Disaster recovery compliance within the cloud, part 2: A structured approach
Compliance inside the cloud is fraught with misconceptions and myths. That is particularly true with regards to something as wide as disaster recuperation (DR) compliance where in fact the requirements are seldom prescriptive and often predicated on legacy risk-mitigation strategies that don’t take into account the excellent resilience of contemporary cloud-centered architectures. For regulated entities at the mercy of principles-structured guidance such as many finance institutions (FIs), the duty lies with the FI to find out what’s essential to adequately recover from a tragedy event. Without clear directions, FIs are vunerable to producing incorrect assumptions concerning their compliance needs for DR.
In Part 1 of the two-part series, We provided a few examples of common misconceptions possess about compliance specifications for disaster recovery inside the cloud FIs. PARTLY 2, I outline five actions you can take in order to avoid these misconceptions when architecting DR-compliant workloads for deployment on Amazon Web Providers (AWS).
1. Identify workloads prepared for deployment
It’s typical for FIs to get a portfolio of workloads they’re considering deploying to the cloud and frequently want to know they can be compliant over the panel. But compliance isn’t a one-size-fits-all domain-it’s in line with the characteristics of every workload. For example, will the workload contain individually identifiable information (PII)? Might it be utilized to store, procedure, or transmit charge card information? Compliance would depend on the solutions to queries such as for example these and should be assessed on a case-by-case basis. Therefore, step one in architecting for compliance would be to identify the precise workloads you intend to deploy to the cloud. This real way, you can measure the requirements of the specific workloads rather than be distracted by areas of compliance that may not be appropriate.
2. Define the workload’s resiliency requirements
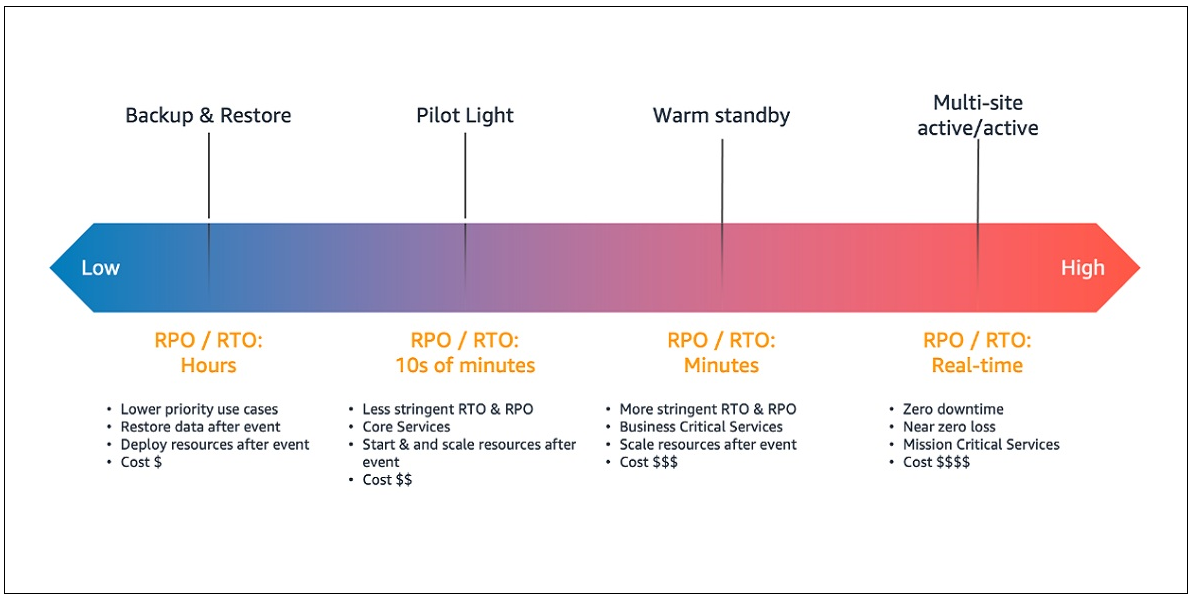
Resiliency may be the ability of a workload to recuperate from service or infrastructure disruptions. DR can be an important section of your resiliency strategy and concerns how your workload responds to a tragedy event. DR strategies on AWS range between simple, low priced options such as for example restore and backup, to more technical options such as for example multi-site active-active, as shown in Figure 1.
To find out more, You’re encouraged by me to learn Seth Eliot’s blog series on DR Architecture on AWS along with the AWS whitepaper Disaster Recovery of Workloads on AWS: Recovery in the Cloud.
The DR strategy you select for a specific workload is dependent on your own organization’s requirements for avoiding lack of data-known because the recovery point objective (RPO)-and reducing downtime where in fact the workload isn’t available -known because the recovery time objective (RTO). RPO and RTO are fundamental factors for determining the minimum architectural specifications essential to meet up with the workload’s resiliency requirements. For instance, can the workload’s RTO and RPO be performed utilizing a multi-AZ architecture within a AWS Region, or do the resiliency requirements necessitate deploying the workload across multiple AWS Regions? Even though your workload isn’t at the mercy of explicit compliance requirements for resiliency, understanding these requirements is essential for assessing other areas of DR compliance, including data geodiversity and residency.
3. Confirm the workload’s data residency requirements
WHEN I mentioned in Part 1, data residency requirements might restrict which AWS Regions or Region it is possible to deploy your workload to. Therefore, you need to verify if the workload is at the mercy of any data residency requirements within applicable regulations, corporate policies, or contractual obligations.
To be able to assess these requirements, you need to review the explicit language of certain requirements in order to understand the precise constraints they impose. You need to consult legal also, privacy, and compliance subject-matter specialists to assist you interpret these requirements in line with the characteristics of the workload. For instance, do the requirements declare that the info cannot leave the united states specifically, or can the necessity be met in order the data could be accessed from that country long? Does the necessity restrict you from storing a copy of the info in another country-for example, for backup and recovery purposes? Imagine if the info is encrypted and will only be read using decryption keys kept within the house country? Consulting subject-matter specialists to greatly help interpret these requirements might help you avoid making overly restrictive assumptions and imposing unnecessary constraints on the workload’s architecture.
4. Confirm the workload’s geodiversity requirements
An individual Region, multiple-AZ architecture is enough to meet up a workload’s resiliency requirements often. However, if the workload is at the mercy of geodiversity requirements, the length between the AZs within an AWS Region may not comply with the minimum distance between individual data centers specified by certain requirements. Therefore, it’s critical to verify whether any geodiversity requirements connect with the workload.
Like data residency, it’s vital that you measure the explicit language of geodiversity requirements. Are they on paper in a regulation or corporate policy, or are they a< just;em> recommended practice? Can certain requirements be met if the workload is deployed across three or even more AZs even though the minimum distance between those AZs is significantly less than the specified minimum distance between your primary and backup data centers? If it’s a corporate policy, does it enable exceptions if an alternative solution method provides equal or greater resiliency than asynchronous replication between two geographically distant data centers? Or simply the organization policy is outdated and really should be revised to reflect modern risk mitigation techniques. Understanding you will be helped by these parameters avoid unnecessary constraints as you assess architectural choices for your workloads.
5. Assess architectural options to meet up the workload’s requirements
That you realize the workload’s requirements for resiliency now, data residency, and geodiversity, it is possible to measure the architectural options that meet these requirements in the cloud.
According to AWS Well-Architected guidelines, you should shoot for the simplest architecture essential to meet your requirements. This consists of assessing if the workload could be accommodated inside a single AWS Region. If the workload is constrained by explicit geographic diversity requirements or has resiliency requirements that can’t be accommodated by way of a single AWS Region, you might have to architect the workload for deployment across multiple AWS Regions. If the workload is constrained by explicit data residency requirements also, then it could not be possible to deploy to multiple AWS Regions. In cases such as for example these, you can use our AWS Solution Architects to assess hybrid options that may meet your compliance requirements, such as for example using AWS Outposts, Amazon Elastic Container Service (Amazon ECS) Anywhere, or Amazon Elastic Kubernetes Service (Amazon EKS) Anywhere. Another option could be to take into account a DR solution where your on-premises infrastructure can be used as a backup for a workload running on AWS. In some full cases, this might be considered a long-term solution. In others, it might be an interim solution until certain constraints could be removed-for example, a noticeable change to corporate policy or the introduction of additional AWS Regions in a specific country.
Conclusion
Let’s recap by summarizing some guiding principles for architecting compliant DR workloads as outlined in this two-part series:
- Avoid assumptions; confirm the known facts. If it’s not on paper, it’s unlikely to certainly be a mandatory compliance requirement.
- Consult professionals. Legal, privacy, and compliance, in addition to AWS Solution Architects, AWS security and compliance specialists, along with other subject-matter specialists.
- Avoid generalities; concentrate on the specifics. There is absolutely no one-size-fits-all approach.
- Shoot for simplicity, not zero risk. Don’t use multiple AWS Regions when one will suffice.
- Don’t get distracted by exceptions. Concentrate on your current requirements, not workloads you’re not ready to deploy to the cloud yet.
When you have feedback concerning this post, submit comments in the Comments section below.
Want more AWS Security how-to content, news, and show announcements? Follow us on Twitter.


You must be logged in to post a comment.