Disaster recovery compliance within the cloud, part 1: Common misconceptions
Compliance within the cloud may seem challenging, for businesses in heavily regulated sectors such as for example financial services especially. Regulated finance institutions (FIs) must adhere to regulations (often in several jurisdictions), global security specifications, their very own corporate policies, and contractual obligations making use of their clients and counterparties even. These various compliance specifications might impose constraints on what their workloads could be architected for the cloud, and could require interpretation on which FIs must do to become compliant. It’s typical for FIs to create assumptions concerning their compliance requirements, that may result in unnecessary expenses and increased complexity, and may not making use of their strategic objectives align. A modern, rationalized method of compliance might help FIs prevent imposing unwanted constraints while conference their mandatory requirements.
In my own role being an Amazon Web Providers (AWS) Compliance Expert, I use our financial services clients to recognize, assess, and determine answers to deal with their compliance requirements because they proceed to the cloud. Probably the most common problems clients ask me about will be how to adhere to disaster recovery (DR) needs for workloads they intend to operate in the cloud. In this website post, I share a few of the standard misconceptions FIs possess about DR compliance in the cloud. In Part 2, I outline a organized approach to creating compliant architectures for the DR workloads. As my principal market is Canada, the examples in this website article pertain to FIs working in Canada largely, however the principles and guidelines are highly relevant to regulated organizations in virtually any national country.
“Exactly why isn’t there the checklist for compliance within the cloud?”
Compliance specifications are occasionally prescriptive: “if X, you should do Y then.” When needs are prescriptive, it’s generally clear everything you must do to become compliant. For instance, the Payment Cards Industry Data Security Regular (PCI DSS) necessity 8.2.4 obliges businesses that process, shop, or transmit charge card information to “alter user passwords/passphrases at least one time every 3 months.” However in the financial providers sector, compliance specifications for managing operational dangers could be subjective. When regulators consider what is referred to as a principles-based method of setting regulatory anticipations, each FI must assess their specific dangers and determine the mitigating settings essential to conform with the organization’s tolerance for operational danger. Because the guidelines aren’t prescriptive, there is absolutely no “checklist for attaining compliance.” Instead, principles-centered requirements are guidelines that FIs are anticipated to consider because they implement and design technology solutions. They’re, by definition, at the mercy of interpretation and will be susceptible to misconceptions and myths among FIs and their providers. To illustrate this, let’s appearance at two areas of DR that are often misunderstood within the Canadian monetary services industry: information residency and geodiversity.
“My data must stay in nation X”
Information residency or information localization is a requirement of specific data-models processed and stored within an IT system to stay inside a specific jurisdiction (for instance, a nation). As discussed inside our Plan Perspectives whitepaper, unlike historical perspectives, information residency doesn’t provide much better security. Most cyber-episodes are usually perpetrated remotely and attackers aren’t deterred by the actual physical location of these victims. In fact, data residency can set you back an organization’s goals for safety and resilience counter. For instance, data residency needs can limit your options our clients have whenever choosing the AWS Area or Regions where to perform their production workloads. That is especially challenging for customers who would like to use multiple Regions for recovery and backup purposes.
It’s typical for FIs operating in Canada to assume that they’re necessary to keep their data-particularly consumer data-in Canada. The truth is, there’s very small from a statutory viewpoint that imposes this type of constraint. Not one of the private industry privacy laws include information residency specifications, nor do the financial solutions regulatory recommendations. There are several host to records needs in Canadian federal economic providers legislation such as for example THE LENDER Act and The INSURANCE FIRMS Act, but they are narrow in scope and apply primarily to business records relatively. For some Canadian FIs, their specifications are more a outcome of their very own corporate plans or contractual obligations frequently, not imposed simply by public policies or regulations externally.
“My data centers need to apart”< become X kilometers;/h2>
Geodiversity-brief for geographic diversity-will be the idea of maintaining the very least distance between backup and main data processing sites. Geodiversity is founded on the theory that requiring a particular distance between data facilities mitigates the chance of location-dependent disruptions such as for example natural disasters. The basic principle is pertinent in a cloud processing context still, but is not really the only consideration with regards to planning DR. The cloud enables FIs to define operational resilience needs rather than limiting themselves to antiquated company continuity preparing and DR principles like physical data middle implementation requirements. Legacy disaster recovery architectures and options, and lifting and shifting this kind of DR strategies in to the cloud, can diminish the possible benefits of making use of the cloud to boost operational resilience. Modernizing your details technology does mean modernizing your organization’s method of DR.
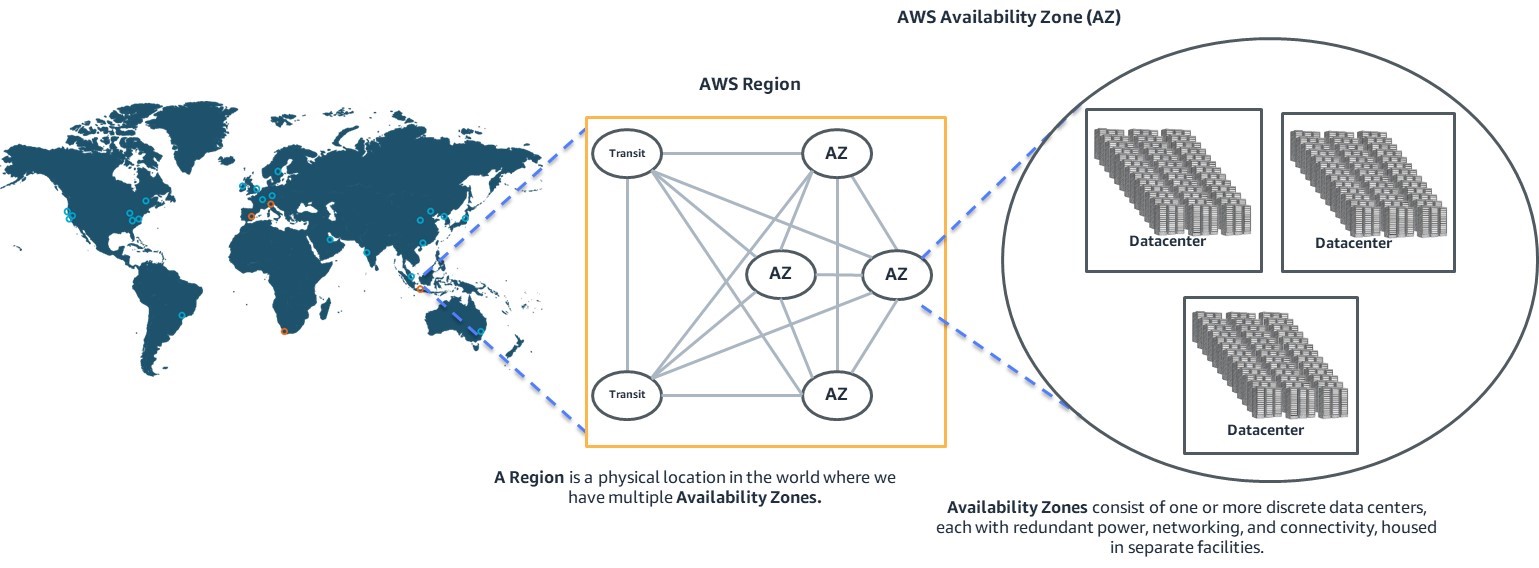
In the cloud, vast physical distance separation can be an anti-pattern-it’s an arbitrary metric that does little to greatly help organizations achieve availability and recuperation objectives. At AWS, we style our global infrastructure in order that there’s a meaningful range between your Availability Zones (AZs) in a AWS Region to aid high availability, but near sufficient to facilitate synchronous replication across those AZs (an AZ being truly a cluster of information centers). Figure 1 displays the relationship between Areas, AZs, and data facilities.
Synchronous replication across several AZs allows you to minimize data loss (thought as the recovery point goal or RPO) and reduce the quantity of time that workloads are unavailable (thought as the recovery time goal or RTO). Nevertheless, the low latency necessary for synchronous replication will become less achievable because the distance between information centers increases. As a result, a geodiversity necessity that mandates the very least distance between data facilities that’s too much for synchronous replication might prohibit you from benefiting from AWS’s multiple-AZ architecture. A multiple-AZ architecture can perform RPOs and RTOs that aren’t achievable with a straightforward geodiversity mitigation strategy. For more information, make reference to the AWS whitepaper Disaster Recuperation of Workloads on AWS: Recovery within the Cloud.
Once again, it’s a standard perception among Canadian FIs that the disaster recuperation architecture because of their production workloads must adhere to specific geodiversity requirements. Nevertheless, you can find no statutory requirements relevant to FIs working in Canada that mandate the very least distance between data facilities. Some FIs could have corporate guidelines or contractual obligations that impose geodiversity requirements, but for many FIs I’ve caused, geodiversity is really a < usually;em>suggested practice when compared to a formal policy rather. Informal corporate guidelines might have some value, however they aren’t absolute guidelines and shouldn’t be dealt with exactly like mandatory compliance requirements. In any other case, you might be unintentionally restricting yourself from benefiting from far better risk management techniques.
“But if it is a compliance necessity, doesn’t that mean I’ve no selection?”
Both of the prior examples illustrate the significance of not merely confirming your compliance specifications, but recognizing the foundation of these requirements also. It may be infeasible to acquire an exception to an externally-imposed obligation like a regulatory necessity, but exceptions as well as revisions to corporate plans aren’t unthinkable if you can show that modern techniques provide equal or higher protection against a specific risk-for example, the higher availability and fast recoverability supported by way of a multiple-AZ architecture. Think about whether your compliance requirements give some known degree of flexibility within their application.
Furthermore, because several needs are principles-based, they might be subject to interpretation. You have to think about the specific vocabulary of the necessity in the context of the workload. For instance, a data residency necessity may not explicitly prohibit you from storing a duplicate of the content internationally for backup and recuperation purposes. For this good reason, I would recommend that you consult relevant specialists from your own legal, personal privacy, and compliance groups to assist in the interpretation of compliance specifications. You understand the lawful boundaries of one’s compliance requirements once, AWS Solutions Architects along with other financial services industry specialists such as for example myself will help you assess viable options to meet up your preferences.
Bottom line
In this very first section of a two-part collection, I provided a few examples of common misconceptions possess about compliance needs for disaster recovery inside the cloud FIs. The key would be to avoid producing assumptions that may impose better constraints on your own architecture than are essential. In Component 2, I demonstrate a structured method for architecting compliant DR workloads which will help you to prevent these preventable missteps.
For those who have feedback concerning this post, submit remarks in the Remarks area below.
Want a lot more AWS Security how-to articles, news, and show announcements? Stick to us on Twitter.


You must be logged in to post a comment.