How exactly to configure Duo multi-aspect authentication with Amazon Cognito
Adding multi-aspect authentication (MFA) decreases the chance of user accounts take-over, phishing episodes, and password theft. Incorporating MFA while supplying a frictionless sign-in experience demands one to offer a selection of MFA choices that support an array of users and products. Let’s observe how you can make that happen with Amazon Cognito and Duo Multi-Factor Authentication (MFA).
Amazon Cognito user pools are user directories which are utilized by Amazon Web Services (AWS) customers to control the identities of these customers also to add sign-within, sign-up and user administration features with their customer-facing internet and mobile applications. Duo Security can be an APN Partner that delivers unified access safety and multi-factor authentication options.
In this website post, I demonstrate how exactly to use Amazon Cognito custom authentication movement to integrate Duo Multi-Factor Authentication (MFA) into your sign-within flow and offer an array of MFA options to your visitors. Some second factors accessible through Duo MFA are usually cellular phone SMS passcodes, authorization of login via telephone call, push-notification-based acceptance on smartphones, biometrics on gadgets that assistance it, and protection keys which can be attached via USB.
How it functions
Amazon Cognito consumer pools allow you to create a custom authentication flow that authenticates customers predicated on a number of challenge/response cycles. This flow may be used by one to integrate Duo MFA into your authentication as a custom challenge.
Duo Web supplies a software development package to create it easier so that you can integrate your web apps with Duo MFA. You will need a merchant account with Duo and a credit card applicatoin to safeguard (which could be produced from the Duo admin dashboard). Once you create the application in the Duo admin dashboard, take note the integration essential (ikey), secret important (skey), and API hostname. This info, as well as a random string (akey) that you generate, will be the primary elements used to integrate your Amazon Cognito user swimming pool with Duo MFA.
Note: ikey, skey, and akey are usually known as Duo keys.
Duo MFA will be built-into the sign-in stream as a custom problem. To perform that, you should generate a signed problem demand making use of Duo APIs and utilize it to load Duo MFA within an iframe and ask for the user’s second element. Once the user answers the task, a signed reaction is returned to the application and delivered to Amazon Cognito for verification. If the reaction is valid the MFA challenge is prosperous then.
Let’s have a closer consider the sequence of parts and calls involved with this flow.
Implementation details
In this area, I walk you through the end-to-finish flow of integrating Duo MFA with Amazon Cognito utilizing a custom authentication circulation. To help you with this particular integration, I constructed a demo project that delivers deployment methods and sample program code to produce a working demo within your environment.
Create and configure the user pool
The first step would be to create the AWS resources necessary for the demo. That can be done that by deploying the AWS CloudFormation stack as described within the demo project.
Several implementation details to understand:
- The template produces an Amazon Cognito user pool, app client, and AWS Lambda triggers which are used for the customized authentication.
- The template accepts ikey, skey, and akey as inputs. For safety, the parameters are usually masked in the AWS CloudFormation gaming console. These parameters are kept in a key in AWS Secrets Manager with a resource policy which allows appropriate Lambda functions read usage of that secret.
- Duo keys are usually loaded from secrets supervisor at the initialization of generate auth problem and verify auth problem Lambda triggers to be utilized to generate sign-request and verify sign-response.
Authentication movement

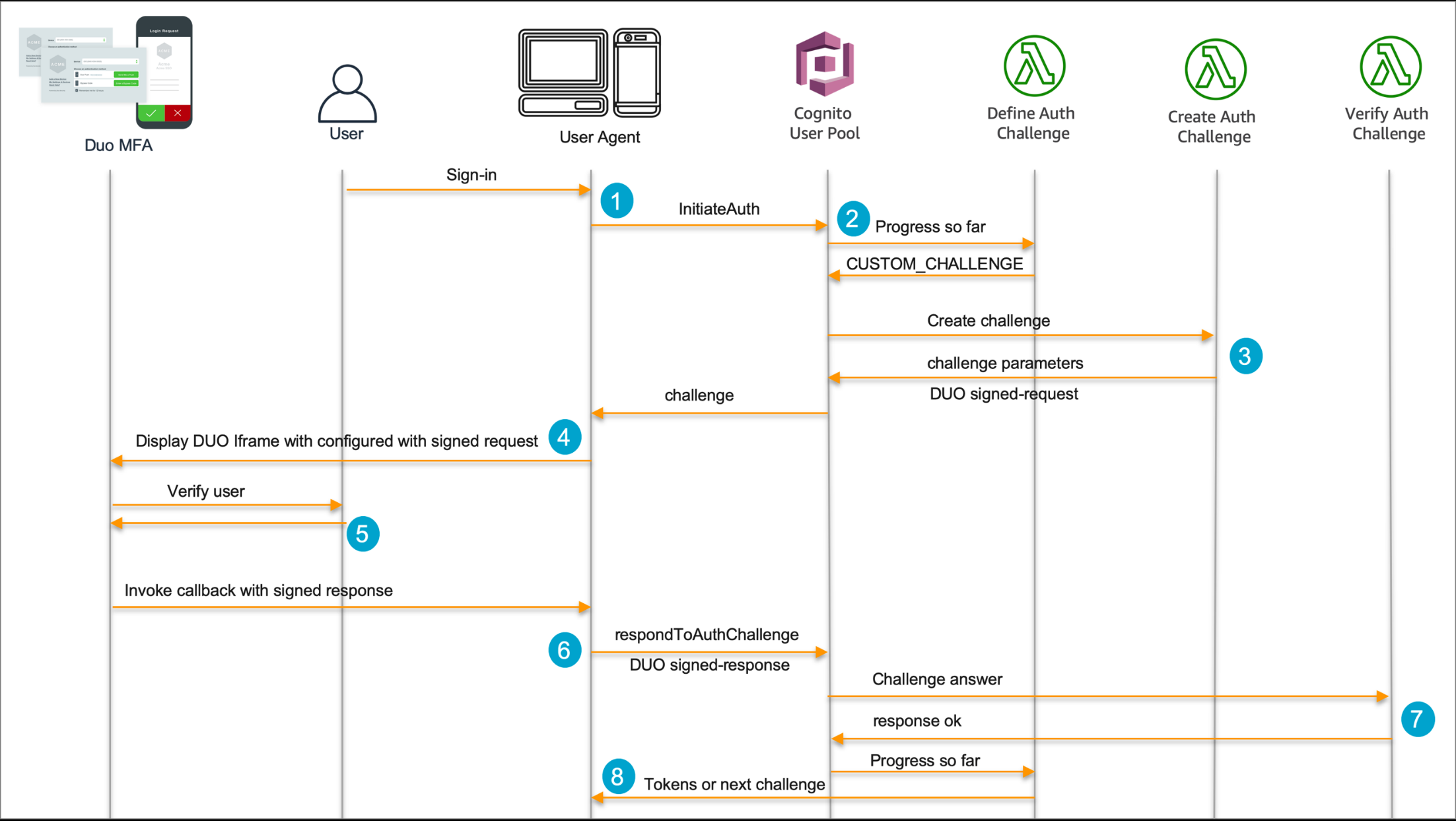
Figure 1: User authentication procedure for the customized authentication flow
The preceding sequence diagram (Figure 1) illustrates the sequence of calls to register a user, which are the following:
- In your application, an individual is offered a sign-in UI that captures their consumer title and password and begins the sign-in stream. A script-working in the browser-begins the sign-in process utilizing the Amazon Cognito authenticateUser API with Customized_AUTH set because the authentication circulation. This validates the user’s credentials using Secure Remote Password (SRP) process and progresses to the second problem if the credentials are legitimate.
Note: The authenticateUser API immediately starts the authentication procedure with SRP. The initial challenge that’s delivered to Amazon Cognito will be SRP_A. This is accompanied by PASSWORD_VERIFIER to verify the user’s credentials.
- After the SRP problem step, the define auth problem Lambda result in will return Custom made_CHALLENGE which will move manage to the create auth challenge bring about.
- The create auth problem Lambda trigger generates a Duo signed demand using the Duo keys in addition to the username and returns the signed ask for as challenging to the client. This is a sample program code of what create auth problem should appear to be:
- The customer initializes the Duo Internet library with the signed demand and shows Duo MFA within an iframe to ask for another factor from an individual. To initialize the Duo library, you will need the api_hostname that’s generated for your software in the Duo dashboard, the sign-request that has been received as challenging, and a callback function to invoke following the user does complete the MFA step. That is done on your client side the following:

You must be logged in to post a comment.