Enterprise Ransomware Protection
Ransomware attacks are a significant threat to enterprises worldwide. These malicious attacks can cripple an organization, leading to halt operations, data loss, financial damage, and a tarnished reputation. To combat this growing menace, strong and unyielding enterprise ransomware protection strategies are essential. This blog post delves into effective measures for safeguarding your business against ransomware threats, helping you ensure continuity and security.
Understanding Ransomware: A Growing Threat
Ransomware is a type of malicious software that encrypts files on a victim’s IT environment, rendering them inaccessible. Attackers then demand a ransom payment in exchange for the decryption key. Ransomware attacks can target any organization, regardless of size or industry, making it imperative for businesses to implement comprehensive protection strategies.
The Impact of Ransomware on Enterprises
The consequences of a ransomware attack can be devastating. Here are some potential impacts:
- Financial Loss: Paying the ransom can be costly, and there is no guarantee that the attackers will provide the decryption key. Additionally, a larger cost for organizations, in most cases higher than the ransom is the cost of halted operations, and in some cases revenue lost for not being able to sell its products or services.
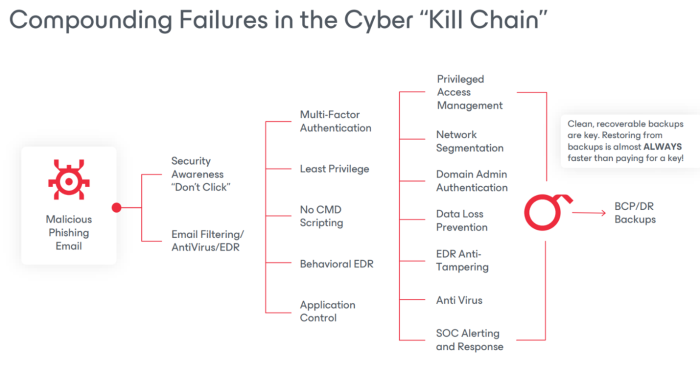
- Data Loss: Even if the ransom is paid, there is a risk of data corruption or loss during the decryption process. Regular backups are crucial, but without proper protection, these too can be compromised.
- Reputation Damage: Customers and clients expect their data to be secure. A ransomware attack can erode trust and damage an organization’s reputation, leading to long-term business consequences. There are no guarantees that customer data was not exfiltrated or stolen for future cyber crimes.
- Regulatory Penalties: Data protection regulations, such as GDPR and CCPA, impose strict requirements on organizations to protect personal data. A ransomware attack resulting in a data breach can lead to substantial fines and legal repercussions.
Key Strategies for Enterprise Ransomware Protection
To effectively protect your enterprise from ransomware attacks, a multi-layered approach is necessary. Here are some key strategies:
1. Employee Training and Awareness
Human error is often the weakest link in cybersecurity. Training employees to recognize phishing emails, suspicious links, and other common attack vectors is crucial. Regular awareness programs can significantly reduce the risk of a ransomware attack.
2. Regular Data Backups
Implementing a robust backup strategy is essential for ransomware protection. Regularly back up critical data and store copies offsite or in the cloud. Ensure that backups are encrypted and test the restoration process periodically to confirm data integrity.
3. Advanced Endpoint Protection
Deploying advanced endpoint protection solutions can help detect and prevent ransomware infections. These tools use machine learning and behavioral analysis to identify and block malicious activity in real-time. Keep all endpoint devices updated with the latest security patches.
4. Network Segmentation
Segmenting your network can limit the spread of ransomware within your organization. By isolating critical systems and data, you can contain an infection and prevent it from affecting the entire network. Implement access controls to restrict unnecessary communication between segments.
5. Email and Web Security
Many ransomware attacks are delivered via email or compromised websites. Implement email filtering solutions to block malicious attachments and links. Web security solutions can prevent access to known malicious websites and protect against drive-by downloads.
6. Regular Software Updates
Outdated software can contain unpatched vulnerabilities that ransomware exploits. Regularly update all software, including operating systems, applications, and security solutions. Enable automatic updates where possible to ensure timely patching of critical vulnerabilities.
7. Incident Response Planning
Having a well-defined incident response plan is crucial for minimizing the impact of a ransomware attack. This plan should include procedures for detecting an attack, containing the spread, communicating with stakeholders, and recovering from the incident. Regularly test and update your incident response plan to ensure its effectiveness.
8. Multi-Factor Authentication (MFA)
Implementing MFA adds an extra layer of security to your authentication processes. Even if an attacker obtains login credentials, they will still need a second form of verification to gain access. MFA can significantly reduce the risk of unauthorized access and ransomware attacks.
Veeam’s Role in Ransomware Protection
At Veeam, we understand the critical importance of ransomware protection for enterprises. Our comprehensive data protection solutions are designed to help businesses safeguard their data and ensure continuity in the face of ransomware threats.
Veeam Data Platform
- Early Threat Detection: AI-powered, built-in Malware Detection Engine performs low-impact inline entropy and file-extensions analysis during backup for immediate detection.
- Proactive Threat Hunting: Backup anomalies instantly reported to Service NOW and other SIEM tools for immediate triage.
- YARA rules: Avoid reinfection with YARA content analysis to identify ransomware strains to prevent the reintroduction of malware into the data backups
- Veeam Threat Center: Highlight threats, identify riks, and measure the security score of the backup environment.
- Immutable Backups: Protect your backups from being modified or deleted by ransomware with immutable storage options.
- Automated Recovery Testing: Ensure your backups are recoverable with automated testing and verification.
- Granular Recovery: Quickly recover individual files, applications, or entire VMs, minimizing downtime and data loss.
Veeam ONE
Veeam ONE provides advanced monitoring and analytics to help you stay ahead of potential ransomware threats. Key features include:
- Proactive Alerts: Receive real-time alerts for suspicious activity, enabling you to respond quickly to potential ransomware attacks.
- Capacity Planning: Ensure your backup infrastructure can handle the demands of recovery in the event of an attack.
- Compliance Reporting: Generate detailed reports to demonstrate compliance with data protection regulations.
Veeam Recovery Orchestrator
Veeam Recovery Orchestrator simplifies disaster recovery planning and execution, ensuring your business can recover swiftly from a ransomware attack. Key capabilities include:
- Automated Orchestration: Automate the recovery process, reducing the potential for human error.
- Compliance Documentation: Automatically generate documentation to prove compliance with recovery objectives.
- Testing and Validation: Regularly test your recovery plans to ensure they meet your business’s needs.
Veeam Cyber Secure
Veeam Cyber Secure is an unparalleled white glove service for Veeam Data Platform Premium customers. It includes expert design, support, and implementation services to make sure customers remain resilient. Veeam Cyber Secure offers quarterly assessments, training, and world-class ransomware incident response coverage from Coveware by Veeam. To complete the cyber secure coverage, ransomware recovery warranty is available, providing a reimbursement up to $5M USD to assist with recovery expenses.
Veeam Cyber Secure helps organizations get secure, stay secure, and minimize damage in the case of a ransomware attack.
Before a ransomware attack:
- Architectural design and implementation assistance
- Advanced Veeam onboarding
- Quarterly assessments and annual resiliency design review to avoid configuration drift and stay up to date on evolving security capabilities
- A dedicated Support Account Manager
- Prioritized incident routing with Veeam SWAT response team
- Coveware ransomware security training suited for audiences including executives, boards, and security teams
- Quarterly adversary tactics, techniques, and procedures (TTPs) analysis session
During a ransomware attack
- Coveware ransomware incident response retainer with 24/7 availability and 15-minute incident response SLA (2 incidents per year)
After a ransomware attack
- Optional $5M Ransomware Warranty
Conclusion
Ransomware is a threat that requires a proactive and comprehensive approach to protection. By implementing the strategies outlined in this blog post, enterprises can significantly reduce their risk and ensure the continuity of their operations. Veeam’s suite of data protection solutions, including the introduction of our Veeam Cyber Secure, provide the robust defense needed to safeguard your business against ransomware, ensuring your critical data remains secure and accessible.
Veeam protects your data before, during, and after a cyber incident through Veeam Cyber Secure, helping you with backup and security best practices, incident response through Coveware by Veeam, and financial protection after an attack.
Investing in enterprise ransomware protection is not just about preventing attacks; it’s about maintaining trust, compliance, and the ability to recover swiftly when the unexpected happens. Stay ahead of the threat with Veeam and protect what matters most to your business.
For more information on how Veeam can help protect your enterprise from ransomware explore our comprehensive solutions for enterprise applications. Don’t wait for an attack to happen — act now to secure your business’s future.
The post Enterprise Ransomware Protection appeared first on Veeam Software Official Blog.




You must be logged in to post a comment.