Getting started off with AWS SSO delegated administration
Lately, AWS launched the opportunity to delegate management of AWS Single Sign-About (AWS SSO) in your AWS Businesses organization to an associate account (a merchant account apart from the management account). This post will highlight a practical method of using this new function. For the documentation because of this function, notice Delegated management in the AWS Single Sign-On Consumer Guide.
<pre> <code> <p>With <a href="https://aws.amazon.com/businesses/" focus on="_blank" rel="noopener noreferrer">AWS Companies</a>, your business corporation can manage your accounts even more securely and at level. One of the great things about Organizations will be that it integrates with a great many other AWS providers, so that you can centrally manage accounts and the way the solutions in those accounts may be used.</p>
<p>AWS SSO is where you are able to create, or connect, your workforce identities inside AWS just once, and then manage gain access to centrally across your AWS firm. It is possible to create user identities straight in AWS SSO, or you can provide them from your own Microsoft Active Directory or perhaps a standards-based identity provider, such as Okta Common Directory or Azure Advertisement. With AWS SSO, you obtain a unified management experience to define, personalize, and assign fine-grained entry.</p>
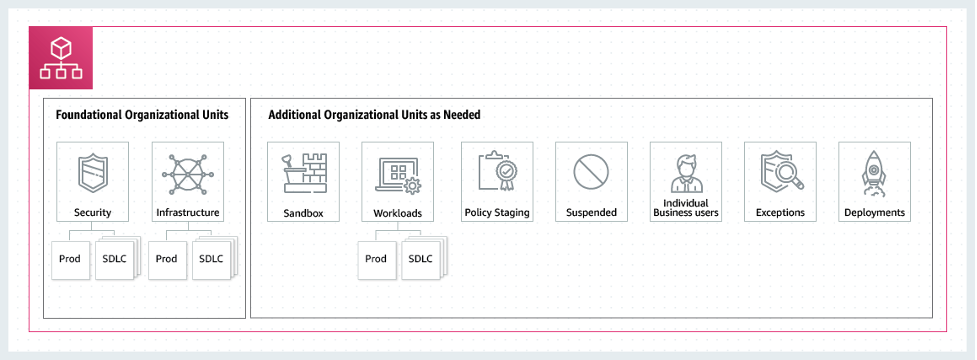
<p>Automagically, the management account within an AWS organization gets the power and authority to control member accounts in the business. Due to these additional permissions, it is very important exercise minimum privilege and tightly handle usage of the management account. <a href=”https://aws.amazon.com/companies/getting-started/best-practices/” focus on=”_blank” rel=”noopener noreferrer”>AWS recommends</a> that enterprises create a number of accounts particularly designated for protection of the organization, with proper settings and access management guidelines in place. AWS offers a method where many services could be administered for the business from the member account; this is usually known as a <em>delegated administrator</em> accounts. These accounts can have a home in a <a href=”https://docs.aws.amazon.com/prescriptive-guidance/most recent/security-reference-architecture/security-tooling.html” focus on=”_blank” rel=”noopener noreferrer”>security organizational device (OU)</the>, where administrators can enforce organizational policies. Physique 1 is an exemplory case of a recommended group of OUs in Agencies.</p>
<div id=”attachment_25227″ course=”wp-caption alignnone”>
<img aria-describedby=”caption-attachment-25227″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/05/10/picture1.png” alt=”Figure 1: Recommended AWS Institutions OUs” width=”977″ elevation=”360″ class=”size-complete wp-image-25227″>
<p id=”caption-attachment-25227″ course=”wp-caption-text”>Figure 1: Recommended AWS Businesses OUs</p>
</div>
<p>Numerous AWS services support this delegated administrator model, including <a href=”https://docs.aws.amazon.com/guardduty/current/ug/guardduty_organizations.html” focus on=”_blank” rel=”noopener noreferrer”>Amazon GuardDuty</the>, <a href=”https://docs.aws.amazon.com/securityhub/most recent/userguide/designate-orgs-admin-account.html” focus on=”_blank” rel=”noopener noreferrer”>AWS Protection Hub</the>, and <a href=”https://docs.aws.amazon.com/macie/most recent/user/accounts-mgmt-ao.html” focus on=”_blank” rel=”noopener noreferrer”>Amazon Macie</the>. For an up-to-date complete listing, discover <a href=”https://docs.aws.amazon.com/organizations/most recent/userguide/orgs_integrate_services_list.html” focus on=”_blank” rel=”noopener noreferrer”>AWS services which you can use with AWS Companies</the>. AWS SSO is currently the newest addition to the set of providers in which it is possible to delegate administration of one’s users, groupings, and permissions, which includes third-party applications, to an associate account of one’s organization.</p>
<h2>How exactly to configure the delegated administrator accounts</h2>
<p>In this situation, your enterprise AnyCompany comes with an organization comprising a management account, a merchant account for managing safety, in addition to a few associate accounts. You have allowed AWS SSO in the business, but you desire to enable the protection team to control permissions for accounts and functions in the organization. AnyCompany doesn’t want one to supply the security team usage of the management account, plus they furthermore want to make certain the security group can’t delete the AWS SSO construction or manage usage of that account, and that means you opt to delegate the management of AWS SSO to the safety account.</p>
<p><strong>Notice</strong>: There are some things to consider when coming up with this change, that you should review prior to you enable delegated management. These items are protected in the console through the process, and are explained in the area <a href=”https://aws.amazon.com/blogs/security/getting-started-with-aws-sso-delegated-administration/#_Considerations_when_delegating” target=”_blank” rel=”noopener noreferrer”>Factors when delegating AWS SSO management</a> in this article.</p>
<h3>To delegate AWS SSO management to a security accounts</h3>
<ol>
<li>In the <a href=”https://gaming console.aws.amazon.com/agencies” focus on=”_blank” rel=”noopener noreferrer”>AWS Organizations system</a>, get on the <a href=”https://docs.aws.amazon.com/organizations/recent/userguide/orgs_getting-started_concepts.html” focus on=”_blank” rel=”noopener noreferrer”>management accounts</a> with a user or role which has permission to utilize <a href=”https://docs.aws.amazon.com/organizations/most recent/APIReference/API_RegisterDelegatedAdministrator.html” focus on=”_blank” rel=”noopener noreferrer”>institutions:RegisterDelegatedAdministrator</the>, and also AWS SSO administration permissions.</li>
<li>In the <a href=”https://gaming console.aws.amazon.com/singlesignon/home” focus on=”_blank” rel=”noopener noreferrer”>AWS SSO system</a>, demand Region where AWS SSO is allowed.</li>
<li>Choose <strong>Configurations</strong> on the left routing pane, and then pick the <strong>Administration</strong> tab on the proper side.</li>
<li>Under <strong>Delegated administrator</strong>, select <strong>Register accounts</strong>, simply because shown in Figure 2.
<div id=”attachment_25228″ course=”wp-caption alignnone”>
<img aria-describedby=”caption-attachment-25228″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/05/10/picture2.jpg” alt=”Figure 2: The registered account switch inside AWS SSO” width=”763″ height=”225″ course=”size-full wp-picture-25228″>
<p id=”caption-attachment-25228″ course=”wp-caption-text”>Figure 2: The <strong>Register accounts</strong> key in AWS SSO</p>
</div></li>
<li>Think about the implications of designating a delegated administrator accounts (as described in the area <a href=”https://aws.amazon.com/blogs/security/getting-started-with-aws-sso-delegated-administration/#_Considerations_when_delegating” target=”_blank” rel=”noopener noreferrer”>Factors when delegating AWS SSO management</a>). Choose the account you intend to have the ability to manage AWS SSO, and choose < then;strong>Register accounts</strong>, mainly because shown in Figure 3.
<div id=”attachment_25229″ course=”wp-caption alignnone”>
<img aria-describedby=”caption-attachment-25229″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/05/10/picture3.jpg” alt=”Figure 3: Selecting a delegated administrator accounts inside AWS SSO” width=”995″ height=”751″ course=”size-full wp-picture-25229″>
<p id=”caption-attachment-25229″ course=”wp-caption-text”>Figure 3: Selecting a delegated administrator account inside AWS SSO</p>
</div></li>
</ol>
<p>You need to visit a success message to point that the AWS SSO delegated administrator account is currently setup.</p>
<h3>To eliminate delegated AWS SSO administration from an accounts</h3>
<ol>
<li>In the <a href=”https://gaming console.aws.amazon.com/businesses” focus on=”_blank” rel=”noopener noreferrer”>AWS Organizations system</a>, get on the <a href=”https://docs.aws.amazon.com/organizations/best and newest/userguide/orgs_getting-started_concepts.html” focus on=”_blank” rel=”noopener noreferrer”>management accounts</the> with a consumer or role which has permission to utilize <a href=”https://docs.aws.amazon.com/organizations/newest/APIReference/API_DeregisterDelegatedAdministrator.html” focus on=”_blank” rel=”noopener noreferrer”>companies:DeregisterDelegatedAdministrator</the>.</li>
<li>In the <a href=”https://gaming console.aws.amazon.com/singlesignon/home” focus on=”_blank” rel=”noopener noreferrer”>AWS SSO system</a>, demand Region where AWS SSO is allowed.</li>
<li>Choose <strong>Configurations</strong> on the left routing pane, and then pick the <strong>Administration</strong> tab on the proper side.</li>
<li>Under <strong>Delegated administrator</strong>, choose <strong>Deregister accounts</strong>, simply because shown in Figure 4.
<div id=”attachment_25230″ course=”wp-caption alignnone”>
<img aria-describedby=”caption-attachment-25230″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/05/10/picture4.jpeg” alt=”Figure 4: The Deregister account switch inside AWS SSO” width=”470″ height=”288″ course=”size-full wp-picture-25230″>
<p id=”caption-attachment-25230″ course=”wp-caption-text”>Figure 4: The <strong>Deregister accounts</strong> switch in AWS SSO</p>
</div></li>
<li>Think about the implications of eliminating a delegated administrator accounts (as described in the area <a href=”https://aws.amazon.com/blogs/security/getting-started-with-aws-sso-delegated-administration/#_Considerations_when_delegating” target=”_blank” rel=”noopener noreferrer”>Factors when delegating AWS SSO management</a>), after that enter the account title that is presently administering AWS SSO, and select <strong>Deregister accounts</strong>, mainly because shown in Figure 5.
<div id=”attachment_25231″ course=”wp-caption alignnone”>
<img aria-describedby=”caption-attachment-25231″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2022/05/10/picture5.jpeg” alt=”Figure 5: Considerations of deregistering the delegated administrator inside AWS SSO” width=”460″ height=”415″ course=”size-full wp-picture-25231″>
<p id=”caption-attachment-25231″ course=”wp-caption-text”>Figure 5: Considerations of deregistering the delegated administrator inside AWS SSO</p>
</div></li>
</ol>
<p>There are some considerations you have to keep in mind once you delegate AWS SSO administration. The initial consideration will be that the delegated administrator accounts will not be capable to perform the next actions:</p>
<ul>
<li>Delete the AWS SSO construction.</li>
<li>Delegate (to other accounts) management of AWS SSO.</li>
<li>Manage user or group usage of the management account.</li>
<li>Manage authorization sets which are provisioned (have the user or team assigned) in the business management accounts.</li>
</ul>
<p>For types of those last 2 actions, consider the subsequent scenarios:</p>
<p>In the initial scenario, you are controlling AWS SSO from the delegated administrator account. You want to provide your colleague Saanvi usage of all of the accounts in the business, like the management account. This step wouldn’t normally be allowed, because the delegated administrator accounts cannot manage usage of the management account. You’ll need to get on the management accounts (with a consumer or role which has appropriate permissions) to provision that entry.</p>
<p>In another scenario, you want to change the permissions Paulo has in the administration account by modifying the plan mounted on a ManagementAccountAdmin permission set, which Paulo currently has usage of. In this scenario, you’ll also have to do that in the management account, because the delegated administrator accounts doesn’t have permissions to change the permission set, since it will be provisioned to a consumer in the management accounts.</p>
<p>With those caveats at heart, users with correct access in the delegated administrator account can control permissions and assignments for users and groups through the entire AWS organization. To find out more about limiting that handle, observe <a href=”https://docs.aws.amazon.com/singlesignon/current/userguide/iam-auth-access-using-id-guidelines.html#policyexamplemanageaccount” focus on=”_blank” rel=”noopener noreferrer”>Allow a consumer to manage AWS SSO for particular accounts</the> in the AWS Solitary Sign-On User Manual.</p>
<p>Deregistering a good AWS SSO delegated administrator account won’t affect any permissions or even assignments within AWS SSO, but it will take away the ability for customers in the delegated accounts to control AWS SSO from that accounts.</p>
<h2>Extra considerations if you are using Microsoft Energetic Directory</h2>
<p>You can find additional considerations that you should keep within mind if you are using Microsoft Active Directory (AD) being an identity provider, specifically if you are using <a href=”https://docs.aws.amazon.com/singlesignon/most recent/userguide/provision-users-from-ad-configurable-ADsync.html” focus on=”_blank” rel=”noopener noreferrer”>AWS SSO configurable Advertisement sync</the>, and which AWS accounts the directory resides in. To be able to make use of AWS SSO delegated management once the identity source is defined to Dynamic Directory, AWS SSO configurable Advertisement sync must be allowed for the directory. Your organization’s administrators must synchronize Energetic Directory users and organizations you would like to grant usage of into an AWS SSO identification store. Once you enable AWS SSO configurable Advertisement sync, a new function that <a href=”https://aws.amazon.com/about-aws/whats-new/2022/04/aws-single-sign-on-configurable-synchronization-microsoft-active-directory/” target=”_blank” rel=”noopener noreferrer”>released in April</the>, Active Directory administrators can choose which customers and groups obtain synced into AWS SSO, much like how other external identification providers work today with all the <a href=”https://docs.aws.amazon.com/singlesignon/most recent/developerguide/what-is-scim.html” focus on=”_blank” rel=”noopener noreferrer”>Program for Cross-domain Identity Administration (SCIM) v2.0 process</a>. This real way, AWS SSO is aware of users and groups actually before they’re granted usage of specific accounts or functions, and AWS SSO administrators don’t need to manually seek out them.</p>
<p>One more thing to take into account when delegating AWS SSO administration when working with AD being an identity source is usually where your directory resides, that’s which AWS account owns the directory. If you opt to switch the AWS SSO identification source from any source to Energetic Directory, or change it out from Energetic Directory to any source, then your directory must have a home in (be possessed by) the accounts that the change has been performed in. For instance, if you are presently signed into the management account, it is possible to only change the identification resource to or from web directories that have a home in (are possessed by) the administration account. To learn more, notice <a href=”https://docs.aws.amazon.com/singlesignon/most recent/userguide/manage-your-identity-source.html” focus on=”_blank” rel=”noopener noreferrer”>Manage your identification source</the> in the AWS Individual Sign-On User Guideline.</p>
<h2>Guidelines for managing AWS SSO with delegated management</h2>
<p>AWS recommends the next best practices when working with delegated management for AWS SSO:</p>
<ul>
<li>Maintain individual permission sets for used in the business management account (versus all of those other accounts). This way, permissions could be kept separate and handled from within the management accounts without causing confusion on the list of delegated administrators.</li>
<li>When granting usage of the organization management accounts, grant the usage of groups (and permission units) designed for access for the reason that account. This can help enable the main of <em>minimum privilege</em> because of this important accounts, and helps to ensure that AWS SSO delegated administrators can manage all of those other organization as effectively as you possibly can (by reducing the amount of users, organizations, and permission sets which are off limits in their mind).</li>
<li>In the event that you strategy on using among the AWS Directory Services for Microsoft Active Directory (<a href=”https://docs.aws.amazon.com/directory-support/?id=docs_gateway” focus on=”_blank” rel=”noopener noreferrer”>AWS Managed Microsoft Advertisement or Advertisement Connector</the>) mainly because your AWS SSO identification resource, locate the directory and the AWS SSO delegated administrator accounts in exactly the same AWS accounts.</li>
</ul>
<h2>Summary</h2>
<p>In this article, you learned all about a helpful new function of AWS SSO, the opportunity to delegate administration of one’s users and permissions to an associate account of one’s organization. AWS recommends as a greatest practice that the administration accounts of an AWS business be secured by way of a least privilege entry model, where as few individuals as possible get access to the accounts. It is possible to enable delegated management for supported AWS solutions, which includes AWS SSO, as a good tool to assist your organization minimize usage of the management accounts by moving that handle into an AWS accounts designated designed for security or identification services. We encourage one to consider AWS SSO delegated management for administrating accessibility in AWS. To learn more concerning the new feature, observe <a href=”https://docs.aws.amazon.com/singlesignon/most recent/userguide/delegated-admin.html” focus on=”_blank” rel=”noopener noreferrer”>Delegated management</the> in the AWS Solitary Sign-On User Manual.</p>
<p>In case you have feedback concerning this post, submit feedback in the <strong>Feedback</strong> area below. For those who have questions concerning this post, start a fresh thread on the <a href=”https://forums.aws.amazon.com/discussion board.jspa?forumID=76″ target=”_blank” rel=”noopener noreferrer”>AWS IAM discussion board</the> or <a title=”contact AWS Assistance” href=”https://system.aws.amazon.com/assistance/home” focus on=”_blank” rel=”noopener noreferrer”>contact AWS Assistance</the>.</p>
<p><strong>Want a lot more AWS Security how-to content material, news, and show announcements? Adhere to us on <a name=”Twitter” href=”https://twitter.com/AWSsecurityinfo” focus on=”_blank” rel=”noopener noreferrer”>Twitter</the>.</strong></p>
<!– ‘”` –>
