Hands-on walkthrough of the AWS System Firewall flexible rules engine
AWS System Firewall is really a managed service that means it is an easy task to provide fine-grained system protections for all of one's Amazon Virtual Personal Clouds (Amazon VPCs) to make sure that your visitors will be inspected, monitored, and logged. The firewall scales automatically together with your network traffic, and will be offering built-in redundancies made to provide high availability.AWS System Firewall supplies a flexible rules motor that gives you the capability to write a large number of firewall guidelines for granular plan enforcement. It helps inbound and outbound internet filtering for unencrypted website traffic. For encrypted website traffic, AWS System Firewall inspects the domain title supplied by the Server Title Indicator (SNI) through the Transport Layer Protection (TLS) handshake. Furthermore, it includes an intrusion prevention program (IPS), which gives active traffic flow examination to help you determine and block vulnerability exploits.
By third , blog post, you’ll deploy a demo AWS Network Firewall inside your AWS accounts to interact, first-hand, using its rules motor.
Answer overview
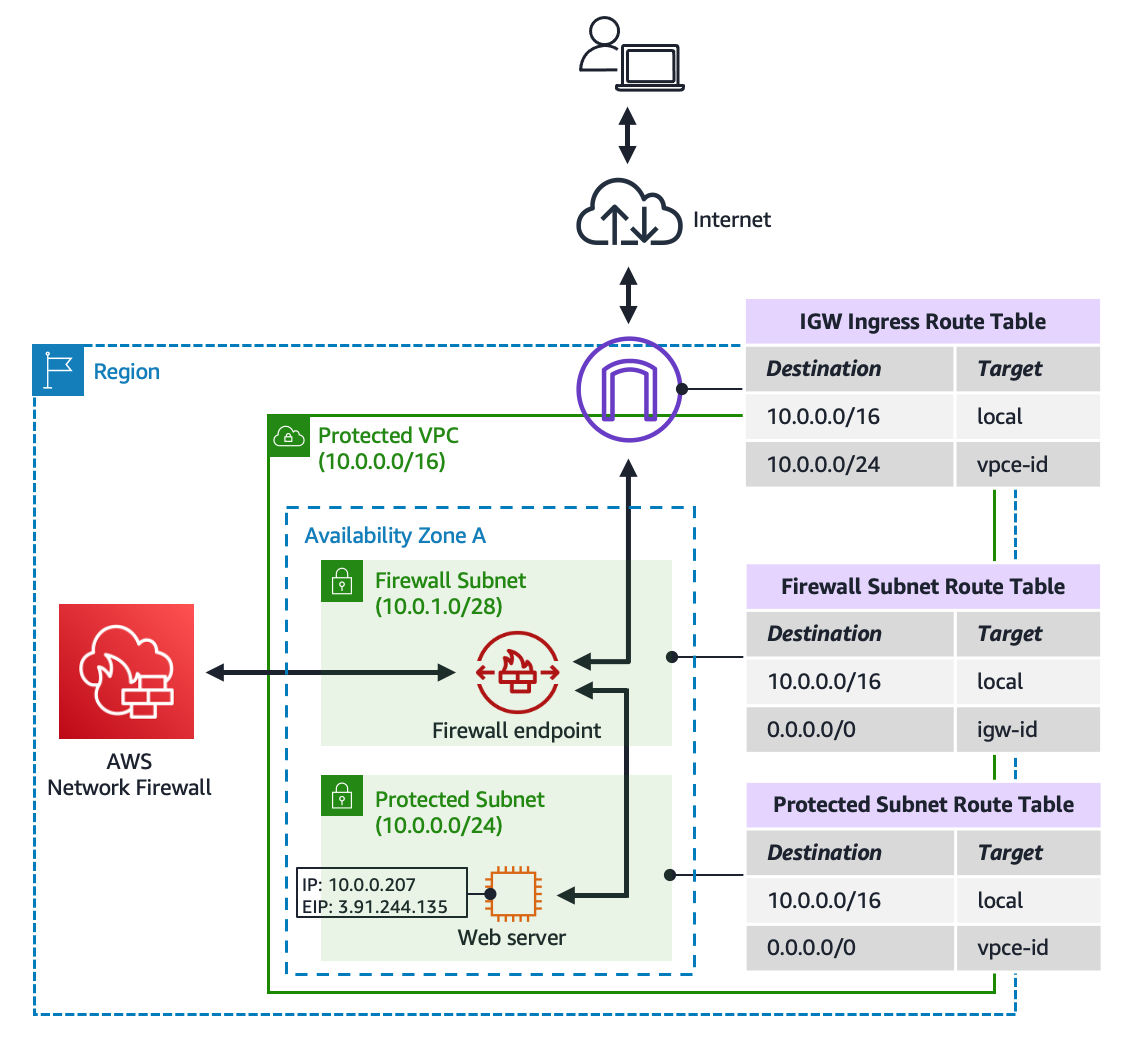
The perfect solution is in this article uses route tables to send all network traffic to a firewall endpoint, as shown in Figure 1.

Figure 1: Solution summary
Through the walkthrough, you’ll include firewall rules to impact traffic flows to plus from the web server running upon Amazon Elastic Compute Cloud (Amazon EC2) in a guarded subnet. Furthermore, the demo firewall will be configured to deliver alert logs to Amazon CloudWatch, therefore you’ll start to see the filtering carried out by stateful rule groupings.
How does this ongoing work?
The AWS System Firewall runs on the rules engine that processes rules differently based on whether you’re performing stateless or stateful examination.
When performing stateless inspection, almost all individual packets within a circulation are evaluated against each guideline within your policy. Guidelines are processed in rigid order in line with the priority assigned in their mind, with lower numbered guidelines (for instance, 1) getting precedence over higher numbered rules (for instance, 100).
Stateless rules inspect every packet in isolation, without regard to factors like the direction of traffic, or if the packet is section of a preexisting, approved connection. It has performance benefits, as the security plan makes a choice sooner. However, in addition, it means that the plan cannot take the higher context of a movement into consideration before deciding. For example, if you want to automatically allow come back traffic, this is simply not something a stateless plan is most effective for.
Stateful rule inspection differently works. The stateful rules motor processes your guidelines in the region of their actions establishing, with move rules first processed, then fall, after that alert. The motor stops digesting when it discovers a match. The firewall furthermore takes under consideration the purchase that the rules come in the rule team, and the concern assigned to the principle, if any.
For instance, a pass guideline with important of 1 1 will undoubtedly be processed in front of you pass rule with important of 2. However, a drop rule with important of 1 1 will be processed in the end pass rules have already been evaluated, which includes those with a lesser priority. To find out more about rule order assessment, observe Rule actions inside AWS Network Firewall in the AWS System Firewall Developer Manual.
Stateful rules take into context the complete flow from begin to finish, which affects how your rules are evaluated.
For instance, think about the following IPS principle:
fall tcp any any -> any any (msg:"Deny all the TCP traffic"; sid: 1000003; rev:1;)</program code>The firewall will recognize a match up in the beginning of the TCP handshake as shown in Figure 2, and immediately fall that traffic, and all of the subsequent traffic.

Figure 2: The three-way handshake utilized by TCP
It is because the stateful engine is making the decision for the whole flow, not only for individual packets. After the stream is dropped, no some other rules are usually evaluated for that circulation. This behavior means guidelines that just match during later elements of a flow will never be evaluated.
Let’s check out another instance:
pass any any -& tls;gt; any any (tls.sni; articles:"aws.amazon.com"; startswith; nocase; endswith; msg:"Permit HTTPS usage of aws.amazon.com"; sid:1000002; rev:1;)
fall tcp any any -> any any (msg:”Deny all the TCP traffic”; sid: 1000003; rev:1;)
As written, the initial rule won't match as the TCP protocol may be the first protocol that may appear in the original flow, you start with the TCP handshake. Consequently, once the flow starts, as the first rule will undoubtedly be evaluated, you will see no TLS process to match, so the drop guideline will match rather and drop all the traffic to aws.amazon.com. In order to avoid this, you need to write rules that just evaluate after a program has been established utilizing the movement keyword, for instance:
move tls any any -> any any (tls.sni; content material:"aws.amazon.com"; startswith; nocase; endswith; msg:"Permit HTTPS usage of aws.amazon.com"; sid:1000002; rev:1;)
fall tcp any any -> any any (stream:founded,to_server; msg:”Deny all the TCP traffic”; sid: 1000003; rev:1;)
Now, whenever your demand to aws.amazon.com is manufactured, the firewall will allow TCP handshake complete before evaluating the TCP fall rule. At this point, the rule action purchase will need precedence and the move rule will match, allowing all of those other visitors through for that circulation.
To conclude, when writing stateful guidelines for AWS System Firewall, you’ll desire to bear in mind the principle action, the concern (if any), and if the rule is intended to complement upstream or downstream for confirmed network flow.
Essential : The program code template provided to aid the walkthrough action below is supposed for deployment inside a development environment. We’ve provided some protection hardening measures in your code, but further refinements will undoubtedly be required ahead of deploying this solution inside a production environment. To learn more, see GUIDELINES for Security, Identification, & Compliance .
Walkthrough prerequisites
Perform initial deployment actions
To initiate the deployment
- Making use of your device’s command range interface (CLI), browse the AWS Git repository useful for this demo in order to a local directory on your own gadget: git clone https://github.com/aws-samples/aws-network-firewall-demo. In the event that you don’t possess a Git client on your own device, download the next document and extract it locally: https://github.com/aws-samples/aws-network-firewall-demo/archive/major.zip.
- Get on the AWS Management System and choose the AWS Area where you’d prefer to deploy the demo. Start to see the AWS Regional Solutions List to ensure that AWS System Firewall comes in your selected Area. In the illustration, we chosen Us all East (N. Virginia).
- In the search package in the navigation bar, get into CloudFormation, after that in the serp’s, select CloudFormation.
- Choose Create Stack, select Template is usually ready, select Upload a template document. Choose Document to choose AWS-Network-Firewall-demo.yaml that you locally saved.
- Choose Next. Enter a stack title (for the instance, we utilized MyFirewallStack), choose < then;strong>Next.
- On the next screens, keep the defaults, and continue steadily to select Next and soon you reach Step 4 – Evaluation.
- Under Abilities, choose the check package We acknowledge that AWS CloudFormation may create IAM assets with custom titles, then select Create stack.
- The stack status is CREATE_Inside_Improvement. Pick the Refresh button to refresh the standing periodically. Upon completion, the position adjustments to CREATE_COMPLETE.
Make system connections to the net server
Given that the demo atmosphere is deployed, you’ll make system connections to and from the net server inside the protected subnet through the AWS Network Firewall.
To create system connections to the net server
- In the AWS CloudFormation gaming console, navigate to your firewall stack’s Outputs tab. On the worthiness for the WebServerURL open up the context (right-click) menus, and select Open up Link in Fresh Tab, as shown in Physique 3.

Figure 3: Firewall stack’s outputs tab
You will notice a Hello Globe response from the net server in a fresh browser tab, as demonstrated in Number 4.

Figure 4: Web server’s Hello Planet page
- To deliver Internet Control Message Process (ICMP) echo requests to the net server, within your device’s command collection enter ping internet server’s public DNS title (changing web server’s general public DNS title with the firewall stack’s WebServerURL output, minus the http:// prefix). You will notice successful echo replies from the net server, as shown in Shape 5.

Body 5: Successful echo replies from the net server
- In the AWS Management Console, head to Providers and select EC2.
- In EC2 console, in the remaining navigation pane, choose Situations.
- Choose the WebServer example and select Connect.
- Select Program Manager and < then;strong>Connect. This can securely access the example without needing SSH keys or perhaps a bastion host. Remember that personal Session Supervisor entry was configured once you released the AWS CloudFormation template through the initial deployment methods.
- In the Session Supervisor system, validate that the net server will be able to retrieve content from aws.amazon.com utilizing the cURL device. Enter curl https://aws.amazon.com, as shown in Amount 6.

Figure 6: Retrieving content from aws.amazon.com
You will notice the Session Supervisor console populated with multiple pages of HTML content, as shown in Figure 7.

Figure 7: Successfully retrieved content from aws.amazon.com
- Repeat the prior stage to confirm that you can retrieve articles from other websites aswell. For instance, enter curl https://www.amazon.com.
Create firewall guidelines
Given that you’ve verified building system connections to and from the net server, this means that that the AWS Network Firewall isn’t restricting any traffic. You’ll right now create firewall guidelines to restrict these connections. While this is achieved with AWS CloudFormation, because of this specific demo you’ll create the guidelines straight in the AWS Administration Console.
To generate firewall guidelines
- In the AWS Management Console, in the search package in the routing bar, get into VPC, then in the serp’s, select VPC.
- In the still left navigation pane, choose Network Firewall rule organizations. Pick the StatelessRuleGroup firewall rule team.
- To include a guideline that blocks Ping simply by dropping all ICMP visitors, inside the Guidelines section, go for Edit guidelines.
- Select Put rule, and enter the next values, mainly because shown in Figure 8:
- For Priority, enter 5.
- For Process, choose ICMP and obvious the All check container.
- For Resource and Location, select Any IPv4 tackle.
- For Actions, choose Fall.
- Choose Increase, then select Save.

Figure 8: New guideline that drops ICMP visitors
- In the remaining navigation pane, select Network Firewall rule groupings. Choose the StatefulRuleGroup firewall rule team.
- Next, you will add 3 sample Suricata compatible IPS guidelines:
- someone to permit inbound HTTP usage of the EC2-based internet server
- someone to permit outbound HTTPS usage of aws.amazon.com
- someone to deny all the TCP visitors
These specific rules work by coordinating particular keywords in a packet’s payload. Select Edit guidelines. Replace the contents of the written text box with the next:
move any any -& http;gt; any any (http.host; dotprefix; content material:".amazonaws.com"; endswith; msg:"Permit HTTP usage of the net server"; sid:1000001; rev:1;)pass any any -> tls; any any (tls.sni; articles:”aws.amazon.com”; startswith; nocase; endswith; msg:”Permit HTTPS usage of aws.amazon.com”; sid:1000002; rev:1;)
fall tcp any any -> any any (movement:set up,to_server; msg:”Deny all the TCP traffic”; sid: 1000003; rev:1;)
- Select Conserve rule team.
-
Verify the potency of the firewall tips
To verify that the firewall is restricting visitors based on the guidelines that you created, proceed through these ways.
To verify the potency of the firewall guidelines
- Concur that you’re still in a position to browse the internet server’s Hello Entire world web page (by browsing to firewall stack’s WebServerURL).
- From the command prompt on your own device, send ICMP echo requests to the net server by getting into ping web server’s open public DNS title. As the firewall will be filtering ICMP, observe that the requests are actually timing out, as shown in Physique 9.

Figure 9: The net server no more responds to ICMP echo requests
- Hook up to the net server’s console using Program Manager. To verify that the net server is still in a position to retrieve content from aws.amazon.com, enter curl https://aws.amazon.com.
- Make an effort to retrieve content material from other websites, aswell. For instance, enter curl https://www.amazon.com. You’ll observe that the request now occasions out.
See the firewall’s alert logs
Once you launched the AWS CloudFormation template through the initial deployment steps, the firewall was pre-configured to send out alert logs to Amazon CloudWatch Logs. You can observe any filtering completed by its stateful rule organizations. The AWS System Firewall may also be set up to utilize other logging destinations, such as for example Amazon Basic Storage Support (Amazon S3) and Amazon Kinesis Information Firehose.
To see the firewall’s alert logs
- In the search package in the navigation bar, get into CloudWatch, after that in the serp’s select CloudWatch.
- On the remaining navigation bar, select Insights to interactively research and analyze your log information.
- In the Select log group(s) fall down list, choose the check package for the log team that begins with MyFirewallStack-AWSNetworkFirewallLogGroup, mainly because shown in Figure 10. Choose Work query.

Figure 10: Run a query contrary to the firewall’s log team
- Scroll right down to see a set of records, and choose one of these to observe its contents. As there’s a little delay for the firewall to deliver its logs to CloudWatch, in the event that you don’t notice a set of records, wait a couple of minutes and re-operate the query. You discover information regarding the alert’s action, connected signature, and TLS SNI, as shown in Physique 11.

Figure 11: Viewing among the firewall’s log information
This concludes the walkthrough. It is possible to continue to test out the AWS System Firewall rules engine, and in addition explore its logging abilities.
Cleanup
Terminate the sources that were deployed because of this walkthrough in order to avoid unnecessary expenses.
To delete your demo stacks
- If you’ve manually created any extra firewall rule organizations and added them to the firewall plan, delete them from the firewall plan.
- Demand CloudFormation service and choose the stack you created previous, such as for example MyFirewallStack.
- Choose Delete, after that select Delete Stack.
- The stack status is initially DELETE_IN_Improvement. Pick the Refresh button to refresh its status periodically. The status modifications to DELETE_COMPLETE after completed and the stack title no more appears in your set of active stacks.
Summary
By following a walkthrough in this website post, you deployed a good example AWS Network Firewall inside your AWS accounts and attempted its rules motor. This included getting together with the firewall’s versatile rules engine to fall ICMP visitors and restrict usage of certain content. AWS System Firewall has fine-grained handle that can serve a variety of other use instances, such as for example blocking outbound Server Information Block (SMB) requests to avoid the pass on of malicious exercise.
If you’d prefer to find out more about managing these guidelines across accounts, start to see the post Enforce your own AWS System Firewall protections at level with AWS Firewall Supervisor.
In case you have feedback concerning this post, submit feedback in the Feedback area below. For those who have questions concerning this post, start a fresh thread on the AWS System Firewall forum or contact AWS Assistance.
Want a lot more AWS Security how-to content material, news, and show announcements? Adhere to us on Twitter.
