Extended and relevant Recognition with SecureX
In a latest blog , Al Huger spoke about Cisco’s vision of Extended Recognition and Response (XDR) ; specifically within the breadth of definitions in the market and clarifying Cisco’s description of XDR:
“A unified protection incident detection and reaction system that collects and correlates information from multiple proprietary safety components automatically.”
He also detailed the true way Cisco’s method of XDR is started upon our cloud-native system SecureX. In this website series I’m likely to broaden on that XDR description and explore how prolonged detection along with other XDR outcomes may be accomplished these days leveraging the SecureX system and integrated products.
The phrase “Extended Recognition” conjures up a graphic of several data elements, perhaps most of them considered reduced fidelity signals otherwise, all merged right into a single, high-fidelity alert. This extended detection is indeed wonderful an analyst can access the business enterprise relevance immediately, the risk, the primary cause and the correct response actions; maybe this alert is indeed explainable that all this could be done instantly at machine-scale. Before we reach this constant state of nirvana, let’s have a step back and appearance at the expression “Extended Recognition” and that end condition. Everything begins with a recognition.
But could it be important?
That question – “but could it be important” – is due to a far more fundamental one: what does this alert mean if you ask me? Today inside our security operations centres, we can have a genuine number of items that generate detections, observations, sightings, etc. that feed into our operational procedures. By themselves these alerts indicate something of fascination with the space of this security tool potentially. For instance, an Endpoint Recognition and Response item such as for example Cisco Secure Endpoint can make the observation of a malicious document seen on a bunch or a Network Recognition and Response item such as for example Cisco Secure System Analytics can make an observation of a bunch downloading a suspiciously higher amount of information. These alerts reveal that something happened however, not what this means in the context of the surroundings that it fired -your environment – creating that authentic question: “but could it be important?”
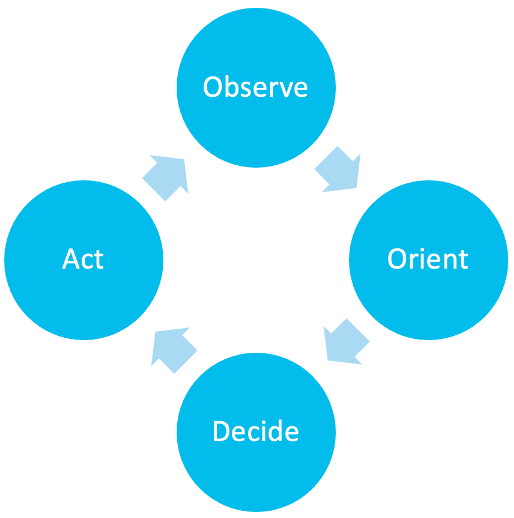
If you ask me “importance” is in the attention of the beholder. So what can certainly be a false positive in a single atmosphere is that high-fidelity, actionable pure-gold occasion in another: with the only real difference being the surroundings the alert fired in. If we revisit the idea of the OODA (Observe, Orient, Decide, Work) loop for an instant, this is actually the second action of Orientation, bringing into consideration the environment variables that whenever held contrary to the initial observation accelerate the actions and decision phases.

In the Orient phase we have been bringing domain variables, like the user, device, application, severity, etc., to answer fully the question “but could it be important together?” and the essence behind what we have been doing is expansion: extending the observation, or that preliminary detection into something even more. This is actually the empirical prioritisation of incidents that issue.
This elevation of an observation or perhaps a recognition to an incident worth focusing on is really a central concept in Extended Recognition and Response. The results that we want may be the creation of an extremely actionable incident, one which is enriched with information and context concerning the nouns and verbs included in order that we can create an informed decision concerning the incident and, within an ideal planet, playbook a response in a way that when comparable incidents, with comparable verbs and nouns show up, trigger the right response actions automatically.
Among the trickiest elements of this discussion is what those variables – those nouns and verbs – are and which are the types that matter to a business. Some customers I’ve caused treat endpoint events because the highest intensity and highest danger, others choose MITRE Strategies, Techniques and Processes (TTPs) as their major objects of interest among others might prioritise around customers, devices, functions and applications within an organization. This great amount of variability signifies that there has to be versatility in the methodology of incident development, promotion and decoration.
Risk-Based Extended Recognition with SecureX
Our objective would be to enable a risk-based method of incident management. This enables a consumer of Cisco’s security recognition and response items to prioritise detections into incidents predicated on their own idea of danger – which as talked about, could vary corporation by organization.
In Cisco SecureX we’ve an Incident has been called by a good artifact. The SecureX Incident is really a combination of occasions, alerts, and cleverness concerning a possible protection compromise, which drives an incident reaction process which includes confirmation, triage, remediation and investigation. This idea of an Incident, in conjunction with configuration configurations in the integrated items and the investigation top features of Cisco SecureX Response will undoubtedly be used because the basis for the Extended enrichment and Recognition in this website series.
Today, an Incident could be created via an investigation or risk hunting exercise manually, or promoted automatically, predicated on construction, from some integrated items. As a construct the Incident is made on the Cisco Threat Cleverness Module (CTIM) and contains several primary tenants that enable enrichment with various variables linked to the Incident.
In the below number for example we’ve an Incident that has been automatically created through advertising from Cisco Secure Network Analytics. In the picture below, we visit a Custom Security Occasion “Employees to Bottling Range” with a higher severity level (the way the severity degree was derived would be the subject of another blog in this collection).

Clicking on “Investigate Incident” will start an investigation within Cisco SecureX Threat Reaction , immediately enriching the Observables in the Incident (in cases like this comprising two IP Addresses, a Macintosh Deal with and a username) leading to the beneath enrichment. This basic investigation enriched (or prolonged) the incident with information related from those observables across nine various integrated products, leading to the below diagram.

At this point we are able to further investigate, determining the relevancy or even impact associated with the sightings. But first we will have a Snapshot and include it to the present incident, conserving the enrichment.

While this very easy procedure took an alert in one item, manufactured an Incident and extended it with information from another item, we haven’t however dug into a few of the fundamentals that we desire to explore in this collection: namely, how exactly we can triage, prioritise and react to detections predicated on risk-driven metrics and variables that issue to your organization. Future articles in this collection will explore the various integrated items in SecureX and how their detections could be promoted, extended plus enriched in SecureX. In the next write-up in this series, we will begin with the automated promotion and triaging of endpoint events into Cisco SecureX.
Thinking about seeing the Incident Supervisor doing his thing? Activate your SecureX accounts now.
We’d want to hear everything you think. Ask a relevant question, Comment Below, and Remain Linked to Cisco Secure on sociable!
Cisco Secure Social Stations
Instagram
Facebook
Twitter
LinkedIn

You must be logged in to post a comment.