sensitive applications or line-of-business resources logically.
- Complements existing network and application security services on AWS by giving control and visibility to layer 3 through 7 network traffic for the entire VPC.
Automating deployment of Network management and Firewall of Network Firewall rules support management at-scale and assist in timely response, as Network Firewall was created to block usage of insecure sites before they impact your resources. For the perfect solution is in this website post, you’ll use an AWS CloudFormation template to deploy the network architecture with Network Firewall.
Solution architecture
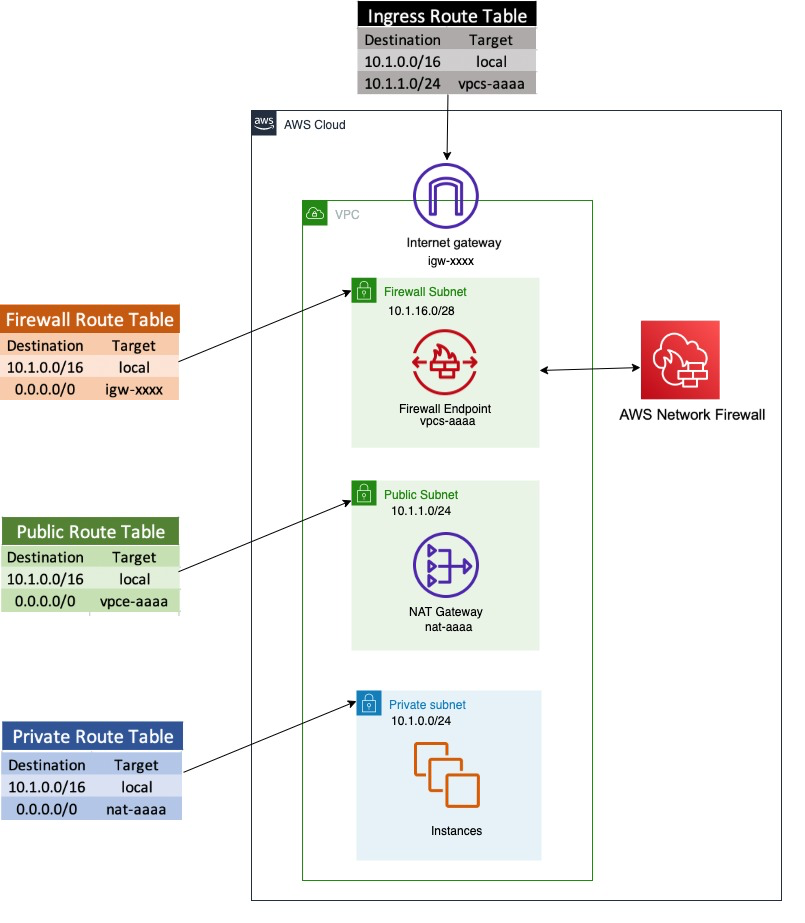
Figure 1 shows an example architecture to show how users have the ability to download malware files, and ways to prevent this using network firewall rules.
Network Firewall is deployed within a VPC architecture, where it really is put into line with the traffic to and from the web.

Figure 1. Network architecture diagram
The network architecture shown in Figure 1 includes three subnets:
- A network firewall subnet
Hosts the Network Firewall endpoint interface. All outbound traffic out of this network goes through the web gateway. - A public subnet
Hosts a NAT gateway. Another hop from the general public subnet may be the Network Firewall endpoint, where all traffic could be inspected before being forwarded to the web. - An exclusive network subnet
Used to host your client instances. All outbound traffic out of this network would go to the NAT gateway endpoint.
In the network architecture shown in Figure 1, only 1 AZ is shown for simplicity, but guidelines recommend deploying infrastructure across multiple AZs
To perform the CloudFormation deployment template
-
- To create the architecture shown in Figure 1, launch the provided CloudFormation deployment template utilizing the Launch stack button in step two 2 below.
This CloudFormation template:- Creates VPCs and appropriate subnets as required by the network architecture.
- Creates a route table with appropriate routes and attaches it to the correct subnet (i.e. private subnet, firewall subnet, public subnet).
- Creates a test instance with appropriate security groups.
- Deploys Network Firewall with firewall policy.
- Creates a Rule Group SampleStatefulRulegroupName with Suricata rules, that is not mounted on a firewall policy
- To launch the stack, click on the Launch Stack button below.
- To create the architecture shown in Figure 1, launch the provided CloudFormation deployment template utilizing the Launch stack button in step two 2 below.
- Name the newly created stack (for instance, nfw-stack).
- The template may also install two sample rules which will be used to safeguard against accessing two sample malware site URLs, nonetheless it won’t attach them to a firewall policy< automatically;/li>
- You can view that Network Firewall with firewall policy was deployed within the basic CloudFormation deployment. It created Suricata rules in rule groups also, but is not mounted on the firewall policy yet.
Note: If you don’t attach the rule to the Network Firewall, it shall not supply the required protection.
Example: confirming vulnerability
We’ve identified two sample URLs which contain malware to utilize for demonstration.
In the example screen shot below, we tested vulnerability by logging into test instance using AWS Session Manager. and at the shell prompt, used wget to gain access to and download a malware file.
Figure 2 that follows is really a screenshot of what sort of user could access and download two different malware files.
Note: Since these URLs contain malware files, we do not recommend users perform this test, but are providing a screenshot as a demonstration. If you want to test capability to download files actually, use URLs you understand are safe for testing.

Figure 2. Insecure URL access
Network Firewall policies
Prior to the Network is established by the template Firewall rule group, a Network is established because of it Firewall policy and attaches it to the Network Firewall. An AWS Network Firewall firewall policy defines the protection and monitoring behavior for a firewall. The facts of the behavior are defined in the rule groups that you increase your policy.
Network Firewall rules
A Network Firewall rule group is really a reusable group of criteria for handling and inspecting network traffic. You can add a number of rule groups to a firewall policy within policy configuration. The included template does this for you personally.
Network Firewall rule groups are either stateful or stateless. Stateless rule groups evaluate packets in isolation, while stateful rule groups evaluate them in the context of these traffic flow. Network Firewall runs on the Suricata rules engine to process all stateful rules.
Suricata rules may be used to develop a Network Firewall stateful rule to avoid insecure URL access. Figure 3 shows the Suricata rules that the template adds and attaches to the Network Firewall policy to be able to block usage of the sample malware URLs found in the prior example.

Figure 3. Suricata rules in a Network Firewall rule group
Attach the rule group to the Network Firewall policy
Once you launched the CloudFormation template, it created these rules in the rule group automatically. You’ll now be attaching this rule group to the firewall policy to be able to enable the protection. You shall need similar rules to block the test URLs which are useful for your testing.
Figure 3 shows two Suricata rules which have been configured to block the insecure malware URLs.
To include Suricata rules to Network Firewall
To boost site security and drive back downloading malware, you can include Suricata rules to Network Firewall to secure your website. You’ll do that by:
- Creating and attaching a firewall policy to the Network Firewall.
- Creating rules within rule groups, which are mounted on the firewall policy
- Testing to verify that usage of malware URLs from the instance is blocked.
Let’s review Suricata Rules which are created, which may be mounted on Network Firewall.
Suricata rule parts
Each Suricata rule has three parts:
-
-
Action
-
drop action that needs to be taken
-
-
Header
-
http this is actually the traffic protocol
$HOME_NET < anywhere;span>$HOME_NET is really a Suricata variable. Automagically it really is set to the CIDR selection of the VPC where Network Firewall is deployed and any identifies any source port
$EXTERNAL_NET 80 where $EXTERNAL_NET 80 is really a Suricata standard variable that identifies traffic destination, and 80 identifies the destination port
-> may be the direction that tells where direction the signature must match
-
-
Options
-
msg “MALWARE custom solution” – gives textual information regarding the signature and the possible alert
flow to_server,established – it really is used to complement on the direction of the < and flow;span>established identifies match on established connections
classtype trojan-activity – gives information regarding the classification of alerts< and rules;/p>
sid:xxxxx gives every signature its id
content “xxxx” – This keyword is vital and the pattern is identified because of it your signature should match.
http_uri is really a content modifier that can help you match and only on the request URI< specifically;/p>
rev:xxx this goes alongside sid keyword. The version is represented because of it of the signature
The signatures in the Suricate rule shown in Figure 3 will block traffic that matches the http_uri contents /data/js_crypto_miner.html and /data/java_jre17_exec.html once the traffic is set up from the VPC to the general public network.
To add a rule group to a preexisting Network Firewall
In Figure 4, the Network Firewall includes a policy attached. nonetheless it doesn’t have a rule group

Figure 4. An insurance plan is attached, however, not a rule group
-
- As shown in Figure 5, choose Add rule group to start out adding your Suricata rule to the Network Firewall.
- Choose Add from existing stateful rule groups to add an created Suricata rule group already.

Figure 5. Choose Add rule group
-
- Figure 6 shows the Suriacata rule groups which are created already. SampleStatefulRulegroupName may be the rule group developed by the CloudFormation template.
- Choose the rule group and choose Add stateful rule group to complete adding the rule group to Network Firewall.

Figure 6. Review the rule groups which are created
-
- Figure 7 demonstrates the rule group SampleStatefulRulegroupName is area of the < now;strong>Stateful rule group portion of Network Firewall screen, which completes adding Suricata rules to Network Firewall.

Figure 7. Shows the brand new rule group is added
Example: validating the solution
Your Network Firewall is currently configured to block malware URLs which are defined in the rulegroup SampleStatefulRulegroupName.
As in the example above where we confirmed vulnerability, Figure 8 shows how exactly to validate that the answer is protecting your users from accessing malware sites now.
Figure 8 shows a user attempting to access exactly the same insecure URLs we tested earlier and implies that the URLs are actually blocked and the attempted connection times out.
Note: Since these URLs contain malware files, we do not recommend users perform this test, but are providing a screenshot as a demonstration. If you want to actually test capability to download files, use URLs you understand are safe for testing.

Figure 8. Insecure URL access blocked
Validating blocking access helps your security team make sure that applications or users on your own network cannot download malware. You can include similar rules for just about any URLs you identify as insecure. SOC operators are not sure of updating CloudFormation templates typically, but you may use a deployment pipeline where in fact the data necessary for the rule is stored in Amazon DynamoDB and use AWS Lambda functions to automate updating rules.
That you have a good example running now, you should implement a whole rule set that meets your requirement from the publicly available malware list such as for example CISSECURITY MALWARE LIST.
Cleanup
AWS resources designed for testing can lead to additional costs. Since a CloudFormation template was utilized by this environment, it is possible to remove all AWS resources from the solution by deleting the CloudFormation stack you named previously (for instance, nfw-stack).
Conclusion
A strategy is described by this website for preventing users from downloading malware. The answer presented uses AWS Network Firewall to secure your environment by blocking usage of the specified malware URLs. The supplied CloudFormation template may be used to automate this protection, also to create a test environment to simulate the scenario easily.
For additional best practice information, see:
When you have feedback concerning this post, submit comments in the Comments section below. When you have questions concerning this post, contact AWS Support.
.
Want more AWS Security news? Follow us on Twitter.


You must be logged in to post a comment.