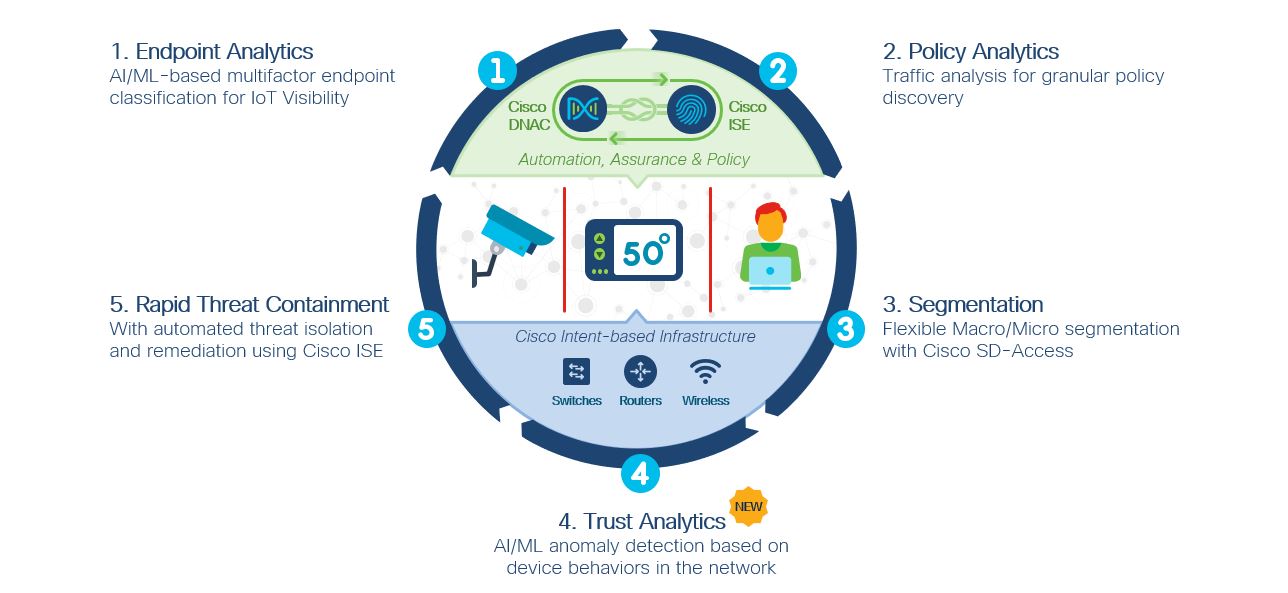
Establish, Enforce, and Continuously Verify Rely on with SD-Access in EASY STEPS
To effectively protect precious data assets across campuses from infiltration, exfiltration, and ransomware, Business IT needs deep presence into everything connecting to the system and the capability to segment gadgets by entry permissions and security guidelines. The target is to achieve a Zero-Trust Enterprise predicated on least-privileged access concepts that prevents the lateral motion of threats and immediately isolates any offending endpoint or intrusion.
Today, millions of business endpoints are usually protected with implementations of Cisco Software-Defined Entry ( SD-Accessibility ), a remedy within Cisco DNA Middle. Thousands of enterprises already are well along on the journey to finding a zero-trust system using endpoint analytics, plan analytics, segmentation, and fast threat containment abilities of SD-Access. Right now, with the intro of Constant Trusted Gain access to with SD-Access Rely on Analytics- making use of AI/ML anomaly modeling and spoofing prevention-the five phases of attaining zero-trust can be found to all forms of businesses at any phase of their implementation. The entire Cisco SD-Access answer provides inherent versatility for enterprises to begin with or carry on the zero-trust journey in accordance with their company priorities and preferred outcomes.
This software release will undoubtedly be generally available (GA) in mid-June 2021, or contact your account team for early access.

Existing Networks Reap the benefits of a Flexible Zero Believe in Journey
Cisco realizes that NetOps and SecOps must develop segmentation upon what’s already in place, adding capabilities in phases to attain the desired zero trust end result for both existing and brand new network installations. Organizations may use SD-Access to start out the trip to zero believe in at different stages based on business priorities.
Adventist Wellness started its zero rely on trip with Cisco AI Endpoint Analytics to get and categorize over 75,000 compute and IoT devices on the multi-state spanning network. Cisco AI Endpoint Analytics utilizes Deep Packet Examination (DPI) and sophisticated AI/ML algorithms to find crowdsourced databases to obtain additional granular information about a variety of device types. Adventist Wellness actually uses the enhanced gadget presence from AI Endpoint Analytics to recognize devices which are discontinued and no lengthier supported by producers, which are more vunerable to malware intrusions along with other threats. Adventist Wellness views AI Endpoint Analytics being an enabling technology that delivers the much-needed endpoint presence and safety grouping that will assist define their long term segmentation policies.
KB Securities required a more efficient approach to managing segmentation access plans as their workforce relocated openly among campus buildings. Rather than manually adjusting individual guidelines, they're using SD-Entry segmentation to instantly adjust and apply accessibility policies because the workforce shifts among wired and wifi networks, eliminating time-consuming guide interventions.
Among the largest finance institutions on the planet needed a zero believe in method for protecting the business’s worldwide connected endpoints. IT thought we would implement the brand new SD-Access Rely on Analytics to investigate and model regular endpoint conduct to detect anomalies that indicate intrusion efforts before they can result in a data breach of delicate information.
In SAIC Volkswagen’s new Modularer Elektrobaukasten plant-a modular chassis created by Volkswagen designed for electric cars-the creation systems have to be on individual networks for dependability and stability reasons. But rather of creating distinct networks, SD-Access just segments the single bodily network into several logical systems that keep production techniques traffic separate, but beneath the control of 1 Cisco DNA Middle. As a total result, the system is more manageable, also it can easier connect and secure a large number of IoT and robotic products through the entire plant. With Cisco SD-Access, SAIC Volkswagen could use existing L2 gain access to switches, enabling a easy migration of solutions and reducing up-front expenses.

Enterprises Come in Control of these Zero-Trust Journey
The opportunity to start the zero trust journey at a spot that aligns with the business enterprise priority for every enterprise expands the quantity and forms of use cases for Cisco SD-Access. Cisco SD-Access may be the only remedy in the market that provides all of the capabilities necessary for Zero-Trust at work with Presence (endpoint analytics and visitors policy discovery), Segmentation, Constant Trust Evaluation, and Containment which can be applied in phases to meet up each organization’s security objectives.
The recent updates to the SD-Access solution lowers the barrier to go on a zero-trust journey, in existing especially, heterogeneous networks. Each stage along the trip provides incremental value because the threat surface area diminishes and enterprises benefits more manage over every endpoint that joins the system by restricting the sources with that they can communicate. For instance, a new individual BYOD linking to the network could be identified, categorized, and at first assigned to a protection group segment that just has very limited usage of enterprise resources before device and proprietor are verified.
“AI Endpoint Analytics has greatly simplified how exactly we manage our network. We obtain the granular details we are in need of for every device, sufficient reason for its smart grouping of similar gadgets, we save time and decrease complexity by orders of magnitude.” – Brian Jensen, System Analyst, NEW YORK Department of Health insurance and Human Providers
Implement SD-Gain access to Segmentation Without Routed Entry
To support current estates that use a lot more traditional networking constructs, SD-Access now facilitates Layer 2 Switched Access like the option of preserving current VLANs and Ip pools. In this deployment situation, the SD-Access Material originates at the system aggregation layer. The perfect solution is offers the versatility for enterprises to map current entry VLANs to macro/micro segments in the SD-Access Fabric. To minimize lateral motion of threats, enterprises likewise have the option to increase the micro-segmentation plans to the Layer 2 Switched Accessibility node. These flexible style choices enable enterprises to begin with their zero-trust trip without re-designing their current networks.

Cisco SD-Access now supports Coating 2 Switched Gain access to
“Cisco networking products, Cisco DNA Middle, and SD-Access gave all of us a flexible networking system that we could adjust to our unique requirements. We could actually integrate third-party commercial switches, keep carefully the factory operating effectively by rapidly locating and repairing network issues, and totally free our highly-qualified engineers from day-to-day operational burdens.” – Xiaoqing XU, IT Director, SAIC Volkswagen
Deploy Macro-Segmentation Before Implementing Cisco ISE
The completely automated turnkey fabric-based architecture provided by SD-Access can be an attractive option to MPLS-based VRF, VRF-lite along with other operationally cumbersome legacy segmentation technologies. With Cisco DNA Middle release 2.2.2.0, we’ve disaggregated the features within SD-Access Materials. Enterprises will have the option to utilize SD-Access to quickly achieve macro-segmentation of systems even yet in scenarios where Cisco ISE isn’t currently being utilized to authenticate endpoints. This program helps it be easier for companies to begin with with SD-Entry and expand to additional use instances at their very own deployment pace and routine.
You Can’t Secure EVERYTHING YOU Can’t See
Among the early barriers to begin with building a zero-trust business is knowing what gadgets are usually connecting to the system, which devices and programs they’re communicating with, and creating a deep historical viewpoint to detect anomalies. That’s why numerous organizations-such because the Adventist Wellness example-begin with Endpoint Analytics to comprehend the existing threat surface and apply plan analytics to comprehend the behavior of visitors patterns.
Implementing Constant Trust Evaluation with the brand new Cisco Believe in Analytics allows IT to build up and use types of typical gadget behaviors, utilization, and traffic background to understand “regular” network operations to safeguard against spoofing attacks. Rely on Analytics detects visitors from endpoints which are exhibiting unusual conduct by pretending to become trusted endpoints using Mac pc Spoofing, Probe Spoofing, or Man-in-the-Middle techniques. When Believe in Analytics detects this kind of anomalies, it indicators Endpoint Analytics to lessen the Trust Rating for the endpoint to totally deny or limit usage of the network.

Supplementing the system with Cisco Identity Solutions Motor completes the continuous believe in cycle by aggregating gadget classification, segmentation rules, plus trust analytics to keep track of, identify, and isolate any kind of detected device anomalies that may indicate a breach or even infection. Cisco ISE provides quick danger containment and remediation by instantly detecting and isolating suspicious products or individuals logging in from uncommon or unknown locations.
Attaining Zero Trust is really a Flexible Journey
As the ultimate goal is really a zero-trust state for several devices, applications, and folks, each implemented capacity for SD-Access enables enterprises to get greater control on the protection of the system. To prioritize preferred outcomes, enterprises come in manage of the speed of the trip from starting place to end results. The Zero-Trust Business becomes a flexible trip as campus systems grow and adjust to new endpoint devices, IoT systems, geographic configurations, and applications which can be accessed from anywhere. All these improvements for the flexible trip to zero rely on are great things about Cisco DNA Center launch 2.2.2.0. Start your trip to zero trust nowadays with Cisco SD-Access.
“We have been convinced that SD-Access can help us create our operational manufacturing processes more efficient. Because of its holistic strategy and the interfaces to some other systems, we are able to automate a substantial part of our day to day work. During our Proof-of-Concept screening we verified that both linking L2 non-material switches to the SD-Access material and utilizing L2-just overlays are expected. Combined with the ability to configure customized VLAN IDs on the SD-Access fabric, they are a few of the fundamental functions we need to supply the necessary services for the customers.” – Christoph Hofmann, Referent IT-Betrieb Netze, Mitteldeutsche Flughafen AG (Leipzig and Dresden airports within Germany)
< p style=”text-align: middle”> Register right now for the Network Insider Collection on the internet seminar on June 22, 2021, where we delve into the most recent improvements in Cisco DNA Middle and SD-Access.
To find out more, visit these Cisco sources:
Cisco ISE 3.1 Simplifies the Changeover to Cloud
Cisco DNA Center Zero-Have confidence in Networking Ask the Professional Video
Have a look at our Cisco Networking movie channel
Sign up to the Cisco Networking blog site

You must be logged in to post a comment.