How exactly to automate incident response within the AWS Cloud for EC2 instances
Among the security epics primary to the AWS Cloud Adoption Framework (AWS CAF) is really a concentrate on incident response and preparedness to handle unauthorized activity. Multiple strategies exist in Amazon Web Services (AWS) for automating classic incident response strategies, and the AWS Security Incident Response Guide outlines several strategies. This write-up demonstrates one specific way for instantaneous reaction and acquisition of infrastructure information from Amazon Elastic Compute Cloud (Amazon EC2) instances.
Incident response starts with detection, progresses to investigation, and follows with remediation then. This process is not any various in AWS. AWS solutions such as for example Amazon GuardDuty, Amazon Macie, and Amazon Inspector provide recognition capabilities. Amazon Detective assists with investigation, including tracking and collecting information. After that, after your security corporation decides to do this, pre-provisioned and pre-prepared runbooks enable faster action towards an answer. One basic principle outlined in the incident reaction whitepaper and the AWS Well-Architected Framework may be the notion of pre-provisioning systems and policies to help you to react quickly to an incident response event. The answer I present here offers a pre-provisioned architecture for an incident reaction system which you can use to react to a suspect EC2 example.
Infrastructure overview
The architecture that I outline in this website post automates these regular actions on a suspect compute instance:
- Capture all of the persistent disks.
- Capture the example state at the proper time the incident reaction mechanism is started.
- Isolate the example and drive back accidental example termination.
- Perform operating system-level information collecting, such as for example memory captures along with other parameters.
- Notify the administrator of the actions.
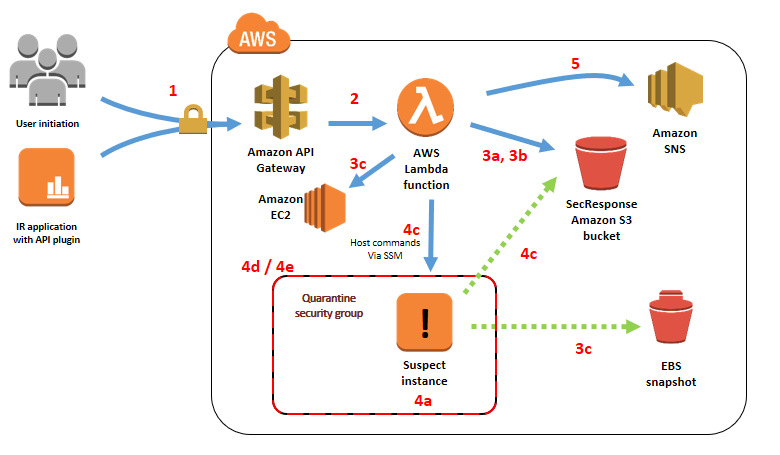
The solution in this website post accomplishes these tasks through the next logical flow of AWS services, illustrated in Figure 1.

Number 1: Infrastructure deployed by the accompanying AWS CloudFormation template and associated job stream when invoking the primary API
- A application or user phone calls an API having an EC2 instance ID to start out data collection.
- Amazon API Gateway initiates the primary logic of the procedure by instantiating an AWS Lambda functionality.
- The Lambda function performs the next information gathering steps before producing any changes to the infrastructure:
- Save example metadata to the SecResponse Amazon Simple Storage Service (Amazon S3) bucket.
- Save the snapshot of the example console in order to the SecResponse S3 bucket.
- Initiate an Amazon Elastic Block Store (Amazon EBS) snapshot of most persistent block storage space volumes.
- The Lambda function modifies the infrastructure to keep gathering information then, by doing the next steps:
- Place the Amazon EC2 termination security flag on the example.
- Remove any present EC2 instance user profile from the example.
- If the example is managed by AWS Systems Manager:
- Attach an EC2 instance user profile with reduced privileges for operating system-level information collecting.
- Perform operating system-level information gathering activities through Systems Supervisor on the EC2 example.
- Remove the instance user profile after Systems Manager provides completed its measures.
- Create a quarantine protection group that lacks each ingress and egress tips.
- Move the instance in to the created quarantine safety team for isolation.
- Send an administrative notification by means of the configured Amazon Simple Notification Service (Amazon SNS) topic.
Solution features
Utilizing the mechanisms outlined in this article to codify your incident reaction runbooks, you can observe the following advantages to your incident response program.
Preparing for incident reaction before a good incident occurs
Both AWS CAF and Well-Architected Framework advise that customers formulate identified procedures for incident response, and test those runbooks before an incident. Tests these processes before a meeting occurs decreases the proper time it takes one to respond in the production environment. The sample infrastructure proven in this article demonstrates ways to standardize those procedures.
Constant incident response artifact collecting
Codifying your processes directly into set infrastructure and program code prepares you for the necessity to collect data, but additionally standardizes the collection approach into a repeatable plus auditable sequence associated with What information had been collected when and just how. This decreases the likelihood of lacking data for potential future investigations.
Walkthrough: Deploying infrastructure and starting the procedure
To implement the perfect solution is outlined in this article, you have to deploy the infrastructure very first, and start the info collection procedure by issuing an API call then.
The code example in this website post requires that you provision an AWS CloudFormation stack, which creates a good S3 bucket for storing your occasion artifacts and the serverless API that makes use of API Gateway and Lambda. Afterward you execute a query from this API to do this on a focus on EC2 instance.
The infrastructure deployed by the AWS CloudFormation stack is really a group of AWS components as depicted previously in Shape 1. The stack includes all of the ongoing services and configurations to deploy the demo. It doesn’t add a target EC2 example which you can use to check the mechanism found in this post.
Cost
The cost because of this demo is minimum as the base infrastructure is totally serverless. With AWS, you merely purchase the infrastructure that you utilize, so the individual API call released in this demo expenses fractions of a single thing. Artifact storage expenses shall incur S3 storage space prices, and Amazon EC2 snapshots will be stored at their respective costs.
Deploy the AWS CloudFormation stack
In upcoming updates and posts, we will display how to setup this security response mechanism in the independent account designated for security, but also for the purposes of the post, your demo stack need to reside in exactly the same AWS account because the target instance that you create within the next section.
First, begin by deploying the AWS CloudFormation template to provision the infrastructure.
To deploy this template in the us-east-1 region
- Select the Start Stack button to open up the AWS CloudFormation gaming console pre-loaded with the template:

- (Optional) Inside the AWS CloudFormation console, on the Specify Details web page, customize the stack title.
- For the LambdaS3BucketLocation and LambdaZipFileName areas, keep the default values for the reasons of the blog. Customizing this industry enables you to customize this code illustration for your own reasons and store it within an S3 bucket of one’s choosing.
- Customize the S3BucketName field. This must be a distinctive S3 bucket name globally. This bucket will be where gathered artifacts are usually kept for the demo in this website. You need to customize it beyond the default worth for the template to instantiate correctly.
- (Optional) Customize the SNSTopicName industry. This name offers a meaningful label for the SNS subject that notifies the administrator of what which were performed.
- Choose Following to configure the stack choices and depart all default settings set up.
- Choose Following to examine and scroll to underneath of the page. Select all three check out boxes beneath the Features and Transforms section, close to each one of the three acknowledgements:
- We acknowledge that AWS CloudFormation may create IAM sources.
- We acknowledge that AWS CloudFormation may create IAM assets with custom made names.
- We acknowledge that AWS CloudFormation may need the following capability: Capacity_AUTO_EXPAND.
- Choose Create Stack.
Set upward a target EC2 example
To be able to demonstrate the functionality of the mechanism, a target is necessary by you host. Provision any EC2 example in your accounts to do something as a focus on for the security reaction mechanism to do something upon for information selection and quarantine. To improve affordability and demonstrate complete functionality, I recommend selecting a small instance dimension (for instance, t2.nano) and optionally signing up for the instance into Techniques Manager for the capability to later execute Work Order API queries. For additional information on configuring Systems Supervisor, make reference to the AWS Systems Manager User Guide.
Retrieve required details for system initiation
The complete security response mechanism triggers via an API call. To initiate this call successfully, you need to collect the API URI and key information first.
To discover the API URI and essential information
- Navigate to the AWS CloudFormation gaming console and pick the stack that you’ve instantiated.
- Choose the Outputs tab and conserve the value for the main element APIBaseURI. This is actually the bottom URI for the API Gateway. It’ll resemble https://abcdefgh12.execute-api.us-east-1.amazonaws.com.
- Next, demand API Gateway system and pick the API with the title SecurityResponse.
- Choose API Keys, and pick the only key current then.
- Following to the API key industry, choose Show to reveal the main element, and conserve this worth to a notepad for later on use then.
(Optional) Configure administrative notification through the created SNS subject
One aspect of the mechanism is that it transmits notifications through SNS subjects. It is possible to optionally subscribe your e-mail or another notification pipeline system to the developed SNS topic to be able to receive notifications on activities taken by the machine.
Initiate the protection response mechanism
Note that, inside this demo program code, you’re utilizing a simple API essential for limiting usage of API Gateway. In creation applications, you’ll use an authentication system such as for example Amazon Cognito to control access to your API.
To start the security response system, initiate a Relaxation API query contrary to the API that has been created within the AWS CloudFormation template. You initial create this API contact with a curl order to be work from the Linux system.
To create the API initiation curl command
- Copy the next example curl command.
curl -v -X POST -we -H "x-api-essential: 012345ABCDefGHIjkLMS20tGRJ7othuyag" https://abcdefghi.execute-api.us-east-1.amazonaws.com/DEMO/secresponse -d ' "instance_id":"i-123457890" ' - Replace the placeholder API essential specified inside the x-api-essential HTTP header together with your API key.
- Replace the example URI route together with your API’s specific URI. To generate the entire URI, concatenate the bottom URI detailed in the AWS CloudFormation result you gathered formerly with the API contact path, that is /DEMO/secresponse. This complete URI for the specific API contact should carefully resemble this sample URI route: https://abcdefghi.execute-api.us-east-1.amazonaws.com/DEMO/secresponse
- Replace the value linked to the key example_id with the example ID of the prospective EC2 example you created.
Because this system initiates by way of a simple API contact, it is possible to integrate it with present workflow management techniques easily. This enables for complex data selection and forensic processes to be incorporated with existing incident reaction workflows.
Evaluation the gathered information
Note that the next items were uploaded like objects in the safety response S3 bucket:
- A gaming console screenshot, as shown in Body 2.
- (If Systems Supervisor is configured) stdout info from the commands which were operate on the host operating-system.
- Example metadata in JSON form.

Figure 2: Illustration outputs from the successful completion of the blog post’s system
Additionally, if you load the Amazon EC2 console and scroll right down to Elastic Block Store, that EBS is seen by you snapshots can be found for several persistent disks as shown in Figure 3.

Figure 3: Proof an EBS snapshot from the successful run
You can even verify that the previously outlined protection controls come in place by viewing the instance in the Amazon EC2 console. You need to see the elimination of AWS Identity and Access Management (IAM) functions from the mark EC2 instances and that the instance has already been placed into system isolation through a recently created quarantine security team.
Remember that for the reasons of this demo, all given details that you gathered is stored in exactly the same AWS account because the workload. As a best exercise, many AWS clients choose instead to shop this information within an AWS accounts that’s particularly designated for incident reaction and analysis. A separate account provides very clear isolation of restriction and perform of access. Using AWS Organizations service control policies (SCPs) and IAM permissions, your security team may limit access to stick to security policy, legal assistance, and compliance regulations.
Clean upward and delete artifacts
To clean upward the artifacts from the answer in this post, 1st delete all provided information within your security response S3 bucket. After that delete the CloudFormation stack that has been provisioned in the beginning of this process to be able to tidy up all remaining infrastructure.
Conclusion
Placing workloads within the AWS Cloud permits pre-provisioned and explicitly described incident reaction runbooks to end up being codified and rapidly executed upon suspect EC2 instances. This permits one to gather data in minutes that took hours as well as days using manual processes previously.
When you have feedback concerning this post, submit remarks in the Comments section below. Should you have questions concerning this post, start a brand new thread on the Amazon EC2 forum or contact AWS Support.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.

You must be logged in to post a comment.