Finding your way through Critical Infrastructure Changes within Australia
In lighting of the latest May 2021 Federal Spending budget, which puts concentrate on Cybersecurity, the Australian Government’s increased focus on protecting essential infrastructure from cyberattacks can be an important part of strengthening our capability to defend the Australian economy and society most importantly.
The Australian Government’s Safety Legislation Amendment (Important Infrastructure) Costs 2020 introduces an expanded and improved legislative framework for safeguarding critical infrastructure and techniques of national importance (CISONS), building on 2018’s Security of Vital Infrastructure (SOCI) Act. Significant in this new Bill may be the growth of the entities it addresses, beyond the utilities and ports protected beneath the SOCI 2018 Work to now include conversation and data facilities along with industries such as advanced schooling, research, grocery and food, healthcare, transportation, and many more. All in all, 11 industries are incorporated now.
There is a lot work to be achieved for affected entities, you start with the necessity to understand the obligations which will be placed upon them and to ensure they are able to meet these expectations. At Cisco, we’ve been mixed up in consultative method the Australian federal government is taking actively, not only as an integral player in an market that is included in this legislation, but being an advocate for the customers in every sectors also. {Our initial {insight} can be {discovered} here and comments on the {publicity|direct exposure} draft here.
The government’s strategy {could be} {divided} into three key areas (note: {that is} our grouping); reporting obligations, cyber risk {administration}, and operational capabilities.
-
- Reporting obligations {relate with} organisational, {provide} chain, and asset {info|details} – {this category {also contains} cyber incident reporting,|this category {consists of|contains} cyber incident reporting,} {with {enough time} window for notification {furthermore} being shortened.|with {enough time} window for notification being shortened.}
-
- Cyber {danger} management {will dsicover} organisations {having to} adopt ({should they} haven’t already) {danger} management processes for {crucial|essential|important|vital} services, {considering} all hazards, {requirements and threats.} Cyber risk {will probably} {are categorized as} the ownership of {table|panel|plank} or executive leadership, {{once we} have seen elsewhere {all over the world}.|{once we} have seen {all over the world} elsewhere.} {Industry specific regulations {may also be} likely,|Industry specific regulations {tend} {furthermore},} with regulators appointed {for every} industry, and co-{style} of standards and {needs|specifications} the stated {objective}.
-
- {For} operational capabilities, {{we will have} the bolstering of cyberthreat {discussing|posting|revealing|expressing} and incident assistance.|{we will have} the bolstering of cyberthreat incident and sharing assistance.} {Faster and industry-{particular} cyberthreat sharing {will undoubtedly be} an important {capacity to} uplift readiness {over the} board.|Faster and industry-{particular} cyberthreat sharing {will be} an important {capacity to} uplift readiness {over the} board.} The government {can be} {buying} furthering the Australian Cyber {Protection|Safety} Centre’s (ACSC) incident {reaction} and assistance capabilities. {A lot more} on {which can be} read {inside our} submission.
Much, {nevertheless}, remains undefined, with {field|industry} specific workshops {along with other} efforts still {ahead} (at time of {composing|creating}). That doesn’t mean {we ought to|we have to} wait – {{there exists a} lot {we are able to} do {to get ready} for {what’s} ahead.|{there exists a} lot {we are able to} do ahead {to get ready} for what is.}
{Finding your way through} what’s {forward}
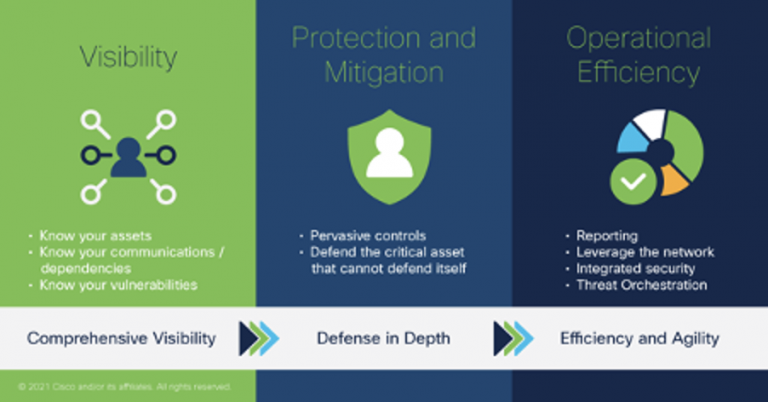
We can {breakdown} {what you can do} today into three {places|locations}:

Firstly, visibility {is crucial} – knowing what {property|resources|possessions} you {possess}, how they {talk to} {one another}, and over what protocols. {Because the} {aged|older|outdated|previous} adage {will go}, you cannot secure {everything you} don’{t about know,} but you {furthermore} can’t {observe|notice|discover|find} what isn’t visible. {In lots of} organisations, {and particularly Operational Technology {conditions},|and Operational Technology environments {especially},} {visibility is lacking,} {although it remains {crucial|essential|important|vital} to {knowing} vulnerabilities and truly {having the ability to} assess risk.|although it {continues to be} critical to understanding vulnerabilities and {having the ability to} assess risk truly.}
{Once we {know very well what} we are securing,|We know what {we have been} securing once,} we can {proceed|shift} onto mitigating known weaknesses and protecting it. {{The truth} today is {that lots of} organizations have devices {which are} insecure operationally {because of} not being patched,|{Nowadays|These days} is {that lots of} organizations have devices {which are} insecure operationally {because of} not being patched {the truth},} but as aforementioned, you can’t patch {everything you} don’t {understand} about. {{Understanding} what you have {furthermore} means {it is possible to} better assess what {extra} layers of defense {could possibly be} useful.|{Understanding} {everything you} have also means {it is possible to} assess what {extra} layers of defense {could possibly be} useful better.}
{Now that {we’ve} gained {presence} and begun {to do something},|{That people} have gained {presence} and begun {to do something} now,} we can {concentrate on} improving operational {effectiveness|performance}. The competing pressures of elevated cyberthreat landscapes and constrained budgets {imply|suggest|indicate} {we should} do more with {much less}, and {obtaining|getting|locating|acquiring|selecting} efficiencies {is vital} for managing {the excess} new responsibilities {that may|which will} come {beneath the} expanded Act, {like the} {have to} report incidents faster.
These {appear to be} challenging tasks, {however the} {procedure for} adaptation to the proposed changes {within} the Act {could be} smoothed by {concentrating on} integrated security. {Developing your network as {an electronic} platform means the {protection|safety} components can all {interact},|{Building|Establishing|Creating} your network as {an electronic} platform means the {protection|safety} components can all {continuing|continuous} work together,} incorporating the ingestion of {danger|risk} intelligence, sharing of {related|appropriate} context, enhancing {recognition} and response {abilities|features}, and containment and {recuperation} {procedures|functions}. But this all {takes a} cohesive approach.
{Security {is not any} longer a bolt-on {item}.|Security {is not any} a bolt-on product {lengthier}.} It {should be} integrated with {options}, {{which} means solutions {should be} considered holistically.|and this means {options} must holistically {be looked at}.} Digitization interweaves digital {abilities|features} {in your} businesses, and {we should} engineer digital capabilities {exactly the same} {method} we engineer {bodily|actual physical|actual} infrastructure. An all-hazards {strategy|method|technique} {backs this up} concept, and cybersecurity {should be} baked into everything we {perform}.
Cisco embraces this holistic {strategy|method|technique}, and embeds cybersecurity within its {items} , and {guarantees} the cyber {requirements} of our {clients} {are in} the forefront of everything we {perform}. {As {a reliable} partner of key {crucial|essential|important|vital} infrastructure operators globally and within Australia,|As {a reliable} partner of key {crucial|essential|important|vital} infrastructure operators and within Australia globally,} Cisco knows {how exactly to} {assist} navigate the digitization and cybersecurity {difficulties|problems|issues} {the present day} critical infrastructure landscape {provides|offers|gifts}. {In case you have|For those who have|When you have|Should you have} further {attention|curiosity}, please {get in touch with} a Cisco representative {to go over} how to best {plan} your {crucial|essential|important|vital} infrastructure obligations.
We’d {want to} hear {everything you} think. {Ask a relevant question,} Comment Below, and {Remain} {Linked to} Cisco Secure on {interpersonal}!
Cisco Secure Social {Stations}
Instagram
Facebook
Twitter
LinkedIn

You must be logged in to post a comment.