Define a custom program duration and terminate dynamic sessions in IAM Identification Center
Managing usage of applications and accounts takes a balance between delivering basic, convenient access and handling the risks connected with active user classes. Predicated on your organization’s requirements, you might like to ensure it is simple for customers to sign in also to operate long good enough to obtain their work done, minus the disruptions connected with requiring re-authentication. You could also consider shortening the session to greatly help meet your protection or compliance requirements. Simultaneously, you might want to terminate active sessions your users don’t need, such as for example sessions for former workers, sessions that the user didn’t sign out on another device, or periods with suspicious activity.
<pre> <code> <p>With <a href="https://aws.amazon.com/iam/identity-middle/" target="_blank" rel="noopener">AWS IAM Identification Middle (successor to AWS Individual Sign-On)</the>, you now have the choice to configure the correct session duration for the organization’s needs when using new session administration capabilities to check up active user classes and revoke unwanted periods.</p>
<p>In this website post, You’re showed by me how exactly to use these new functions in IAM Identification Center. First, You’re walked by me through how exactly to configure the program duration for the IAM Identity Center users. You then are showed simply by me how exactly to identify existing active sessions and terminate them.</p>
<h2>What’s IAM Identification Center?</h2>
<p><a href=”https://aws.amazon.com/iam/identity-middle/” target=”_blank” rel=”noopener”>IAM Identity Middle</a> can help you safely create or connect your workforce identities and manage their entry centrally across AWS accounts and apps. IAM Identity Center may be the recommended method for workforce identities to gain access to AWS assets. In IAM Identity Middle, you can integrate having an external identity service provider (IdP), such as for example Okta General Directory, Microsoft Azure Dynamic Directory, or Microsoft Dynamic Directory Domain Services, being an identity source or it is possible to create users within IAM Identification Center directly. The ongoing service is made on the capabilities of <a href=”https://aws.amazon.com/iam/” focus on=”_blank” rel=”noopener”>AWS Identity and Accessibility Management (IAM)</the> and emerges at no additional expense.</p>
<h2>IAM Identity Center classes< and sign-in;/h2>
<p>You may use IAM Identity Center to gain access to accounts and applications also to get credentials for the <a href=”https://aws.amazon.com/console/” focus on=”_blank” rel=”noopener”>AWS Management Gaming console</the>, <a href=”https://aws.amazon.com/cli/” focus on=”_blank” rel=”noopener”>AWS Command Line User interface (AWS CLI)</the>, and <a href=”https://aws.amazon.com/developer/tools/” focus on=”_blank” rel=”noopener”>AWS SDK</the> sessions. Once you get on IAM Identity Center by way of a web browser or the AWS CLI, an AWS accessibility portal session is established. When you federate in to the console, IAM Identification Center uses the program period setting on the authorization set to regulate the length of the program.</p>
<blockquote>
<p><strong>Be aware</strong>: The access portal session timeframe for IAM Identity Middle differs from the <a href=”https://docs.aws.amazon.com/singlesignon/most recent/userguide/howtosessionduration.html” focus on=”_blank” rel=”noopener”>IAM permission set program duration</the>, which defines just how long a user can gain access to their accounts through the IAM Identification Center gaming console.</p>
</blockquote>
<p>Prior to the release of the brand new session management function, the AWS access portal session duration was fixed at 8 hours. You can now configure the session period for the AWS entry portal in IAM Identification Center from quarter-hour to 7 days. The access portal program duration determines the way the user can accessibility the portal long, programs, and accounts, and operate CLI instructions without re-authenticating. Should you have an exterior IdP linked to IAM Identity Middle, the access portal program duration would be the lesser of either the program duration that you occur your IdP or the program length defined in IAM Identification Center. Users can gain access to applications and accounts before access portal program expires and initiates re-authentication.</p>
<p>When users access apps or accounts through IAM Identification Center, it creates yet another session that’s separate but linked to the AWS entry portal program. AWS CLI sessions utilize the AWS accessibility portal session to gain access to functions. The duration of console periods is defined as area of the authorization set that an individual accessed. Whenever a console program starts, it continues before duration expires or an individual ends the program. IAM Identity Center-enabled program sessions re-verify the AWS gain access to portal session around every 60 mins. These sessions continue before AWS access portal program terminates, until another application-specific problem terminates the program, or before user terminates the program.</p>
<p>In summary:</p>
<ul>
<li>Following a user signs directly into IAM Identity Center, they are able to access their assigned applications and functions for a set period, after which they need to re-authenticate.</li>
<li>In case a user accesses an assigned permission set, an individual has usage of the corresponding function for the duration defined in the permission set (or by an individual terminating the session).</li>
<li>The AWS can be used by the AWS CLI access portal session to gain access to roles. The AWS CLI refreshes the IAM authorization set in the backdrop. The CLI work continues to run before access portal program expires.</li>
<li>If customers access an IAM Identification Center-enabled application, an individual can retain usage of an application for an hour following the access portal program has expired.</li>
</ul>
<blockquote>
<p><strong>Notice</strong>: IAM Identity Center doesn’t presently support session management abilities for <a href=”https://docs.aws.amazon.com/singlesignon/newest/userguide/manage-app-session.html” focus on=”_blank” rel=”noopener”>Energetic Directory identity sources.</the></p>
</blockquote>
<p>To learn more about session management functions, see <a href=”https://docs.aws.amazon.com/singlesignon/most recent/userguide/authconcept.html#sessionsconcept” target=”_blank” rel=”noopener”>Authentication classes</the> in the documentation.</p>
<h2>Configure session timeframe</h2>
<p>In this area, I show you how exactly to configure the program duration for the AWS access portal in IAM Identity Center. It is possible to choose a program duration between a quarter-hour and seven days.</p>
<p>Program duration is really a global setting inside IAM Identity Center. Once you set the program duration, the utmost session duration pertains to IAM Identity Center customers.</p>
<h3>To configure program duration for the AWS entry portal:</h3>
<ol>
<li>Open up the <a href=”https://system.aws.amazon.com/singlesignon” focus on=”_blank” rel=”noopener”>IAM Identity Center gaming console</the>.</li>
<li>In the remaining navigation pane, choose <strong>Configurations</strong>.</li>
<li>On the <strong>Configurations</strong> page, pick the <strong>Authentication</strong> tab.</li>
<li>Under <strong>Authentication</strong>, close to <strong>Session configurations</strong>, select <strong>Configure</strong>. </li>
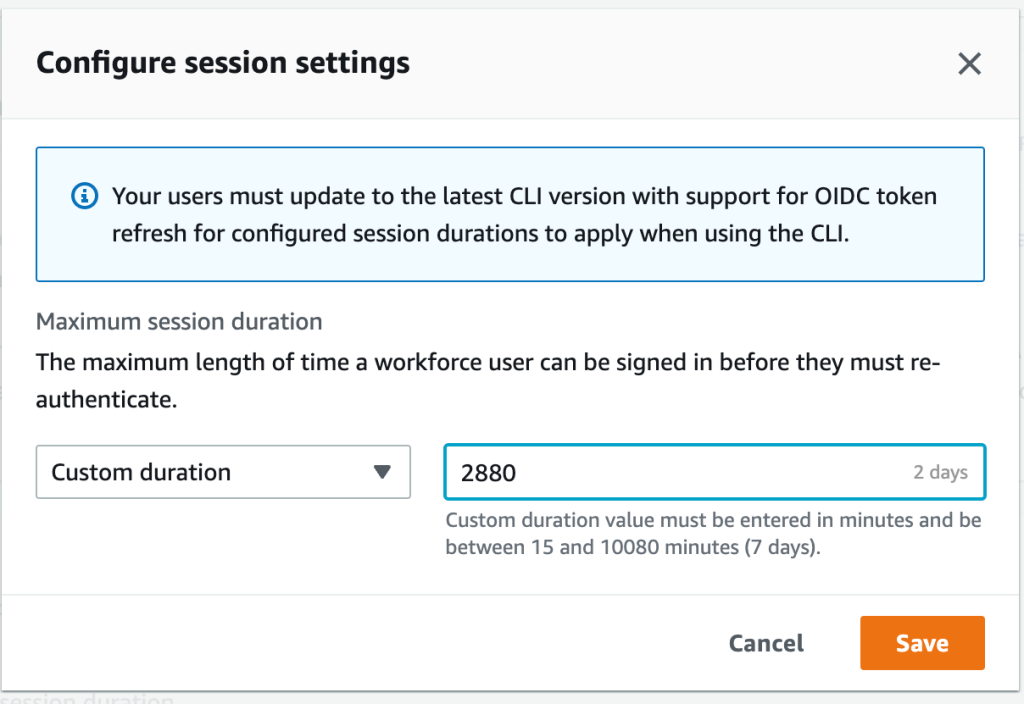
<li>For <strong>Configure program settings</strong>, select a maximum session period from the set of pre-defined program durations in the dropdown. To create a custom program duration, go for <strong>Custom made duration</strong>, enter the distance for the program in minutes, and choose < then;strong>Save</strong>. </li>
</ol>
<div id=”attachment_28419″ course=”wp-caption alignleft”>
<img aria-describedby=”caption-attachment-28419″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2023/01/27/img1-5-1024×704.png” alt=”Body 1: Established access portal program duration” width=”760″ course=”size-large wp-picture-28419″>
<p id=”caption-attachment-28419″ course=”wp-caption-text”>Figure 1: Set access portal program duration</p>
</div>
<p>Congratulations! You possess modified the session duration for the users just. This new duration shall take influence on each user’s next sign-in.</p>
<h2>Discover and terminate AWS accessibility portal periods</h2>
<p>With this particular new release, you will discover active portal sessions for the IAM Identity Center users, and when needed, it is possible to terminate the sessions. This could be useful in situations like the following:</p>
<ul>
<li>The user no more works for the organization or was taken off tasks that gave them usage of applications or permission models that they should no more use.</li>
<li>In case a gadget is stolen or shed, you could be contacted by an individual to get rid of the session. This reduces the chance that someone shall access these devices and utilize the open session.</li>
</ul>
<p>In these full cases, you can get a user’s active sessions in the AWS access portal, choose the session that you’re thinking about, and terminate it. According to the situation, you could also desire to deactivate sign-in for an individual from the operational program before revoking the user’s session. It is possible to deactivate sign-in for customers in the IAM Identification Center system or in your third-celebration IdP.</p>
<p>In the event that you deactivate the user’s sign-in in your IdP first, and deactivate the user’s sign-in in IAM Identity Center then, deactivation shall take impact in IAM Identity Middle without synchronization latency. However, in the event that you deactivate an individual in IAM Identity Middle first, then it’s possible that the IdP could activate an individual again. By initial deactivating the user’s sign-in in your IdP, it is possible to avoid the user from signing in once you revoke their program again. This step is advisable whenever a consumer has left your company and should no more have access, or if you suspect a legitimate user’s credentials had been stolen and you desire to block access and soon you reset the user’s passwords.</p>
<p>Termination of the gain access to portal session will not affect the dynamic permission set program started from the entry portal. IAM role program duration when assumed from the accessibility portal will last provided that the duration specified in the authorization established. For AWS CLI classes, it can take around an full hr for the CLI to terminate following the access portal program is terminated.</p>
<blockquote>
<p><strong>Suggestion</strong>: Activate <a href=”https://aws.amazon.com/iam/features/mfa/” focus on=”_blank” rel=”noopener”>multi-aspect authentication (MFA)</the> whenever we can. MFA provides an additional level of protection to greatly help prevent unauthorized people from gaining usage of systems or information.</p>
</blockquote>
<h3>To control active access portal periods in the AWS gain access to portal:</h3>
<ol>
<li>Open up the <a href=”https://gaming console.aws.amazon.com/singlesignon” focus on=”_blank” rel=”noopener”>IAM Identity Center system.</the></li>
<li>In the still left navigation pane, choose <strong>Customers</strong>.</li>
<li>On the <strong>Customers</strong> page, pick the username of an individual whose sessions you wish to manage. This goes to a full page with the user’s details.</li>
<li>On the user’s page, pick the <strong>Energetic sessions</strong> tab. The real number in parentheses close to <strong>Energetic sessions</strong> indicates the real number of current dynamic sessions because of this user.
<div id=”attachment_28420″ course=”wp-caption alignleft”>
<img aria-describedby=”caption-attachment-28420″ src=”https://d2908q01vomqb2.cloudfront.net/22d200f8670dbdb3electronic253a90eee5098477c95c23d/2023/01/27/img2-6-1024×464.png” alt=”Amount 2: View dynamic access portal classes” width=”680″ course=”size-large wp-picture-28420″>
<p id=”caption-attachment-28420″ course=”wp-caption-text”>Figure 2: View active entry portal periods</p>
</div> </li>
<li>Choose the sessions you want to delete, and select <strong>Delete session</strong>. A dialog container shows up that confirms you’re deleting active classes for this user.
<div id=”attachment_28421″ course=”wp-caption alignleft”>
<img aria-describedby=”caption-attachment-28421″ src=”https://infracom.com.sg/wp-content/uploads/2023/02/img3-4-1024×589-1.png” alt=”Determine 3: Delete selected dynamic sessions” width=”680″ course=”size-large wp-picture-28421″>
<p id=”caption-attachment-28421″ course=”wp-caption-text”>Figure 3: Delete selected active periods</p>
</div> </li>
<li>Examine the given information within the dialog box, and if you would like to continue, select <strong>Delete session</strong>.</li>
</ol>
<h2>Bottom line</h2>
<p>In this website post, you discovered how IAM Identity Center manages classes, how exactly to modify the program duration for the AWS access portal, and how exactly to view, lookup, and terminate active access portal periods. I furthermore shared some easy methods to take into account the appropriate session length for your use situation and related methods that you ought to take when terminating classes for customers who shouldn’t have authorization to register again after their program is finished.</p>
<p>With this particular new feature, you have significantly more control over user program management now. You may use the console to create configurable session lengths predicated on your organization’s safety specifications and desired end-user knowledge, and you will terminate sessions also, helping you to manage sessions which are longer needed or possibly suspicious no.</p>
<p>For more information, notice <a href=”https://docs.aws.amazon.com/singlesignon/newest/userguide/manage-app-session.html” focus on=”_blank” rel=”noopener”>Manage IAM Identity Middle integrated application periods</the>.</p>
<p> <br>In case you have feedback concerning this post, submit remarks in the<strong> Remarks</strong> area below. For those who have questions concerning this write-up, <a href=”https://gaming console.aws.amazon.com/assistance/home” focus on=”_blank” rel=”noopener noreferrer”>contact AWS Assistance</the>.</p>
<p><strong>Want a lot more AWS Security news? Stick to us on <a name=”Twitter” href=”https://twitter.com/AWSsecurityinfo” focus on=”_blank” rel=”noopener noreferrer”>Twitter</the>.</strong></p>
<!– ‘”` –>
