Guidelines and advanced styles for Lambda code signing
Amazon Web Services (AWS) recently released Code Signing for AWS Lambda. Employing this feature, you can assist enforce the integrity of one’s code artifacts and be sure that only trusted programmers can deploy program code to your AWS Lambda functions. These days, let’s review a simple use case alongside guidelines for lambda program code signing. After that, let’s dive strong and discuss two superior patterns-one for centralized signing and something for cross account level validation. You may use these advanced designs to use program code signing in a distributed possession design, where you have individual groups for designers writing program code and for groups in charge of enforcing particular signing profiles or for publishing layers.
Secure software growth lifecycle
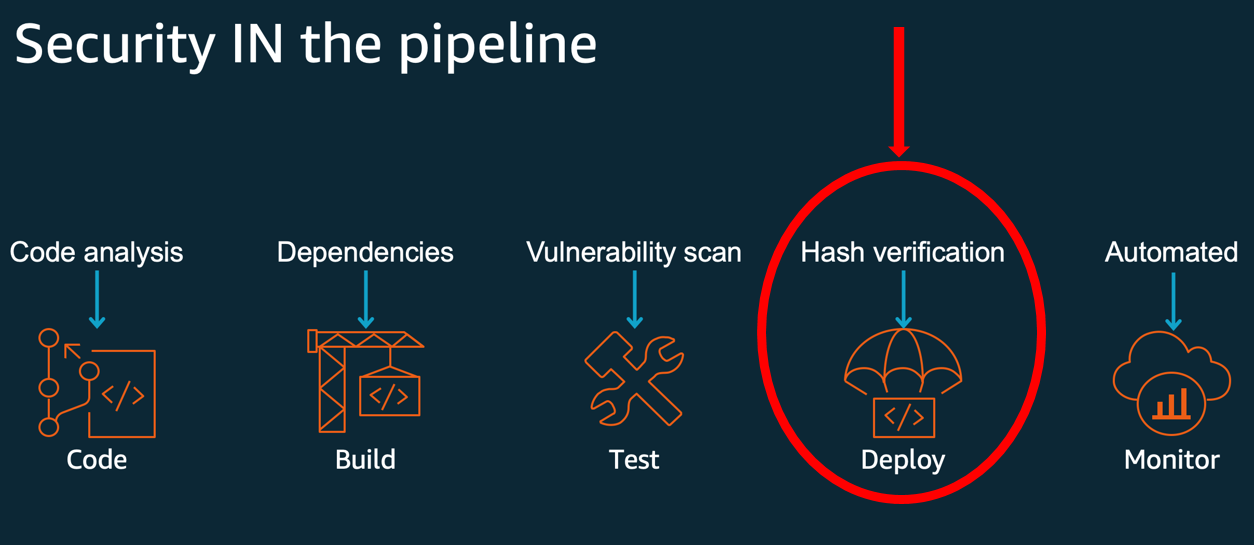
For context of everything you receive by this capability, let’s consider the safe software development lifecycle (SDLC). You will need different types of security controls for every of one’s development phases. A synopsis of the protected SDLC development stages-program code, build, check, deploy, and monitor-, alongside applicable security controls, are available in Figure 1. You may use program code signing for Lambda to safeguard the deployment phase and present a cryptographically solid hash verification.

Figure 1: Program code signing offers hash verification within the deployment stage of the secure SDLC
Adding Security into DevOps and Implementing DevSecOps Using AWS CodePipeline provide more information on building a safe SDLC, with a specific focus on the program code analysis controls.
Basic pattern:
Figure 2 displays the essential pattern described in Code signing for AWS Lambda and within the documentation. The essential code signing pattern utilizes AWS Signer on a ZIP document and phone calls a create API to set up the signed artifact within Lambda.

Figure 2: The essential code signing design
The essential pattern illustrated in Figure 2 is really as follows:
- An administrator creates the signing user profile in AWS Signer. A signing user profile will be analogous to a program code signing certification and represents a publisher identification. Administrators can offer access via AWS Identity and Access Management (IAM) for programmers to utilize the signing user profile to indication their artifacts.
- Administrators develop a program code signing configuration (CSC)-the new resource within Lambda that specifies the signing profiles that get to sign program code and the signature validation plan that defines whether to warn or even reject deployments that fail the signature checks. CSC could be attached to new or even existing Lambda functions make it possible for signature validations on deployment.
- Developers use among the allowed signing profiles to indication the deployment artifact-the ZIP file-within AWS Signer.
- Programmers deploy the signed deployment artifact to the function making use of either the CreateFunction API or even the UpdateFunctionCode API.
Lambda performs signature checks before accepting the deployment. The deployment fails if the signature checks fall short and you have established the signature validation plan in the CSC to reject deployments making use of ENFORCE mode.
Program code signing checks
Program code signing for Lambda provides four signature checks. Very first, the integrity verify confirms that the deployment artifact hasn’t been altered after it had been signed making use of AWS Signer. Lambda performs this verify by complementing the hash of the artifact with the hash from the signature. The next check may be the supply mismatch examine, which detects in case a signature isn’t existing or if the artifact is usually signed by way of a signing user profile that isn’t specific in the CSC. The 3rd, expiry verify, will fail in case a signature will be past its stage of expiration. The 4th is the revocation examine, that is used to notice if anyone offers explicitly marked the signing user profile useful for signing or the signing work as invalid by revoking it.
The integrity check must succeed or Lambda shall not run the artifact. Another three checks could be configured to either prevent invocation or generate a caution. These checks are carried out to be able until one verify fails or all checks be successful. As a security head concerned about the protection of program code deployments, you may use the Lambda program code signing checks to fulfill different security assurances:
- Integrity – Provides assurance that program code is not tampered with, by making certain the signature on the create artifact is legitimate cryptographically.
- Supply mismatch – Provides assurance that just trusted entities or designers can deploy program code.
- Expiry – Provides assurance that program code running within your environment isn’t stale, by ensuring signatures were created inside a certain time and day.
- Revocation – Enables security administrators to eliminate rely on by invalidating signatures following the fact so they cannot be useful for code deployment should they have been uncovered or are or else no more trusted.
The final three checks are enforced only when you have set the signature validation policy-UntrustedArtifactOnDeployment parameter-in the CSC to ENFORCE. If the plan is defined to WARN, failures in virtually any of the mismatch after that, expiry, and revocation checks will log a metric known as a signature validation mistake in Amazon CloudWatch. The very best practice because of this setting would be to set the policy to WARN initially. Then, you can keep track of the warnings, if any, and update the plan to enforce when you’re self-confident in the results in CloudWatch.
Centralized signing enforcement
In this scenario, you’ve got a security administrators group that manages and approves signing profiles centrally. The group centralizes signing profiles to be able to enforce that all program code working on Lambda will be authored by way of a trusted programmer and isn’t tampered with after it’s signed. To get this done, the security administrators group really wants to enforce that developers-in exactly the same account-can just create Lambda features with signing profiles that the group has accepted. By owning the signing profiles utilized by developer teams, the lifecycle is controlled by the security team of the signatures and the capability to revoke the signatures. Are instructions for developing a signing user profile and CSC here, and enforcing their use then.
Create a signing user profile
To produce a signing profile, you’ll utilize the AWS Command Line Interface (AWS CLI). Begin by logging directly into your account because the central safety role. That is an administrative function that’s scoped with permissions necessary for establishing code signing. You’ll develop a signing profile to utilize for an application called ABC. These example instructions are composed with prepopulated ideals for things such as profile brands, IDs, and descriptions. Alter those as befitting your application.
To develop a signing profile
- Operate this command:
Running this order shall provide you with a signing profile edition ARN. It will appearance something like arn:aws:signer:sa-east-1:XXXXXXXXXXXX:/signing-profiles/profile_for_application_ABC/XXXXXXXXXX. Take note of this worth to utilize in later commands.
Because the security administrator, you need to grant the developers usage of use the user profile for signing. You do this utilizing the add-profile-permission command. Remember that in this illustration, you’re explicitly only granting authorization for the signer:StartSigningJob action. You might want to grant permissions to additional actions, such as signer:GetSigningProfile or signer:RevokeSignature, by making additional phone calls to add-profile-permission.
- Run this control, replacing with the main you’re using:
Create a CSC
You want to create a CSCwith the signing user profile that you also, as the protection administrator, want all of your developers to use.
To develop a CSC
Run this order, replacing with the result from Step 1 hands down the preceding procedure-Create the signing profile:
Running this control will give you the CSCARN which will look something similar to arn:aws:lambda:sa-east-1:XXXXXXXXXXXX:code-signing-config:approved-csc-XXXXXXXXXXXXXXXXX. Take note of this worth to use later.
Write an IAM plan utilizing the new CSC
That the safety administrators team has generated this CSC now, how do they make sure that all it is utilized by the developers? Administrators may use IAM to grant usage of the CreateFunction API, with all the new lambda:CodeSigningConfig condition crucial with the CSC ARN you created. This can ensure that programmers can create functions only when program code signing is enabled.
This IAM policy shall permit the developer roles to generate Lambda functions, but only when they’re utilizing the approved CSC. The excess clauses Deny the designers from creating their very own signing profiles or CSCs, so they are forced to utilize the ones supplied by the central team.
To compose an IAM plan
Run the next command. Replace with the CSC ARN you created earlier.
Create a signed Lambda functionality
Now, the programmers have permission to generate new Lambda features, but only when the features are usually configured with the authorized CSC. The accepted CSC can specify the configurations for Lambda signing plans, and lists what profiles are usually approved for signing the event code with exactly. Which means that developers for the reason that account is only going to have the ability to create features if the features are usually signed with a user profile authorized by the main team and the programmer permissions have been put into the signing user profile used.
To develop a signed Lambda perform
- Upload any Lambda program code file to an Amazon Simple Storage Service (Amazon S3) bucket with the name main-function.zip. Remember that your S3 bucket should be version enabled.
- Indication the zipped Lambda functionality using AWS Signer and the next command, replacing and with the right details from your own uploaded main-perform.zip.
- Download the produced ZIP file from your own Lambda bucket newly. It will be called something similar to signed-XXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX.zip.
- For convenience, rename it to signed-main-function.zip.
- Run the next command, replacing with the ARN of one’s Lambda execution role, and changing with the consequence of the sooner procedure Create the CSC.
Cross-accounts centralization
The utilization is supported by this pattern case where in fact the security administrators and the designers are working in exactly the same account. You might want to implement this across various accounts, which requires generating CSCs in particular accounts where developers have to deploy and upgrade Lambda functions. To get this done, you may use AWS CloudFormation StackSets to deploy CSCs. Stack sets enable you to roll out CloudFormation stacks across several AWS accounts. Use AWS CloudFormation StackSets for Multiple Accounts within an AWS Corporation illustrates how exactly to use an AWS CloudFormation template for deployment to several accounts.
The security administrators can detect and respond to any changes to the stack set deployed CSCs through the use of drift detection. Drift recognition can be an AWS CloudFormation function that detects unmanaged adjustments to the assets deployed making use of StackSets. To complete the answer, Implement automatic drift remediation for AWS CloudFormation using Amazon CloudWatch and AWS Lambda shares a remedy for taking automatic remediation when drift is definitely detected inside a CloudFormation stack.
Cross-accounts validation for Lambda layers
So far, the various tools are had by one to sign your personal Lambda code in order that no-one can tamper with it, and you’ve reviewed a design where one group creates and owns the signing profiles to be utilized by different programmers. Let’s look at yet another advanced design where you publish program code as a signed Lambda layer in a single account, and you utilize it in a Lambda function in another account then. A Lambda layer can be an archive containing extra code that you could use in a function.
Because of this, let’s consider how exactly to set up program code signing when you’re using layers across two accounts. Layers permit you to make use of libraries in your functionality without needing to consist of them in your deployment package deal. It’s possible to create a layer in a single account also, and have another account consume that coating. Let’s become a publisher of a level. In this use situation, you wish to use program code signing in order that consumers of one’s layer might have the protection assurance that no-one provides tampered with the coating. Note that if you enable program code signing to verify signatures on a level, Lambda may verify the signatures on the event code also. Therefore, all your deployment artifacts should be signed, using a user profile detailed in the CSC mounted on the function.
Number 3 illustrates the cross-account layer pattern, in which a layer is signed simply by you within a publishing accounts and a function uses that layer within another consuming account.

Figure 3: This sophisticated pattern works with cross-account layers
Are the steps to create this setup here. Be logging directly into two various accounts you’ll, your publishing accounts as well as your consuming account.
Make the publisher signing account
Running this order shall offer you a profile version ARN. Take note of the worth returned to utilize in a later stage.
To create a publisher signing user profile
- Inside the AWS CLI, get on your publishing accounts.
- Run this command to produce a signing profile for the publisher:
Sign your layer program code using signing profile
Next, you would like to indication your layer program code with this particular signing profile. Because of this example, utilize the blank layer program code out of this GitHub project. You may make your personal layer by developing a ZIP document with all of your code files contained in a directory backed by your Lambda runtime. AWS Lambda layers has instructions for creating your personal layer.
After that you can sign your layer program code utilizing the signing profile.
To signal your layer program code
- Name your own Lambda layer code document blank-python.zip and upload it to your S3 bucket.
- Indication the zipped Lambda perform using AWS Signer with the next command. Replace and with the facts from your own uploaded blank-python.zip.
Publish your own signed layer
Publish the resulting now, signed layer. Remember that the layers themselves don’t possess signature validation on deployment. However, the signatures will be checked when they’re put into a function.
To publish your signed coating
- Download your brand-new signed ZIP document from your own S3 bucket, and rename it signed-layer.zip.
- Run the next command to create your layer:
This command will return information regarding your published layer newly. Seek out the LayerVersionArn and take note of it for use afterwards.
Grant read accessibility
For the last part of the publisher account, you need to grant read usage of the layer utilizing the add-layer-version-permission command. In the next command, you’re granting usage of an individual account utilizing the principal parameter.
(Optional) You can instead elect to grant usage of all accounts inside your company by using “*” because the principal and adding the organization-id parameter.
To grant read access
- Run the next command to grant study usage of your layer, changing with the accounts ID of one’s second account:
Create a CSC
It’s time to change your AWS CLI to utilize the consuming accounts. A CSC could be developed by this consuming take into account their Lambda features that specifies what signing profiles are allowed.
To develop a CSC
- Inside the AWS CLI, log from your own publishing accounts and into your consuming accounts out.
- The consuming account will require a signing profile of its to sign the primary Lambda code. Operate the following command to generate one:
- Run the next command to produce a CSC that allows program code to end up being signed possibly by the publisher or even the buyer. Replace with the user profile edition ARN you created inside the preceding action. Replace with the signing user profile from the Help make a publisher signing user profile procedure. Take note of the CSC came back by this command to utilize in later steps.
Create the Lambda function utilizing the CSC
When creating the event that uses the signed layer, it is possible to pass within the CSC that you created. Lambda shall check out the signature on the event code in this task.
To develop a Lambda function
- Use your personal lambda code function, or even make a duplicate of blank-python.zip, and rename it consumer-main-function.zip.) Upload consumer-main-functionality.zip to the versioned S3 bucket inside your consumer accounts.
Note: If the S3 bucket doesn’t possess versioning enabled, the task will fail.
- Sign the event with the signing user profile of the buyer account. Replace and inside the next command with the title of the S3 bucket you uploaded the consumer-main-function.zip to and the edition.
- Download your new document and rename it to signed-consumer-main-perform.zip.
- Run the next command to produce a new Lambda perform, changing with a legitimate Lambda execution function and with the worthiness returned from the prior procedure: Creating the CSC.
- Lastly, add the signed layer from the publishing account in to the configuration of this function. Run the next command, replacing with the effect from the preceding phase Publish your signed level.
Lambda shall check out the signature on the coating code in this task. If the signature of any deployed level artifact will be corrupt, the Lambda functionality stops you from attaching the coating and deploying your program code. That is true of the mode you choose-WARN or ENFORCE regardless. If you have several layers to increase your function, all layers should be signed by you invoked inside a Lambda function.
This capability allows layer publishers to talk about signed layers. A publisher can indication all layers utilizing a specific signing user profile and ask all of the layer consumers to utilize that signing profile among the allowed profiles within their CSCs. When somebody uses the level, they are able to trust that the coating originates from that publisher and hasn’t already been tampered with.
Conclusion
You’ve learned some best patterns and methods for using program code signing for AWS Lambda. You understand how code signing ties in the protected SDLC, and what worth you get from each one of the program code signing checks. Additionally you learned two styles for using program code signing for distributed ownership-one for centralized signing and something for cross account level validation. Regardless of your role-as a programmer, as a central safety group, or as a coating publisher-you may use these tools to greatly help enforce the integrity of program code artifacts in your company.
You can find out about Lambda program code signing in Configure code signing for AWS Lambda.
When you have feedback concerning this post, submit remarks in the Comments section below. Should you have questions concerning this post, start a brand-new thread on the AWS Lambda forum or contact AWS Support.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.
